Those pesky registry keys required by critical security patches
With the “storm” around Meldown and Spectre slowly winding down, I would like to remind everyone on registry changes that are required by the latest patches released by Microsoft.
In most cases, the anti-virus that you are running should have created the required registry key that will allow installation of the released security patches. However, keep in mind that if the registry key is not present, that the patches will not be installed: not only that, in case the registry key is missing even future patches might not be installed, according to the Microsoft’s support web page at https://support.microsoft.com/en-us/help/4072699/january-3-2018-windows-security-updates-and-antivirus-software.
So, in order to make sure that all patches have been successfully installed make sure that the registry key mentioned in the article exists – there are various tools that can help with this.
The story with the registry key reminded me of another critical security patch that also requires a registry key to be set in order to properly work. I often tend to find servers missing this in internal penetration test, and the consequences are very serious.
The patch I am referring to is KB2871997 (https://docs.microsoft.com/en-us/security-updates/SecurityAdvisories/2016/2871997), originally from 2014. This patch helps remove clear text credentials from memory on affected Windows operating systems – something that Mimikatz, an attacker’s favorite tool successfully exploits.
In the figure below you can see how Mimikatz successfully extracts the plain text password from an unpatched Windows 2008R2 server.
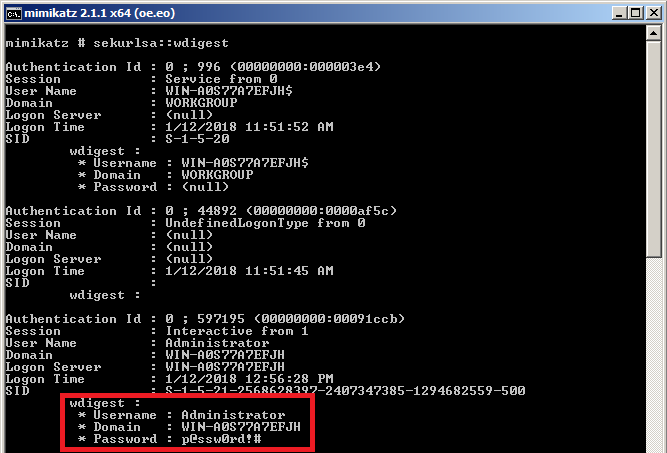
Unfortunately, even after installing the patch, the clear text password is still in memory – Microsoft presumably did not want to change the default behavior for WDigest. The problem is that many administrators missed that the registry key needs to be added – as I mentioned previously, in (too) many internal penetration tests I find Windows 2008R2 servers which are fully patched, but miss this registry key. Once an attacker gets administrator privileges, on such a system, he can run Mimikatz and dump plain text password.
Additionally, after applying the patch, you also need to reboot the server for the patch to finally take effect – until the server has been rebooted the passwords are still available in memory. Once this has been finally done, plain text passwords will not be available in the memory, as shown in the figure below:
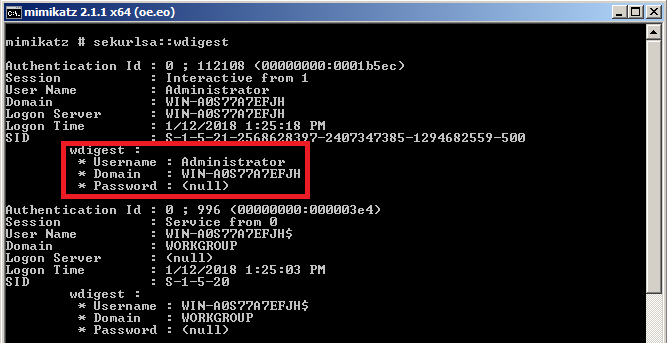
If you are still running Windows 2008R2 servers, make sure that both the patch and registry key have been successfully applied. Additionally, make sure that you monitor this registry key and any potential changes on servers: an attacker could possibly change the value of the registry key to any other value (i.e. 1) and wait for the server to reboot; once rebooted the server will again start keeping plain text passwords in memory. Something to watch for.

Comments
So you will have to create it manually in order for Windows to stop caching the plain-text password in memory.
Once you do that (you can use DWORD 32-bit) make sure that all users fully log out or you restart the server in order to clear previously cached plain-text passwords in memory.
Anonymous
Jan 17th 2018
6 years ago