Port 0 DDOS
Following on the stories of amplification DDOS attacks using Chargen, and stories of "booters" via Brian Kreb's, I am watching with interest the increase in port 0 amplification DDOS attacks.
Typically these are relatively short duration, 15 to 30 minute, attacks aimed at a residential IP address and my speculation is that these are targeted at "booting" participants in RPG games. On the networks I have access to these are usually in the 300 Mbps to 2.0 Gbps range. The volume would most certainly be very debilitating for the target, and sometimes their neighbors, but for the most part doesn't cause overall problems for the network. The sources are very diverse.
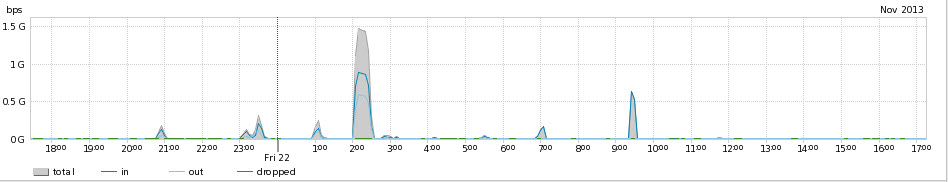
Unfortunately I do not have an ability to get packets of any of these attacks, but I am questioning whether this traffic is actually destined for port 0 or if it is actually fragmentation attacks that are being interpreted as source port 0 traffic.
Jim Macleod at lovemytool.com does an excellent job of describing what I am suspecting.
If anyone has packets available from one of these attacks, I would love to review them.
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)



Comments
I believe various techniques are used such as seeing the target's Skype handle and acquiring their IP through methods that I am sure you are aware of. I believe some game matches are even hosted on individual computers rather than servers, and the IP can be acquired through connection monitoring, etc.
For reference, I just ran a search and this is from 2012:
http://www.teamliquid.net/forum/viewmessage.php?topic_id=365825
-meloncully
Anonymous
Nov 24th 2013
1 decade ago
166.78.24.147
162.243.40.151
173.45.238.125
50.56.176.218
Wireshark - source port 0 and destination port 0...
Very frustrating.
Anonymous
Dec 5th 2013
1 decade ago