SystemBC Malware Activity
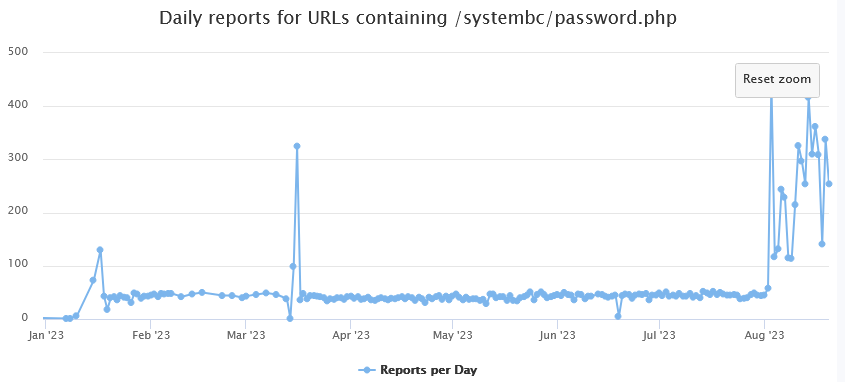
This month, my DShield sensor captured for the first time this request: /systembc/password.php. I checked back for the past 6 months and only have noticed this request this 5 times this month from 4 different sources. According to some references, this is likely the SystemBC Remote Access Trojan (RAT), all 4 IPs are part of the Digital Ocean ASN and only one has been reported as likely malicious. Several samples have been reported to Any.run this month.
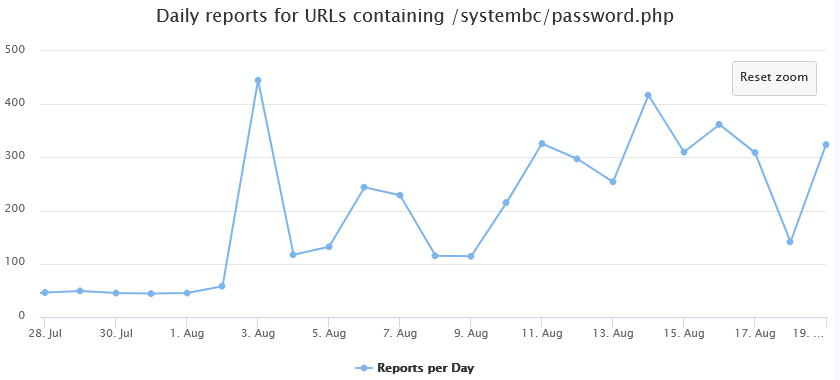
To verified if there was some kind of change, I reviewed DShield logs submission for the past year and noticed nothing really significant until the beginning of Jan 2023 looking for this directory. However, starting on the 3rd of Aug 2023, there a significant change in the daily report for this directory going from an average of 30 submission to 445 and overing in the hundred since then.[1]
Indicator of Compromised
170.64.155.243
161.35.62.73
165.22.160.237
178.128.79.70
/systembc/password.php
/upl.php
[1] https://isc.sans.edu/weblogs/urlhistory.html?url=%2Fsystembc%2Fpassword.php
[2] https://isc.sans.edu/diary/Excel+spreadsheets+push+SystemBC+malware/27060
[3] https://malpedia.caad.fkie.fraunhofer.de/details/win.systembc
[4] https://medium.com/walmartglobaltech/inside-the-systembc-malware-as-a-service-9aa03afd09c6
[5] https://bazaar.abuse.ch/sample/964a9d8fbfd1886a93c1c09493db044bd37e517c4def61aa779c8734cb5cd68d/
[6] https://any.run/malware-trends/systembc
[7] https://www.virustotal.com/gui/ip-address/178.128.79.70/detection
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu

Comments