Catching up with Blank Slate: a malspam campaign still going strong
Introduction
"Blank Slate" is the nickname for a malicious spam (malspam) campaign pushing ransomware targeting Windows hosts. I've already discussed this campaign in a previous diary back in March 2017. It has consistently sent out malspam since then. Today I collected 11 Blank Slate emails, so this diary examines recent developments from the Blank Slate campaign.
Today's Blank Slate malspam was pushing Cerber and GlobeImposter ransomware.
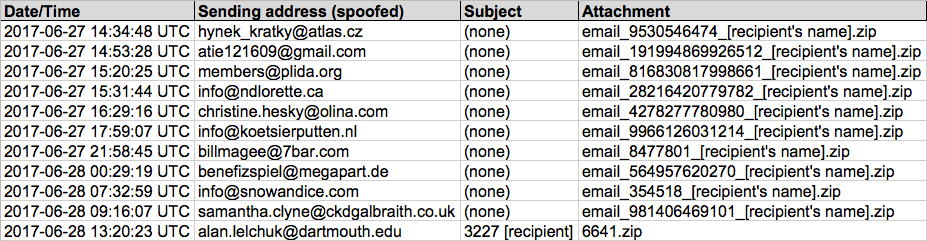
Shown above: Screenshot of spreadsheet tracking for the 11 emails (image 1 of 3).
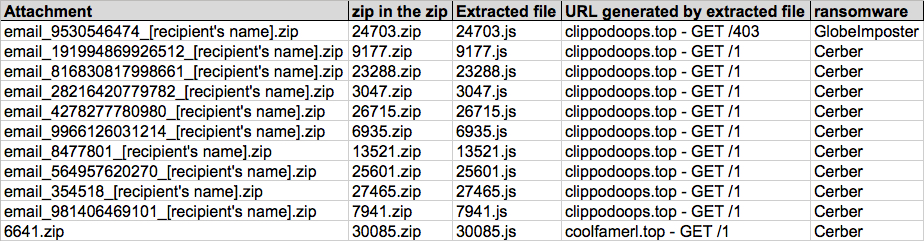
Shown above: Screenshot of spreadsheet tracking for the 11 emails (image 2 of 3).
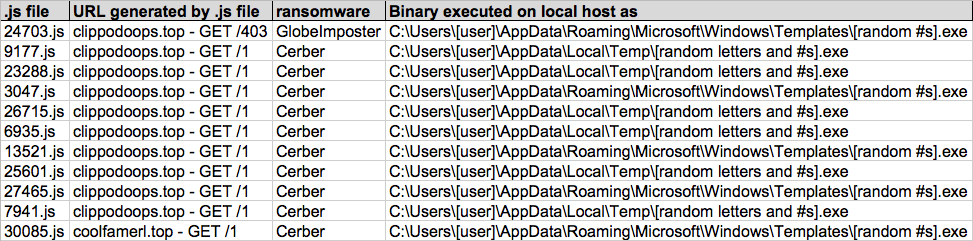
Shown above: Screenshot of spreadsheet tracking for the 11 emails (image 3 of 3).
The malspam
Normally, emails from this campaign are blank messages with vague subject lines and attachments that don't indicate what it is. That's why I've been calling it the "Blank Slate" campaign.

Shown above: Example of a typical Blank Slate email from today, Wednesday 2017-06-28.
However, since yesterday, the Blank Slate campaign has sent several Microsoft-themed messages. We've seen this before. As recently as 2017-04-13, I documented Blank Slate malspam using fake Microsoft messages that led to fake Chrome installation pages. Those fake Chrome pages sent victims zip archives containing malicious .js files designed to infect Windows hosts with ransomware.
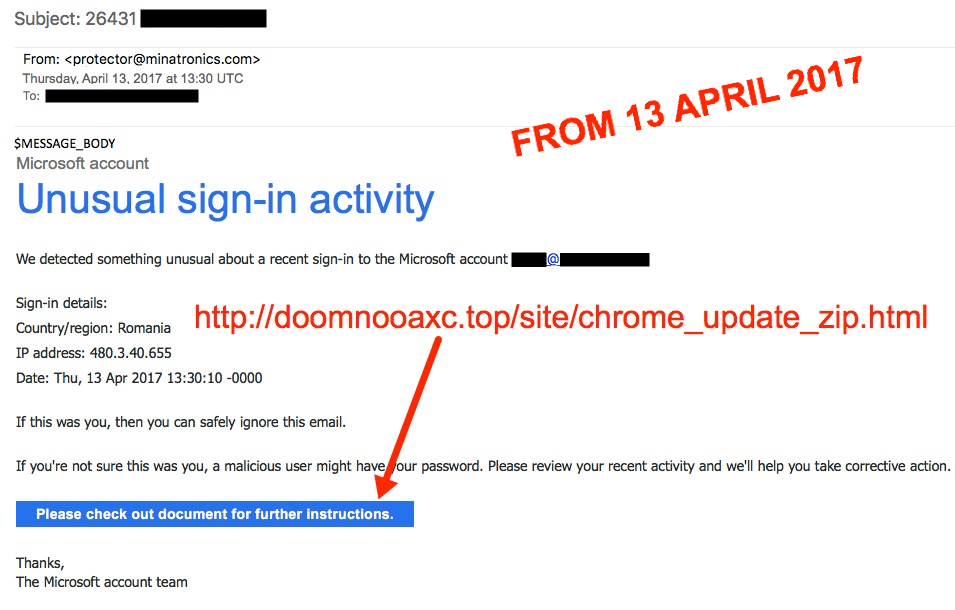
Shown above: Microsoft-themed Blank Slate email from April 2017.
Today's messages look similar to previous Microsoft-themed emails; however, this time they don't have links to a fake Chrome page. Instead, they have zip attachments containing malicious .js files.
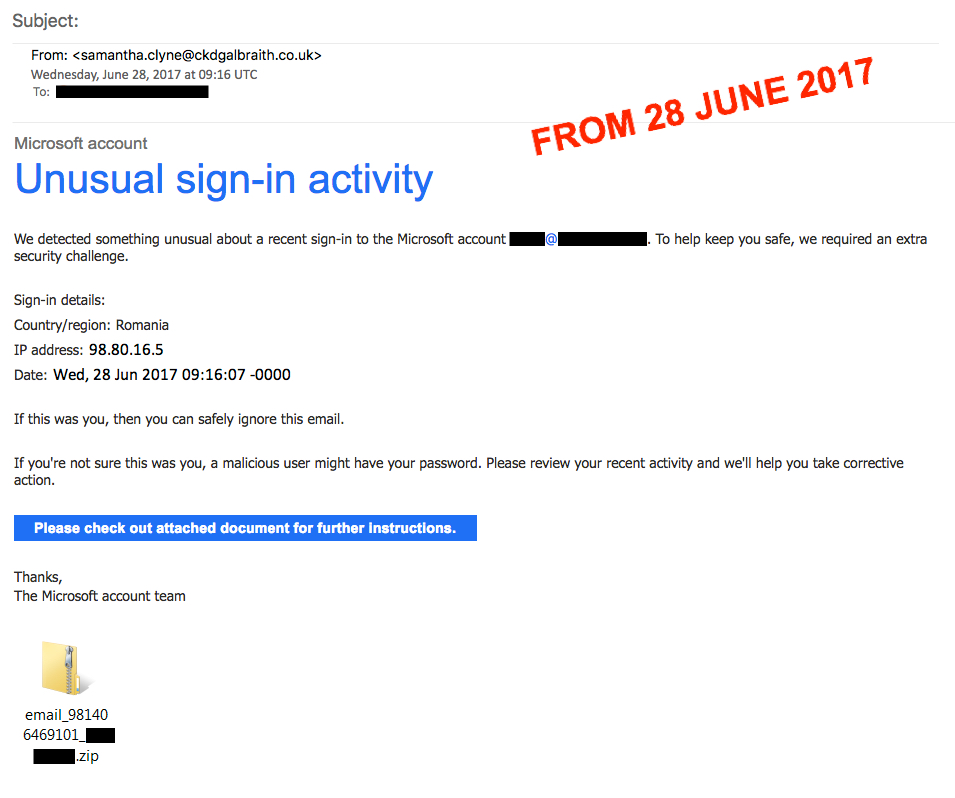
Shown above: Microsoft-themed Blank Slate email from today, Wednesday 2017-06-28.
Otherwise, these emails are similar to previous waves of Blank Slate malspam.
The attachments
As usual, the zip attachments are double-zipped, and they contain a .js file designed to infect a Windows computer with ransomware. I saw two types of .js files. One was about 9 kB in size, and it ran the downloaded ransomware from the user's AppData\Local\Temp directory. The other type of .js file was about 31 kB in size, and it ran the downloaded ransomware from the user's AppData\Roaming\Microsoft\Windows\Templates directory.

Shown above: Example of a 9 kB .js file from this wave of malspam.
The traffic
Traffic is also typical of what we've seen before with Blank Slate malspam. Ransomware binaries are typically downloaded in the clear from a domain name ending with .top.

Shown above: Ransomware binary downloaded by one of the .js files.
No post-infection traffic was noted for today's GlobeImposter ransomware. I saw the typical post-infection for today's Cerber samples.

Shown above: Traffic generated by a Cerber sample from today's malspam, filtered in Wireshark.
Post infection
As others have noted Twitter and elsewhere, recent Cerber samples use "CRBR" as their name in the decryption instructions. File extensions used by Cerber for any encrypted files consist of 4 characters based on the MachineGuid of the infected Windows host.
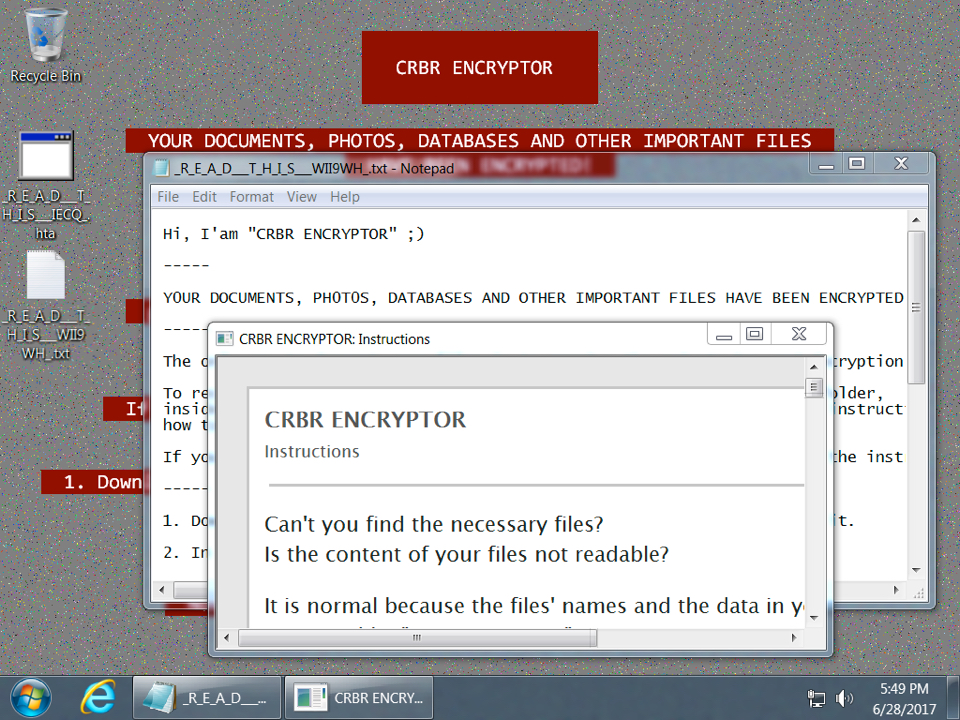
Shown above: Desktop of a Windows host infected with one of today's Cerber samples.

Shown above: Based on the above MachineGuid, and all my encrypted files end with .BRAD
GlobeImposter also acts the same as we've seen before. Encrypted files use the .crypt file extension.
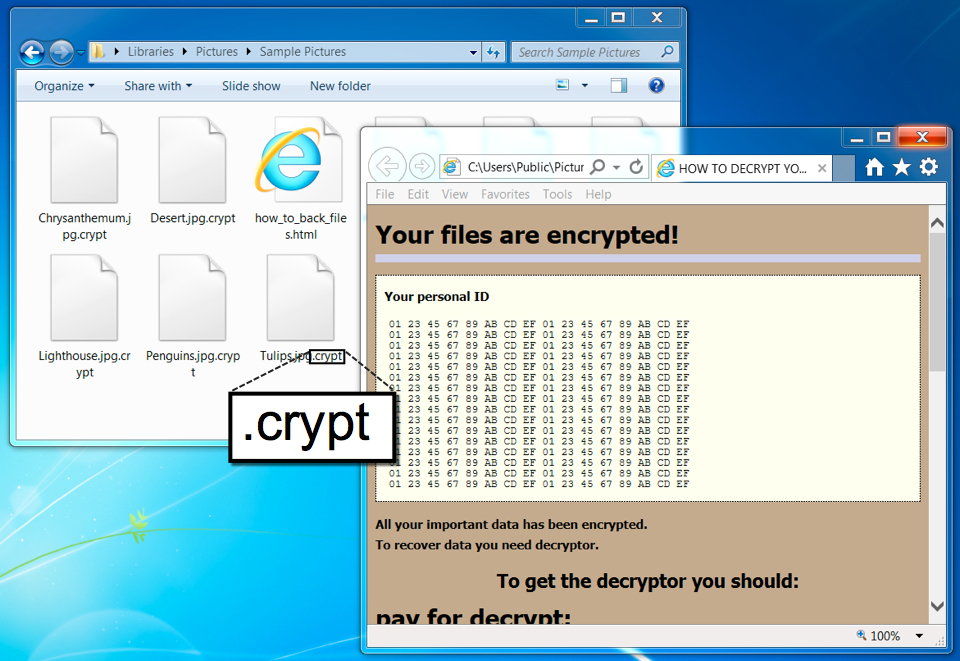
Shown above: Desktop from a Windows host infected with today's GlobeImposter sample.
Indicators of Compromise (IOCs)
The following are SHA256 hashes for the today's extracted .js files:
- 10358fb055b8d8e0d486eafc66be180d52481667fb63bf4e37bf9cafe5a0dbdb - 7941.js
- 153b11ae2df30b671bd0bd54af55f83fd2a69e47c8bb924b842bc1b44be65859 - 25601.js
- 1cbf043831b16ca83eeaff24f70b1a3ea4973d2609e64db33fd82cc0629f1976 - 6935.js
- 567bb9c835306e02dbedc5f10e32c77a2c6f1c2f28ff49c753f963776a9378b5 - 30085.js
- 7ecd1253aad0935df1249d6504d3f4090a00466fa159c2ec4e2d141b4b75068f - 9177.js
- 8b7202a672290e651f9d3c175daaf2b8a3635eba193e925da41bd880a611f2af - 13521.js
- 8ec6455eb9f8a72fef35e9a330e59153f76b8ebd848c340024669e52589ceb18 - 23288.js
- b6ab00337d1e40f894ca3959ee9a19e4c9e59605ed1f2563f0bde4df5f76981b - 27465.js
- c9f71912dd39d4d4ed9f54f6a51f99ee0687e084c2e8782f0b0d729b743e7281 - 3047.js
- d19233fd99213f5a1d299662d9693eb6bc108d72ce676893bc69c8d309caa54a - 26715.js
- ed855d0b4cfd5150a4b44a1d3b6c26224e2990743d977804bab926d569aa963b - 24703.js
The following are SHA256 hashes for ransomware samples downloaded by the extracted .js files:
- 0dc831b502f29d4a6a68da9e511feb8c646af4fcfdeaaee301cb5b0dbaf47c5f - Cerber
- 703b1ea2b0310efdc194b178c777c2e63d5ad1b7f2ac629c01ffa1b36859ba2f - GlobeImposter
- b1be5af4169014508b17d2de5aa581ea62988cc4d3570ed2ed7f9fb931a5902b - Cerber
- d1ed3742380539fbef51804e1335c87dd0ef24a6de7f0aa09ce26ad1efe4bcef - Cerber
The following are domains, HTTP requests, and IP addresses associated with today's Blank Slate malspam:
- 103.52.216.15 port 80 - coolfamerl.top - GET /1 [returned Cerber]
- 103.52.216.15 port 80 - clippodoops.top - GET /403 [returned GlobeImposter]
- 103.52.216.15 port 80 - clippodoops.top - GET /1 [returned Cerber]
- 77.12.57.0 thru 77.12.57.31 (77.12.57.0/27) UDP port 6893 [Cerber post-infection scan]
- 19.48.17.0 thru 19.48.17.31 (77.12.57.0/27) UDP port 6893 [Cerber post-infection scan]
- 87.98.176.0 thru 87.98.179.255 (87.98.176.0/22) UDP port 6893 [Cerber post-infection scan]
- 216.170.123.2 port 80 - xpcx6erilkjced3j.1t2jhk.top - Domain leading to the Cerber decryptor
Email from the GlobeImposter decryption instructions: chines34@protonmail.ch
Final words
As I noted last time, potential victims must open the zip attachment, open the enclosed zip archive, then double-click the final .js file. That works on default Windows configurations, but properly-administered Windows hosts and decent email filtering are enough, I think, to keep most people from worrying about Blank Slate.
This is definitely not as serious the recent Petya/NotPetya ransomware outbreak on 2017-06-27. I still wonder how many people are fooled by Blank Slate malspam. Does anyone know someone who was actually infected from these emails? If so, please share your story in the comments section below.
Pcap and malware samples for this ISC diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments
Jorge
Anonymous
Jun 29th 2017
8 years ago