More Exotic Excel Files Dropping AgentTesla
Excel is an excellent target for attackers. The Microsoft Office suite is installed on millions of computers, and people trust these files. If we have the classic xls, xls, xlsm file extensions, Excel supports many others! Just check your local registry:
Attackers like to use more “exotic” extensions to increase chances of evading simple and stupid rules at mail gateways. This time, the extension used was “.xlam”. I spotted several emails (probably from the same campaign) that delivered .xlam files to potential victims.
An XLAM file is a macro-enabled add-in used to add new features to Excel. The icon looks like Excel and should make the user confident to open it:

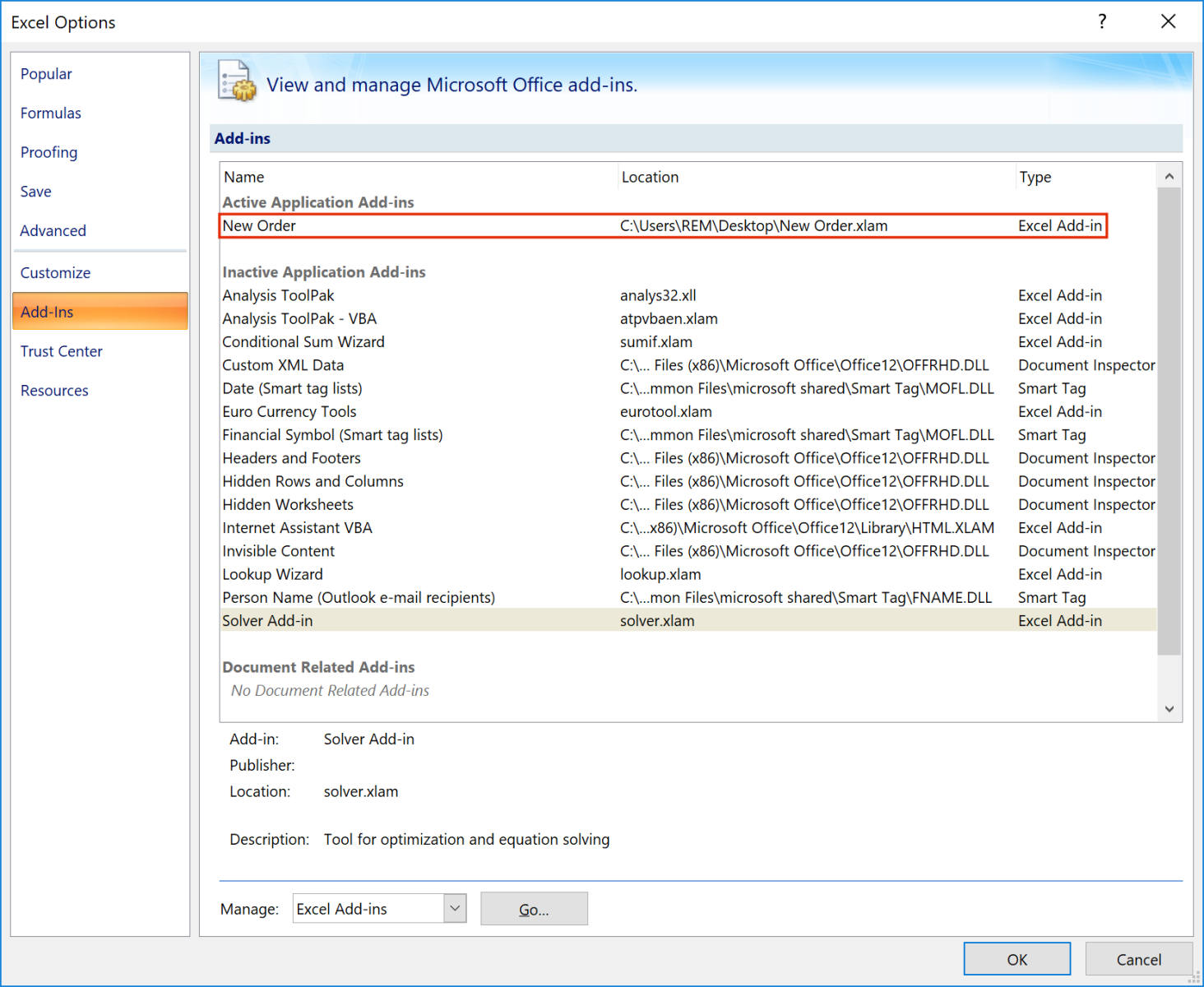
Once loaded, you can see the add-on in Excel:
The add-on has the following SHA256: 72006dfd34f5b043e6763b16ff8399382e69ad356e8c6b9e71ec908674dab55c and a VT score of 30/56[1].
If you read “macro-enabled”, it’s not classic VBA macro, but this add-on contains an exploit for the good old Equation Editor (CVE-:2017-1182). If successfully exploited, the add-on will download a malicious VBS script and execute it:
C:\Windows\System32\WScript.exe" "C:\Users\user01\AppData\Roaming\oldgyyudi.vbs"
The URL from where the script is downloaded is http://80[.]76[.]51[.]248/afk.vbs
The script has the following SHA256: d93c28f9ceeac993f652f976e12eba842716d571370bcdb2dd912965aa6274fb (unknown on VT at this time) and is pretty well obfuscated. Here is an example of a function that reverses a string:
Escola = drRgvLwPScMUPVCgWhShgMSmjRqaWCUXzUCPCcDqXCNWRLWXvdWLpQmrjqdvCWZzRcUiWUrawWCsywwLLVsoBPeWDkNtPrWMEMEPZlGYBLWZMhMmMMZVWgeCwhgXq
Escola = eKRiX(eKRiX(eKRiX(Escola)))
[...]
Function eKRiX(iNcPxLbcdBdHlsOAcdpbduplKWscQhRhriWZpuxAGtjteLbDKxgbQjArhOoIuccrMKcNHRiJWiuBxLOUbKyUuLcboDKKbzuhLJCTwrTtcOspGRMunLiIoOogKuiencc)
qArcGzUDayYkTOOcTWLZccaLRrsnUkODDkkHOcpTDMaUNzsXrXTnHUTYLCqrOfyGNJkRLUQnMLOQNWUnKOGkMWUTNJYZLiUZfNzHyccKMKwINzNLYNINsrKBWzsDi =
Chr(83)&Chr(116)&Chr(114)&Chr(82)&Chr(101)&Chr(118)&Chr(101)&Chr(114)&Chr(115)&Chr(101)
nnUTLnLIujuBNUwLIOWkWRfBJwUWcrGrIawtWSLIShigAikDLGDwKWLmrGcvRaoIUUPcgOaklvOcDQGiLyaiKLoLeDUGkpPfQkKaimahWwOfgGUcuLaveqcDWObduPr =
"eKRiX = "
nnUTLnLIujuBNUwLIOWkWRfBJwUWcrGrIawtWSLIShigAikDLGDwKWLmrGcvRaoIUUPcgOaklvOcDQGiLyaiKLoLeDUGkpPfQkKaimahWwOfgGUcuLaveqcDWObduPr = nnUTLnLIujuBNUwLIOWkWRfBJwUWcrGrIawtWSLIShigAikDLGDwKWLmrGcvRaoIUUPcgOaklvOcDQGiLyaiKLoLeDUGkpPfQkKaimahWwOfgGUcuLaveqcDWObduPr +
qArcGzUDayYkTOOcTWLZccaLRrsnUkODDkkHOcpTDMaUNzsXrXTnHUTYLCqrOfyGNJkRLUQnMLOQNWUnKOGkMWUTNJYZLiUZfNzHyccKMKwINzNLYNINsrKBWzsDi
nnUTLnLIujuBNUwLIOWkWRfBJwUWcrGrIawtWSLIShigAikDLGDwKWLmrGcvRaoIUUPcgOaklvOcDQGiLyaiKLoLeDUGkpPfQkKaimahWwOfgGUcuLaveqcDWObduPr = nnUTLnLIujuBNUwLIOWkWRfBJwUWcrGrIawtWSLIShigAikDLGDwKWLmrGcvRaoIUUPcgOaklvOcDQGiLyaiKLoLeDUGkpPfQkKaimahWwOfgGUcuLaveqcDWObduPr + "(iNcPxLbcdBdHlsOAcdpbduplKWscQhRhriWZpuxAGtjteLbDKxgbQjArhOoIuccrMKcNHRiJWiuBxLOUbKyUuLcboDKKbzuhLJCTwrTtcOspGRMunLiIoOogKuiencc)"
execute(nnUTLnLIujuBNUwLIOWkWRfBJwUWcrGrIawtWSLIShigAikDLGDwKWLmrGcvRaoIUUPcgOaklvOcDQGiLyaiKLoLeDUGkpPfQkKaimahWwOfgGUcuLaveqcDWObduPr)
End Function
The variable Escola will contain the string "Startup".
The next payload is downloaded from http://80[.]76[.]515.]248/afrique.txt, which returns a Base64-encoded string (reversed) that is decoded as a PE file (SHA256: e45d91008eb19ecc3c9e6aab13339bc327c2c61b97215b0d2cc98c23b0db057a). This is an AgenTesla with the following config:
{
"rule": "AgentTeslaV4",
"family": "agenttesla",
"credentials": [
{
"host": "mail.worlorderbillions.top",
"port": 587,
"email_to": "absach@worlorderbillions[.]top",
"password": “xxxxxxxxxxxxxxxxx”,
"protocol": "smtp",
"username": "absach@worlorderbillions[.]top"
}
]
}
[1] https://www.virustotal.com/gui/file/72006dfd34f5b043e6763b16ff8399382e69ad356e8c6b9e71ec908674dab55c
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key

Comments