Incident Response Methodologies Worm Infection Cheat Sheet
The CERT Societe Generale (site is in French and English) has published a 6 Steps IRM Worm Infection cheat sheet (English only) freely available for download here. "Feel free to contact us if you identify a bug or an error in these IRMs." [2]
[1] http://cert.societegenerale.com/en/publications.html
[2] http://cert.societegenerale.com/resources/files/IRM-1-Worm-Infection.pdf
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
Firefox, Thunderbird and SeaMonkey Security Updates
Mozilla Firefox fixes multiple flaws which could let remote users execute arbitrary code, access information and access restricted resources.
"Mozilla developers identified and fixed several memory safety bugs in the browser engine used in Firefox and other Mozilla-based products. Some of these bugs showed evidence of memory corruption under certain circumstances, and we presume that with enough effort at least some of these could be exploited to run arbitrary code." [1]
http://www.mozilla.org/security/announce/2011/mfsa2011-12.html
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
0 Comments
DSL Reports advise 9,000 accounts were compromised
The web site www.dslreports.com has sent out an email notification that around 9,000 accounts have been compromised.
The site has a write up of the incident here: http://www.dslreports.com/forum/r25793356-site-user-password-intrusion-info
Thank you to ISC reader Alan for passing this on.
Chris Mohan --- Internet Storm Center Handler on Duty
2 Comments
VMware ESXi 4.1 Security and Firmware Updates
The patch resolves several security issues (CVE-2011-1786, CVE-2010-1324, CVE-2010-1323, CVE-2010-4020, CVE-2010-4021, and CVE-2011-1785) affecting OpenLDAP and KRB5.
The full list of issues fixed with patch ESXi410-201104401-SG is available here and the patch can be downloaded here.
[1] http://kb.vmware.com/kb/1035108
[2] http://www.vmware.com/patch/download/
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
0 Comments
McAfee VirusScan Enterprise: False Positive Detection Generic.dx!yxk in DAT 6329
McAfee Labs have issued an alert that McAfee VirusScan DAT file 6329 is returning a false positive for spsgui.exe. This is impacting SAP telephone connectivity functionality.
McAfee have a work around for the issue documented in KB71739 https://kc.mcafee.com/corporate/index?page=content&id=KB71739
Chris Mohan --- Internet Storm Center Handler on Duty
0 Comments
Gathering and use of location information fears - or is it all a bit too late
With all the excitement in the media at the moment about vendors being able to track our every move*, Apple have released Q&A [1] on what data they actually track on the iPhone.
It's an interesting enough read and may calm the fears of some of being tracked. Or perhaps not.
The Internet Storm Center has published a number of stories on data being collected, in a delightful variety of ingenious ways, then sold to marketers to gain a better insight in to how to get the consumer to spend more money. This wealth of information from raw data has huge applications and, as an example, the Dutch Police took the initiative. They bought data from TomTom to place speed traps and cameras [2], which is a very sneaky idea and much more accurate for revenue generation that building them on busy roads. In case you were attempting new land speed records on Dutch roads, all the data purchase was anonymous, so you're safe from the digital arm of the law...
The part of this story that is thought-provoking comes from customer pressure on TomTom to stop doing this. TomTom have agreed and changed their policy on-selling the traffic data.
When many raise their voices in complaint, threaten to leave the service and create negative publicity does it make a different to the mega corporations? Or have we simply lost this battle all ready as we signed, check-boxed or clicked "agree" a EULA [3] giving our acceptance to track, monitor, use and sell any data generated.
I'll leave it up to you to decide if consumer power is one thing that can make a difference once you discover something is tracking your every move.
Of course, if you constantly updating your location in FourSquare, Facebook, Twitter et al while using your loyalty cards then you may not care in the first place.
[1] http://www.apple.com/pr/library/2011/04/27location_qa.html
[2] http://www.engadget.com/2011/04/27/tomtom-user-data-sold-to-danish-police-used-to-determine-ideal/
[3] http://www.webopedia.com/TERM/E/EULA.html
*Fancy that - I mean it's not like I'm carrying at least two items that bleat out my location every few seconds that are designed so people can get in contact wherever I am. Plus I pay a small fortune for the privilege to own the lovely, shiny devices - I could be my own privacy's own worst enemy. Hmmm.
Chris Mohan --- Internet Storm Center Handler on Duty
7 Comments
Cisco Security Advisories
Two Cisco security advisories have been published: Multiple Vulnerabilities in Cisco Unified Communications Manager and Cisco Wireless LAN Controllers Denial of Service Vulnerability
The details below have been taken from the Cisco's advisories:
Cisco Security Advisory: Multiple Vulnerabilities in Cisco Unified Communications Manager
Document ID: 112878
Advisory ID: cisco-sa-20110427-cucm
Revision 1.0
For Public Release 2011 April 27 1600 UTC (GMT)
+---------------------------------------------------------------------
Summary
=======
Cisco Unified Communications Manager (previously known as Cisco CallManager) contains the following vulnerabilities:
* Three (3) denial of service (DoS) vulnerabilities that affect Session Initiation Protocol (SIP) services
* Directory transversal vulnerability
* Two (2) SQL injection vulnerabilities
Cisco has released free software updates for affected Cisco Unified Communications Manager versions to address the vulnerabilities. A workaround exists only for the SIP DoS vulnerabilities.
This advisory is posted at
http://www.cisco.com/warp/public/707/cisco-sa-20110427-cucm.shtml
Affected Products
=================
Vulnerable Products
+------------------
The following products are affected by at least one of the vulnerabilities that are described in this advisory:
* Cisco Unified Communications Manager 6.x
* Cisco Unified Communications Manager 7.x
* Cisco Unified Communications Manager 8.x
Note: Cisco Unified Communications Manager version 5.1 reached end of software maintenance on February 13, 2010. Customers who are using Cisco Unified Communications Manager 5.x versions should contact your Cisco support team for assistance in upgrading to a supported version of Cisco Unified Communications Manager.
Products Confirmed Not Vulnerable
+--------------------------------
Cisco Unified Communications Manager version 4.x is not affected by these vulnerabilities. No other Cisco products are currently known to be affected by these vulnerabilities.
Cisco Security Advisory: Cisco Wireless LAN Controllers Denial of Service Vulnerability
Document ID: 112916
Advisory ID: cisco-sa-20110427-wlc
Revision 1.0
For Public Release 2011 April 27 1600 UTC (GMT)
+---------------------------------------------------------------------
Summary
=======
The Cisco Wireless LAN Controller (WLC) product family is affected by a denial of service (DoS) vulnerability where an unauthenticated
attacker could cause a device reload by sending a series of ICMP packets.
Cisco has released free software updates that address this vulnerability.
There are no available workarounds to mitigate this vulnerability.
This advisory is posted at
http://www.cisco.com/warp/public/707/cisco-sa-20110427-wlc.shtml
Affected Products
=================
Vulnerable Products
+------------------
This vulnerability affects Cisco WLC software versions 6.0 and later. The following products are affected by the vulnerability described in
this Security Advisory:
* Cisco 2100 Series Wireless LAN Controllers
* Cisco WLC526 Mobility Express Controller (AIR-WLC526-K9)
* Cisco NME-AIR-WLC Modules for Integrated Services Routers (ISRs)
* Cisco NM-AIR-WLC Modules for Integrated Services Routers (ISRs)
Note: The Cisco NM-AIR-WLC have reached End-of-Life and End-of-Software Maintenance. Please refer to the following
document for more information:
http://www.cisco.com/en/US/prod/collateral/modules/ps2797/prod_end-of-life_notice0900aecd806aeb34.html
Chris Mohan --- Internet Storm Center Handler on Duty
0 Comments
Is the Insider Threat Really Over?
There has been a bit of press lately about how external threats are overtaking internal threats in the near term. Traditionally it has been viewed that internal threats (i.e. disgruntled employees) pose a greater threat to an organization than outsiders. In reality, the lines are blurring but external attackers are becoming more sophisticated in their attacks. That said, I was made aware by a coworker of an interesting controversy emerging from South Korea. In essence, one of their major banks was offline and unable to process any transactions for several days. Around April 12, customers were unable to perform ATM transactions, online transactions or any in-bank transactions for about a day. For several days afterwards, transaction were highly unreliable. In essence, this bank (Nongyhup Bank, NH Bank) basically suffered a catastrophic system failure.
According to reports, a contractor from IBM had his laptop infected, which in turn successfully attacked about 60% of the banks infrastructure and crippled its ability to do business. The running controversy is whether this was an insider attack or someone who compromised a contractor and used as used it as a beach-head to get into the bank. That investigation is playing out and we'll see where that goes. From what I can tell (and that's limited because... well... I don't speak Korean) there was a contractor's laptop that was compromised, Chinese IP addresses were involved (and for those of you who know the geopolitical history know that is entirely unsurprising) and there are 300,000 some odd complaints about people not being able to get their money who are in various states of non-pleased.
Like I said, the investigation is ongoing and who knows what really will happen.
Disclaimers aside, my first thought was the IMF incident which ultimately led to the spectacular collapse of Satyam. Maybe that's not the case here, but I do know when I've applied for contractor positions at pretty big firms, I've been appalled by how easy it would be to game the system and, for that matter, how easy the system has been gamed.
In this particular case, there has been a non-trivial amount of incidents that should have served as a warning sign for internal controls. My personal favorite expression regarding the failures of this bank and how they responded (after it became catastrophic) is that they started a 2011 training session with "a highly critical self-reflection and atonement". Maybe I'm odd, I find that expression humorous.
Ultimately, organizations security is determined by who it trusts to run the shop. If all you do is a phone screen (which may or may not be the actual person who is going to start the job the following Monday), you may be asking for trouble.
What are your thoughts? How important is it to consider the insider threat and to vet your contractors and employees?
Background:
IEEE: South Korean NH Bank's Week-Long System Failure That Affected 30 Million An Inside Job?
Korea Times: Chinese IPs linked to Nonghyup crash
The Dong-A-Ilbo: `Nonghyup Bank averaged 2 financial accidents per month`
--
John Bambenek
bambenek at gmail /dot/ com
Bambenek Consulting
7 Comments
Sony PlayStation Network Outage - Day 5
The Sony PlayStation Network and Qriocity service have been down since Wednesday the 20th. Sony is still working on bringing them back online. Sony is communicating regularly on this - you can find their original and current updates here:
http://blog.us.playstation.com/2011/04/22/update-on-playstation-network-qriocity-services/
and
http://blog.us.playstation.com/2011/04/25/psn-update/
Reading between the lines, they seem to be following the methodology for Incident Response, commonly phrased in these steps that I learned in SEC504:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons Learned
Given that we're a number of days in, I hope that they are working on later phases of Eradication, making sure that the original attack vector is taken care of so that once they bring the service back online they won't see a recurrance of the event.
Hats off to them - they're doing all the right things, and communicating regularly with their client community as they do it ! I feel for them, given the length of the outage though.
===============
Rob VandenBrink
Metafore
15 Comments
What's Your (IP) Address Worth?
Now that we're officially out of IPv4 addresses, a new marketplace has sprung up to buy and sell them (or rather, to broker transfers from one organization to another with dollar figures attached). Sites like www.depository.net, www.addrex.net and www.tradeipv4.com look like they'll be with us for a while.
Having said that, ARIN.NET continues to administer all transfers in North America (US, Canada and parts of the Caribbean), including transfers of addresses that were allocated by Internic, back before ARIN.NET existed (https://www.arin.net/about_us/media/releases/20110330.html). This is a good thing, since most ISPs won't route for an address block unless the registration is correct at the appropriate RIR (Regional Internet Registry ==> https://www.arin.net/knowledge/rirs.html)
I can't personally vouch for any of these sites. As always, evaluate the reputation of sites you do business on, and this certainly counts as business transactions! It's also important to run any transfer of address space through the RIR that has authority in your jurisdiction. You don't want to find that the addresses you thought you had are not in fact yours!
===============
Rob VandenBrink
Metafore
0 Comments
Image search can lead to malware download
Reader Stephanie told us that during an image search of a Mussolini image in google found a site downloading malware. I decided to look into this issue further to see what I could find. Before starting, please be careful on what you do, as this page is still alive.
I clicked the image found in google. The following script was received from the host:
The URL loads the following javascript, which is coded:
After decoding, it rises an executable, MD5 ef42a441af5e5a250f18aeb089698c35. It does not perform any changes to the system, but it connects to 69.50.197.243 TCP port 8000 to further download for malware content.
Such attacks are common. How to minimize the risk of these attacks? We can summarize some controls:
- Malware perimeter defense: You can use any malware product to test HTTP, FTP and any other protocol allowed for the inside users.
- Please download files from well-known sites. If you need to download something from unknown sites, please take all measures to check and review the downloaded content before using it.
- I tested noscript against this webpage and it was correctly blocked. I do not recall a similar control for Internet Explorer. Maybe one of our readers can recommend one?
- Host IPS can protect the machine for buffer overflow or similar attacks triggered by exploits or malware.
- And, of course, the Antivirus.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
8 Comments
iPhoneMap: iPhoneTracker port to Linux
Remember the news about iPhone recording all the places where it goes? iPhoneTracker was developed to map the information when the iPhone is synchronized to a OSX machine. Handler Bojan ported it to Linux and named it iPhoneMap. I tested it myself on cygwin and works perfect.
You need to install the DBD-SQLite and DBI perl modules before executing the application. After the installation, go to C:\Users\<your user name>\AppData\Roaming\Apple Computer\MobileSync\Backup. You will find a directory about 41 chars long very similar to a SHA1 hash. Go inside that directory and execute inside the find_sqlite.py script. It will get you the name containing the GPS stored information. After that, issue the following command:
If you open your index.html file with your favorite browser, you will see a map like this one:
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
1 Comments
In-house developed applications: The constant headache for the information security officer
Although perimeter security controls are well publicized, there are many suppliers who can offer them in different countries and these devices can fit into all types of budgets, there are still security problems in custom applications developed within companies that are not so easily solved.
In the modern corporate world, the immediacy of business is a predominant feature. For people responsible for computer security is a challenge because we need to find a balance between the needs required by business, the solution time and the risks that the company can tolerate in information assets.
This week we were dealing with an incident relating to unauthorized access and information leakage of a web application. When we analyzed the logs of the IPS, we find the following:
This pattern is repeated continuously with a number of web pages that make up the application. All request were successfully served. I made the following questions:
- Where is the check for the tag "Referer"? Although this tag is very easy to spoof using any intermediate proxy used in vulnerability analysis, works enough to embarrass people that downloads the webpage on their computers, modify the HTML source to modify the parameters for the forms actions and from the page stored continue their transactions.
- Where is the session id issued by Tomcat for this HTTP request? I asked what happened to the Tomcat configuration for requesting sessions when different servlet invoked. Natural behavior that I expected to see was a redirect to the homepage to request username and password. Response received was that the functionality was not implemented because the business was waiting for an urgent application to come out with a public campaign and that this functionality would be covered once the campaign ended.
- The previous response I received made me raise another question: Is session timeout implemented? I received the same answer: It was not implemented for the same reasons outlined above.
We found other repeated pattern of packets, which turned out to be the root cause of the incident:
Someone with interactive access to the server could upload a modified servlet, which the attacker invoked in the HTTP request and then it was possible to modify and retrieve information from the application.
The lessons learned from the case are as follows:
- Periodically review the information security baseline measures of security for computers that make up the IT infrastructure of your company and verify that all the devices have them in their own settings. In case any of them can not have it implemented, document and minimize the risk with another control.
- Do not skip the normal process of software development, especially those steps involving functional testing and security testing. Any error that presents in production will be far more costly than to discover and correct it before posting the application to users.
- According to the authentication means, the risks of information assets and security controls are in place at your company, define a security architecture for applications that include the method for input data validation, internal processing control, message integrity, validation of the output data, data encryption, file security and system audit logs.
- Although you may become victim of a gang of cyber criminals looking to commit the information and finance business, the vast majority of incidents are presented by vulnerabilities that are well documented, that common people are well-aware of and become materialized because carelessness when implementing IT solutions for business.
- It is clear that security measures can never be an obstacle to achieving business goals, but keep in mind that business goals can be seriously affected by the fault or negligence in the implementation of information security controls.
-- Manuel Humberto Santander Peláez | http://twitter.com/manuelsantander | http://manuel.santander.name | msantand at isc dot sans dot org
1 Comments
Adobe Reader and Acrobat Security Updates
Adobe released important security updates for Adobe Reader X (10.0.2) and earlier 10.x and 9.x versions for Windows and Macintosh OS. The bulletin is posted here.
"CVE-2011-0611, is being actively exploited in the wild against both Adobe Flash Player, and Adobe Reader and Acrobat, as well as via a Flash (.swf) file embedded in a Microsoft Word (.doc) or Microsoft Excel (.xls) file delivered as an email attachment targeting the Windows platform. Adobe Reader X Protected Mode mitigations would prevent an exploit of this kind from executing."[1]
Affected software:
Adobe Reader X (10.0.1) and earlier versions for Windows
Adobe Reader X (10.0.2) and earlier versions for Macintosh
Adobe Acrobat X (10.0.2) and earlier versions for Windows and Macintosh
NOTE: Adobe Reader 9.x for UNIX, Adobe Reader for Android, and Adobe Reader and Acrobat 8.x are not affected by CVE-2011-0611.
[1] http://www.adobe.com/support/security/bulletins/apsb11-08.html
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
5 Comments
Silverlight Update Available
Microsoft has issued a security patch for Silverlight KB2526954. It fixes several security issues. However, the Microsoft link to KB2526954 is still not live. If you have Microsoft update running, it is ready to install. This is rated as important and will auto install.
Direct download http://go.microsoft.com/fwlink/?LinkID=149156
[1] http://www.microsoft.com/getsilverlight/Get-Started/Install/Default.aspx
-----------
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot edu
2 Comments
Virustotal.com hiccup
Yes, Virustotal.com appears to be down and/or not resolve correctly in DNS at the moment.
4 Comments
iPhone GPS Data Storage
We received a number of comments regarding the release of the iPhone tracker [1], a tool which plots geo location data stored in iOS backups. All iOS devices (iPhone as well as iPad) will accumulate location information over time, and store it as part of backup files. The iPhone tracker will read this file and plot the information.
However, this information is not sent to any remote sides (at least not that this is known so far). Mobile operators may of course keep their own geo location data. As a simple counter measure, it is recommended to encrypt backups using a strong password.
And of course yet more interesting data for mobile forensics.
[1] http://petewarden.github.com/iPhoneTracker
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
6 Comments
Data Breach Investigations Report published by Verizon
Verizon have published their comprehensive annual breach investigations report today. Their analysis makes for interesting reading, for example they point out that a whopping 86% of breaches were discovered by outside third parties, and not by the victim organization internally. The chart on top of page 55/56 in the report shows, quite compellingly, the average time spans between "intrusion" and "compromise", as well as between "compromise" and "discovery". The former is in minutes to days, the latter in weeks to months. As for the cause of the breaches: "Exploitation of default or guessable credentials" is in the top three. Kinda where Cliff Stoll was already at, 20 years ago.
0 Comments
SQL injection: why can’t we learn?
Recently we have been all witnesses of two high profile incidents where the attackers exploited SQL injection vulnerabilities: the now infamous HBGary Federal hack and the Barracuda Networks hack. What’s even more worrying about these two incidents is that they happened to companies which are information security consultants/product developers.
SQL injection vulnerabilities have really been around for ages – the first reference I can remember of was Rain Forest Puppy’s article for Phrack 54 “NT Web Technology Vulnerabilities” that was published back in 1998 (yes – SQL injection is almost 13 years old!). However, as we can see from the examples that happened recently (and from many other cases – just take a look at the mass SQL injection attacks that are performed automatically by malware these days) SQL injection vulnerabilities are unfortunately here to stay.
During my penetration testing engagements I often see various frameworks that are being used to develop web applications. These frameworks are really more and more advanced these days and can in many cases automatically protect the application against common attacks such as SQL Injection or Cross Site Scripting.
While this is good and frameworks definitely help make applications more secure (note that I didn’t say secure), one thing that I always like to stress out to developers that they should still pay attention to all these vulnerabilities. If nothing else, you never know if your application will end up on a server that will have a different or misconfigured version of the framework you used which will suddenly make your application vulnerable!
Another thing to keep in mind is that web application firewalls aren’t almighty. While they can do a good job, I’ve also seen too many misconfigured WAF products that were easy to bypass. The web technology is developing quickly and if you don’t keep up with it, it is quite possible that in 6 months a new attack/language/whatever will be introduced that will allow one to bypass your (old) WAF. Take Adobe Flash for example – not only for client side vulnerabilities – but also for attacks such as Cross Site Flashing that are more and more common.
So are the bad guys any better? Unfortunately, the answer is YES. When I get my hands on, I always try to analyze server side scripts that the bad guys use – these are usually scripts running on their C&C servers that help them control infected machine, issue and schedule tasks and so on.
While previously we were seeing all kinds of bad code (both bad looking and full of vulnerabilities), today I can unfortunately say that the bad guys have much improved their game. Below you can see an excerpt of a server side script used by some malware. It’s in PHP (the most popular platform for bad guys) and besides being nice and easy to read, notice how they nicely used the addslashes() call on all variables to make sure that any occurrence of a single quote, double quote, backslash and NULL byte characters is properly escaped.
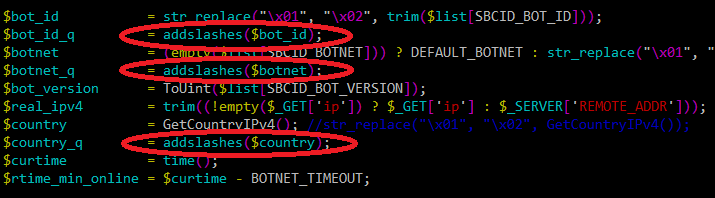
So, if the bad guys can do it, we should be better to – so please use couple of minutes to educate your developers about the dangers of writing insecure code.
--
Bojan
INFIGO IS
4 Comments
Wordpress.com Security Breach
Wordpress reported mid last week that they suffered a compromise that involved an attacker getting root access to some of their servers. They haven't released much in the way of specifics of what has happened but indicate that usernames and passwords could have been compromised for those with accounts with the Wordpress site itself (as distinct from people who simply run Wordpress to power blogs on their on systems). This, once again, brings to the fore the need of using strong passwords for online sites and for using unique passwords for each site.
The bigger issue, however, is with the multiplicity of online sites and social media, the amount of accounts that individuals needs to maintain is vast. I counted my own list of accounts and just for the non-professional ones, I have 23 or so logins. Strong passwords help (particularly if they are over 12 characters) but there becomes the problem of remembering them all. Combine that with the fact most online sites use the "e-mail address" as the username, there is a big problem.
What mitigates this is deployment of decentralized authentication and OpenID is a good example. At that point, a user can keep a strong password in one place (and even better, use two-factor authentication) that is trusted. As far as I can tell, Wordpress.com doesn't allow OpenID to register a blog but can be set up if you maintain your own wordpress installation. The takeaway is, if you run an interactive online website, investigate using OpenID to register & authorize users. If you get breached, you no longer have a password that can be stolen to assume someone's online identity.
For users, where you can, use OpenID (or similar) schemes that let you maintain your online identity in one place. Facebook and twitter have similar features if you don't mind giving those companies the ability to data-mine what sites you interact with. Many sites still need you to create an account with a password before you can switch to OpenID. In that case, create the account, set up OpenID, then change the password to be strong and long and store it somewhere safe (in the off chance you need the actual password some day). A malicious individual still could "proxy" off an existing session and do bad things if they already compromised your PC, but you would not have to worry about the mass compromises that have hit Wordpress, Gawker and others recently.
--
John Bambenek
bambenek at gmail /dot/ com
Bambenek Consulting
7 Comments
Oracle Patch Update Pre-Release Announcement
On Tuesday, April 19, 2011, Oracle plans to release a collection of patches as a part of their Critical Patch Update. This Patch Update contains fixes across hundreds of their products and corrects some 73 new security vulnerabilities. Please take a look at the Pre-Release Announcement located at Oracle, and start planning your patch management strategy for your organization.
www.oracle.com/technetwork/topics/security/cpuapr2011-301950.html
Scott Fendley ISC Handler
0 Comments
New Versions of Wireshark released
Earlier today, Wireshark announced the release of a new stable and old-stable versions of this versatile network protocol analysis tool used heavily in the networking and security community. The new version corrects many bugs including a potential remote code execution vulnerability. As always, it is recommended that you update any computers you use for packet analysis or capturing.
More information is available at :
www.wireshark.org/lists/wireshark-announce/201104/msg00001.html
www.wireshark.org/lists/wireshark-announce/201104/msg00002.html
Scott Fendley
ISC Handler On Duty
0 Comments
MS11-020 (KB2508429) Upgrading from Critical to PATCH NOW
Based on notifications received from Microsoft we are upgrading the rating of MS11-020 (KB 2508429, CVE-2011-0661) from Critical to PATCH NOW. See: http://isc.sans.edu/diary.html?storyid=10693 for the full table.
The Remote Code Exploit is possible without authentication, so this presents a serious risk to internal networks. Think Downadup/Conficker, or think lateral movement if that will help motivate patching.
Also note that this patch requires a reboot of your system.
Sorry.
-KL
8 Comments
Sysinternals updates, a new blog post, and webcast
Process Monitor v2.95, TCPView v3.04, Autoruns v10.07 have updates here [1]
Of equal interest as the tools update is Part 1 of an analysis of a Stuxnet infection with Sysinternals tools here [2]
[1] http://blogs.technet.com/b/sysinternals/archive/2011/04/13/updates-process-monitor-v2-95-tcpview-v3-04-autoruns-v10-07-and-a-new-blog-post-and-webcast-from-mark.aspx
[2] http://blogs.technet.com/b/markrussinovich/archive/2011/03/30/3416253.aspx
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
1 Comments
Apple Security Patches for OS X and iOS
Unlike Microsoft, Apple has so far not committed to a regular patch cycle, and today's release of IOS 4.3.2 as well as the OS X Security Update 2011-002 came somewhat as a surprise. [1]
Both include security fixes that should be applied rather sooner then later. The OS X update also includes Safari 5.0.5 . We will update this diary once the Apple support page with security details is live.
The patch is pretty small compared to other Apple patches (about 4 MB). You need to restart your system after applying the security patch. I applied it to one system with PGP full disk encryption, and so far no ill effects.
[1] http://support.apple.com/kb/DL1376
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
dshield.org now DNSSEC signed via .org
To coincide with today's webcast about DNSSEC [1], I changed how the dshield.org zone is DNSSEC signed. The zone itself has been signed for a while now, but I used "look aside validation" via isc.org . For a few months now, it has been possible to have .org zones directly signed by .org, and I decided to give it a try. Please let me know if you see any issues. If you plan to deploy DNSSEC yourself, see Verisign's [3] nice testing tool as well as the visualization tool by DNSVIZ [4].
[1] https://www.sans.org/webcasts/isc-threat-update-20110413-94083
[2] http://dlv.isc.org
[3] http://dnssec-debugger.verisignlabs.com
[4] http://dnsviz.net/d/dshield.org/dnssec/
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
Update to Adobe Flash 0-day: Patch will be out soon
Adobe updated its advisory, stating that we should have a patch at least for the "non sandbox" versions of Adobe Acrobat and Reader by April 25th [1]. Flash player will get a fix even earlier (April 15th = this week Friday). Adobe Reader X for Windows, which uses the new "Protected Mode" feature to limited the exploitability of this vulnerability, will have to wait until June 14th.
Little Table to clarify:
| Flash | Reader 9 | Reader 10.x | Reader 10.0.1 | Reader 10.0.2 aka "X" | |
| Windows | 4/15 | 4/25 | 4/25 | 4/25 | 6/14 |
| Macintosh | 4/15 | 4/25 | 4/25 | 4/25 | 4/25 |
for more details, see the URL below.
[1] http://www.adobe.com/support/security/advisories/apsa11-02.html
Update: corrected patch date for Adobe Reader X for Windows. Was 6/25.. but should have been 6/14. Thanks Luc for pointing this out to me!)
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
1 Comments
Yet another Adobe Flash/Reader/Acrobat 0 day
Adobe released that a so far unpatched vulnerability has been used in recent targeted attacks.
Flash Player 10.2.153.1 is vulnerable, as is the flash player component used to execute flash in Adobe Reader / Acrobat. Adobe Reader X is vulnerable bu but not exploitable.
At this time, according to Adobe, the attack is performed using Flash files embedded in Word documents.
Note that Flash may be embedded in other Office document formats like Excel. Adobe is not planning on an out of band patch at this point, as Adobe Reader X is not exploitable.
[1] http://www.adobe.com/support/security/advisories/apsa11-02.html
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
10 Comments
April 2011 Microsoft Black Tuesday Summary
Here are the April 2011 Black Tuesday patches. Enjoy!
Overview of the April 2011 Microsoft Patches and their status.
| # | Affected | Contra Indications | Known Exploits | Microsoft rating | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS11-018 | Cumulative Security Update for Internet Explorer ( Replaces MS11-003 ) | |||||
| Internet Explorer 6-8 CVE-2011-0094 CVE-2011-0346 CVE-2011-1244 CVE-2011-1245 CVE-2011-1345 |
KB 2497640 | No Known Exploits. | Severity:Critical Exploitability: 1,1,?,3,1 |
Critical | Critical | |
| MS11-019 | Vulnerabilities in SMB Client Could Allow Remote Code Execution ( Replaces MS10-020 ) | |||||
| Windows CVE-2011-0654 CVE-2011-0660 |
KB 2511455 | No Known Exploits. | Severity:Critical Exploitability: 2,1 |
Critical | Critical | |
| MS11-020 | Vulnerability in SMB Server Could Allow Remote Code Execution ( Replaces MS10-012 MS10-054 ) | |||||
| Windows CVE-2011-0661 |
KB 2508429 | No Known Exploits. | Severity:Critical Exploitability: 1 |
Critical | Critical | |
| MS11-021 | Vulnerabilities in Microsoft Excel Could Allow Remote Code Execution ( Replaces MS10-080 MS10-087 ) | |||||
| Office XP SP3-2010, Office 2004-2011 for Mac, Open XML File Format Converter, Excel Viewer SP2, Office Compatibility Pack for 2007 file formats CVE-2011-0097 CVE-2011-0098 CVE-2011-0101 CVE-2011-0103 CVE-2011-0104 CVE-2011-0105 CVE-2011-0978 CVE-2011-0979 CVE-2011-0980 |
KB 2489279 | No Known Exploits. | Severity:Important Exploitability: 1,1,1,2,2,2,1,1,1 |
Important | Important | |
| MS11-022 | Vulnerabilities in Microsoft PowerPoint Could Allow Remote Code Execution ( Replaces MS09-017 MS10-036 MS10-087 MS10-088 ) | |||||
| PowerPoint CVE-2011-0655 CVE-2011-0656 CVE-2011-0976 |
KB 2489283 | No Known Exploits. | Severity:Important Exploitability: 2,2,1 |
Important | Important | |
| MS11-023 | Vulnerabilities in Microsoft Office Could Allow Remote Code Execution ( Replaces MS10-087 ) | |||||
| Office XP - 2007, Office 2004 - 2008 for Mac, Open XML File Format Converter CVE-2011-0107 CVE-2011-0977 |
KB 2489293 | POC Available. | Severity:Important Exploitability: 1,2 |
Important | Important | |
| MS11-024 | Vulnerability in Windows Fax Cover Page Editor Could Allow Remote Code Execution | |||||
| Fax Services, Fax Server Role CVE-2010-3974 |
KB 2527308 | POC Available. | Severity:Important Exploitability: 3 |
Critical | Important | |
| MS11-025 | Vulnerability in Microsoft Foundation Class (MFC) Library Could Allow Remote Code Execution | |||||
| Visual Studio .NET 2003 - 2010, Visual C++ 2005 - 2010 Redistributable Package CVE-2010-3190 |
KB 2500212 | No Known Exploits. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS11-026 | Vulnerability in MHTML Could Allow Information Disclosure | |||||
| MHTML CVE-2011-0096 |
KB 2503658 | ACTIVELY EXPLOITED. | Severity:Important Exploitability: 3 |
PATCH NOW! | Important | |
| MS11-027 | Cumulative Security Update of ActiveX Kill Bits ( Replaces MS10-034 ) | |||||
| Windows XP- 7, Server 2003-2008 CVE-2010-0811 CVE-2010-3973 CVE-2011-1243 |
KB 2508272 | POC Available. | Severity:Critical Exploitability: ?,?,? |
Critical | Critical | |
| MS11-028 | Vulnerability in .NET Framework Could Allow Remote Code Execution ( Replaces MS09-061 MS10-060 MS10-077 ) | |||||
| .NET framework (all supported version) CVE-2010-3958 |
KB 2484015 | No Known Exploits. | Severity:Critical Exploitability: 1 |
Critical | Critical | |
| MS11-029 | Vulnerability in GDI+ Could Allow Remote Code Execution ( Replaces MS09-062 MS10-087 ) | |||||
| Windows XP-Vista, Windows Server 2003-2008, Office XP CVE-2011-0041 |
KB 2489979 | No Known Exploits. | Severity:Critical Exploitability: 1 |
Critical | Critical | |
| MS11-030 | Vulnerability in DNS Resolution Could Allow Remote Code Execution ( Replaces MS08-020 MS08-037 MS08-066 ) | |||||
| Windows XP - 7, Windows Server 2008 CVE-2011-0657 |
KB 2509553 | No Known Exploits. | Severity:Critical Exploitability: 2 |
Critical | Critical | |
| MS11-031 | Vulnerability in JScript and VBScript Scripting Engines Could Allow Remote Code Execution ( Replaces MS09-045 MS10-022 MS11-009 ) | |||||
| OpenType Compact Font Format (CFF) driver CVE-2011-0663 |
KB 2514666 | No Known Exploits. | Severity:Critical Exploitability: 2 |
Critical | Important | |
| MS11-032 | Vulnerability in the OpenType Compact Font Format (CFF) Driver Could Allow Remote Code Execution ( Replaces MS11-007 ) | |||||
| OpenType Compact Font Format (CFF) driver CVE-2011-0034 |
KB 2507618 | No Known Exploits. | Severity:Critical Exploitability: 3 |
Critical | Important | |
| MS11-033 | Vulnerability in WordPad Text Converters Could Allow Remote Code Execution ( Replaces MS10-067 ) | |||||
| Microsoft Wordpad CVE-2011-0028 |
KB 2485663 | No Known Exploits. | Severity:Important Exploitability: 1 |
Important | Important | |
| MS11-034 | Elevation of Privilege Vulnerabilities in Windows Kernel-Mode Drivers (Replaces MS10-012 ) | |||||
| Kernel Mode Drivers CVE-2011-0662 CVE-2011-0665 CVE-2011-0666 CVE-2011-0667 CVE-2011-0670 CVE-2011-0671 CVE-2011-0672 CVE-2011-0673 CVE-2011-0674 CVE-2011-0675 CVE-2011-0676 CVE-2011-0677 CVE-2011-1225 CVE-2011-1226 CVE-2011-1227 CVE-2011-1228 CVE-2011-1229 CVE-2011-1230 CVE-2011-1231 CVE-2011-1232 CVE-2011-1233 CVE-2011-1234 CVE-2011-1235 CVE-2011-1236 CVE-2011-1237 CVE-2011-1238 CVE-2011-1239 CVE-2011-1240 CVE-2011-1241 CVE-2011-1242 |
KB 2506223 | No Known Exploits. | Severity:Important Exploitability: 1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,2,1,1,1,3,1,1,1,1 |
Important | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
SANS SEC401 coming to central OH in May, see http://www.sans.org/mentor/details.php?nid=24678
16 Comments
Layer 2 DoS and other IPv6 Tricks
IPv6, just like IPv4, is a layer 3 (Network Layer) protocol. However, it does depend on Layer 2 (Link Layer) to reach the next hop. Historically, Layer 2 has been a fertile attack breeding ground. Layer 2 protocols like Ethernet do not address these security issues and are build to be lightweight rather then secure. The assumption is that physical access to the network is restricted, and with that physical access controls can be used to mitigate most Layer 2 risks.
Of course, this hasn't been true for most networks. Wireless access, access to unsecured network jacks in public areas and even remote access via compromised hosts inside the network have been shown to provide access to layer 2. 802.1x is probably the best option to mitigate most of these threats, but even 802.1x will not protect you from a compromised authenticated workstation, and 802.1x can be difficult to implement in many scenarios.
So how does this all apply to IPv6? One of the big changes in IPv6 is that ARP is replaced with the Neighbor Discovery Protocol (NDP). NDP is based on ICMPv6. In addition, Router Advertisements (RA) are used to configure hosts.
Probably the most important thing to understand: Neither NDP or RA prevent by default any attacks we have seen against ARP or DHCP. Just like for ARP and DHCP, we need to be able to detect and mitigate spoofing.
NDP Spoofing
By default, NDP messages are not authenticated, just like ARP is not authenticated. In its simplest form, we can use the NDP to impersonate a legitimate host on the local network to play man in the middle (MITM). MITM attacks work and can be applied just like with IPv4
Variations of the attack can be used in denial of service as well. Just like for IPv4, an IPv6 host will check if the address it is about to use is already used. By just responding to these checks ("gratuitous ARP" in IPv4), we are able to to prevent a host from obtaining an address.
RA Spoofing
The RA protocol replaces DHCP in many cases and can be used to assign IP addresses. Spoofing router advertisements can help with MITM attacks as the attack is now pretending to be a router. In a regular IPv6 network, this may only be partially successful as the rogue router is competing with legitimate routers. But by assigning itself a high priority and creating a DoS against the legitimate router, the attack has a decent chance of succeeding.
Recently (see a few diaries back), this attack was demonstrated against IPv4 networks by combining it with NAT-PT and the preference of current operating systems to route over IPv6 if both IPv4 and IPv6 are available.
Of course, if you just spoof random RA, you will be able to mess up hosts sufficiently to stop responding at all.
Attack Tools
There is probably at least one tweet/slashdot/digg "event" a day advertising a new tool to implement these attacks. To save yourself some time: Check out the THC IPv6 attack library. It already implements a lot of these tools including a nice library to implement more. Implementing the same tools again in scappy gets you some python brownie points though.
Defenses
For the IPv4 versions of these attacks, many vendors implemented defenses, and there are open source tools like arpwatch to help you detect these attacks. In addition, we have just gotten used to watching out for these attacks and a reasonably skilled network admin is usually able to spot ARP spoofing.
For IPv6, we are a bit behind the curve when it comes to defenses. RFC 6105 outlines a mechanism calls "RA Guard" [1] that can be used to identify legitimate routers and only allow RA messages from switch ports connected to authorized routers, just like we are used to when configuring DHCP Snooping.
RFC3971 defines a mechanism called "SEND" (Secure Neighbor Discovery" which uses PKI to sign ND messages. In addition, cryptographically generated addresses (CGA) are used to avoid spoofing on the local network. However, this protocol is not yet widely implemented and the overhead associated with it can cause DoS conditions itself.
Unlike ARP messages, the ICMPv6 messages could be routed. However, a host is not supposed to accept any ND or RA message with a TTL of less then 255.
Summary
Layer 2 defense is not easy. In particular defending against DoS. The best thing you can probably do is to know what's supposed to be on your network, and be able to quickly detect and disconnect misbehaving hosts.
[1] http://tools.ietf.org/rfc/rfc6105.txt
[2] http://tools.ietf.org/rfc/rfc3971.txt
[3] http://tools.ietf.org/rfc/rfc3972.txt
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
2 Comments
GMail User Using 2FA Warned of Access From China
A few months ago, after the infamous "Aurora" attack, it became known that GMail accounts are under active attack from entities in China. In response, Google added a warning banner to its GMail accounts notifying users if someone logged into the account from China recently.
We had one user reporting such an incident, and are wondering if others have seen this warning recently. This user did use Google's two factor authentication, which is of course in particular concerning.
What security precautions do you take if you use GMail? Do you archive/delete old email? Any scripts you use for it that you could share? Do you use Google's two factor authentication?
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
10 Comments
Recent security enhancements in web browsers (e.g. Google Chrome)
About a couple of weeks ago we talked about the new Firefox 4 security features. Today is Google's Chrome turn, due to the recently added and short term upcoming security features:
- Malicious downloads protection: Making use of Google's Safe Browsing API, Chrome will warn users when trying to download a suspected malicious executable file (starting with Windows executables, .exe) . URL: http://googleonlinesecurity.blogspot.com/2011/04/protecting-users-from-malicious.html
- Out-of-date browser plug-ins warnings: The latest Chrome version automatically warns users about any out-of-date plug-ins when they access a web page that requires a plug-in that’s not current. By default the plug-in won't run and the user will see a message to get the latest version of the plug-in. This complements the granular plug-ín blocking capabilities added to Chrome 10. URL: http://googleonlinesecurity.blogspot.com/2011/03/chrome-warns-users-of-out-of-date.html
- Due to the recent CA compromises, once again, the trustworhtiness on the Internet PKI (SSL/TLS digital certificates) is under evaluation. Some initiatives, based on digital certificate reputation services or, at the end, on DNSSEC are moving forward. URL: http://googleonlinesecurity.blogspot.com/2011/04/improving-ssl-certificate-security.html or Perspectives.
With no doubt, web browser and plug-ins security are crucial for a trusted Internet and Web browsing experience, thus improvements in this field are always welcomed.
Without entering into the web browsers wars (or debate ;) to declare which one is the best one (...all them are pieces of software), I honestly recommend you to use (or at least have handy) a few of them and use them for different purposes. Some (the web browsers you trust more) should be used for casual browsing, running in a restrictive mode (NoScript, HTTPS Everywhere, disabling plug-ins, etc) to offer you the best protection. Others should only be used for critical browsing to confidential and sensitive sites. All them are going to become victims (again) of vulnerabilities in the future, so having multiple alternatives will help you to accommodate 0-days and unpatched flaws while still be able to securely (if possible) browse the web.
In any case, always use the latest and most updated version of any web browser (with all the available plug-in updates applied): Firefox 4, Internet Explorer 9, Chrome 10, Opera 11, or Safari 5.
----
Raul Siles
Founder and Senior Security Analyst with Taddong
www.taddong.com
0 Comments
Pros and Cons of "Secure" Wi-Fi Access
Recently I have been involved in a couple of initiatives that addressed Wi-Fi security as one of their main topics. One of them is the upcoming SANS April OUCH issue, focused on "Staying Secure Online when Traveling". The main constraint associated to user awareness programs is the length limitation on the information shared with users, requiring very clear, simple, and direct messages.
Secure Wi-Fi access awareness is a key component of overall user security nowadays, as most users (if not all) connect daily to one or multiple Wi-Fi networks from their laptops, smartphones, tables, and other mobile (personal and professional) devices.
Fortunately, the ISC audience shares a very technical profile, so it becomes the proper forum to go into the technical and security-related details of how Wi-Fi networks are used today worldwide by users, identify areas of improvement, suggest current and future solutions, and take actions.
Although most ISC readers widely accept that WEP is insecure, aware of well known vulnerabilities since year 2001 and knowing it is possible to get the WEP key in less than a minute (or less) since April 2007, still today lots of vendors and service providers deliver their Wi-Fi equipment (Wi-FI access points) configured by default widely open or with WEP (case 0). Besides that, the fact that WEP makes use of a secret key creates a false sense of security on end users, assuming that if there is a secret key involved... it must be secure.
There are three types of Wi-Fi scenarios users commonly connect to:
- A Wi-Fi personal or corporate network, properly secured and configured through WPA2/AES Personal (PSK) or Enterprise, using a robust pre-shared key or the right EAP types and recommended EAP client settings. This kind of network can be considered secure.
- An open or insecure public Wi-Fi network (or Wi-Fi hotspot), using no security at all, WEP, or an easy to guess WPA/WPA2 pre-shared key, where anyone (even external entities) can easily capture and manipulate the traffic from legitimate users. This kind of network is considered insecure.
- A public Wi-Fi network (or Wi-Fi hotspot) properly secured and configured through WPA2/AES Personal (PSK), using a robust pre-shared key. Similar to case 1 but public. This kind of network is considered... secure by most users... although it depends of your Wi-Fi security insight (read below).
A forth very common case all over the world, although we are not going to pay a lot of attention to, is the illegitimate usage of a third party or neighbor unprotected Wi-Fi network without authorization. The "free" access can turn against the unauthorized user, as the owner of the network, as well as other users, can monitor and manipulate the user activities. The saving costs of using a piggybacked connection won't compensate the associated security risks.
There are very simple and common sense options to mitigate some of the different weaknesses and scenarios previously mentioned (identified by case #), while some others are mitigated using additional security layers that not always offer proper protections. Let's analyze pros and cons of the most common scenarios and security practices used today when connecting to all kinds of Wi-Fi networks:
- Case 0: Wi-Fi vendors and service providers must deliver the Wi-Fi equipment configured by default with WPA2/AES-PSK (this could be a reality starting this year; see slides # 44 and 45 of my 2010 GOVCERTL.NL presentation) using a long enough (the IEEE specification says that at least it should have +20 characters) and random enough secret key (pre-shared key), not based on other equipment details (such as the SSID or MAC address, BSSID). The best option would be not to provide a default pre-sahred key at all, and force users to select a custom robust key at installation or deployment time, or force the usage of Wi-Fi Protected Set-up (WPS).
- Case 1: On a secure personal or corporate Wi-Fi network it is assumed that all users within the network are trusted (Please, do not forget about insider threats). In this scenario, it is particularly relevant to monitor the network through a WIDS (Wi-Fi Intrusion Detection System) and ensure the legitimate Wi-Fi client settings are secure and properly configured (including the management of the PNL, Preferred Network List). Remember, once Wi-Fi infrastructures turned out to be secure enough, the Wi-Fi attacks switched to the client side, with Karma-like attacks (impersonating a legitimate network through a fake access point) being extremely dangerous.
- Case 2: The insecurity of public Wi-Fi networks is commonly mitigated by the use of VPN technologies (SSL/TLS or IPSec based), and most people feel confident of using these kind of unprotected Wi-Fi networks combined with VPNs. When you connect to a public or shared network, apply the principle that you are sharing the attacker's network.
There are some facts that must be considered when the real security of a VPN plus a public Wi-Fi network is evaluated. VPN technologies do not protect against layer 2 attacks, therefore an attacker can use the extremely prevalent ARP poisoning attacks to manipulate the victim traffic. Besides that, the establishment of a VPN is in the hands of the user. This means it will take some time to establish the VPN (from seconds to minutes), and it can even not be established at all, due to availability issues or intentional DoS attacks against the VPN infrastructure. All an attacker requires to exploit or compromise the victim mobile device or computer is a few packets before the VPN is established.
A very realistic and common case where this scenario becomes a real risk is in open Wi-Fi hotspots where the authentication takes places through a (web-based) captive portal. Before the user can establish the VPN, she needs to authenticate against the Wi-Fi hotspot and make use of several protocols, typically at least, ARP, DNS and HTTP(S). The attacker only needs to manipulate any or all them to exploit vulnerabilities on the victim device, using one of the most common methods today to compromise client devices, the web browser and its associated plugins (take a look at the "Browser Exploitation for Fun and Profit" trilogy). All these VPN concerns also apply to other scenarios where VPNs are used, such as case 3.
The most secure option, not only for Wi-Fi but for general Internet usage, is to make use end to end encryption and protection for all communications, what typically involves using SSL/TLS technologies for all protocols (IMAP, SMTP, HTTP, etc). The main concerns associated to this are the target service supporting it for the whole session (not just the authentication process), proper verification of the other end due to digital certificate issues (e.g. the "recent" decreased credibility of the Internet PKI due to trusted CA compromises), and the limitation to use these technologies on lower layer protocols (ARP, DNS or even IP; these last two are what DNSSEC and IPSEC are used for).
- Case 3: The main issue associated to public secure Wi-Fi PSK networks is that all users are sharing the same network, thus all them know the pre-shared key, and therefore, even with WPA/WPA2 Wi-Fi encryption, any legitimate user can capture and manipulate the traffic from other legitimate users (any user can extract the temporary key assigned to other users having knowledge of the pre-shared key). The entry requirement to become a legitimate user can be nonexistent (on free public Wi-Fi networks) or the payment of a small fee any attacker can afford.
The main solution to avoid this kind of shared environment is to use WPA2/AES Enterprise technologies for secure public Wi-Fi hotspots, where each user will be assigned an independent temporary key (that cannot be derived from a pre-shared key). The future should follow this route, being the main drawback the verification of the digital certificates associated to the RADIUS servers and the distribution of legitimate usernames and robust passwords (however, from a traffic eavesdropping and manipulation perspective, even sharing a single username and password between all users in this scenario will be more secure than PSK).
Another option to avoid local network attacks is to use the mobile broadband capabilities of your mobile devices instead of a shared Wi-Fi network, enforcing the use of +3G cellular networks and avoiding GPRS/EDGE.
If you are a vendor, can you improve your default Wi-Fi equipment configuration? If you are a service provider, can you provide more secure configurations for home end users, small and medium businesses, and enterprises Wi-Fi equipment? If you are a corporate administrator or security pro, can you improve the security of both your employee and guest Wi-Fi networks, plus the configuration of the corporate Wi-Fi clients? If you are offering any kind of temporary or permanent Wi-Fi access (such as Wi-Fi hotspots) in venues, conferences, hotels, airports, cafés, restaurants, libraries, etc, can you improve the security of these networks? As a user, can you minimize the risk you take when connecting to Wi-Fi networks, avoid insecure environments, and spread the word and create awareness on other users, colleagues, friends, family members, neighbors, management, etc?
It is year 2011, we have the technologies for secure Wi-Fi deployments available, but we are clearly not making use of them in all common usage scenarios. Time to improve (and comment using the section below)!
----
Raul Siles
Founder and Senior Security Analyst with Taddong
www.taddong.com
5 Comments
Have you seen this?
Steve writes,
"I can't put all the pieces together, but there's a malicious scheme afoot involving SQL insertion attempts and search engine optimization, I think. Seeing logs with an insertion attempt for 0x31303235343830303536 (or "1025480056"), I googled the translated value. There are a ton of hits on "1025480056" which include the SQL insertion attack in the link that Google presents. Is this a magic number for Oracle, mysql or MS SQL? Clearly evil, I'm not sure why, though."
Have you seen this before? Do you have any idea what it is? if so, please leave your comments.
Christopher Carboni - Handler On Duty
10 Comments
Reader's Choice
Given all that is happening in the world of information security, it's not too difficult (usually) to find something to write a diary about.
What would you, our faithful readers like to see? Are there tips or tricks you're looking for? Do you want to see more diaries where we pose a challenge for you to solve? Are there specific topics you would like to see?
Write to us or comment on this diary to let us know what you would like to see, or see more of.
Christopher Carboni - Handler On Duty
10 Comments
Dark Black Tuesday Coming Up: 17 Microsoft Bulletins
Microsoft got big plans for everybody for next Tuesday, and I hope you haven't made any dinner plans because you will be busy patching (or working with your old friends like WSUS to get the patches tested and released).
A total of 17 Bulletins are going to be released according to Microsoft's pre-release. 9 bulletins are rated critical and 8 are rated important. It pretty much affects the usual suspects (Windows, Internet Explorer and Office) as well as some less regular guest starts like Microsoft's developer tools.
The critical patches apply pretty much to all versions of Windows (XP, Vista, Windows 7 and 2008) with one or two exceptions.
[1] http://www.microsoft.com/technet/security/bulletin/ms11-apr.mspx
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
3 Comments
Being a good internet neighbour
March 2011 was a busy month with a number of very public announcements on systems being breached. These had different effects on each of us.
The one that had an odd side effect for me was the Lizamoon.com SQL injection attack. My day job has me attempting to protect a large number of staff from themselves and the evils of the internet, which isn't that different to many that read the Diary.
After seeing the alarm about this SQL injection attack, I implemented the standard block list to the identified malware hosting sites [2] and reviewed my firewall logs. Solid security and operational practices meant our systems were safe, but I did find three external websites that had been successfully compromised just from reviewing the proxy web logs. Just to be clear, my company has no anti-disclosure constraints, I was given permission to talk with the attacked sites, this attack is pretty public, I haven't tweaked, fiddled or done stuff* to find this information and they are, unwittingly, attacking my systems and staff. I, as the security guy need to stop this one way or another.
This leads to my First Question**: Should I tell them they have a problem or just blocked 'em too?
The SQL injected web site is a legitimate web site, staff from my company are allowed to access it and being redirecting to Evil Web Site without either party knowing means action has to be taken.
This seems like a no brainer. If you see someone's house is on fire, you let them know.
Second Question: How do I let them know?
The easy way was to get contact details from the infected web site by visiting the site and clicking on contact info. This identified them as a large company and two small businesses, all in my time zone and relatively local to me. I was able to get the helpdesk for the large company, the owner and a shop assistant for the other two.
Third Question: What do I tell them?***
The fun part of talking to non-IT people (most of humanity or so I'm informed) is glibly pointing out "their 'base has been 0wnzed by sqli" might not convey a clear and detailed picture of the issue. Most people know being hacked is a bad thing, so the simple opener of “Your web site has been hacked and as a customer I’d like you to fix it please” was a reasonable start and got their attention. I told them where to get more information on how their website was hacked (Google these terms or go to web site X) and that their IT people need to fix it. I offer them the best of luck with fixing their site and that was it. All of a pretty easy ten minutes on the phone.
The outcome of a few minutes of advice
Two quickly fixed the damage done and seemed please someone had taken the time to let them know they had a problem.
Only the small company with the startled shop assistant haven’t fixed their Lizamoon problem. Despite a couple of follow up emails to the company they are still compromised so I’ve been forced to block that site at our borders. That’s sadly a loss of income for them, but a necessity for us.
Worthwhile being a good internet neighbour?
That’s up to you but the hope is that everyone can take a few minutes to help out a digital stranger in need every once in a while when you can. Many of you reading this help others in your physical lives, in one way or another, and I’m guessing that takes up a lot more time than a phone call or couple of emails to a digital victim.
Kevin Liston’s let’s clean up SQL slammer [3] diaries really shows if problems aren’t fixed and are left they never really go away but with effort, a difference can be made[4].
As always, if you have any better suggestions, insights or tips please feel free to comment.
* e.g. things that could get me fired, arrested, dragged off to a dark room then forced to listen to pan pipes or anything mum wouldn't approve of
** Capitalisation is intentional; it’s there to denote my deep pondering on the topic at hand
*** With so many well publicised social engineering phone scams in Oz [5], I was somewhat nervous about what response I might receive. Fortunately it was all good (as they say here Down Under)
[1] http://isc.sans.edu/diary.html?storyid=10642
[2] http://community.websense.com/blogs/securitylabs/archive/2011/03/31/update-on-lizamoon-mass-injection.aspx
[3] http://isc.sans.edu/diary.html?storyid=9637
[4] http://isc.sans.edu/diary.html?storyid=9871
[5] http://isc.sans.edu/diary.html?storyid=10135
Chris Mohan --- Internet Storm Center Handler on Duty
9 Comments
IPv6 MITM via fake router advertisements
A recent article [1] describes a rather neat variation on how fake router advertisements can be used with IPv6 capable hosts to intercept traffic, including tricking hosts to use IPv6 to connect to systems that normally are not reachable via IPv6.
First lets start with the "old" part of this attack: Fake router advertisements. IPv6 relies a lot more on auto configuration then IPv4. While techniques like "zero configuration" can be used in IPv4, we usually find DHCP used to configure IPv4 networks. In IPv6, routers are typically used to configure a network via "router advertisements". A router advertises which network it is willing to route, and hosts connected to the router will pick an address within this network.
In short, router advertisements can be considered a "DHCP lite" for IPv6. If I introduce a fake router, I get the same effect as I would get from a fake DHCP server in IPv4. However, as only few networks implement IPv6, a fake IPv6 router is likely to be the only IPv6 router. Hosts which so far had no connectivity to the IPv6 internet will now use this fake router to connect. Fake router advertisement tools are very common, we actually play with one in my IPv6 class (fake_router6 from the THC kit)
Big deal. There are not a lot of IPv6 sites. So why should I care? The reason you may need to care is a protocol called "NAT-PT". NAT-PT is an experimental protocol used to connect IPv6 only networks to the legacy IPv4 network. NAT-PT works by returning IPv6 addresses for DNS lookups that would otherwise only return IPv4 addresses. Once a host connects to this "mapped" IPv6 address, the NAT-PT router will translate the IPv6 connection to an IPv4 connection, much like we are used to from IPv4-to-IPv4 NAT.
By combining the fake RA advertisements with NAT-PT, the attacker has the ability to intercept traffic that would normally use IPv4. To make things more interesting, if a host has IPv6 and IPv4 connectivity, the IPv6 connection is preferred, causing this attack to work even better.
What are the work arounds? How do you defend?
- IPv6 is a wonderful protocol. But if you don't need it: Turn it off. If you need it, then monitor and defend it like IPv4
- the attack does require layer 2 access. Physical access to your network should be restricted
- if you use an "open" network (e.g. public wifi), use encryption to protect yourself (SSL, IPSec). This attack is not more deadly in this case then other layer 2 attacks.
[1] http://resources.infosecinstitute.com/slaac-attack/
And also see our IPv6 Security Summit in July
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
6 Comments
DNS.be DDOS
Another DDOS slipped by almost unnoticed (thanks Arnt). A report in Datanews (http://datanews.rnews.be/nl/ict/nieuws/nieuwsoverzicht/2011/04/04/botnet-viseert-belgie/article-1194984299269.htm# in Dutch) mentions that the .be domain was under attack last Sunday. Requests were being made of the servers relating to MX records for other domains. The .be name servers do not look after this information and correctly responded. However the end result was that two out of the 8 servers were overloaded. Even should the other servers be overloaded the TLD is anycast hosted and another 41 or so servers could jump into action. Hence the attack went largely unnoticed by the public.
Mark H
1 Comments
Sony DDOS
The Anonymous group is currently utilising LOIC to DDOS Sony infrastructure. It seems that it is partially successful with a few Sony sites being unavailable at the moment.
Mark H
4 Comments
When your service provider has a breach
As the day progresses more and more Epsilon clients are notifying their customers that their details have been compromised, I got to thinking about what information is readily given to third parties for many different purposes. The outsourcing of certain specialist tasks is nothing new. What I've found in the past though is that information is often handed over without really thinking through any of the consequences should the information be compromised. So here are some of the things I believe you should be doing when handing over client information to third parties. as per usual feel free to add your own experiences and suggestions.
Before handing over any information over you may want to ask the following:
- What is the minimum amount of information that is needed in order to perform the tasks requested? - We often find that people are handing over substantial amounts of data when all that is really required is an email address and a first name. This will of course depend on what the third party is doing for you, but having a think about what they really need is a good starting point. Then it can be risk assessed and a decision taken.
- How are you protecting my information? - Likely you will get a warm fuzzy answer and you will have to sift through it to find out what the real answer is. What you want to look for are things like operational security processes. How are they going to notice if there was a breach? Do they utlise IDS/IPS. Do they have firewalls (and yes sometimes you will get the answer of "no we don't need a firewall"
- Do you have the right to audit? - The answer to this will often give an indication as to what the real answer is to the previous question. If the answer is "no", well ...
- Do they have an incident response process?
- What steps will be taken in the event of a breach and when will you be notified? - i.e. how long will they sit on the compromise before they will let you know that it is gone?
- What happens if the breach is at a subcontractor of the organisation? - Many companies subcontract processes to others.
- Who will carry any additional costs? - In some jurisdictions there is a notification requirement. In some cases this may need to take the form of snail mail, those stamps can be expensive, who will pay for that.
- You may need to communicate any special security requirements you have for your information. You will need to communicate these clearly to the provider so they can meet your expectations.
Collect the answers and have it put into the contract/agreement, that way nobody can forget who would do what and when.
That's my quick start list before handing information over.
Mark H
5 Comments
Extreme Disclosure? Not yet but a great trend!
There is a trend in vigilant disclosure by some companies and service providers. A reader wrote in with a great example of an email disclosure. U.S. Bank informed it's customers of a breach in a partners system. It went on to disclose that the partner system had been accessed by unauthorized users and that customer email addresses had been exposed.
What stuck out for myself and other handlers that commented, was the way the disclosure was handled. U.S. Bank then clearly identified it's information disclosure policy. They followed on to inform customers that at no time was financial data disclosed and that only Epsilon's systems had been accessed.
If you have had any disclosures from vendors please send them in to us. Packets are better but we take disclosures as well!
Below is the email that was relayed.
As a valued U.S. Bank customer, we want to make you aware of a situation that has occurred related to your email address.
We have been informed by Epsilon Interactive, a vendor based in Dallas, Texas, that files containing your email address were accessed by unauthorized entry into their computer system. Epsilon helps us send you emails about products and services that may be of interest to you.
We want to assure you that U.S. Bank has never provided Epsilon with financial information about you. For your security, however, we wanted to call this matter to your attention. We ask that you remain alert to any unusual or suspicious emails.
Please remember that U.S. Bank will never request information such as your personal ID, password, social security number, PIN or account number via email. For your safety, never share this or similar information in response to an email request at any time. To learn more about recognizing online fraud issues, visit:
http://www.usbank.com/cgi_w/cfm/about/online_security/online_fraud.cfm
In addition, if you receive any suspicious looking emails, please tell us immediately.
Call U.S. Bank Customer Service at 800-US-BANKS (800-872-2657).
The security of your information is important to us, and we apologize for any inconvenience this may have caused you. As always, if you have any questions, or need any additional information, please do not hesitate to contact us.
Update
Thanks to all of those that sent in their notifications. On the list so far:
Best Buy, Home Depot, Chase, U.S. Bank, Robert Half, Disney Destinations, Citibank, Hilton Honors. No doubt there will be more to come.
-MH-
UPDATE 2
Epsilon in their press release mentions that only email addresses and names have been compromised for approximately 2 percent of their clients. A quick calculation shows that is at least 50 organisations (over 2500 clients). So a few more of you may be getting notifications.
Richard Porter
--- ISC Handler on Duty
Can be reached:
Twitter: packetalien
Email: richard at isc dot sans dot edu
27 Comments
RSA/EMC: Anatomy of a compromise
Earlier today I had the opportunity to read a blog post by Uri Rivner, the Head of the Security Division of EMC. While the investigation into the RSA/EMC compromise is still ongoing, Mr. Rivner presents a very good summary of what they do know.
Some of the facts as written by Mr. Rivner:
- The first part of the attack was a spear-phishing attempt aimed at non-high-profile targets. The information on the targets was most likely mined from social networking sites. All it took was one of the targeted employees who was tricked into opening an attached Excel spreadsheet.
- The Excel spreadsheet contained a zero-day exploit targeting an Adobe Flash vulnerability.
- The exploit added a backdoor. and installed a remote administration program.
- The malware then captured credentials for user accounts in order to compromise higher value targets.
In my experience this is typical sequence of events for an APT attack. There is very little in this attack that is particularly sophisticated. The big question is what are the defenses that would have prevented or reduced the impact of this attack?
Obviously the first is user education. It is extremely difficult to educate your employees to prevent this sort of targeted spear-phishing attack, but we need to try. The more users who know how to analyze an email to test its legitimacy the less likely an attack like this will succeed.
The bigger one as Mr. Rivner alludes in this blog post is to come up with a new defense paradigm. The traditional paradigm of a well protected perimeter with a soft inside should be dead. There are just too many ways to circumvent the perimeter, spear phishing being just one.
The thing is I don't think this new paradigm is so new. Many have been advocating for years moving the prevention and detection closer to the data. There are a lot of approaches that can be used here, but in my mind it begins with segregating servers from the desktop LAN and controlling access to these protected enclaves as thoroughly or better as we do our perimeters today. It means classifying your data and installing protection and detection technologies appropriate to the sensitivity of the data. It means installing and tuning Data Loss Prevention (DLP) technologies to detect when your sensitive data is leaving your company. It means instrumenting company LANs and WANs so a network baseline can be determined and deviations from this baseline be detected and investigated.
Obviously this is only a partial list of the possible strategies. What else would you like to see done in your organization to help prevent this type of attack?
-- Rick Wanner - rwanner at isc dot sans dot org - http://namedeplume.blogspot.com/ - Twitter:namedeplume (Protected)
17 Comments
LizaMoon Mass SQL-Injection Attack Infected at least 500k Websites
Websense has been tracking a mass SQL-Injection attack for the past few days that started with only a few ten thousand websites and has exploded to potentially over 1 million websites. There doesn't seem to be anything particularly new about the infection mechanism (aside of the scope of its success) and the injection itself only inserts a random snippet of HTML to redirect victims to a rogue AV site that tells the user they are infected.
One of the domains implicated in this attack was registered in October and showed up on the radar in December, so it appears the preparation of this attack has taken some time and it's been perculating for awhile. The bulk of the infections, however, have only just occurred in the last few days. Infected sites tend to use the same URL structure including a file "ur.php". It appears this is only affecting sites using Microsoft SQL Server 2003/2005.
Defense against your sites getting infected is the standard things we ought to be doing anyway in regards to SQL injection (i.e.use prepared statements, filter input for control characters, whitelist if possible, blocklist if not). Webserver administrators should also be checking for sudden appearance of files in their httpdocs directory. More on this as it develops.
--
John Bambenek
bambenek at gmail /dot/ com
Bambenek Consulting
6 Comments
Happy Open Source Intelligence Analysts Day: April 1st
April 1st is upon us. In some circles it is celebrated as "April Fools' Day." I choose to observe it as Open Source Intelligence Analysts' Day-- the one day of the year that we all have to be extra-suspicious of every news article, blog post and tweet. It's a good skill to develop, and we have this unique time where we know that there are hidden gems of disinformation being introduced into the streams of information we've come to rely on the rest of the year.
It's like a tornado drill for truth.
2 Comments



1 Comments