Malware Analysis with elastic-agent and Microsoft Sandbox
Microsoft describes the "Windows Sandbox supports simple configuration files, which provide a minimal set of customization parameters for Sandbox. [...] Windows Sandbox configuration files are formatted as XML and are associated with Sandbox via the .wsb file extension."[6]
Since both, the latest version elastic-agent (7.11+) support antivirus detection, I followed the instructions listed here [1] to configure an agent to test its detection capabilities. For my workstation, I used VMware with a fully patched Windows 10 and saved the current configuration with a snapshot. I wanted to combine both of these features; the elastic-agent and the Microsoft sandbox feature [4][5][6] to analyze my malware sample. Since the Microsoft sandbox doesn't retain anything after it is shutdown, I figure this would be a good alternative vs. restoring my previous VMware snapshot every time I tested a suspicious filename.
One minor inconvenient, if I want to use the agent, I need to add it every time to Elasticsearch to use it. If the elastic-agent isn't installed, Microsoft Defender is enabled. Here is a list of tools to either install or consider installing in the sandbox when it starts:
- Elastic-agent with malware policy (in VMware client and Sandbox client)
- MS SysMon
- MS TCPView
- Consider adding: PowerShell Script Block Logging, example here
- Wireshark to capture traffic from host
- Other browsers: Chrome & Firefox
- PeStudio
- Python
- Internet Services Simulation Suite: INetSim
- Didier Stevens suite of tools
- Proxy setup on VMware client to monitor traffic
- Any other tools you might find useful during the analysis such as this package by @mentebinaria
When starting the sandbox, using a script configured for this purpose, it can automatically load the tools needed with a batch file (MalwareAnalysis.wsb). Here is my example:
<Configuration>
<vGPU>Enable</vGPU>
<AudioInput>Enable</AudioInput>
<VideoInput>Enable</VideoInput>
<ProtectedClient>Enable</ProtectedClient>
<MappedFolders>
<MappedFolder>
<HostFolder>C:\Sandbox</HostFolder>
<ReadOnly>true</ReadOnly>
</MappedFolder>
</MappedFolders>
<LogonCommand>
<Command>C:\users\WDAGUtilityAccount\Desktop\Sandbox\SBConfig.bat</Command>
</LogonCommand>
</Configuration>
Because everything is deleted when you shutdown the sandbox (including the browser, it must be reloaded with the current version every time), I needed a way to automatically start/add/load/update what I needed to perform some basic analysis. I use a batch file I preconfigured with everything I needed to accomplish this task. Here is what I have (C:\Sandbox\SBConfig.bat):
REM Copy elastic-agent to C:\Program Files
C:\Windows\System32\xcopy.exe /i /s C:\Users\WDAGUtilityAccount\Desktop\Sandbox\elastic-agent "C:\Program Files\elastic-agent"
REM Install Sysmon64, vcredist_x86
C:\Users\WDAGUtilityAccount\Desktop\Sandbox\Sysmon64.exe -i -accepteula
C:\Users\WDAGUtilityAccount\Desktop\Sandbox\vcredist_x86.exe /q
REM Add Elastic certificate authority to Sandbox
C:\Windows\System32\certutil.exe -addstore root C:\Users\WDAGUtilityAccount\Desktop\Sandbox\ca.crt
C:\Windows\System32\certutil.exe -addstore root C:\Users\WDAGUtilityAccount\Desktop\Sandbox\stargate.crt
REM Install new Microsoft Edge
start /wait C:\Users\WDAGUtilityAccount\Desktop\Sandbox\MicrosoftEdgeEnterpriseX64.msi /quiet /norestart
REM Install Python
C:\Users\WDAGUtilityAccount\Desktop\Sandbox\python-3.9.2-amd64.exe /quiet InstallAllUsers=1 PrependPath=1 Include_test=0
REM Execute PowerShell scripts
Powershell.exe -executionpolicy remotesigned -File C:\Users\WDAGUtilityAccount\Desktop\Sandbox\ChangeExecutionPolicy.ps1
Powershell.exe -executionpolicy remotesigned -File C:\Users\WDAGUtilityAccount\Desktop\Sandbox\ScriptBlockLogging.ps1
REM Install Wireshark
REM Install npcap manually. Silent only supported with OEM
C:\Users\WDAGUtilityAccount\Desktop\Sandbox\Wireshark-win64-3.4.4.exe /S /D /desktopicon=yes
C:\Users\WDAGUtilityAccount\Desktop\Sandbox\npcap-1.20.exe
The file npcap is last because I'm using the free edition vs. the OEM which will ask to finish the installation after it starts the installer. Before you can enable ScriptBlockLogging in the Sandbox, I need to enable the PowerShell ExecutionPolicy to allow RemoteSigned. This is the command in my script to make that change (ChangeExecutionPolicy.ps1):
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Force
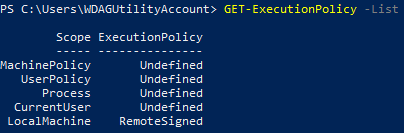
To verify the change was applied, as PowerShell admin, execute the following command:
Get-ExecutionPolicy -List
Producing the following result:
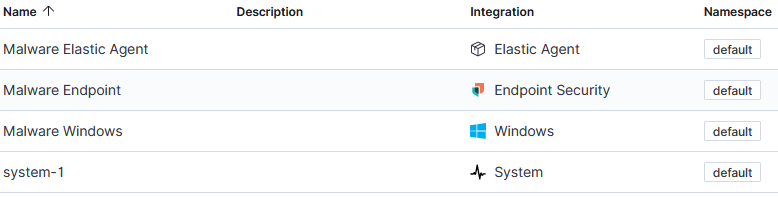
Following the example listed here in this Elastic blog, it is time to create a policy, add the elastic-agent to Elasticsearch (pre-copied with the batch file SBConfig.bat) to run the sample file and monitor its activity. This is the four application part of the policy I configured for my agent:
After launching the script MalwareAnalysis.wsb to start the Sandbox, load, copy and install all the applications from the batch file, it is time to add the elastic-agent to the server, I am ready to launch the suspected malware file for analysis. Last month, my honeypot was uploaded a crypto miner file photo.scr and I'm going to use this file to submit the elastic-agent for analysis.
→ To view the results in Kibana, navigate Security -> Overview -> Detection alert trend
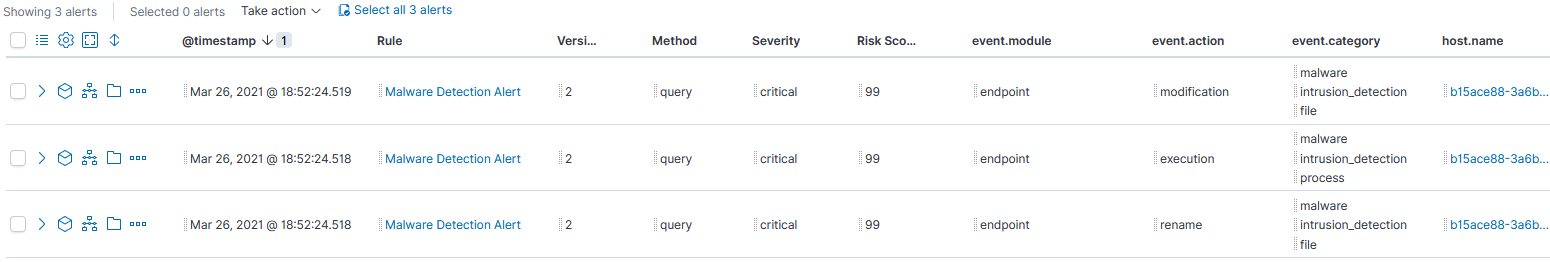
I look for activity that would indicate an alert triggered by malware and filter for the value, then View alerts to examine the flow of the activity. I can then select Analyze the content as to what this photo.scr file accessed or installed on the client. The agent captured 3 alerts:
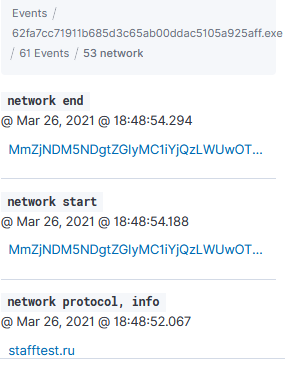
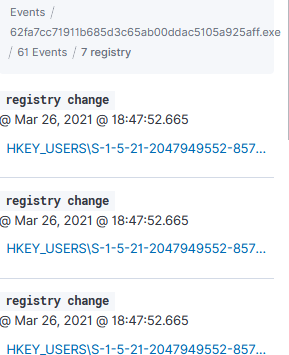
Next is to expand one of those alerts and analyze the activity, the elastic-agent identified: 1 library, 53 networks and 7 registry:
Network Activty
Registry Activity
Each one of the can be expanded to drill further into what happened on the host.
Indicator of Compromise
SHA256
807126cbae47c03c99590d081b82d5761e0b9c57a92736fc8516cf41bc564a7d Photo.scr
[2021-02-08 07:06:36] [1693] [ftp_21_tcp 29914] [103.232.236.239:64149] info: Stored 1578496 bytes of data
Domains
stafftest[.]ru
iqtesti[.]ru
jobtests[.]ru
prtests[.]ru
qptest[.]ru
pstests[.]ru
testpsy[.]ru
profetest[.]ru
hrtests[.]ru
This is one of many tasks Windows Sandbox could be used such as accessing suspicious sites, running untrusted software and scripts starting with Windows network or vGPU disable, without the fear of impacting your normal Windows installation. These various tasks can be accomplished by creating separate .wsb Sanbox script.
[1] https://www.elastic.co/blog/how-to-build-a-malware-analysis-sandbox-with-elastic-security
[2] https://www.elastic.co/endpoint-security/
[3] https://www.elastic.co/guide/en/security/current/install-endpoint.html
[4] https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-sandbox/windows-sandbox-overview
[5] https://techcommunity.microsoft.com/t5/windows-kernel-internals/windows-sandbox/ba-p/301849
[6] https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-sandbox/windows-sandbox-configure-using-wsb-file
[7] https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
[8] https://docs.microsoft.com/en-us/sysinternals/downloads/tcpview
[9] https://github.com/mentebinaria/retoolkit?s=09
[10] https://www.virustotal.com/gui/file/807126cbae47c03c99590d081b82d5761e0b9c57a92736fc8516cf41bc564a7d/detection
[11] https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_logging_windows?view=powershell-7.1
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu




Comments