Malspam pushing Sigma ransomware
Introduction
Sigma ransomware was first reported in November 2017 by places like Malware Mayhem and Cofense (formerly PhishMe). Since then, write-ups on Sigma have occasionally appeared on blogs like My Online Security and Bleeping Computer. A list of notable reports follows:
- 2017-11-09 - Malware Mayhem: Threat Actors Go Gree Using Sigma
- 2017-11-10 - Cofense: Threat Actors Put a Greek Twist on Ransomware with Sigma
- 2017-12-01 - My Online Security: fake Visa notification with password protected word doc delivers malware
- 2017-12-20 - Cofense: Recent Sigma Ransomware Campaign Demonstrates Danger in the Simplest of Changes to Malware Delivery
- 2018-03-09 - My Online Security: Regarding a career! Fake resume malspam delivers Sigma Ransomware
- 2018-03-12 - Bleeping Computer: Sigma Ransomware Being Distributed Using Fake Craigslist Malspam
Sigma ransomware activity dropped in January and February of 2018, but during the past week or so, it's come back. I personally hadn't run across it, but I noticed Sigma ransomware from the same type of malspam campaign I reported in a diary last week.
Today's diary looks at the wave of malspam pushing Sigma ransomware on Tuesday 2018-03-13.
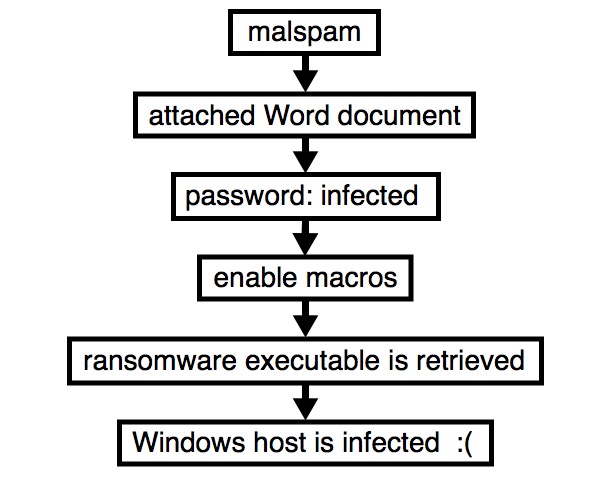
Shown above: Flow chart for an infection from this malspam.
The emails
Patterns in the email headers, message text, and attachment names for this week's example were nearly the same as last week's diary. This time, the attachment names ended with " resume.doc" with the sender's name before it. These characteristics indicate Tuesday's wave of malspam is from the same campaign, and it continues to push various families of ransomware. As before, each attachment had a different file hash
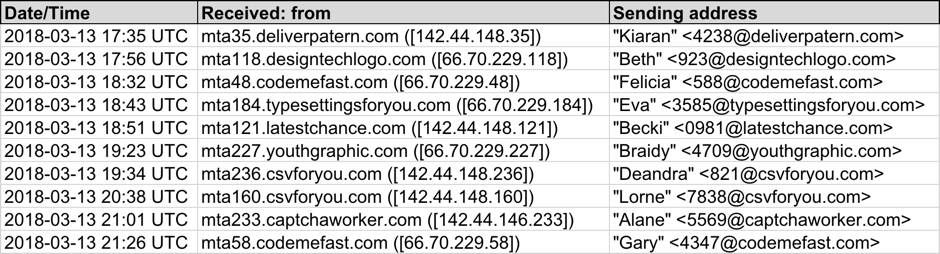
Shown above: Screenshot from the spreadsheet tracker with 10 email samples (part 1 of 2).
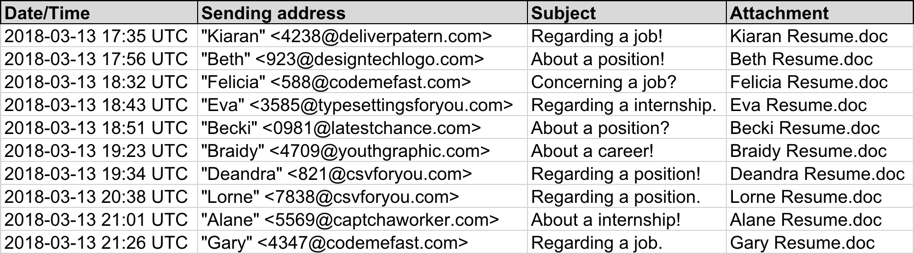
Shown above: Screenshot from the spreadsheet tracker with 10 email samples (part 2 of 2).
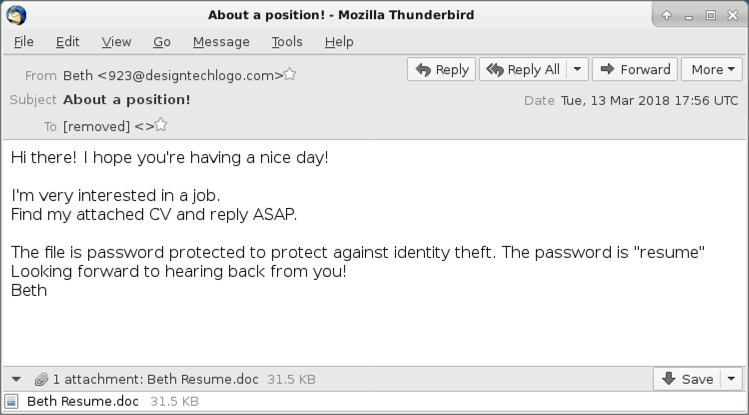
Shown above: Screenshot from one of the emails.
Attachments
As early as Friday of last week, this campaign started using password-protected Word documents. The password was always resume as stated in the emails' text. As usual for this type of malicious Word document, enabling macros will kick off the infection process. The enabled macro will cause the victim's host to retrieve a malware binary to infect a vulnerable Windows host.
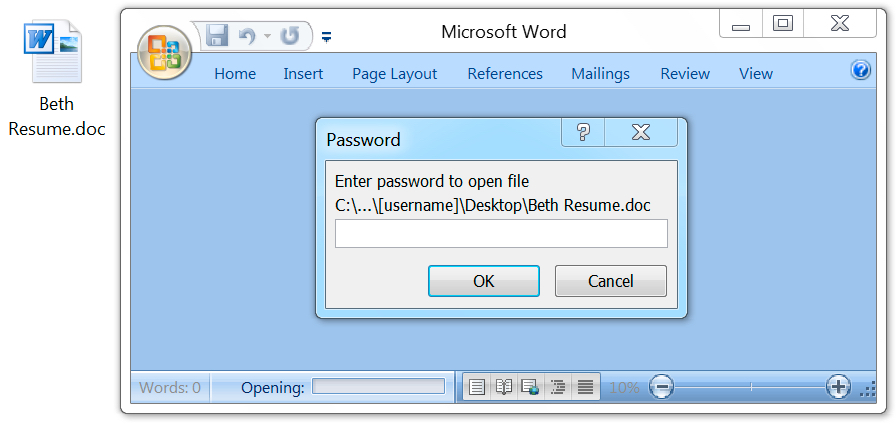
Shown above: Opening the attached Word document generates a prompt for the password.
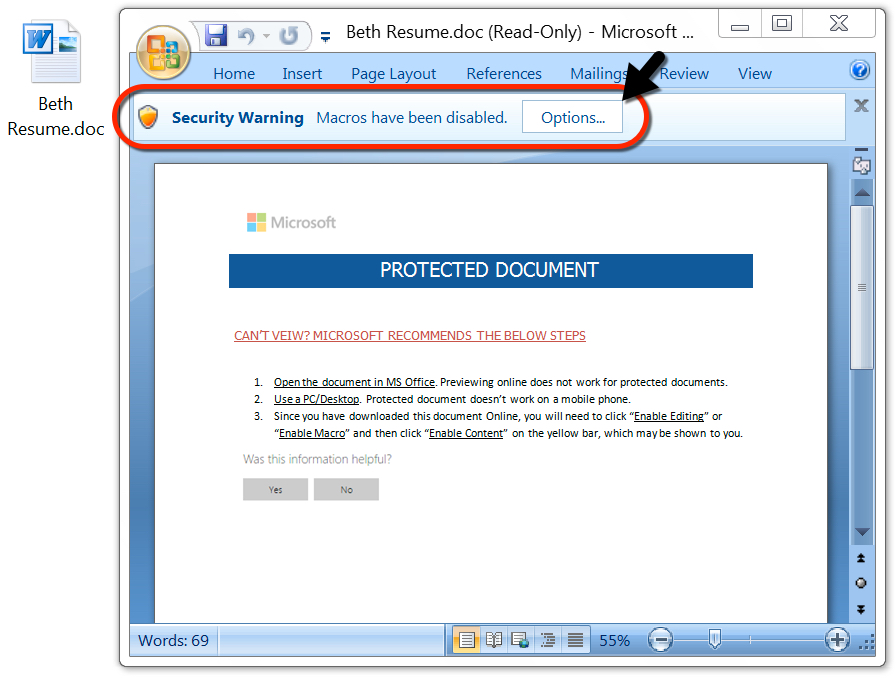
Shown above: After you enter the password, enable macros to start the infection process.
Enabling macros caused my vulnerable Windows host to download a 3.1 MB Windows executable file stored in the user's AppData\Roaming directory as a .tmp file. After the .tmp file appeared, my Windows host had a tor client installed, and another file of the exact same size with a different file hash appeared in the same directory. After they had done their work, both files were quickly deleted from that location.
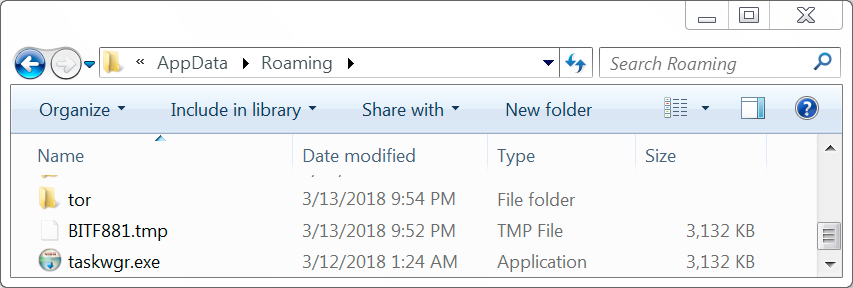
Shown above: Some items in the user's AppData\Roaming directory during the infection.
Infection traffic
After macros were enabled on the Word document, the initial malware binary was downloaded over HTTP using TCP port 80, similar to what we saw this past Friday. The initial download was followed by an IP address check and tor traffic.
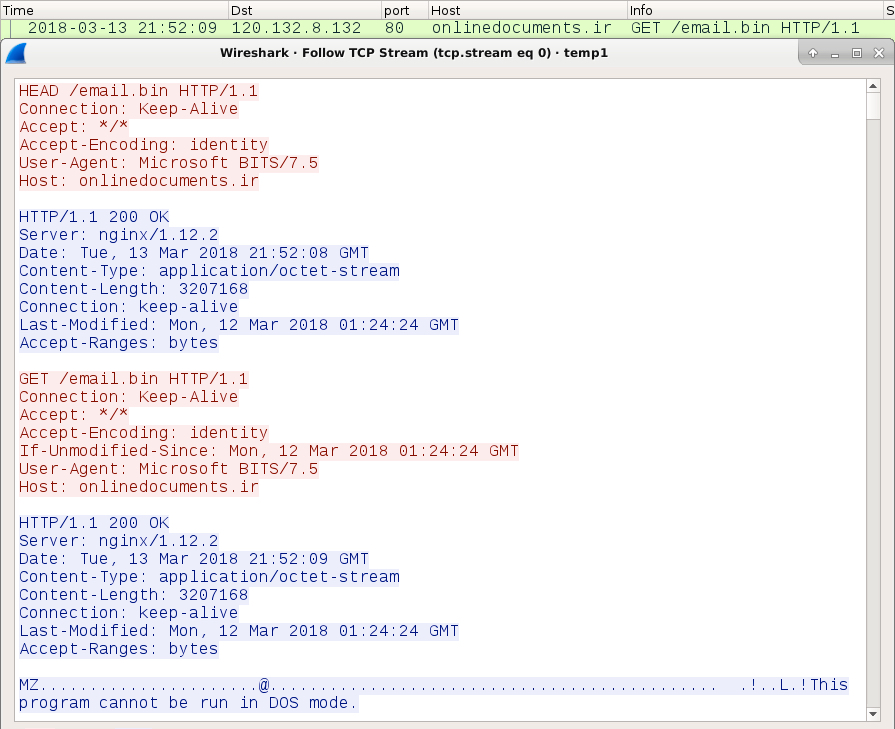
Shown above: My lab host downloading the initial malware binary.
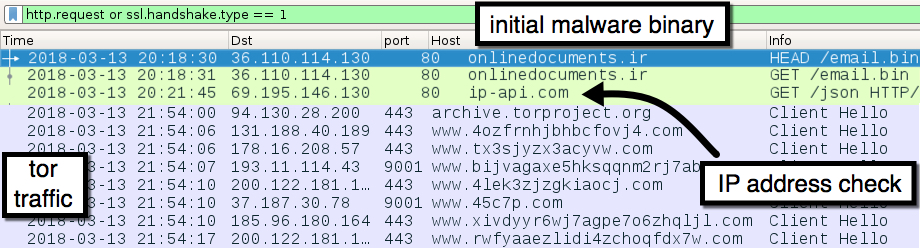
Shown above: The initial malware binary download followed by an IP check and tor traffic.
Forensics on an infected Windows host
The infected Windows host looked the same as previously reported examples of Sigma ransomware infections. Encrypted files did not have any file extensions added. The ransomware decryptor listed $400 USD as the ransom cost.
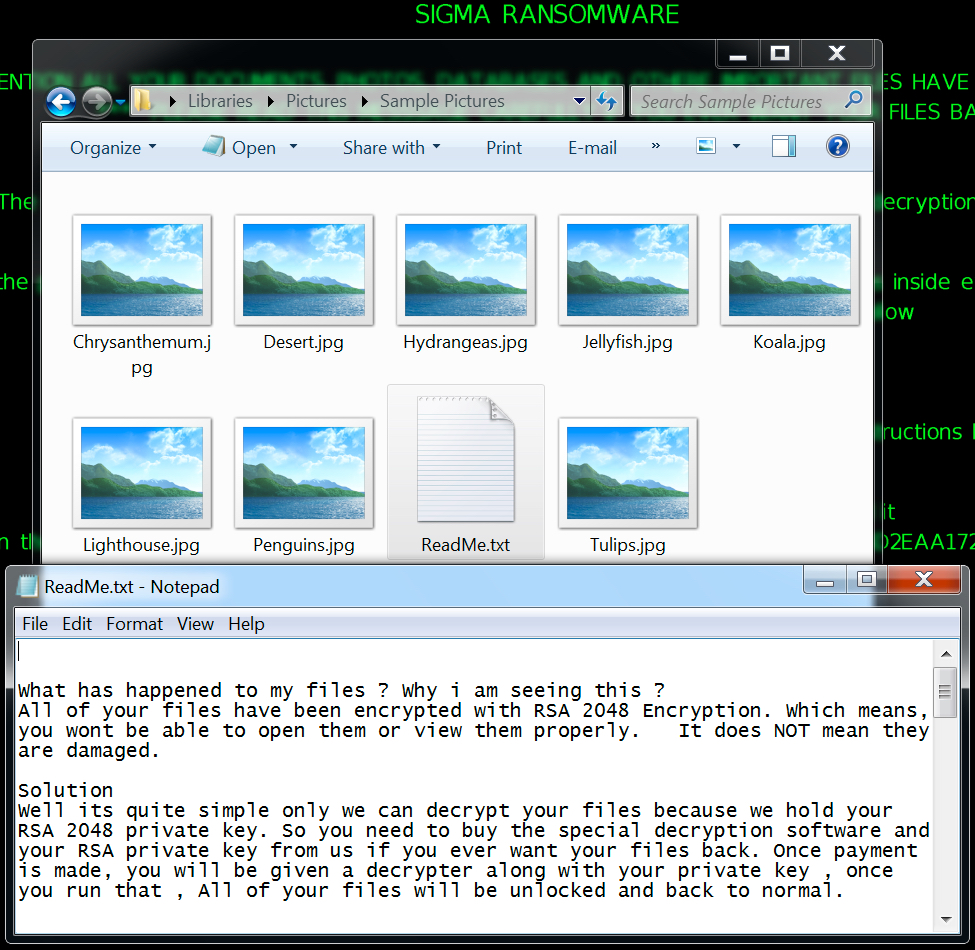
Shown above: Encrypted files and ransomware instructions on my infected lab host.
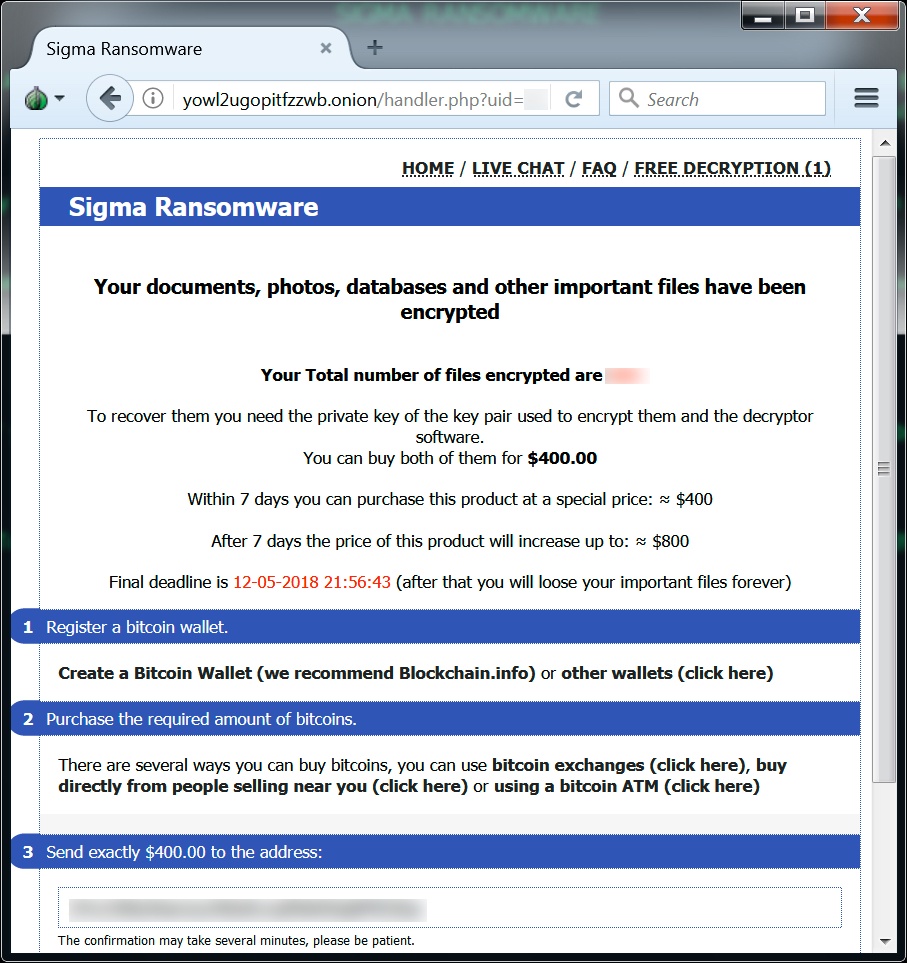
Shown above: Sigma ransomware decryptor from my infected lab host.
My infected lab host had additional files saved to the user's AppData\Roaming\Microsoft directory under a folder with the same name as the ransom ID used in the decryption instructions. An entry was added to the Windows registry to keep the infection persistent.
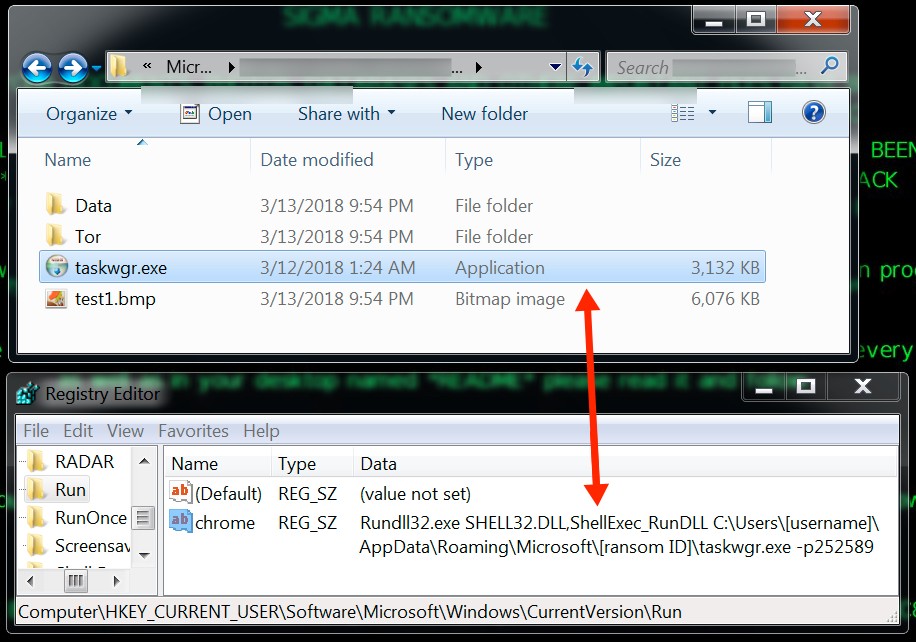
Shown above: More artifacts on my infected lab host.
Indicators
See below for a list of URLs, domains, and file hashes associated with this malspam.
SHA256 hashes for all attachments:
- f504eaea0e389859e38156255661e879def47fb3a667f032fa06b7dfb84276de - Alane Resume.doc
- e8e485a340a56774ee7c83bbc2be48e4185ed1aeefd17e45f75e445cdb561d8a - Becki Resume.doc
- cfba52ab5d939ba45d38179b743a98832f76eb091d37b6e6f2784e95b58eb566 - Beth Resume.doc
- 9793bef2fa003523961862973b946f09f51005b8ac15bfe3a080d7922fa37ee3 - Braidy Resume.doc
- a27328898c137448a745dc37855881dd22aa15d3502b2f2f578fe4d8d6a60b71 - Deandra Resume.doc
- 5d7a4340695f91d50658cc45a815c1f57998c3eb96eb313f5bfe11c135a1f2ad - Eva Resume.doc
- 5fc458775799db577eafc6fb52e8a42ca3938beed8877a76a5b71f02518a9795 - Felicia Resume.doc
- 58510fbc104d73199361b1bfb93cc44c86f64f422ba04df1b29dd96ba3402f8a - Gary Resume.doc
- c7b041e0f7b34a8ac2a2cdb5e55bf3cc72d9cbcd22a453a78338754914824a0f - Kiaran Resume.doc
- 3fa03e6adab2c240c9da3bf51509453e946be78cc75200e177aae969ce44f0fd - Lorne Resume.doc
The following are malware samples retrieved from my infected lab host:
- SHA256 hash: cd25aa002c73bfb68e0c952d8be90b5380a56972e9d3d90f0769a3a312e687cc
- File size: 3,207,168 bytes
- File location: C:\Users\[username]\AppData\Roaming\BITF881.tmp
- SHA256 hash: cbbb8b1b14b3df9d331ece7167ca9ab2b7da61839742a107142016d8d9c6f8e8
- File size: 3,207,168 bytes
- File location: C:\Users\[username]\AppData\Roaming\taskwgr.exe
File location: C:\Users\[username]\AppData\Roaming\Microsoft\[ransom ID]\taskwgr.exe
The following are URLs and domains associated with these infections:
- 120.132.8.132 port 80 - onlinedocuments.ir - GET /email.bin (ransomware binary)
- port 80 - ip-api.com - GET /json (IP check, not inherently malicious)
- various IP addresses - various TCP ports - tor traffic
- yowl2ugopitfzzwb.onion.link (HTTP link for Sigma decryptor)
- yowl2ugopitfzzwb.onion (tor address for Sigma decryptor)
Final words
Ransomware is still at low levels compared to last year, but I'm detecting a small uptick so far during March 2018. We'll see if this trend continues.
Even with the password-protected Word documents, this recent wave pushing Sigma ransomware is no more dangerous than previous ransomware-related malspam attacks. Criminals have already tried these tricks before.
As always, properly-administered Windows hosts are not likely to get infected. To infect their computers, users would have to bypass Protected View and ignore security warnings about activating macros on a Word document. System administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Pcap and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments