SSH Fingerprints Are Important
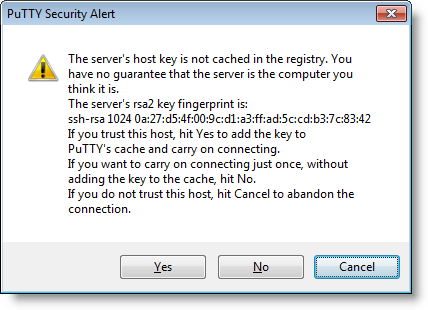
Some years ago, I was preparing Cisco certification exams. I connected via SSH to a new Cisco router, and was presented with this familiar dialog:
This made me think: before proceeding, I wanted to obtain the fingerprint out-of-band, via a trusted channel, so that I could verify it. So I took a console cable, logged on via the serial console, and … then I started to wonder what IOS command to type? A couple of hours later spend with Google, I was no closer to a solution. I could not find an IOS command to display the SSH fingerprint.
I found forum posts advising to connect via a crossover cable and write the presented SSH fingerprint down, but that’s not what I wanted. I had to work out my own solution.
There’s an IOS command to dump your public key: show crypto key mypubkey rsa
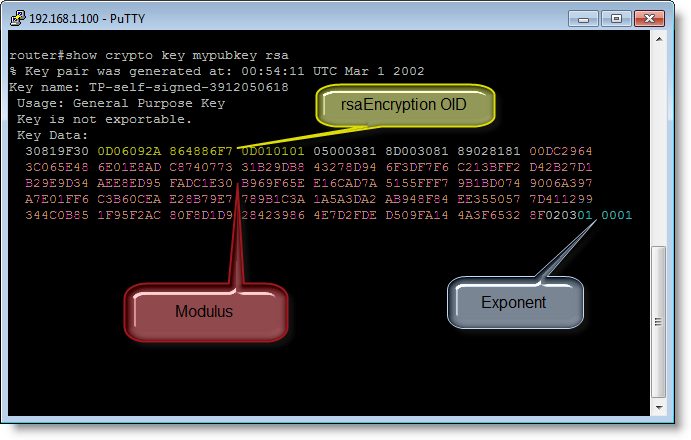
If you take the modulus and exponent of your public key, arrange them in another format (ssh-rsa) and calculate the MD5 hash, then you obtain the fingerprint.
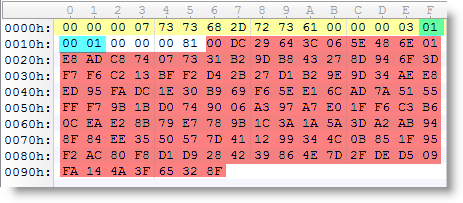
Of course, I could not resist writing a Python program for that :-)
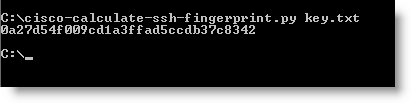
You can find it here.
If you know a Cisco IOS command to obtain the SSH fingerprint key directly, then please post a comment.
Update: on Cisco IOS versions released after I researched this, the "show ip ssh" command now displays the public key in ssh-rsa format (tested on 15.1(4)M3):
SSH Enabled - version 2.0
Authentication timeout: 120 secs; Authentication retries: 3
Minimum expected Diffie Hellman key size : 1024 bits
IOS Keys in SECSH format(ssh-rsa, base64 encoded):
ssh-rsa AAAAB3NzaC1yc2EAA.....
If you decode the base64 encoded ssh-rsa data, and calculate the MD5, you obtain the fingerprint.



Comments
http://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus1000/sw/4_0/security/configuration/guide/n1000v_security/security_6ssh.html
Anonymous
Apr 3rd 2015
1 decade ago
Anonymous
Apr 3rd 2015
1 decade ago
On devices that support the sh ip ssh command you can copy the key, create a new file and run ssh-keygen -lf ios.pub to calculate the finger print.
On the Cisco device
3750x#sh ip ssh
SSH Enabled - version 2.0
Authentication methods:publickey,keyboard-interactive,password
Encryption Algorithms:aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc,aes192-cbc,aes256-cbc
MAC Algorithms:hmac-sha1,hmac-sha1-96
Authentication timeout: 120 secs; Authentication retries: 3
Minimum expected Diffie Hellman key size : 1024 bits
IOS Keys in SECSH format(ssh-rsa, base64 encoded):
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAAAgQDQbH8FnvSpDpEsL3OzzWal1DCFBQmiImg4WWhSwlCu
9mdHb53YigPEXJOlsVdX9KTKIACvwyHu5+yRQXa6+7Ahp7f98c1ac8wRW4Q8EP35kI00l+40LoC5G8eM
iZ5Pz8o8UyAD/zmY1vWJzxs8k4mtdvgI4Pf5C3mmJ8r2nu0Zjw==
Copy the ssh-rsa key including the ssh-rsa and ==.
On you linux\*BSD box create a new file and paste the key in. Make sure it’s one long string with no wrap. In this example I used ios.pub as the file.
Then run the ssh-Keygen utility with the -lf options:
[mhubbard@1s1k-do .ssh]$ ssh-keygen -lf ios.pub
1024 73:e9:e6:e3:f6:52:22:05:fc:d7:5d:d8:d7:ef:12:4d ios.pub (RSA)
When I tried to connect to the device with SSH I received a message showing this key.
Anonymous
Apr 25th 2016
9 years ago