Ongoing IMAP Scan, Anyone Else?
I'm operating a mail server which handles email flows from multiple domains (<20 domains). The server is under a massive IMAPS (port 993) scan for a few days. More details about the ongoing attack:
- Some logins are valid
- Some logins seem to be part of a dictionary
- Some logins are old or unused (like scraped from web pages)
- Some logins have a format 'user@domain.tld', other just the 'user'
[Update: some IP addresses are also testing SMTP AUTH]
There is a strong password policy in place and no credentials were compromized. This is not a brute-force attack, connection attempts are coming by waves. The only impact until now was a pollution of my logs!

There is an OSSEC active-response[1] with the 'repeated_offender' feature enabled (at 30, 60, 120, 240, 480 minutes) but new IP addresses are always detected (like being part of a bot):
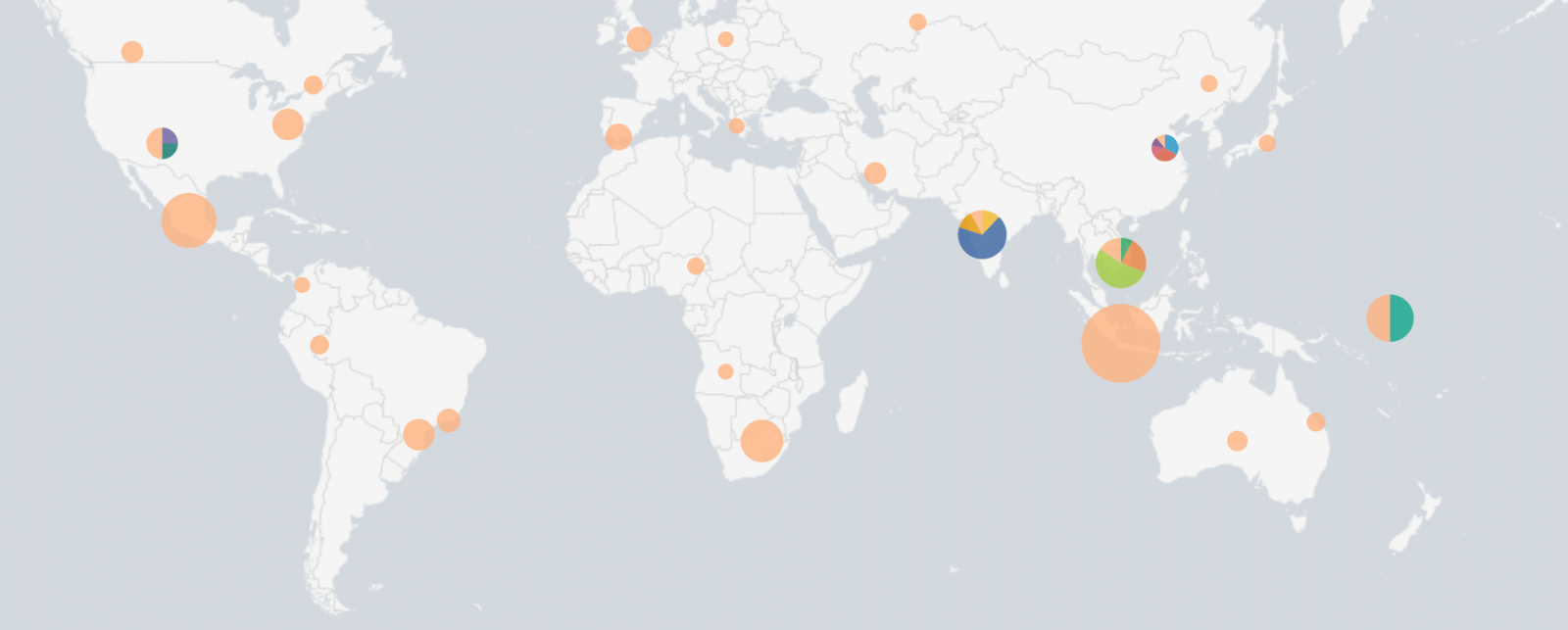
I searched for more information about the offending IP addresses, they do not seem to belong to a known botnet. They are not Tor exit-nodes. Here is the top-10 of active IP addresses:
155.133.82.55
%%ip:184.71.40.22%%
%%ip:50.39.0.12%%
%%ip:185.130.6.226%%
%%ip:119.29.229.87%%
%%ip:80.200.28.68%%
%%ip:80.82.64.102%%
%%ip:212.118.124.109%%
%%ip:139.255.51.42%%
%%ip:151.253.48.108%%
Someone else has already detected the same kind of scan?
[1] http://ossec-docs.readthedocs.io/en/latest/manual/ar/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | British Summer Time | Jul 28th - Aug 1st 2025 |



Comments
Anonymous
Sep 12th 2016
8 years ago
Greg
Anonymous
Sep 14th 2016
8 years ago