3 examples of malspam pushing Loki-Bot malware
Introduction
Loki-Bot (also spelled "Loki Bot" or "LokiBot") is an information stealer that sends login credentials and other sensitive data from an infected Windows host to a server established for each malware sample. It's commonly distributed through malicious spam (malspam), and I usually run across samples of Loki-Bot every day. More information can be found in a SANS Reading Room paper written by Rob Pantazopoulos here.
Malspam pushing Loki-Bot doesn't follow specific patterns. Other malspam campaigns pushing Dridex, Emotet, or Hancitor have very similar emails, where the message text, links and/or attachment names follow specific patterns. This isn't true for Loki-Bot. I can never say if a particular malspam sample I run across will have Loki-Bot or something else until I examine the malware. Malspam pushing Loki-Bot doesn't seem as wide-scale as mass-distribution campaigns like those for Emotet or Hancitor. However, I can usually find at least one or two Loki-Bot malspam samples each day that have been submitted to VirusTotal.
To give you a better idea how different these emails are, I've collected three malspam samples pushing Loki-Bot: one from Monday 2018-02-05 and two from Tuesday 2018-02-06. If we examine these emails and their associated malware, we can get a better sense of malspam-based distribution for Loki-Bot.
General distribution patterns
I've only seen Loki-Bot distributed through malspam. I've not seen Loki-Bot distributed through web-based infection vectors like pop-up browser windows or exploit kits. But I have a limited field of view. If anyone has seen Loki-Bot come through web traffic not caused by malicious email attachments, please leave a comment for this diary.
Malspam pushing Loki-Bot uses email attachments. These attachments are either some sort of archive file containing a Loki-Bot executable, or the attachments are Microsoft Office documents designed to download and install Loki-Bot. In some cases, the documents are files that exploit vulnerabilities like CVE-2017-11882 (example here) to infect Windows hosts with Loki-Bot.
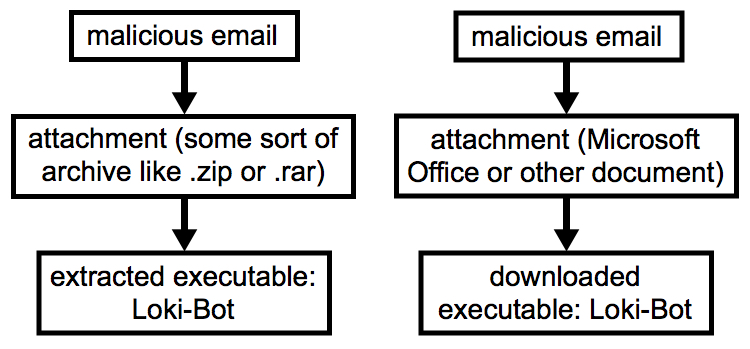
Shown above: Two different types of infection chains for Loki-Bot.
First email example: 2018-02-06 at 12:34 UTC
In the first example, traffic patterns and infection artifacts were fairly straight-forward. The Loki-Bot executable copied itself to a folder under the user's AppData\Roaming directory for persistence. No real surprises here.
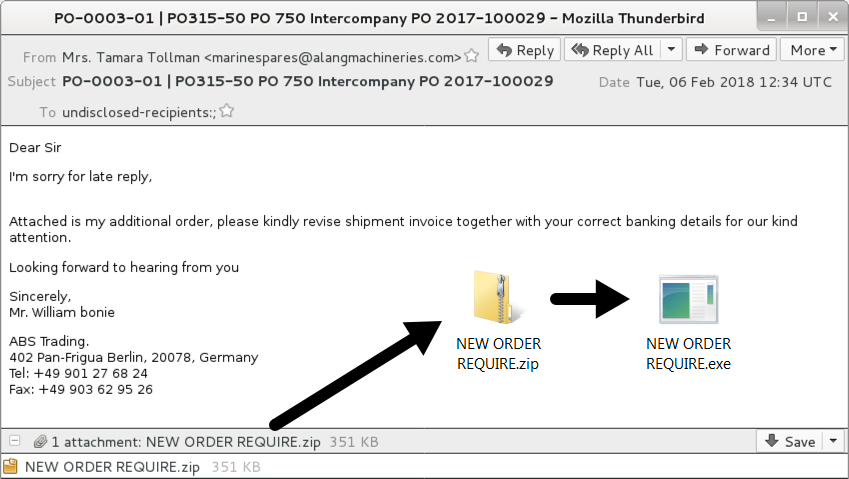
Shown above: Screenshot of the first email example.
Email information:
- Date: Tue, 06 Feb 2018 13:34:06 +0100
- Received: from server1.bollywoodchaska.com ([184.154.131.122])
- From: "Mrs. Tamara Tollman" <marinespares@alangmachineries.com>
- Subject: PO-0003-01 | PO315-50 PO 750 Intercompany PO 2017-100029
- Attachment name: NEW ORDER REQUIRE.zip
- SHA256 hash: 4bb536902c2000f793d539d2887df264156dba1a97460c3ee139a4e1904131c9
- Extracted file: NEW ORDER REQUIRE.exe
- SHA256 hash: afb3edaf073c0d2435fac520ddc846261ff85040494999415657ce35b1246c66
- Post-infection traffic: 192.152.0.152 port 80 - liltem.flu.cc - POST /ml/vrs/sly/lok/panel/fre.php
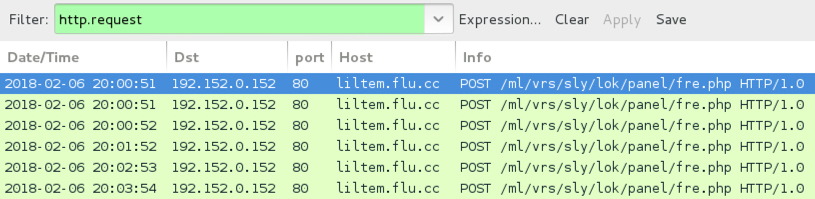
Shown above: Traffic from the infection filtered in Wireshark.
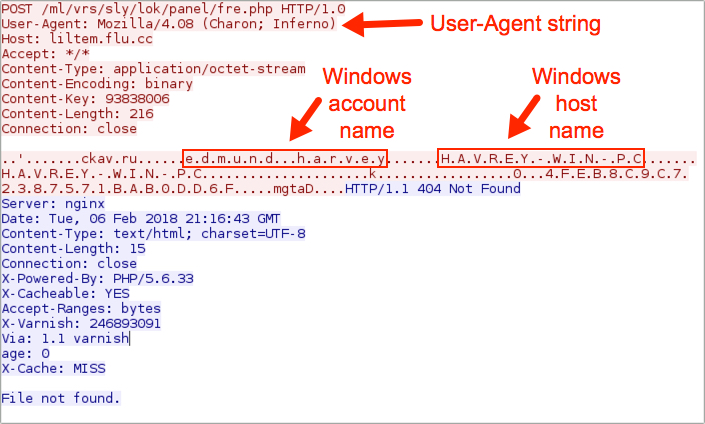
Shown above: One of the HTTP POST requests from an infected Windows host.
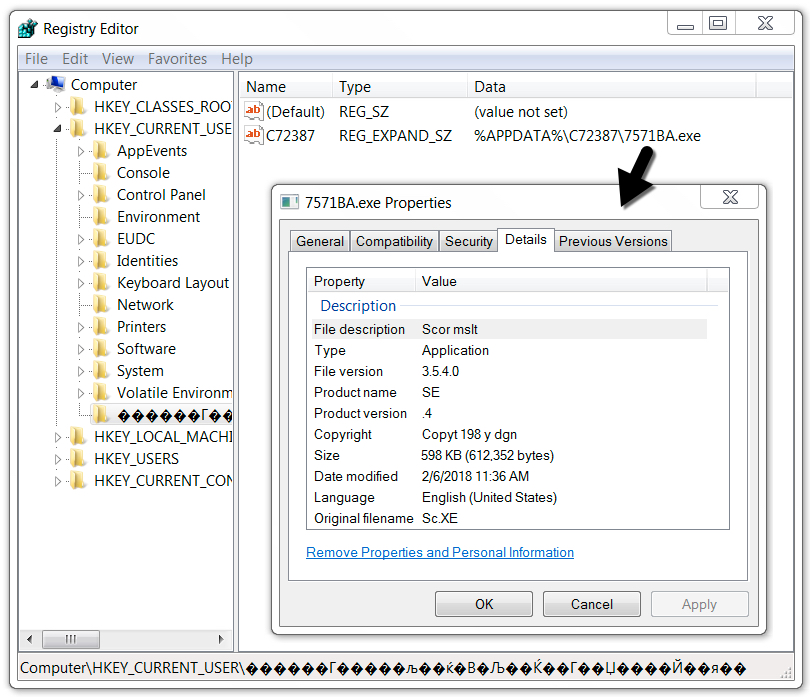
Shown above: Windows registry updated to keep the malware persistent.
Second email example: 2018-02-06 at 13:17 UTC
I've documented ISO attachments used in malspam pushing Loki-Bot back in October 2017, and ISO files were probably used well before that. Again, the traffic patterns and infection artifacts were fairly straight-forward. Again, the Loki-Bot executable copied itself to a folder under the user's AppData\Roaming directory for persistence. Again, no real surprises.
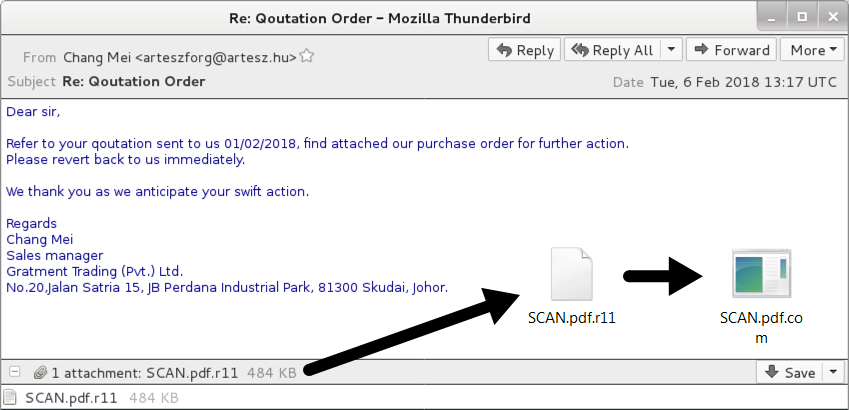
Shown above: Screenshot of the second email example.
Email information:
- Date: Tue, 6 Feb 2018 14:17:27 +0100
- Received: from mail.ivacbd.com ([66.226.72.67])
- From: "Chang Mei"<arteszforg@artesz.hu>
- Subject: Re: Qoutation Order
- Attachment name: SCAN.pdf.r11 (an ISO file)
- SHA256 hash: 5348c7747c150dbc35328a5c89a0b64fa61f1911daf33b1ca24caa79e2eb55b7
- Extracted file: SCAN.pdf.com (a PE32 Windows executable)
- SHA256 hash: d722642b17e8897a092fc9f7b93cc002ee10f37f792171979f9d22f35a673e8c
- Post-infection traffic:
- 185.145.128.60 port 80 - festy18.info - POST /osy/fre.php
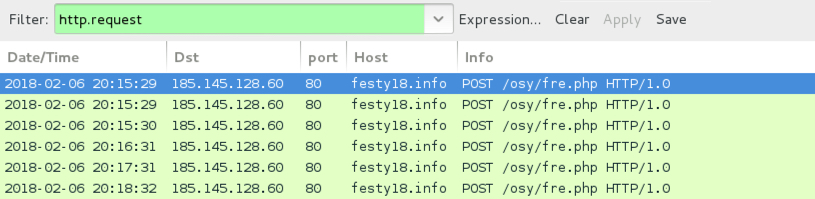
Shown above: Traffic from the infection filtered in Wireshark.
Third email example: 2018-02-05 at 15:03 UTC
This email was a bit different, because it had a Microsoft Excel spreadsheet with a malicious macro that downloaded the Loki-Bot executable. The Loki-Bot executable was made persistent through a Start Menu shortcut. I also saw an Loki-Bot-style entry in the Windows registry. However, that Windows registry entry ran a copy of Microsoft's COM Surrogate, a legitimate program re-named and saved to the usual Loki-Bot location. Perhaps that was a decoy. Otherwise, traffic patterns were as expected. The post-infection artifacts were a little unusual for Loki-Bot, though.
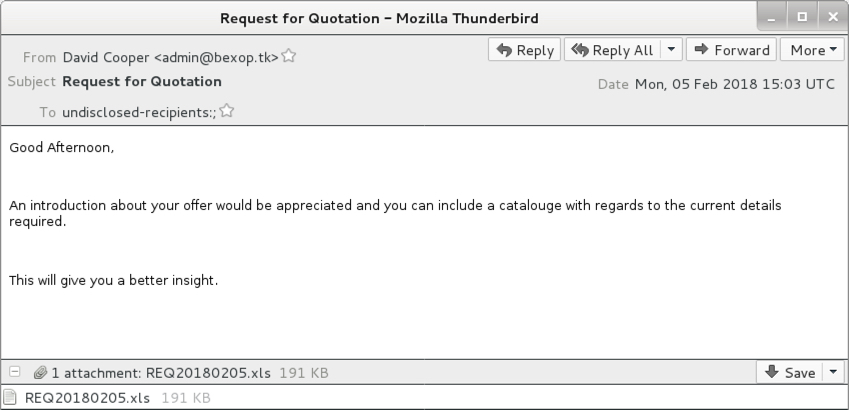
Shown above: Screenshot of the third email example.
Email information:
- Date: Mon, 05 Feb 2018 16:03:33 +0100
- Received: from mail.bexop.tk ([174.138.12.173])
- From: David Cooper <admin@bexop.tk>
- Subject: Request for Quotation
- Attachment name: REQ20180205.xls
- SHA256 hash: ed25239eaa51648ebe7b7597091f98d06e1c9e3e29e78dc865eb70818889b7ce
- Downloaded Loki-Bot: C:\Users\[username]\AppData\Local\Temp\manahj.exe
- SHA256 hash: adccbeba5792ef80048bcbb20f860d368dea9db35814b2c99447fbbe7f310230
- Post-infection traffic:
- 101.99.75.184 port 80 - kdotraky.com - POST /temp/Panel/five/fre.php

Shown above: Email attachment, an Excel spreadsheet with malicious macro.
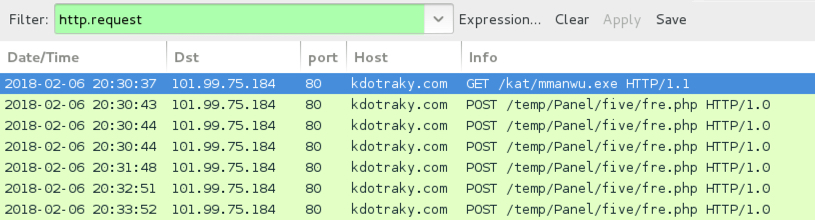
Shown above: Traffic from the infection filtered in Wireshark.
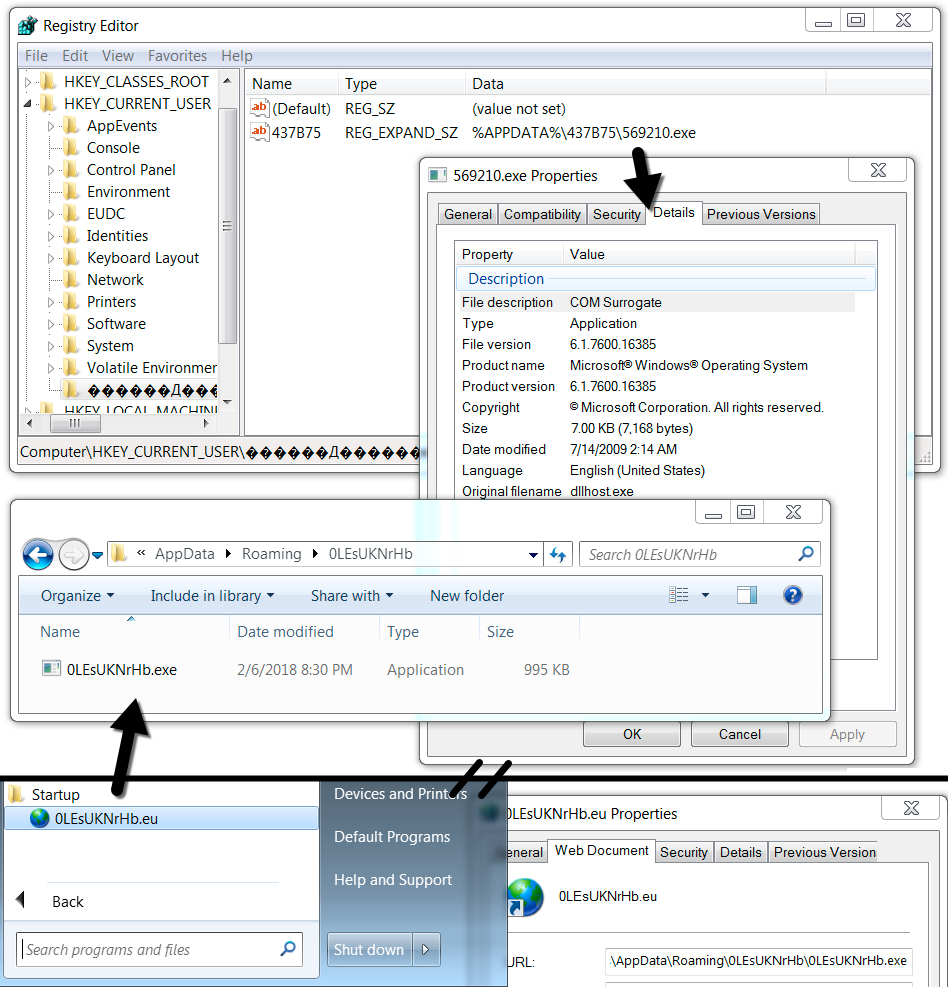
Shown above: Post-infection artifacts on the infected Windows host.
Final words
Within a 24 hour timeframe, I found three emails distributing Loki-Bot. Apart from the general use of an invoice, order, or quotation theme, the emails distributing Loki-Bot didn't have many similarities. With each of the attachments, the infection chain was slightly different, but the end result was the same type of Loki-Bot infection.
As always, the standard disclaimer applies: This malspam is no more dangerous than other types of malspam we see on a daily basis. As always, properly-administered Windows hosts are unlikely to get infected. For Windows hosts, system administrators and the technically inclined can implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
The servers at festy18.info, kdotraky.com, and liltem.flu.cc are all associated with Loki-Bot. If they aren't blocked already, security personnel should block any web-based traffic to these domains if they can.
---
Brad Duncan
brad [at] malware-traffic-analysis.net



Comments