CVE-2020-5135 - Buffer Overflow in SonicWall VPNs - Patch Now
Discovered by Tripwire VERT, CVE-2020-5135 is a buffer overflow vulnerability in the popular SonicWall Network Security Appliance (NSA) which can permit an unauthenticated bad guy to execute arbitrary code on the device.
The following versions of SonicWall are vulnerable:
SonicOS 6.5.4.6-79n and earlier
SonicOS 6.5.1.11-4n and earlier
SonicOS 6.0.5.3-93o and earlier
SonicOSv 6.5.4.4-44v-21-794 and earlier
SonicOS 7.0.0.0-1
After some research, I am unclear how many devices may be vulnerable to this attack. Tenable/Tripwire implies it could be up to approximately 800,000 devices (as detected by Shodan).
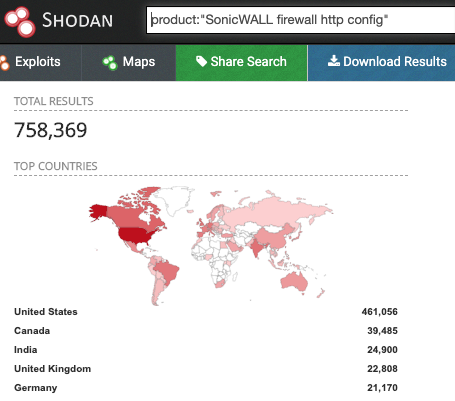
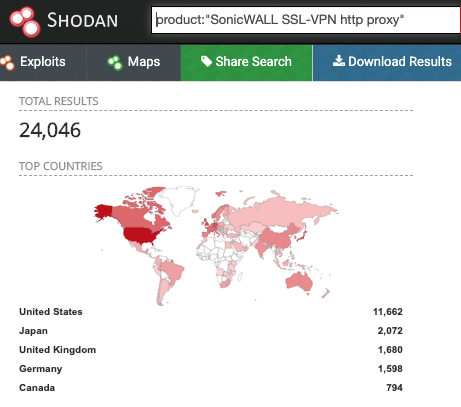
I expect that not all of these devices have the VPN enabled, and some have been updated already, so the number is probably quite a bit lower, but still significant.
I have not been able to find a way to remotely detect which devices are vulnerable. Nmap can be used to detect SonicWall instances, but does not provide enough information to determine the OS version or probe for the vulnerability.
PORT STATE SERVICE REASON VERSION
80/tcp open http-proxy syn-ack ttl 53 SonicWALL SSL-VPN http proxy
|_http-server-header: SonicWALL SSL-VPN Web Server
443/tcp open ssl/http-proxy syn-ack ttl 53 SonicWALL SSL-VPN http proxy
|_http-server-header: SonicWALL SSL-VPN Web Server
50001/tcp filtered unknown no-response
If any of you know of a reliable scanning technique to detect this vulnerability please let me know at our contact page and I will update the diary.
SonicWall released updates last week which fix this vulnerability and several others. Although no known exploit has been detected in the wild. I expect, give recent historical attacks on VPNs, I would expect this one will get a lot of interest from bad guys. I strongly recommend updating as soon as reasonable.
More information can be found at the following links:
https://www.bleepingcomputer.com/news/security/critical-sonicwall-vulnerability-affects-800k-firewalls-patch-now/
https://www.tripwire.com/state-of-security/vert/sonicwall-vpn-portal-critical-flaw-cve-2020-5135/
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2020-0010
-- Rick Wanner MSISE - rwanner at isc dot sans dot edu - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)



Comments
Anonymous
Oct 18th 2020
4 years ago