Keeping an Eye on Dangerous Python Modules
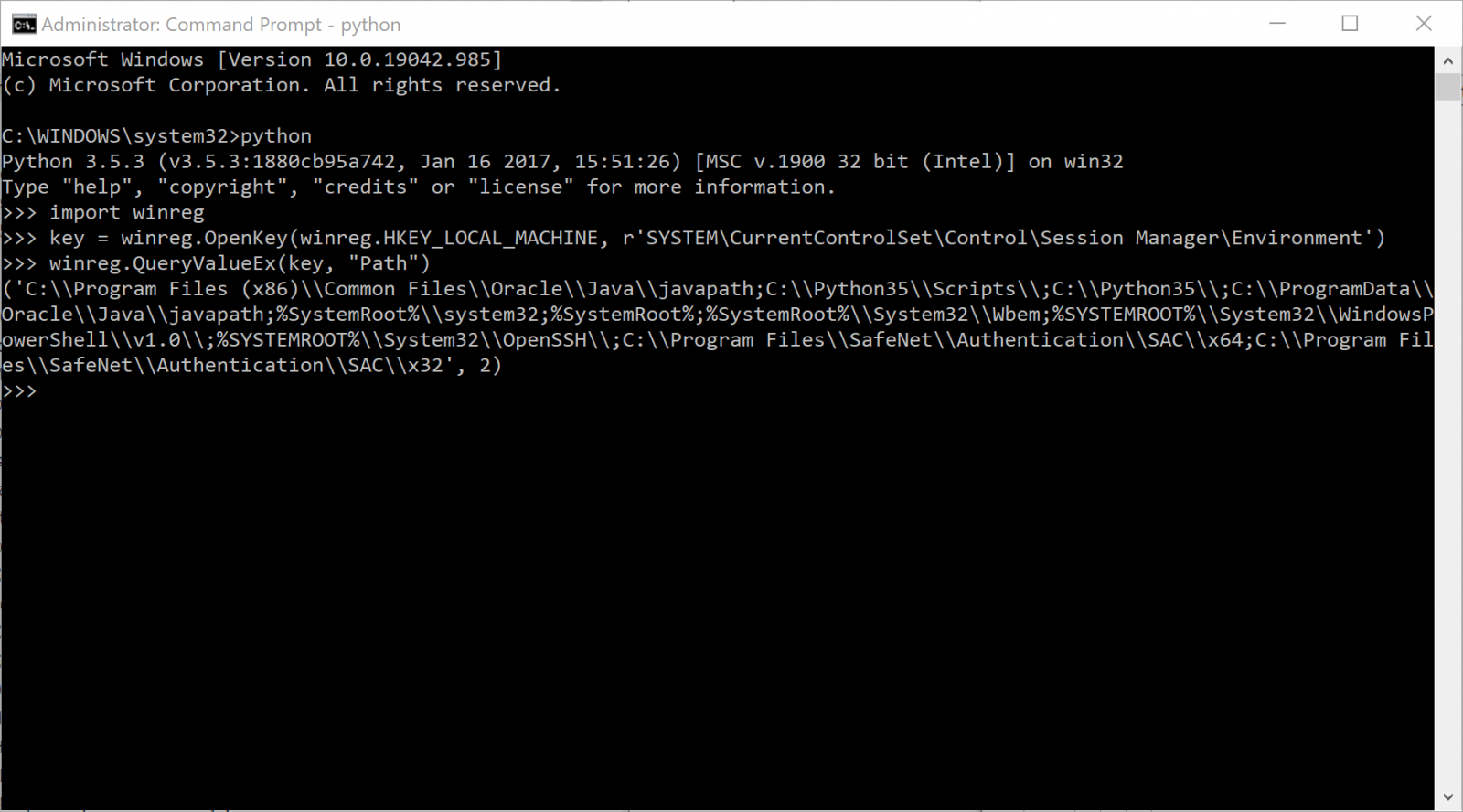
With Python getting more and more popular, especially on Microsoft Operating systems, it's common to find malicious Python scripts today. I already covered some of them in previous diaries[1][2]. I like this language because it is very powerful: You can automate boring tasks in a few lines. It can be used for offensive as well as defensive purposes, and... it has a lot of 3rd party "modules" or libraries that extend its capabilities. For example, if you would like to use Python for forensics purposes, you can easily access the registry and extract data:
This snippet of code starts with an import line. First, I need to load a specific module (in this case winreg) that will add to Python all the required code to manipulate the OS registry hives.
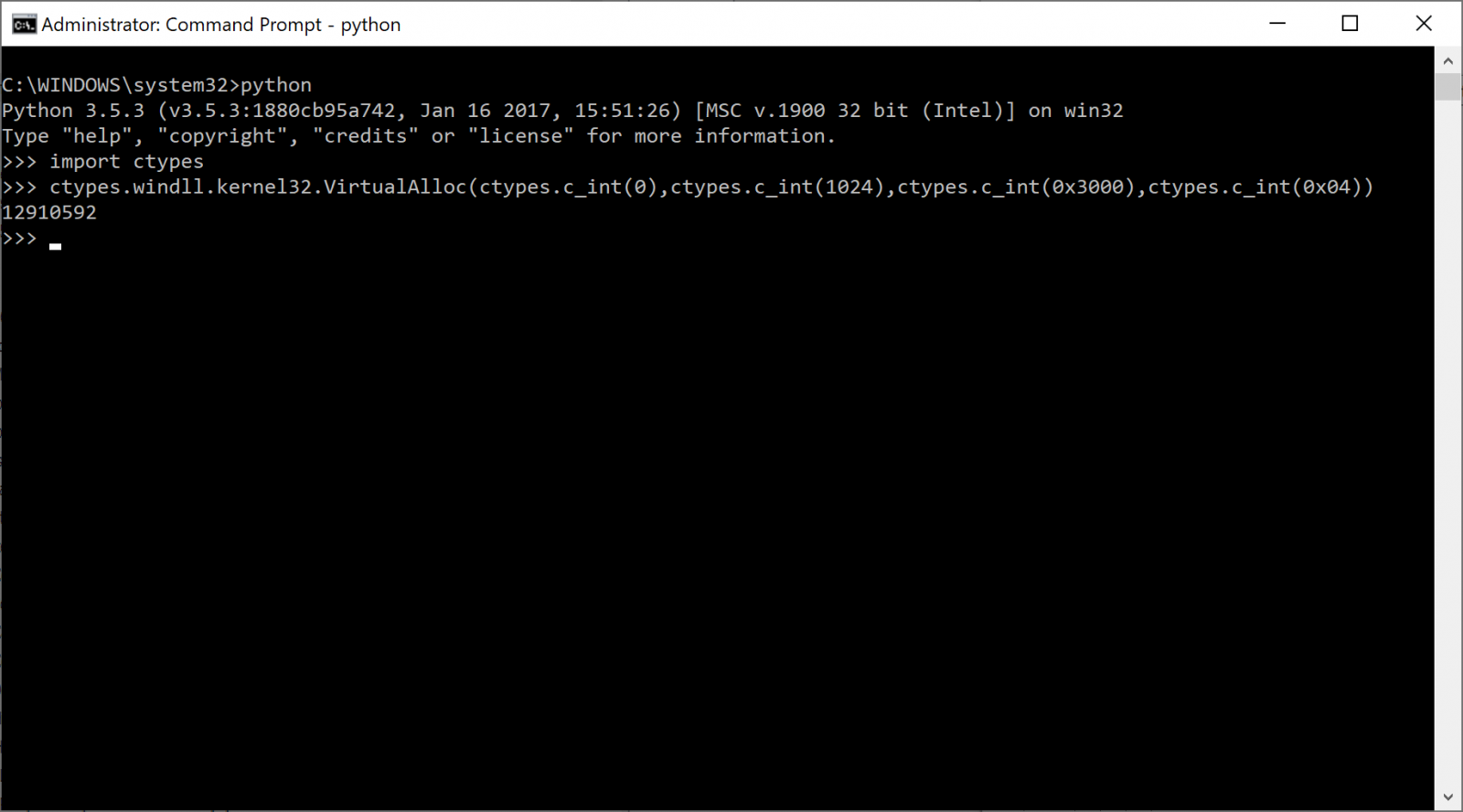
Let's switch back to the "dark side". When an attacker needs to write a piece of code to perform specific tasks, he will search for existing modules and not reinvent the wheel. To search for Python modules, the best place is to visit pypi.org[3]. Let's take another example: injection of code. Python is able to use all the Windows API calls with the help of the ctypes module:
In this example, I'm using the ctypes modules to call the Windows API VirtualAlloc() and allocated 1KB of memory with the flag "0x04" (which means that the memory will be allowed to contain executable code).
ctypes is not a common module used in simple scripts to automate tasks like System Administrators could write. It could be categorized as "suspicious". Let's have another example. I found this malicious script that implements a keylogger. It uses another not common Python module:
The suspicious module is pyHook which "provides callbacks for global mouse and keyboard events in Windows" as the documentation says.
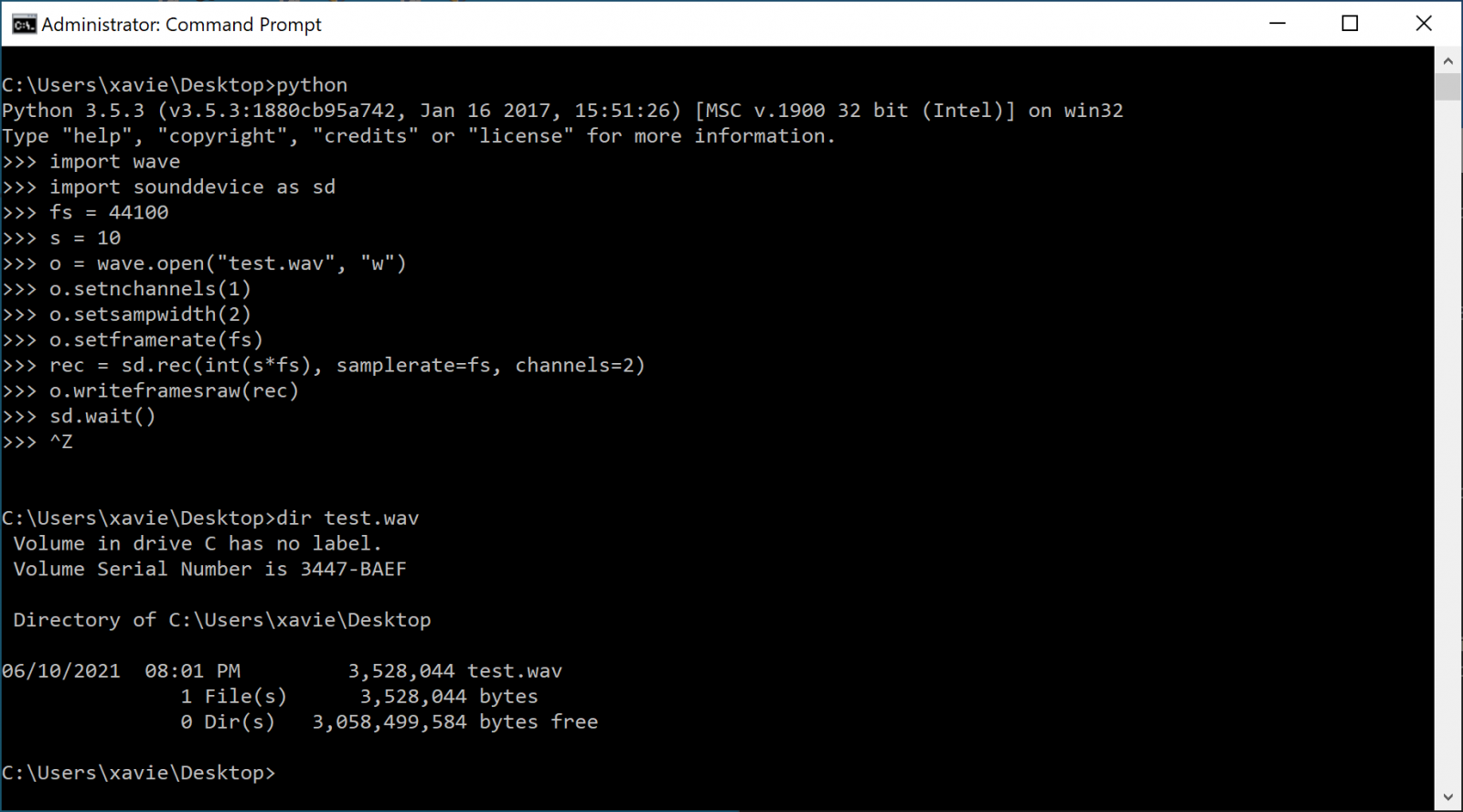
Want more? Let' use now wave and sounddevice to use the host microphone and record some conversations...
Other interesting modules? Use pyscreenshot to take screenshots or pynput to build another type of keylogger.
The question is now, from a defender's perspective, how can we detect suspicious Python modules?
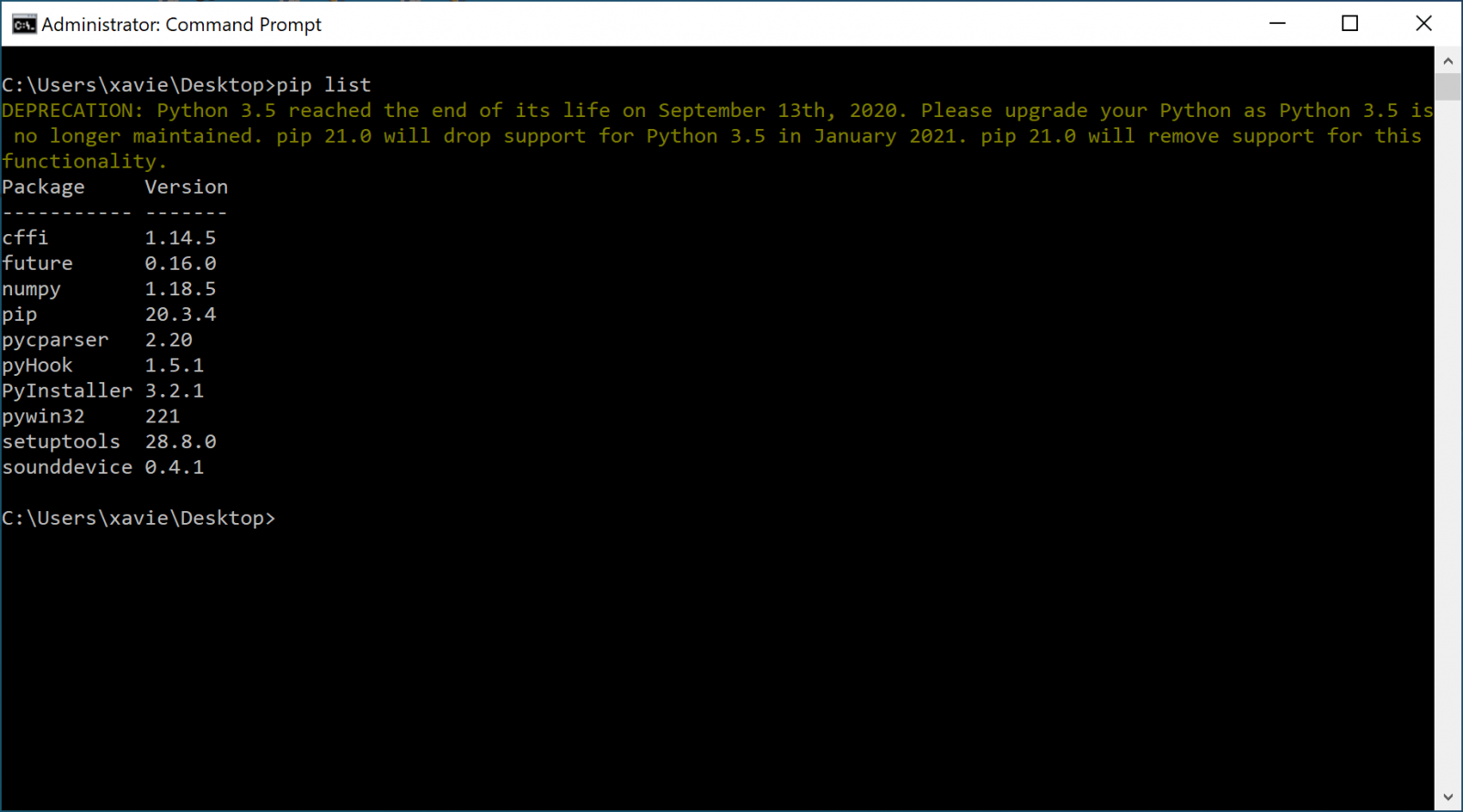
If you have access to the host, you can always use the "pip" command (the utility to manage modules):
pip will list the modules that have been installed "manually" (could be done by an attacker). To get a full list of modules, you can use the help() command in the Python interpreter:
As you can see, it's interesting to spot malicious Python code just by having a look at the imported modules! If you would like to hunt, you can create a YARA rule to search for interesting modules inside text files...
[1] https://isc.sans.edu/forums/diary/Python+and+Risky+Windows+API+Calls/26530
[2] https://isc.sans.edu/forums/diary/From+Python+to+Net/27366
[3] https://pypi.org
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Online | British Summer Time | Jul 28th - Aug 1st 2025 |

.PNG)


Comments