Peeking into .msg files
Readers often submit malware samples, and sometimes the complete email with attachment. For example exported from Outlook, as a .msg file.
Did you know that .msg files use the Compound File Binary Format (what I like to call OLE files), and can be analysed with oledump?
Reader Carlos Almeida submitted a .msg file with malicious .rar attachment.
I'm not that familiar with .msg file intricacies, but by looking at the stream names and sizes, I can often find what I'm looing for:
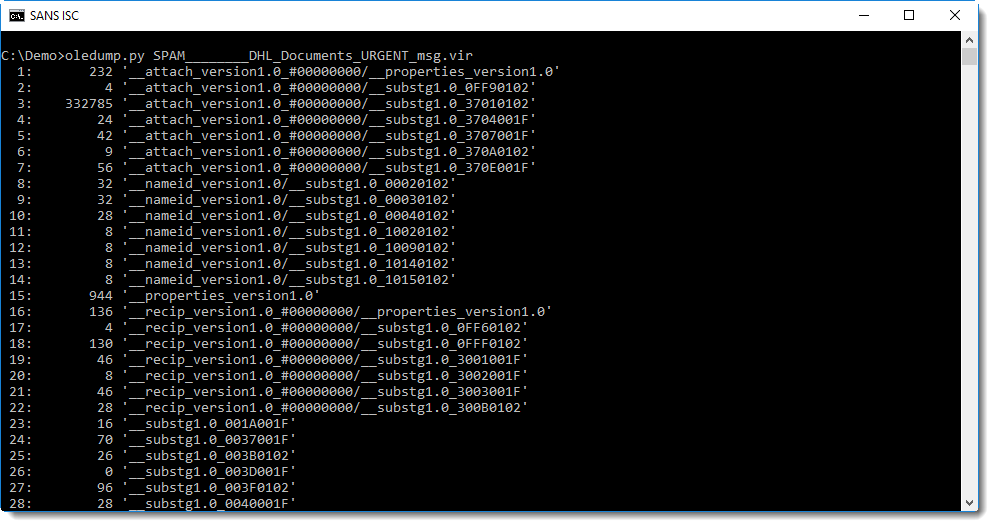
Stream 53 seems to contain the message:
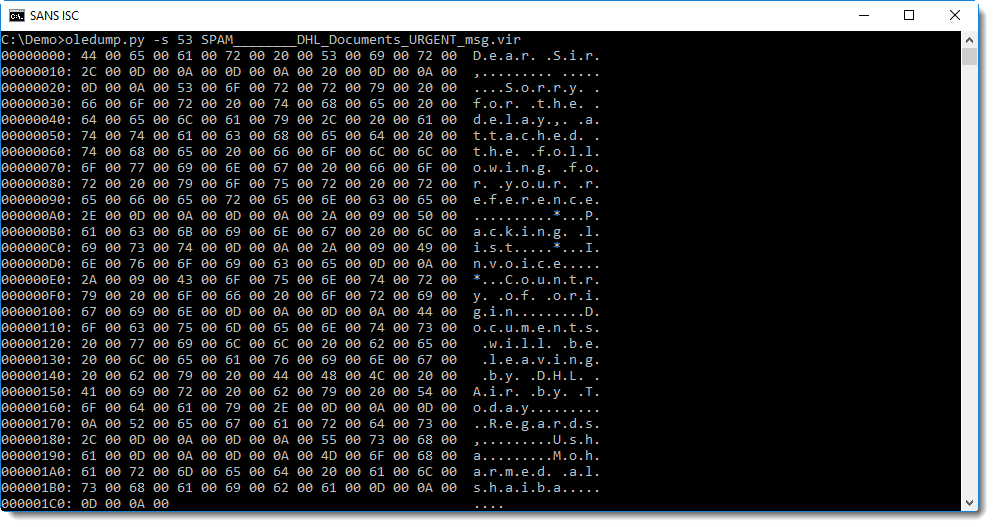
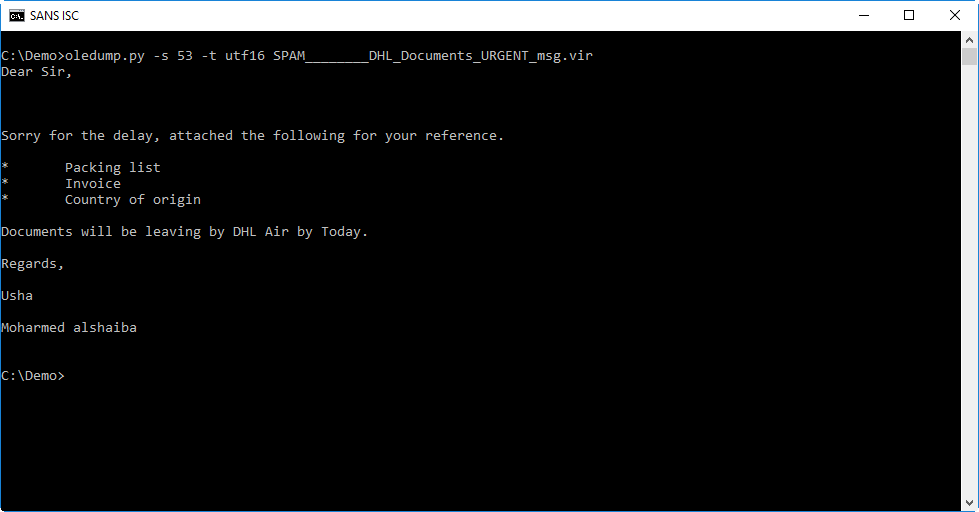
From this hex-ascii dump, you can probably guess that the message is stored in UNICODE format. We can use option -t (translate) of oledump to decode it as UTF-16:
Stream 43 contains the headers. I don't want to disclose private information like our reader's email address, so I grepped for some headers that I can disclose:
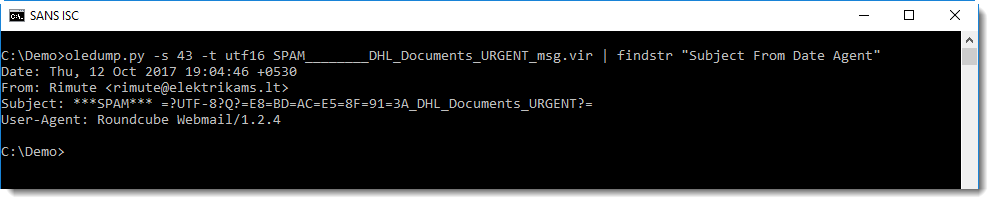
The Subject header is encoded according to RFC1342 because the subject contains non-ASCII characters. It decodes to this:

These are chinese characters that seem to mean the same as FW: (forwarding).
Stream 3 contains the attachment:
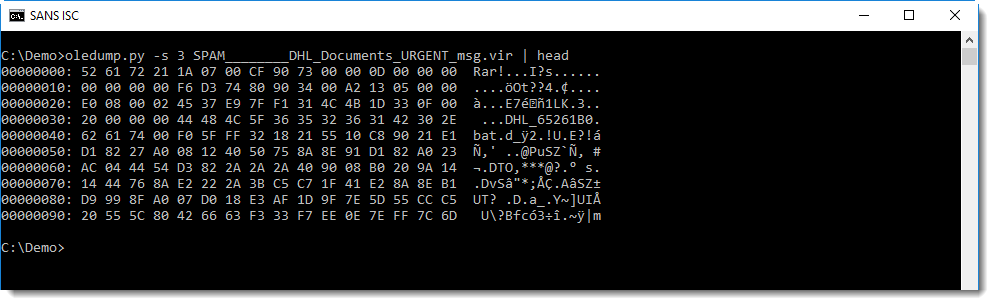
You can see it's a RAR file.
I use 7zip to look into it, and it should be possible to do this without writing the file to disk, by just piping the data into 7zip (options -si and -so can help with piping). But unfortunately, I got errors trying this and resigned to saving it to disk:
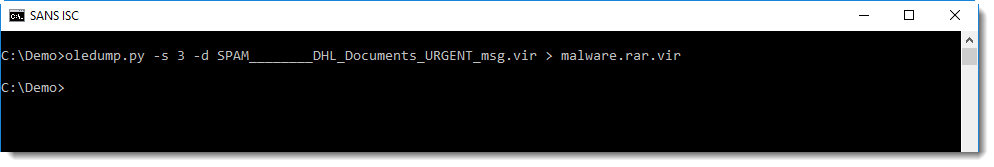
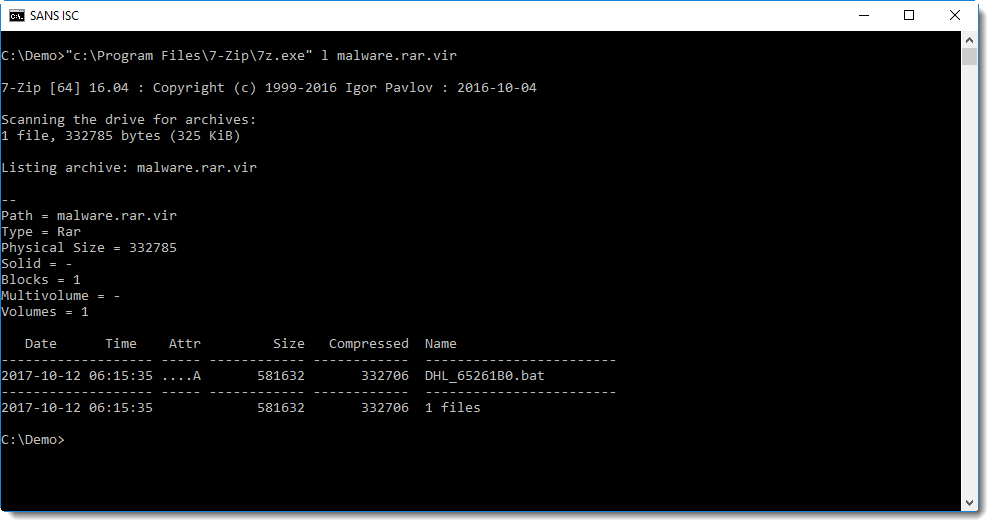
It contains an unusually large .bat file:
It's actually a PE file:
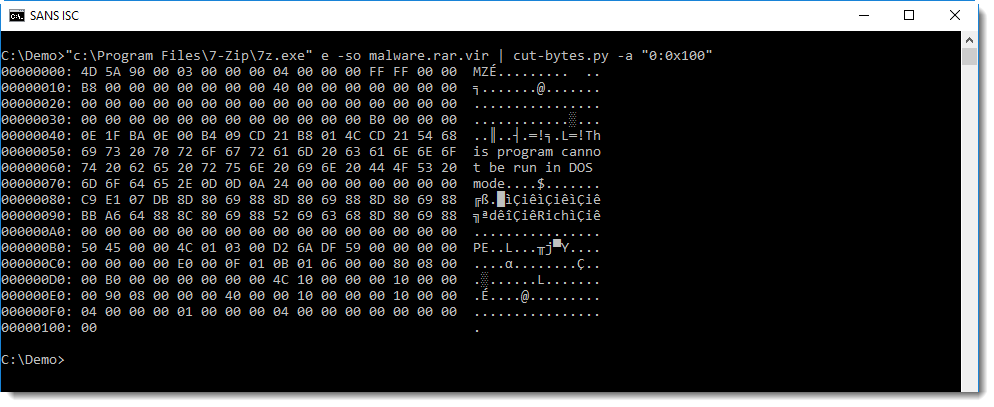
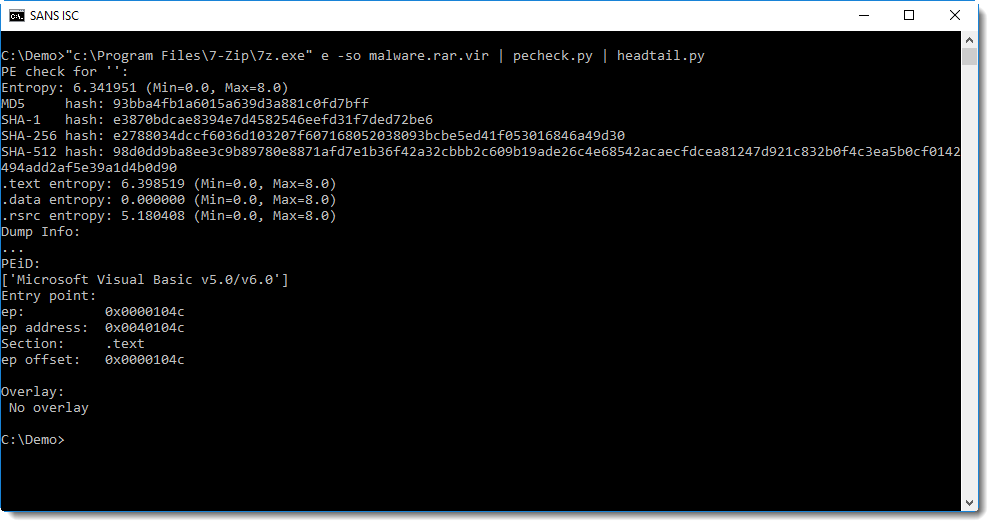
This looks to be a VB6 executable (from the PEiD signature), I should dig up my VB6 decompiler and try to take a closer look.
Of course, it's malware.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com



Comments
Anonymous
Oct 15th 2017
7 years ago
Anonymous
Oct 15th 2017
7 years ago
and also your great SANS team, thank you
learn a lot
Carlos Almeida
Anonymous
Oct 16th 2017
7 years ago
The prefix indicates what the part type is
'3701': 'Attachment data',
'3703': 'Attachment extension',
'3704': 'Attachment short filename',
'3707': 'Attachment long filename',
'370E': 'Attachment mime tag',
'3712': 'Attachment ID (uncertain)'
Anonymous
Oct 16th 2017
7 years ago
Anonymous
Dec 20th 2017
7 years ago