Oversharing
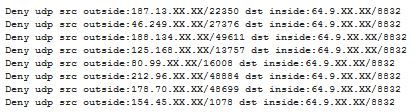
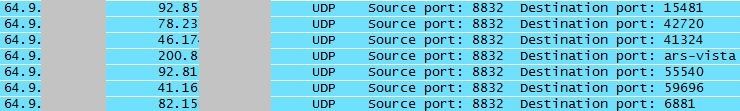
When ISC reader Michael contacted us about "odd UDP traffic from all over" that he was suddenly seeing in his firewall log, we at first assumed that his Internet connection had "inherited" a dynamic IP address that had before been used by a rampant file sharing user, and that Michael was now seeing the "after glow".
We still asked for a PCAP (tcpdump) file though, and when we looked at what Michael sent back, we saw to our surprise ...
... that Michael's network was responding to the traffic. Hmm. Oops!
Closer inquiry then revealed that they had recently updated the firmware on their QNAP TS-659 NAS (network storage) server .. and this new version came with the ability to act as a media and streaming server. It isn't quite clear if the corresponding functionality had been "on" by default, or had been turned on by accident. But once turned off, the "odd UDP traffic" stopped right away.
Lesson learned - after an upgrade, check if things are still how you expect them to be. While most vendors have thankfully learned to keep new "features" turned off by default, you can't quite rely on it. For home use, investing in a small network tap or hub, and every now and then checking the traffic leaving your house is (a) a good security precaution and (b) helps to keep your Wireshark Packet-Fu skills current :)
And while we are on the topic of NAS and storage servers: A CERT vulnerability note released today states that some versions of Synology DiskStation contain a hard-coded password which can be used by remote attackers to establish a VPN into the DiskStation. I wish vendors - prominently including Cisco - would get their bleeping act together, and, after years of "security advisories" on the subject, eventually stop shipping products with hard coded credentials/backdoors! Details on the Synology mess here: http://www.kb.cert.org/vuls/id/534284



Comments
Here's a stupidly pedestrian example. Ever noticed that Bluetooth turns itself back on after every iPhone iOS update? Maybe that's not an enterprise-wide mission-critical issue, but I just don't understand why an update would change ANY user settings unless actual functionality was deprecated or changed.
G
Anonymous
Feb 28th 2014
1 decade ago
Anonymous
Feb 28th 2014
1 decade ago
Anonymous
Feb 28th 2014
1 decade ago