Piktochart - Phishing with Infographics
[This is a guest diary submitted by JB Bowers]
In line with our recent diaries featuring unique attack vectors for credential theft, such as phishing over LinkedIn Mail[1] and pretending to be an Outlook version update[2], we've recently learned of a phishing campaign targetting users of the Infographic service Piktochart.
During the COVID-19 pandemic, nearly every kind of company has moved to use more online collaboration tools. This means that many small businesses, universities, primary and secondary schools, and others that may not be well-trained in online safety will be especially vulnerable to this type of attack, especially if they are using a relatively new tool, like Piktochart.
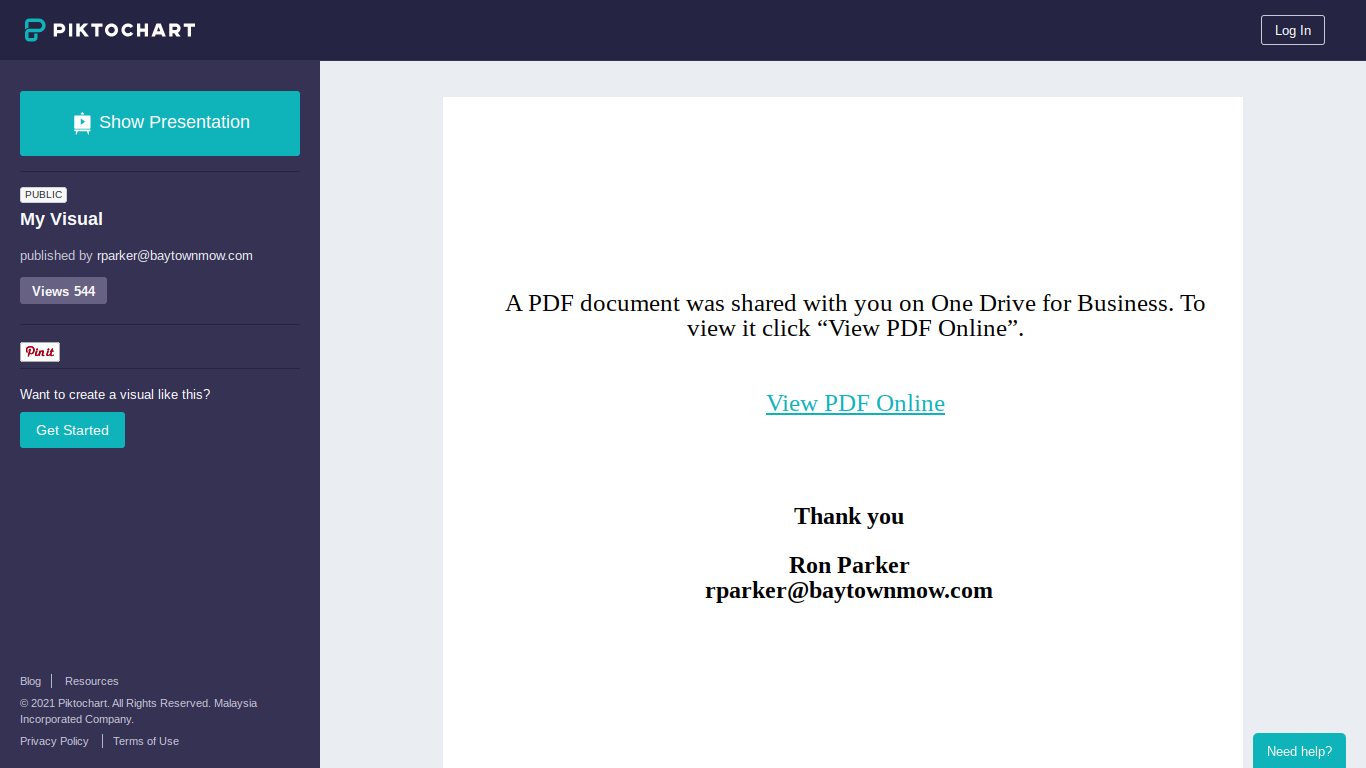
I had not used Piktochart before, but this week, security researcher @pageinsec[3] shared with me an infographic that asks the user to click on a link, in order to read a shared pdf document [4].
Piktochart has about 2,000 registered users, and about 24 million Piktocharts Created and is used by companies such as Forbes, TechCrunch, and others, according to their website. With a legitimate business purpose that is endorsed by some large companies, it is likely this is an effective way for the attackers to evade DNS filtering or other simple defenses against credential-stealing attacks.
Piktochart has a feature that makes it even better for phishing: Their registered "Pro users" can download an actual .pdf file, with the malicious link intact, or as well render the file into several different sizes of .png images, as indicated in the IOCs near the bottom of this page, which might be useful to hunt for similar activity.
An unsuspecting victim would receive an e-mail or social media post including the malicious Piktochart, from someone they knew, whose account had already been compromised. If they click the link, a 2nd stage credential stealer follows, which is a pretty decent-looking (but fake) Microsoft login page hosted at the domain obggladdenlightfoundation(.)org. This base domain currently has "0 out of 87" vendors reporting it as malicious on Virus Total, and is made out to be a non-profit in Lagos, Nigeria. This specific example had a different site registration than most of the other, identical sites I've researched, so it is possible this site was the result of a takeover of a legitimate business' WordPress website, or a redirection of the site's DNS.
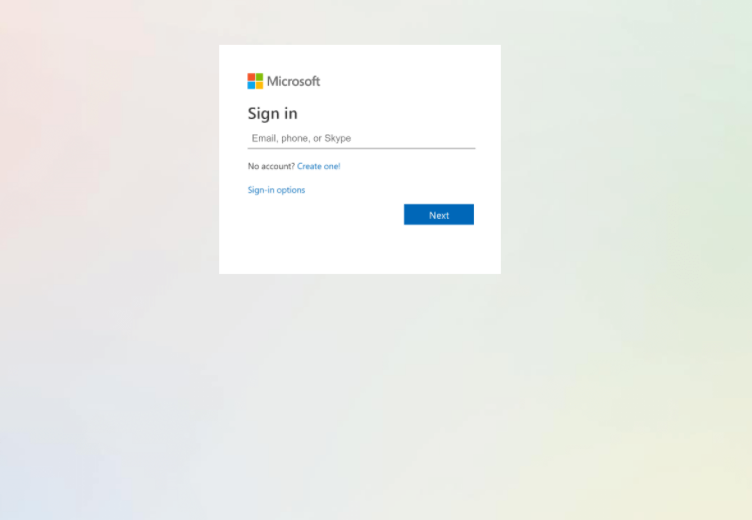
Despite the technical simplicity, this is a dangerous campaign since it is after Microsoft 0365 credentials, and evidence points to the same IP being used for a large variety of credential theft sites. There are quite a few domains on the same IP[5], for example:
pwan-heritage(.)com/pol/OfficeV4/*
secure-official-spotify.pwanplus(.)com
www.dhl-delivery-failure-resolve.naijamail.com - This one includes a nice-looking DHL form [6]
Indicators of compromise - IOCs
URLS/Domains
create.piktochart.com/output/52653368-my-visual
piktochart.com (if not needed for businses)
2nd stage/stealer
obggladdenlightfoundation.org/dfsmith/ofc3
obggladdenlightfoundation.org/dfsmith/ofc3/
obggladdenlightfoundation.org/dfsmith/ofc3/r.php?signin=d41d8cd98f00b204e9800998ecf8427e&auth=39bea2eedcf78c893b4d0898d91bba501390ced533b8de1d796bcc5973da76e5b1cf6668
obggladdenlightfoundation.org/dfsmith/ofc3/s/?signin=d41d8cd98f00b204e9800998ecf8427e&auth=39bea2eedcf78c893b4d0898d91bba501390ced533b8de1d796bcc5973da76e5b1cf666
IP
173.231.197.145 [7]
Hostname: ded5495.inmotionhosting.com
Domain registrar: 007NAMES INC.
*Used in most of the domains
Microssoft cred stealer image - hashes(sha2)
7, 10, and 3kb versions of the same image
a90370dc587b73cd2dbe33504794e83c83dc9f365cd9cd94511593046db5ae09
bc2afe6e49541902541497a6823e1aa0f8e8683e203d4da6bc75590bddebeb702bed6013d59910f6714448cafeda98708886d48978b6b991627526964379efc0
DOM (cred-stealer page)
"
<form id="1MDAwMDMxMjAyMS0wMy0wMjE2MTQ2NTgwMDQ4NTgxMTAx"> <input type="hidden" value="[removed]"><input type="hidden" value="[removed"> </form>
"
Post request
"form id="f2" method="post" action="#" style="margin-bottom: 0px;"> <input required="" type="email" placeholder="Email, phone, or Skype" name="e"
style="outline:none; background-color:transparent;border:0px solid;height:30px;width:300px;font-weight:lighter;font-size:15px;margin-left:5px;padding-bottom:0px;padding-top:0px;"> <img
src="data:image/png;base64"...
Cookies
obggladdenlightfoundation.org/ 1969-12-31
23:59:59 Name: PHPSESSID
obggladdenlightfoundation.org/dfsmith/ofc3/s 1969-12-31
23:59:59 Name: ip11
JB Bowers
@cherokeejb_
References:
[1] - https://isc.sans.edu/forums/diary/The+new+LinkedInSecureMessage/27110
[2] - https://isc.sans.edu/forums/diary/Pretending+to+be+an+Outlook+Version+Update/27144/
[3] - https://apageinsec.wordpress.com/
[4] - https://create.piktochart.com/output/52653368-my-visual
[5] - https://urlscan.io/result/e02ea839-9671-4d31-a039-effd54877c0b/related/
[6] - https://urlscan.io/screenshots/205111b7-b981-48e9-9359-df55f278163b.png
[7] - https://isc.sans.edu/ipinfo.html?ip=173.231.197.145

Comments