DDoS and BCP 38
Quite often on many lists we will hear the term Best Current Practice (BCP) 38 bandied about and further recommendations to implement [1] [2][3][4] (See NANOG Mailing list archive) . Some will say ‘it will aid in DDoS mitigation’ and even others will even state ‘All Internet Service Providers (ISP) should implement this." Now before the philosophical discussions ensue in the comments, it might be a good idea to discuss, technically, what it is? And perhaps what it can do?
BCP 38 A.K.A. RFC 2827 (thank you for correction from our readers) [5] is a best practice methodology around ingress traffic filtering. The specific purpose as stated in the RFC abstract “to prohibit DoS attacks which use forged IP addresses to be propagated from 'behind' an Internet Service Provider's (ISP) aggregation point.” [5]
The BCP 38 outlines the concept of “restricting transit traffic” that comes from a “downstream network to known, and internally advertised prefixes” [5, p.4]. In an overly simplified diagram (My interpretation of the RFC, comments and corrections welcome), it means the ISP says:
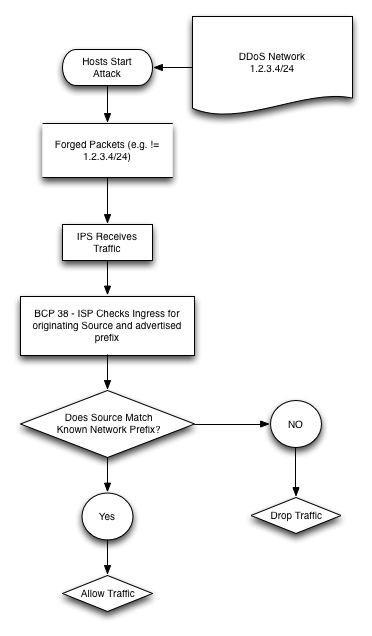
Let us know if you are using or have implemented BCP38? We recommend it and do feel that it has technical merit and can help reduce risk!
UPDATE
A reader noted (see comments) that a purposeful effort by NANOG to get more information out can be found at @ http://www.bcp38.info.
References:
[1] https://isc.sans.edu/diary/A+Chargen-based+DDoS%3F+Chargen+is+still+a+thing%3F/15647
[2] https://isc.sans.edu/diary/Disaster+Preparedness+-+Are+We+Shaken+or+Stirred%3F/11431
[3] https://isc.sans.edu/forums/diary/Where+Were+You+During+the+Great+DDoS+Cybergeddon+of+2013+/15496
[4] https://isc.sans.edu/podcastdetail.html?id=3260
[5] http://tools.ietf.org/html/bcp38
Richard Porter
--- ISC Handler on Duty
Twitter: @packetalien
Blog: http://packetalien.com
"Got Packets?"



Comments
Members of NANOG are putting some efforts to make BCP38 information more available to a wider audience, in the hope that it could create some customers pressure to start cleaning up that mess.
http://www.bcp38.info
PS: Let moderator "hat" bcp38.info know if they can incorporate the graphic in that wiki.
Anonymous
Feb 27th 2014
1 decade ago
Anonymous
Feb 27th 2014
1 decade ago
Thanks!
Anonymous
Feb 28th 2014
1 decade ago
Anonymous
Feb 28th 2014
1 decade ago
Looking into deploy BCP38 on a customer facing interface. I came across some suggestion about deploying something like this.Looking for any input from you guys.
Thx
ip verify unicast source reachable-via rx allow-default 171
access-list 171 deny icmp any any echo log-input
access-list 171 deny icmp any any echo-reply log-input
access-list 171 deny udp any any eq echo log-input
access-list 171 deny udp any eq echo any log-input
access-list 171 deny tcp any any established log-input
access-list 171 deny tcp any any log-input
access-list 171 deny ip any any log-input
Anonymous
Feb 9th 2016
9 years ago