SSH Honeypots (Ab)used as Proxy
$ ssh -L 8443:192.168.254.10:443 user@192.168.254.2
$ ssh -D 8080 user@192.168.254.10
| Event | Hits |
| cowrie.direct-tcp.request | 24242 |
| cowrie.direct-tcp.data | 22967 |
| cowrie.log.open | 15130 |
| cowrie.log.closed | 14679 |
| cowrie.session.connect | 13882 |
| cowrie.session.closed | 13877 |
| cowrie.command.success | 11563 |
| cowrie.client.version | 9019 |
| cowrie.login.success | 8652 |
| cowrie.command.failed | 3948 |
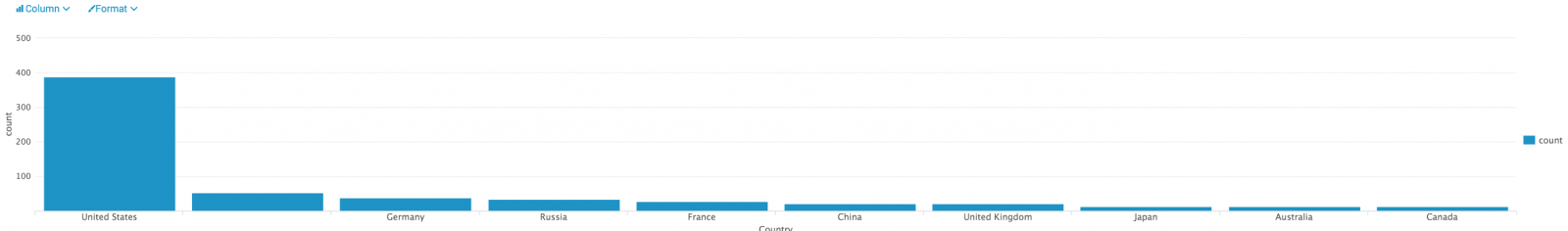
| Country | Hits |
| Germany | 22405 |
| Russia | 1295 |
| United States | 267 |
| Argentina | 76 |
| France | 51 |
| Switzerland | 35 |
| Netherlands | 26 |
| Ukraine | 20 |
| India | 16 |
| Iran | 16 |
| TCP Ports | Hits |
| 80 | 31431 |
| 25 | 1428 |
| 587 | 383 |
| 443 | 271 |
| 465 | 160 |
| 110 | 30 |
| 143 | 13 |
| 1101 | 4 |
| 1102 | 4 |
| 89 | 1 |
If we analyze the relations between the honeypots, sources and destinations, we see that some destinations (blue) were targeted by more than one attacker (green) connected on different honeypots (red):
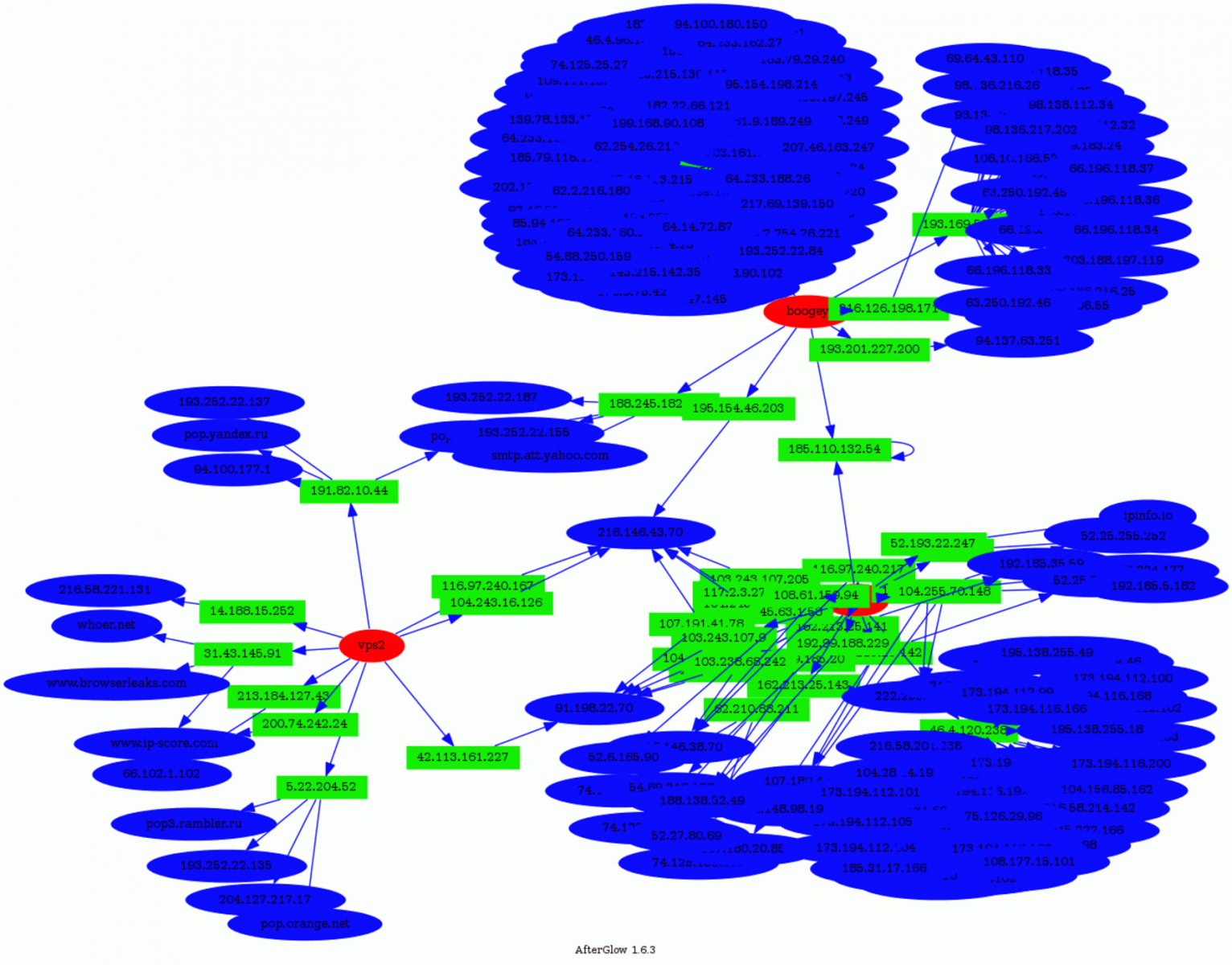
- www.google-analytics.com
- tags.tagcade.com (an ads tag management system)
Some people trying to abuse those services? Feel free to share your findings if you also detected such kind of activity!
To conclude: attackers are not only scanning the Internet to find vulnerable hosts and turn them in bots. They are also looking for ways to hide themselves to perform (maybe) more complex or dangerous attacks.
And keep in mind that if you allow users to SSH to systems that can access the Internet, they can be used as a solution to bypass classic controls in place!
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | British Summer Time | Jul 28th - Aug 1st 2025 |



Comments
is it possible disable Port Forwarding in cowrie?
Searching into my logs... I guess they are using me for spam attacks?!
# Port dst
6828 25
1735 587
790 465
352 80
237 25000
...
Should I use iptables to block outgoing requests?
Thank you very much,
Al
Anonymous
Mar 14th 2016
9 years ago
If I connect to a computer via a private ip address - as shown in the example - and use this computer as a proxy, I don't surf the web with that computers private, but with it's public ip address.
If I could surf showing a private IP address only, that would indeed be an absolutely anonymous surfing. Unfortunately an absolutely unroutable surfing as well..
But surfing under the public address of a third server is more like surfing under a false flag. Since someone is the owner of this proxy and this owner will be able to trace back my surfing session to my computer. Or, if I'm the owner of this server byself, I haven't won anything.
Anonymous
Mar 14th 2016
9 years ago
They are intercepted and logged. No need to prevent them with your local firewall.
Don't disable them, log them and enjoy :)
Anonymous
Mar 14th 2016
9 years ago
But:
- If such SSH server is badly configured, I doubt that logs will be collected (and reviewed!) (IMHO)
- SSH does NOT log TCP forwarding events by default, you'll have to correlate multiple sources to get the attacker's IP. A starting incident could be: "Why is this server sending HTTP requests to Facebook?"
For most of the script kiddies, it is safe enough to abuse SSH servers!
Anonymous
Mar 14th 2016
9 years ago
Source IP statistics:
# Attacker IP
13353 193.169.52.221
7121 193.169.52.214
4882 193.169.52.213
2315 193.169.52.220
621 193.169.52.211
78 193.169.52.212
47 193.169.52.210
17 193.201.225.84
9 193.201.227.200
2 136.243.55.198
1 199.255.137.120
Destination TCP port statistics:
# Target port
22835 25
2575 587
1061 465
1025 80
522 443
293 25000
48 2525
31 26
16 3535
7 143
5 8025
5 6125
5 1025
4 53
3 8800
3 165
2 7777
2 5050
2 250
2 2025
Anonymous
Mar 14th 2016
9 years ago
Anonymous
Mar 14th 2016
9 years ago
http://bl0gg.ruberg.no/2016/02/honeynet-outbound-probes/
http://bl0gg.ruberg.no/2016/02/visualizing-honeypot-activity/
http://bl0gg.ruberg.no/2016/03/visualizing-honeypot-activity-part-ii-tree-maps/
The sheer number of attempts makes relationship maps difficult with data for more than a few days. I've found drill-down treemaps useful for this kind of focused activity.
Anonymous
Mar 14th 2016
9 years ago
Anonymous
Mar 14th 2016
9 years ago
A 'cowrie.json' log will be created.
Anonymous
Mar 14th 2016
9 years ago
Look at the referred tag. I've been doing a very intense study of this and have found that folks using socks proxying in this matter browse pretty much one thing; Porn. And lots of it.
Zach W.
Anonymous
Mar 17th 2016
9 years ago