Testing your website for the heartbleed vulnerability with nmap
by Manuel Humberto Santander Pelaez (Version: 1)
We have received reports by many readers about buggy tools to test for the heartbleed vulnerability. Today I want to show you how easy it is to check for this vulnerability using a reliable tool as nmap.
You just need to trigger a version scan (-sV) along with the script (ssl-heartbleed). The following example with show a command that will scan 192.168.0.107 for this bug:
nmap -sV 192.168.0.107 --script=ssl-heartbleed
This will be the output for a non-vulnerable website. As you can see, no warnings are shown:
.png)
If you are vulnerable, you will get the following:
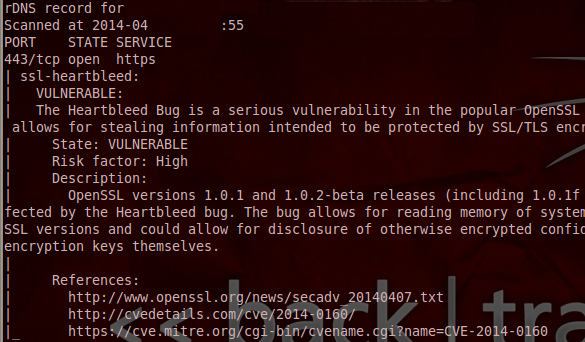
For vulnerability testing, always use reliable tools which won't contain malicious code infecting your computer and won't give you false positive messages.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter:@manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org



Comments
I had to. :)
Anonymous
Apr 18th 2014
1 decade ago
edit ssl-heartbleed.nse portrule function to always return true
portrule = function(host, port)
-- return shortport.ssl(host, port) or sslcert.isPortSupported(port)
return true
end
[cgm@silver ~]$ nmap -p1133 --script=ssl-heartbleed 127.0.0.1
Starting Nmap 6.45 ( http://nmap.org ) at 2014-04-18 21:29 EEST
Nmap scan report for 127.0.0.1
Host is up (0.13s latency).
PORT STATE SERVICE
1133/tcp open unknown
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
Anonymous
Apr 18th 2014
1 decade ago
Anonymous
Apr 19th 2014
1 decade ago
Anonymous
Apr 19th 2014
1 decade ago
Anonymous
Apr 19th 2014
1 decade ago
http://www.tlca.net/forums
Anonymous
Apr 20th 2014
1 decade ago
Anonymous
Apr 21st 2014
1 decade ago
Anonymous
Apr 24th 2014
1 decade ago
<a href="http://holy.be">Test my site</a>
Anonymous
Apr 25th 2014
1 decade ago