Who Is Hunting For Your IPTV Set-Top Box?
 Ever considered starting a company to create software for TV channel distribution over IP? It is big business with service providers "converging" their networks. Everything is better over IP. Why not TV? Having TVs and set-top boxes with two-way IP connectivity allows you to collect all kinds of data from your users. Imagine you cannot only charge people for the content, but you can also sell their data to advertisers. You will know exactly what they watch and when. Are they flipping channels during commercials?
Ever considered starting a company to create software for TV channel distribution over IP? It is big business with service providers "converging" their networks. Everything is better over IP. Why not TV? Having TVs and set-top boxes with two-way IP connectivity allows you to collect all kinds of data from your users. Imagine you cannot only charge people for the content, but you can also sell their data to advertisers. You will know exactly what they watch and when. Are they flipping channels during commercials?
If you would start a company like this: How would you name it? Of course, someone already created a company like this and called it "Stalker" (no kidding!). Then they hired a legal team and "proper" executives, so they renamed it to Ministra (sounds much... well... anyway. it isn't called Stalker at least). But as so often, the original company name survived in their software, and that attracted my attention to these log entries in my honeypot:
GET /stalker_portal/c/version.js HTTP/1.1
Ministra's software ("Stalker Portal") is typically installed on set-top boxes that will then connect to Ministra and various service providers to retrieve content. They had some interesting vulnerabilities in the past, including remote code execution vulnerabilities [1]. There appear to be hundreds of streaming services using this platform.
The request above attempts to download the file version.js, which will tell the attacker what version of the software you are running. We do run HTTP honeypots on different ports, and interestingly, these requests come in almost equally distributed on these ports:
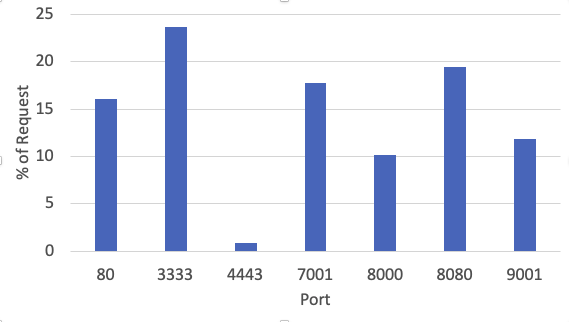
Distribution of Requests among ports
But are these bots just looking for what version you are running? They certainly have more in mind looking at other requests from the same botnet:
HEAD /
GET /system_api.php
GET /c/version.js
GET /
GET /stalker_portal/c/version.js
GET /streaming/clients_live.php
GET /stream/live.php
GET /flu/403.html
GET /b2.php?a=165.22.51.183
The "system_api.php," "version.js," "live.php," and "clients_live.php" requests are related to the Stalker Portal software. They may, in some cases, allow an attacker to download content from the device.
The main purpose of these requests is likely not to compromise the device but to steal content or use the device remotely, for example, to find devices with subscriptions that can stream content from other countries?
flu/403.html and b2.php are likely unrelated (also seeing less of these requests from this particular network).
[1] https://research.checkpoint.com/2019/we-decide-what-you-see-remote-code-execution-on-a-major-iptv-platform/
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|

Comments