Malspam pushing Trickbot malware on Friday 2018-05-11
Introduction
I've consistently noted malicious spam (malspam) distributing Trickbot malware 2 or 3 days every week. My Online Security frequently documents this malspam, and it has occurred on at least five occasions this month from 2018-05-01 through 2018-05-11.
Last week, this Trickbot malspam tried some new tricks. On Wednesday 2018-05-09, Xavier Mertens posted a diary about this campaign using a fake notice for a Adobe PDF web-plugin update to push Trickbot. But by Friday 2018-05-11, this malspam was back to using an RTF attachment that exploits CVE-2017-11882. This is the Microsoft Equation Editor vulnerability. Malspam from this campaign has been routinely using these type of RTF attachments since early April 2018.
Today's diary reviews an RTF attachment using an exploit for CVE-2017-11882 to push Trickbot on Friday, 2018-05-11.
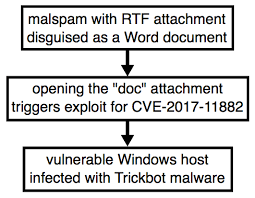
Shown above: Chain of events for a Trickbot infection from Friday.
The email
Email headers from this malspam campaign follow consistent patterns. These emails have a DKIM signature, and the envelope is spoofed as being from noreply-[recipient's email address]@[whatever domain is being used& that day]. An example of the email headers from Friday 2018-05-11 follow. I've replaced the recipient's email address with bob123@whereever.com.
(envelope-from <noreply-bob123=whereever.com@hmrc-email-gov.uk>)
[removed]; Fri, 11 May 2018 11:23:02 -0000
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=key; d=hmrc-email-gov.uk;
h=Mime-Version:Date:To:Subject:From:Content-Type:Message-ID;
bh=pXEjZNFF+nNw2PPQpsYXr5oWSmA=;
b=FL6DqNISXS60W7USA4vCzy4z7Ya/Ikw5uR3y9lbsJ+Mgi4oawDyvFH55IH4lbRrPQNyhnmgvrAwd
t5YpMPB3JCl9Mke0Izf8ltDQLBSAt2vV3qP8oC/WKI4fzuFEEB9diL4IHDDbYYUb32N4SjPaKro8
J6bRiNjZ9CVUa1vgFqE=
Received: by hmrc-email-gov.uk id huluj5octe0l for <bob123@whereever.com>; Fri, 11 May 2018 07:06:36 -0400 (envelope-from <noreply-bob123=whereever.com@hmrc-email-gov.uk>)
Mime-Version: 1.0
Date: Fri, 11 May 2018 07:06:36 -0400
To: bob123@whereever.com
Subject: Accelerated payment notice
From: "HM Revenue & Customs" <noreply@hmrc-email-gov.uk>
Content-Type: multipart/mixed;
boundary=60306fda09ad4cde1f75f5c97bc15a42
Message-ID: <0.0.2.0.1D3E918211D293A.2143242@hmrc-email-gov.uk>
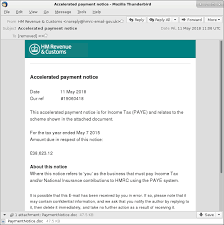
Shown above: Screenshot from an email example.
The RTF attachment
Opening the RTF attachment triggers an exploit for CVE-2017-11882. Vulnerable Windows hosts would then be infected with Trickbot malware. This vulnerability was patched by Microsoft last year on 2017-11-14. People running Windows 10 should already have this patch automatically applied. Additionally, previous versions of Windows like Windows 7 should have been patched as part of the monthly security update process.
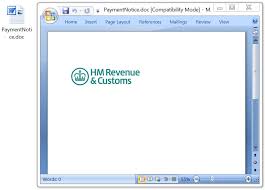
Shown above: The RTF attachment opened on a vulnerable Windows host.
Infection traffic
Network traffic from an infected Windows host follows similar patterns as recent Trickbot infections I documented earlier this month on 2018-05-01 and 2018-05-03. We first see an HTTP GET request for the Trickbot malware binary followed by an IP address check. This is followed by SSL/TLS traffic over ports 447 and/or 449. Other HTTP GET requests for table.png and toler.png deliver follow-up malware.
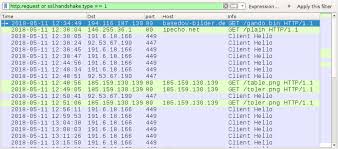
Shown above: Traffic from an infection filtered in Wireshark.
Post-infection forensics
The infected Windows host acted the same as previous Trickbot infections. Unlike many malware families that use the Windows registry to stay persistent, Trickbot infections are kept persistent through a scheduled task. Trickbot is a modular malware, and it contains various components under the directory tree where the Trickbot binary is stored. These components are encoded or otherwise encrypted when saved to disk. On a 64-bit Windows host, these file names end with Dll64.
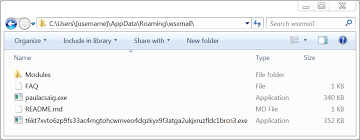
Shown above: Directory where Trickbot was made persistent as paulacsaig.exe.
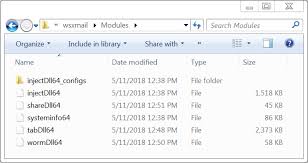
Shown above: Components noted in this Trickbot infection.
Indicators
The following are indicators seen from the Trickbot infection on Friday, 2018-05-11.
Date and time the infection traffic began: Friday 2018-05-11 at 12:34 UTC.
IP addresses, domains and URLs from the infection traffic:
- 194.116.187.130 port 80 - basedow-bilder.de - GET /gando.bin
- port 80 - ipecho.net - GET /plain
- 191.6.18.166 port 449 - SSL/TLS traffic caused by Trickbot
- 92.53.67.190 port 447 - SSL/TLS traffic caused by Trickbot
- 185.159.130.139 port 80 - 185.159.130.139 - GET /table.png
- 185.159.130.139 port 80 - 185.159.130.139 - GET /toler.png
Attachment from the malspam:
SHA256 hash: 64a73552356e540436bf362e68118615f3bea4e3bdb987e2bbd5b51570aa1f6f
- File size: 48,657 bytes
- File name: PaymentNotice.doc
- File description: RTF attachment disguised as Microsoft Word document
Malware retrieved from an infected Windows host:
SHA256 hash: 609cc34749da7ce6e8dbb3de9b7d0be03eca4cea63a4f3b1c383a3d483d0ecd6
- File size: 348,160 bytes
- Location: C:\Users\[username]\AppData\Roaming\wsxmail\
- File name: paulacsaig.exe
- File description: Trickbot malware binary
SHA256 hash: 8bf06a4c2ef57383efdc8fe9b9860c8ede70c63f158b1f58ea9f1fb564710f50
- File size: 360,448 bytes
- Location: C:\Users\[username]\AppData\Roaming\wsxmail\
- File name: t6kt7xvto6zp9fs33ac4mgtohcwrnveo4dgzkyx9f3atga2ukjxruzfldc1brcn3.exe
- File description: Other malware related to the Trickbot infection
Final words
As always, properly-administered Windows hosts are not likely to get infected. As I mentioned earlier, the vulnerability used by this malspam attachment was patched in November 2017. Furthermore, system administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Pcap and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments