Malspam distributing Troldesh ransomware
Introduction
Earlier this week on Monday 2016-11-14, I found an example of malicious spam (malspam) distributing Troldesh ransomware. Troldesh (also called Filecoder or Shade) was initially reported in 2015 [1, 2]. That same year, I documented two examples of Troldesh ransomware delivered through exploit kit campaigns [3, 4]. By July 2016, Microsoft reported a new variant of Troldesh [5], and that seems to be the variant I found on Monday.
This diary takes a closer look at this week's Troldesh infection in my lab environment.
The malspam
The emails I saw from this wave of malspam were disguised as an account change notification from Sberbank of Russia. The emails all had a link in the message that appears to be for sberbank.ru but is actually a completely different URL.
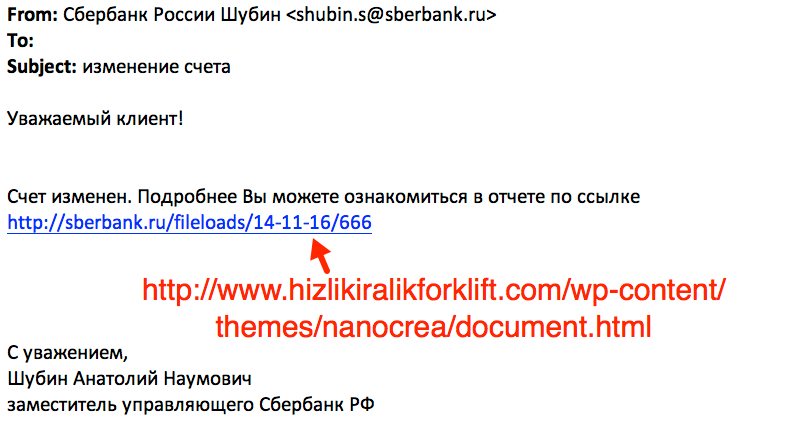
Shown above: Screenshot of the email highlighting the malicious link.
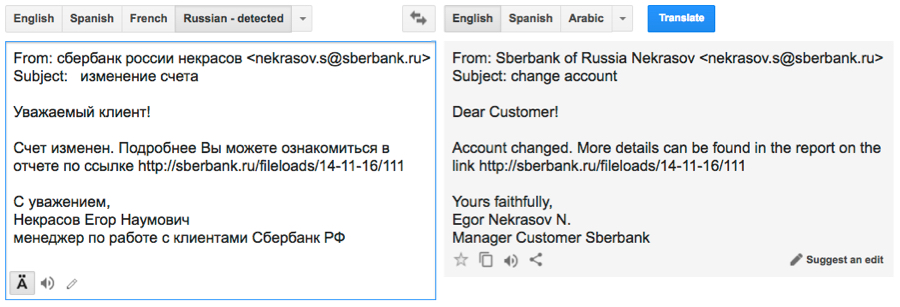
Shown above: Google translation of the Russian language text.
The malware
The URL from the email redirected to another URL leading to a file named document.zip. Within that zip archive is an executable file with an .scr file extension. The name of the file uses Russian language characters that did not display properly on my Windows host.
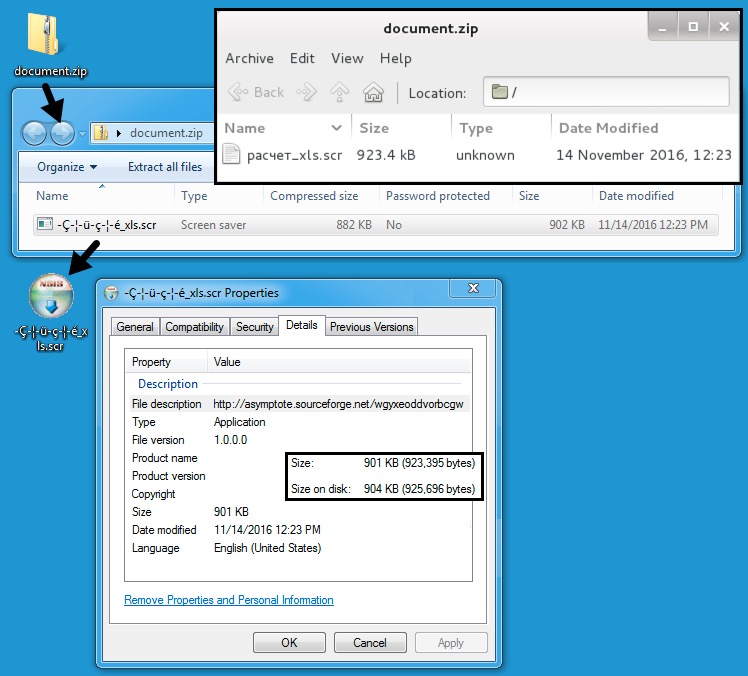
Shown above: The Downloaded zip archive and malware it contains.
Double-clicking the .scr file infected the Windows host, and the desktop quickly displayed indicators for a Troldesh ransomware infection.
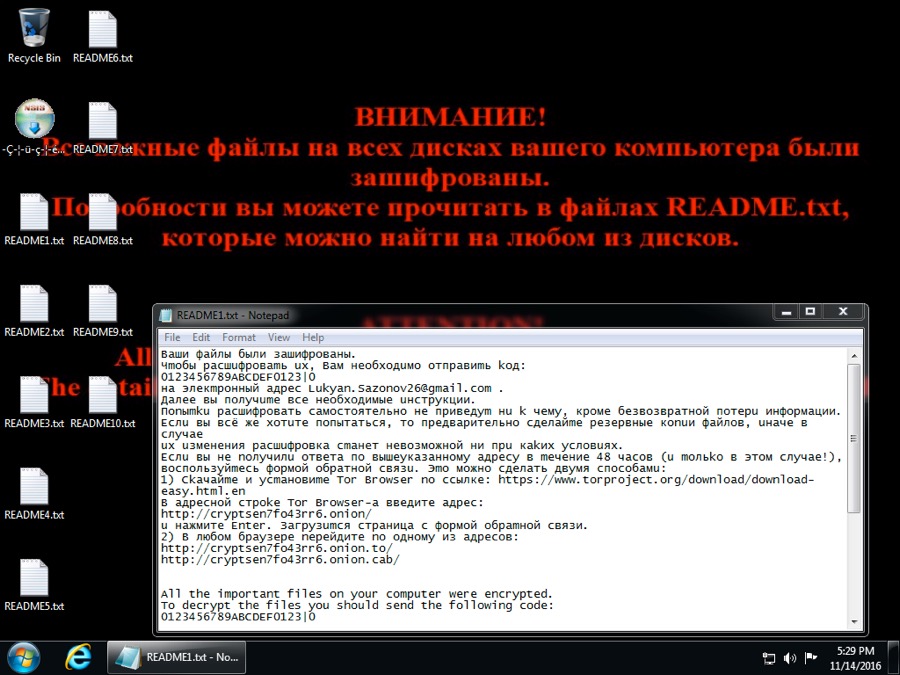
Shown above: Desktop of an infected Windows host.
The encrypted files all had .da_vinci_code as a file extension. This fits what Microsoft reported about the current variant of Troldesh ransomware [5].
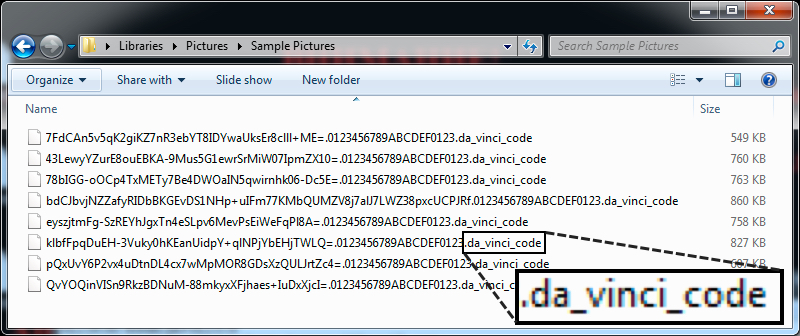
Shown above: File names and extensions for the encrypted files.
I tried the Tor link for the feedback form for additional info.
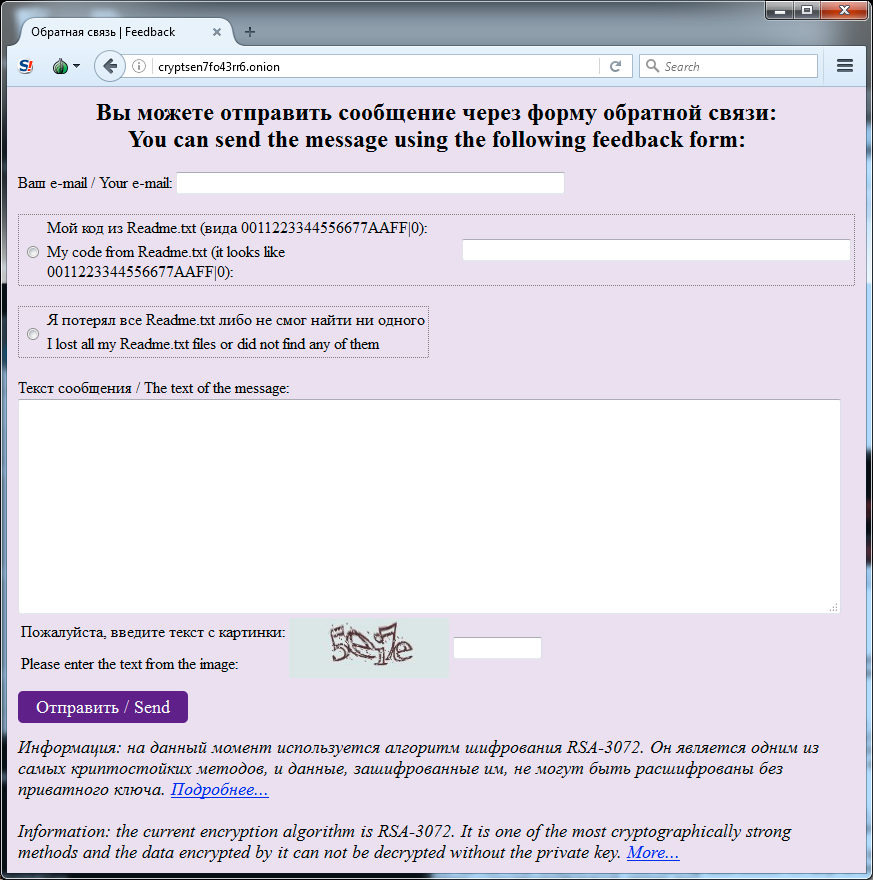
Shown above: Accessing the feedback form from the decryption instructions.
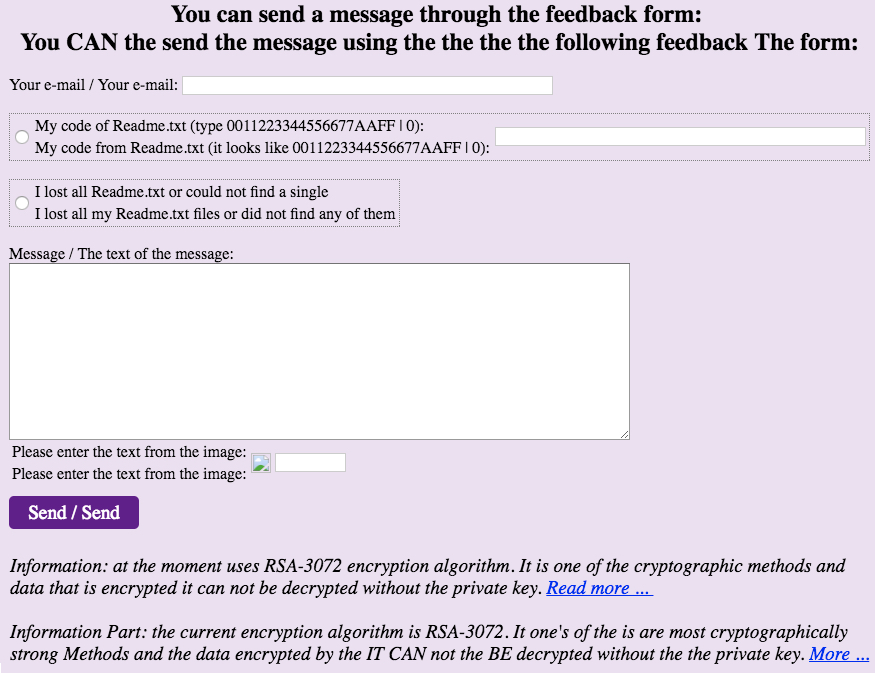
Shown above: Translation of the feedback form to English.
The traffic
The traffic is similar to what I saw from two Troldesh examples last year [3, 4]. This particular infection generated Tor traffic immediately after the ransomware was sent. The infected host also generated an IP address check in a manner consistent with Troldesh ransomware.
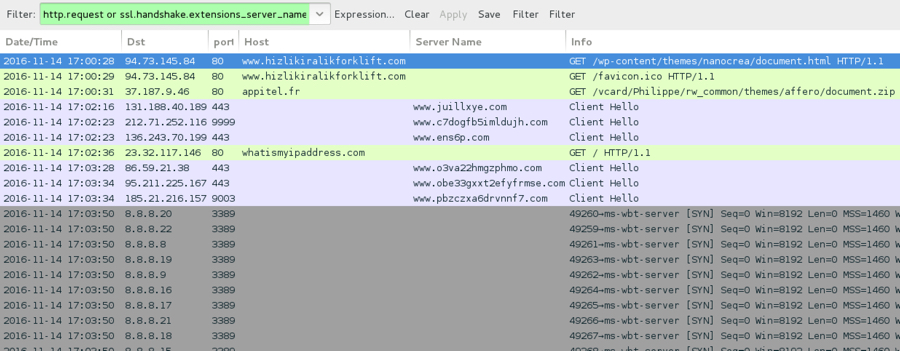
Shown above: Traffic from this infection filtered in Wireshark.
I checked the traffic against Snort 2.9.8.3 using the Snort subscription ruleset, and I also checked it on Security Onion running Suricata with the ET PRO ruleset.
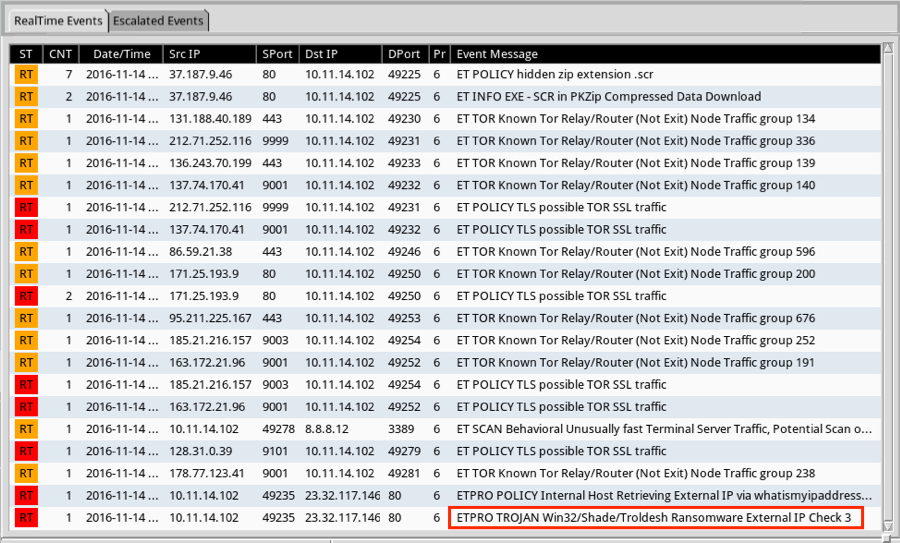
Shown above: Alerts from the ET and ET PRO rulesets.

Shown above: Some of the alerts seen from the Snort ruleset.
Indicators of Compromise (IOCs)
The following are IOCs associated with this infection.
Link from the email and redirect URL to download the zip archive:
- 94.73.145.84 port 80 - www.hizlikiralikforklift.com - GET /wp-content/themes/nanocrea/document.html
- 37.187.9.46 port 80 - appitel.fr - GET /vcard/Philippe/rw_common/themes/affero/document.zip
Downloaded zip archive - file name: document.zip
- SHA256 hash: 99d54e5c2e033d7703d9f449662bfcef1cb2ea0933dcfe0ca97e13e83cb9177b
Extracted malware - file name: расчет_xls.scr
- SHA256 hash: 749ed7d4fc97baa5e1068154fd642b23e9981f273fb18da2e02a8d925d7ca4d8
IP address check by the infected Windows host:
- whatismyipaddress.com - GET /
Tor traffic using various domains, IP addresses, and TCP ports.
Final words
A copy of the infection traffic, associated email, malware, and artifacts can be found here.
Ultimately, Troldesh is one of the many families of malware we see from malspam on a near-daily basis. It remains profitable enough that criminals will not stop distributing it. We expect to find more samples of Troldesh and similar ransomware in the coming months.
Fortunately, best security practices will help prevent infections like the example in today's diary. A good email filtering system, properly administered Windows hosts, and an educated workforce mean users are much less likely to be infected.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
[1] http://blog.checkpoint.com/2015/06/01/troldesh-new-ransomware-from-russia/
[2] https://blogs.technet.microsoft.com/mmpc/2015/08/09/emerging-ransomware-troldesh/
[3] http://www.malware-traffic-analysis.net/2015/04/09/index.html
[4] http://www.malware-traffic-analysis.net/2015/09/18/index.html
[5] https://blogs.technet.microsoft.com/mmpc/2016/07/13/troldesh-ransomware-influenced-by-the-da-vinci-code/



Comments
Anonymous
Nov 18th 2016
8 years ago