Dridex Phishing Campaign uses Malicious Word Documents
This is a guest diary submitted by Brad Duncan.
During the past few months, Botnet-based campaigns have sent waves of phishing emails associated with Dridex. Today, we'll examine a wave that occurred approximately 3 weeks ago. The emails contained malicious Word documents, and with macros enabled, these documents infected Windows computers with Dridex malware.
Various people have posted about Dridex [1] [2], and some sites like Dynamoo's blog [3] and TechHelpList [4] often report on these and other phishing campaigns.
Let's take a closer look at one of the November phishing waves.
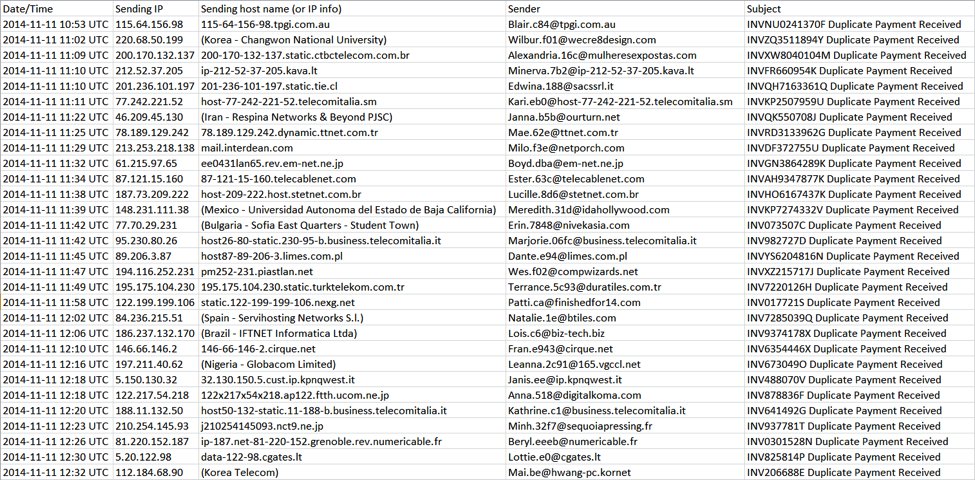
On 11 Nov 2014, I saw at least 60 emails with Duplicate Payment Received in the subject line. This appeared to be a botnet-based campaign from compromised hosts at various locations across the globe.
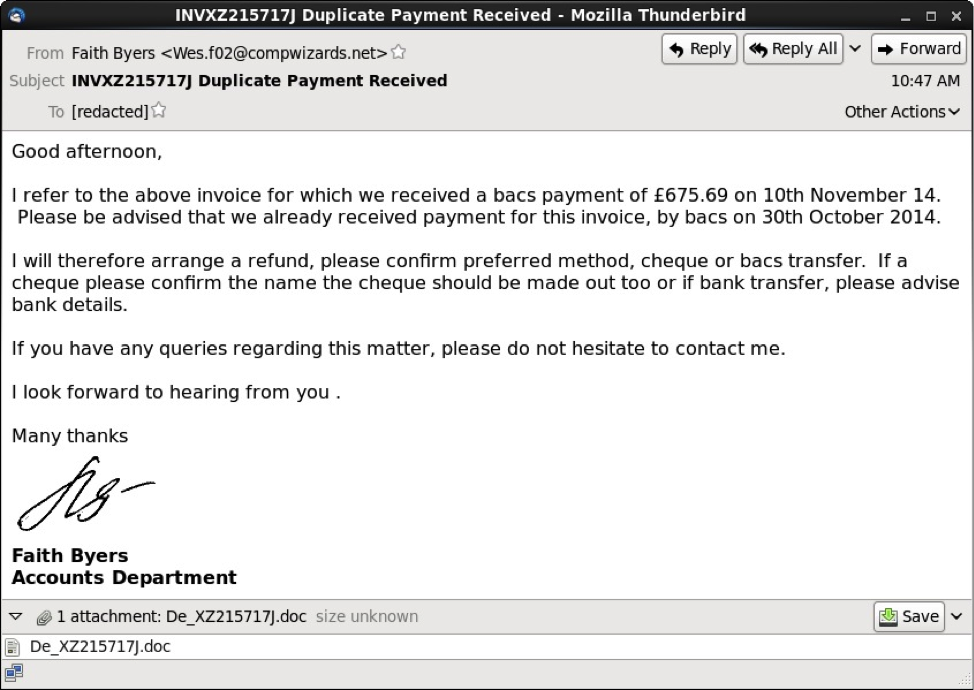
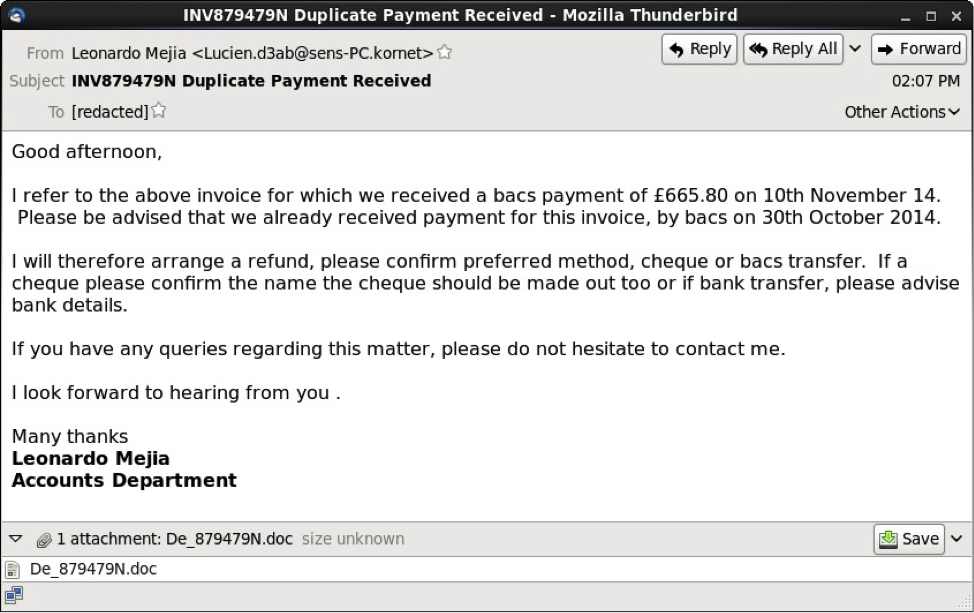
These messages had an HTML component, and some also had an image displaying a written signature.
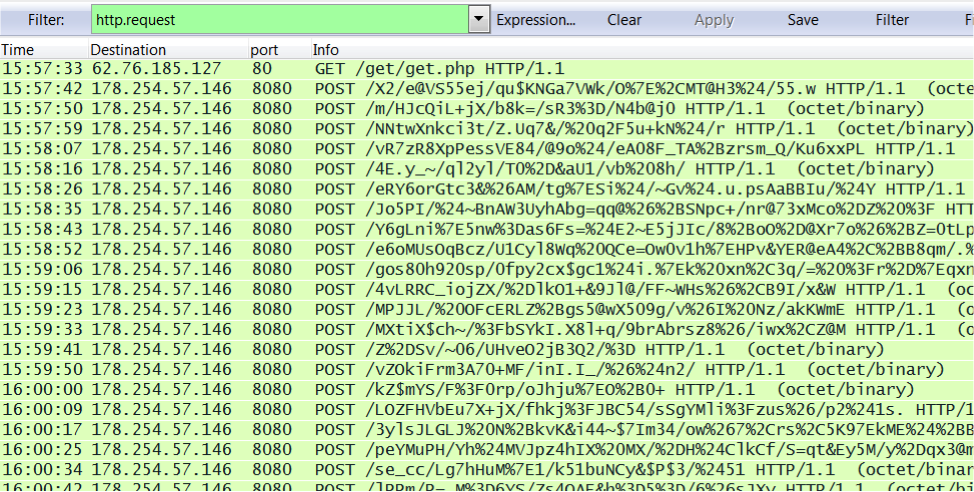
After opening the attached Word document on a Windows host, Dridex was downloaded if macros were enabled. Post-infection traffic began shortly after the download.
Shown above: infection traffic as seen in Wireshark.
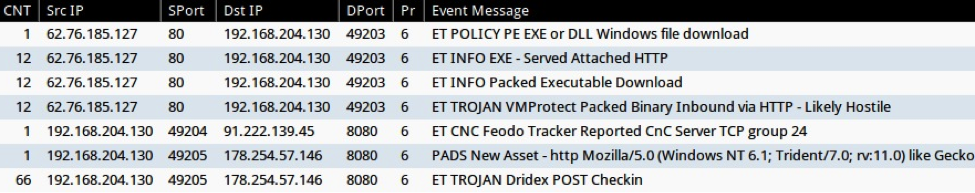
Monitoring the infection traffic on Security Onion, we found alerts for Dridex traffic from the EmergingThreats signature set (ET TROJAN Dridex POST Checkin) [5]
Shown above: events from Sguil in Security Onion.
File hashes changed during this wave of emails, indicating at least 3 different Word documents were used. During this phishing run, Dridex malware came from IP addresses in the 62.76.185.0/24 block. The following were samples were found:
Example of malicious Word document from 11 Nov 2014 phishing email:
https://malwr.com/analysis/M2M2ZDQxM2M2NzFhNDllZDhjMjQzMjAyYzRkNWZhYTA/
Example of Dridex malware downloaded by the above Word document:
https://malwr.com/analysis/YzA3ZDY0ODE2ZjY5NDE3NTlhZjkyNTg3NTIwNDljM2I/
References:
[1] http://stopmalvertising.com/malware-reports/analysis-of-dridex-cridex-feodo-bugat.html
[2] http://www.abuse.ch/?p=8332
[3] http://blog.dynamoo.com/
[4] https://techhelplist.com/index.php/spam-list/
[5] http://doc.emergingthreats.net/2019478
----------
Brad Duncan is a Security Analyst at Rackspace, and he runs a blog on malware traffic analysis at http://www.malware-traffic-analysis.net
| Application Security: Securing Web Apps, APIs, and Microservices | Washington | Jul 14th - Jul 19th 2025 |



Comments
Anonymous
Dec 1st 2014
1 decade ago
Anonymous
Dec 1st 2014
1 decade ago