Out of Band Phishing. Using SMS messages to Evade Network Detection
Many companies have extensive security tools to monitor employee computers. But these precautions often fail for "out of band" access that uses cellular networks instead of Ethernet/WiFi networks. Our reader Isabella sent us this phishing email that they received:
Dear User,
This is to let you know that our web-mail server will be upgraded and maint=
ained soon.
If you don't want your e-mail account to be terminated during the upgrade,
Send "[redacted]" to 6-0-5-5-5-5-1-1-1-1. [altered]
You will receive instructions on how to upgrade your account via text messa=
ge.
If you do not comply with the above, your email access will be disabled.
Please accept our apologies for any inconvenience this may cause.
Regards
System Administrator
[redacted]
Note that the phone number is somewhat obfuscated, likely to protect it from tools inspecting email or network traffic. The user is asked to send an SMS. While SMSs may travel across WiFi networks in some cases, they are usually not accessible to network protection devices. In this case, the user received a link next:
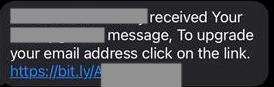
The user is no likely going to click on the link using a mobile device, lessening the risk of discovery to the attacker. The target URL is no longer available, but Isabella reported that the link leads to a phishing page.
The attack was somewhat targeted in that the attacker used consistent branding for the code to be sent. It included the short-form of the organizations name which is why I redacted it above. Even the target domain used (which is no longer reachable to me), "http://micro365upgrade.com" was plausible for an Office 365 upgrade.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Las Vegas | Sep 22nd - Sep 27th 2025 |



Comments
Anonymous
Aug 24th 2021
3 years ago