Firefox 3.5 is available
Firefox 3.5 has been released.
If your browser didn't automagically update, you can download the newest version from http://www.mozilla.com/en-US/firefox/firefox.html
Christopher Carboni - Handler On Duty
Special SANSFIRE 2009 Podcast Presentations - Adrien de Beaupre
Our seventh presentation is by one of our Handlers by the name of Adrien de Beaupre. Adrien is one of our Handlers from Canada. This is a presentation entitled:
"Developing Cyber Threat Intelligence"
I would suggest the way to get these podcasts is through iTunes (if you have iTunes) if not, then you can use whatever method works best for you and follow this link:
http://isc.sans.org/podcast.xml
In order to subscribe through iTunes click here:
Audio and Slides are here: https://www.sans.org/webcasts/show.php?webcastid=92553
-- Joel Esler | http://www.joelesler.net | http://twitter.com/joelesler
0 Comments
Special SANSFIRE 2009 Podcast Presentations - Pedro Bueno
Our sixth presentation is by one of our Handlers by the name of Pedro Bueno. Pedro is one of our Handlers, originally from Brazil (so, hence the accent you will hear) and now residing in Santa Clara. He is a malware researcher for a large Anti-Virus firm. This is a presentation entitled:
"Malwares, Money and Criminal/Terror Activity. The Dangerous Relationship"
I would suggest the way to get these podcasts is through iTunes (if you have iTunes) if not, then you can use whatever method works best for you and follow this link:
http://isc.sans.org/podcast.xml
In order to subscribe through iTunes click here:
Audio and Slides are here: https://www.sans.org/webcasts/show.php?webcastid=92548
-- Joel Esler | http://www.joelesler.net | http://twitter.com/joelesler
0 Comments
De-Obfuscation Submissions
Here are a list of sites that readers have submitted as being particularly useful for de-obfuscation
From Pat:
The DNSStuff site provides some free tools one of which allows you to de-obfuscate URLs. The tools are can be found at http://www.dnsstuff.com/tools/tools/.
Christopher Carboni - Handler On Duty
1 Comments
Obfuscated Code
Earlier today we received a fairly common email from a reader asking us for help de-obfuscating some (in this case) HTML code.
If you have any favorite sites you use to de-obfuscate code whether it's html, jacascript or anything else, send them in and I'll post them as a diary that can be bookmarked as a reference.
Christopher Carboni - Handler On Duty
0 Comments
Special SANSFIRE 2009 Podcast Presentations - Mark Hofman
Our fifth presentation is by one of our Handlers by the name of Mark Hofman. Mark is one of handlers, he lives in Australia. For the first three minutes or so of his presentation there is some horrible noise on his mic, at which point he switches mics and the audio is a lot better.. This is a presentation entitled:
"SOA and XML security"
I would suggest the way to get these podcasts is through iTunes (if you have iTunes) if not, then you can use whatever method works best for you and follow this link:
http://isc.sans.org/podcast.xml
In order to subscribe through iTunes click here:
Audio and Slides are here: https://www.sans.org/webcasts/show.php?webcastid=92543
-- Joel Esler | http://www.joelesler.net | http://twitter.com/joelesler
0 Comments
Special SANSFIRE 2009 Podcast Presentations - Bojan Zdrnja
Our fourth presentation is by one of our Handlers by the name of Bojan Zdrnja. Bojan actually couldn't make it to Baltimore this year at the last minute, but was actually able to give his presentation from Croatia. This is a presentation entitled:
"Using Passive DNS Data to Track Malicious Activities"
I would suggest the way to get these podcasts is through iTunes (if you have iTunes) if not, then you can use whatever method works best for you and follow this link:
http://isc.sans.org/podcast.xml
In order to subscribe through iTunes click here:
Audio and Slides are here: https://www.sans.org/webcasts/show.php?webcastid=92528
-- Joel Esler | http://www.joelesler.net | http://twitter.com/joelesler
0 Comments
IP Address Range Search with libpcap
This week, I received a request to search for a range of destination addresses that cannot easily done using libpcap conventional macro filters but can be done using an IP protocol filter. It is quite easy to filter for a CIDR range (i.e. /23, /24) with a libpcap macro filter but when it comes to search for an unusual list of addresses such as 192.168.25.6 to 192.168.25.35, there is no simple macro to easily do it.
The following example illustrates how to find SYN packets directed to natted addresses where an attempt was made to connect or scan a service natted to an internal resource. I used this filter for addresses located in the range 192.168.25.6 to 192.168.25.35.
tcpdump -nr filename '((ip[16:2] = 0xc0a8 and ip[18] = 0x19 and ip[19] > 0x06) and (ip[16:2] = 0xc0a8 and ip[18] = 0x19 and ip[19] < 0x23) and tcp[13] = 0x02)'
The filter breaks down as follow:
Starting IP Range
ip[16:2] = 0xc0a8 -> First two octets of the IP address is 192.168
ip[18] = 0x19 -> Third octet of the IP address is 25
ip[19] > 0x06 -> Last octet of the IP address is greater than 6
Less than IP Range
ip[16:2] = 0xc0a8 -> First two octets of the IP address is 192.168
ip[18] = 0x19 -> Third octet of the IP address is 25
ip[19] < 0x23 -> Last octet of the IP address is less than 35
Last Part of the Filter
tcp[13] = 0x02 -> If there is a successful match, only print those with SYN packets
This filter yielded for example the following results which in this case are inbound scans:
21:38:28.522588 IP xxx.x.221.157.63662 > 192.168.25.7.443: S 1279429613:1279429613(0) win 65535 <mss 1412,nop,nop,sackOK,nop,wscale 1,nop,nop,timestamp 353141033 0>
04:24:34.438872 IP xxx.xxx.253.36.55395 > 192.168.25.7.443: S 3909380827:3909380827(0) win 65535 <mss 1412,nop,nop,sackOK,nop,wscale 1,nop,nop,timestamp 3199762289 0>
04:24:49.700805 IP xx.xxx.160.65.54640 > 192.168.25.7.443: S 520695074:520695074(0) win 65535 <mss 1412,nop,nop,sackOK,nop,wscale 1,nop,nop,timestamp 2595387575 0>
05:20:18.618965 IP xxx.xxx.124.41.49734 > 192.168.25.7.443: S 3595559815:3595559815(0) win 65535 <mss 1412,nop,nop,sackOK,nop,wscale 1,nop,nop,timestamp 1555543940 0>
This same filter could easily be expended to include search for a specific port instead of any ports to further narrow the search.
Handler on Duty
Guy
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
Teaching Comprehensive Packet Analysis in Ottawa, ON this coming September
2 Comments
New NIAP Strategy on the Horizon
It has been recently announced that the Common Criteria Evaluation and Criteria Scheme (CCEVS) will be undergoing some significant changes in the upcoming months. The most significant is the Protection Profiles (PP) robustness and the elimination of the Medium Robustness Protection Profile. There are a number of aspects to this change that I will not republish here, but anybody that works with CCEVS really needs to give this a good read.
As always, comments are welcome!
Tony Carothers
0 Comments
Special SANSFIRE 2009 Podcast Presentations - State of the Internet Panel
Our third presentation is by all of the Internet Storm Center Handlers that were present (at the time) at SANSFIRE 2009. This is our annual "State of the Internet Panel" presentation.
I would suggest the way to get these podcasts is through iTunes (if you have iTunes) if not, then you can use whatever method works best for you and follow this link:
http://isc.sans.org/podcast.xml
In order to subscribe through iTunes click here:
There are no slides for this presentation.
-- Joel Esler | http://www.joelesler.net | http://twitter.com/joelesler
0 Comments
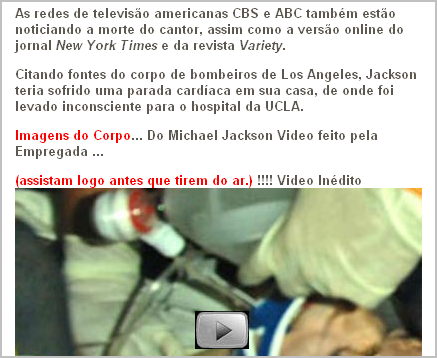
Michael Jackson Spam Distributes Malware
As we anticipated in our yesterday's diary, spammers are starting to exploit attention-grabbing headlines of recent celebrity deaths. Sophos described one such message, with the subject "Confidential===Michael Jackson", in their blog posting. Today we're starting to see reports of these messages directing viduals to websites that distribute malicious software.
For example, Steve Basford emailed us a link to his blog posting, where he discusses a spammed fake news item invites the victim to download a "video" to download. The message said: "As redes de televisão americanas CBS e ABC também estão noticiando a morte do cantor, assim como a versão online do jornal New York Times e da revista Variety..." (See screen shot below.)
Liked this note? Tweet it!
-- Lenny
Lenny Zeltser - Security Consulting
Lenny teaches malware analysis at SANS Institute. You're welcome to follow him on Twitter. You can also track new Internet Storm Center diaries by following ISC on Twitter.
0 Comments
How Malware Defends Itself Using TLS Callback Functions
Malware authors employ numerous and creative techniques to protect their executables from reverse-engineering. The arsenal includes an anti-debugging technique called TLS callback, which I'd like to describe in this note. (Thanks to C. W. for his insights regarding this topic!)
What is TLS?
According to Microsoft, Thread Local Storage (TLS) is a mechanism that allows Microsoft Windows to define data objects that are not automatic (stack) variables, yet are "local to each individual thread that runs the code. Thus, each thread can maintain a different value for a variable declared by using TLS." This information is stored in the PE header. (Windows uses the PE header to store meta information about the executable to load and run the progrem.)
A programmer can define TLS callback functions, which were designed mainly to initialize and clear TLS data objects. From the malware author's perspective, the beauty of TLS callbacks is that Windows executes these functions before execuding code at the traditional start of the program.
How Can TLS Callbacks Confuse Debuggers and Analysts?
Analysts often examine the a malicious program's code by starting with the instructions located at the Entry Point of the executable. The Entry Point is a field in the PE header that stores the address of the "first" instruction in the program that Windows is supposed to execute; debuggers typically take us to that instruction after loading the executable. TLS callback functions allow malware authors to execute malicious code before the debugger has a chance to pause at the traditional Entry Point. This allows malware to infect the system or disable the debugger before the analyst has a chance to look at the sample's code.
Consider the TLS callback technique employed by the Nadnadzzz bot about a year ago. If you load the bot's executable into OllyDbg, you expect to have the debugger pause at its entry point. Instead, OllyDbg seems to immediately say that the process terminated. What happened? You just infected yourself!
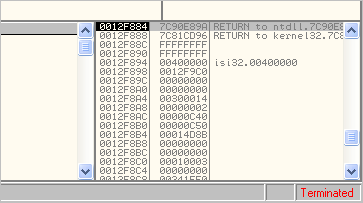
The problem is that before OllyDbg had a chance to pause at the traditional Entry Point instruction, it executed a TLS callback function.
How to Bypass the TLS Callback Defense
To bypass the TLS callback defense to debug the program starting from its "true" beginning of the TLS callback function:
- Configure the debugger to pause on the system entry point, instead of the traditional program entry point.
- Identify the address of the TLS callback function, instead of the traditional program Entry Point.
- Set the breakpoint on the TLS callback function, then run the program if you wish.
If using OllyDbg, you can tell it to pause before TLS callback by going to Debugging options > Events. By default, it's set to pause at "WinMain (if location is known)." Instead, set it to pause at "System breakpoint." This will allow you to control the program before TLS callback functions execute.
.png)
Now you will have a chance to set the breakpoint on the TLS callback function. You need to find it first, though. Ilfak Guilfanov describes a convenient way to do that with IDA Pro in his blog posting. To locate the TLS callback function, load the malicious executable into IDA Pro, then press Ctrl+E to view the executable's entry points. The address of the TLS callback function should be among them.
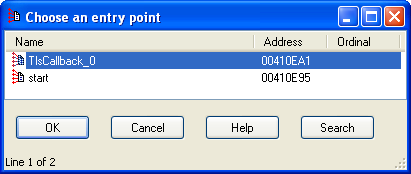
Now you know where to start debugging or otherwise analyzing the program's code. You can do this in IDA Pro. If you prefer OllyDbg, you can return to OllyDbg, and load the malicious program; OllyDbg will now pause at the "system entry point" in ntdll.dll. Press Ctrl+G and enter the address of the TLS callback function, which you located via IDA Pro; set a breakpoint there and continue the analysis.
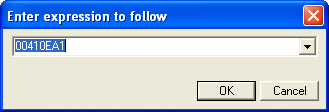
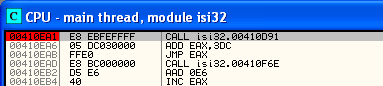
For additional information about TLS callbacks used by malware for anti-debugging, see the links mentioned earlier, as well as:
- Manually create a Tread Local Storage (TLS) Callback
- How to execute code during an application's initialization
- TLS as used in Backlight
If you have other tips and examples of TLS callbacks used by malware, please let us know.
Liked this note? Tweet it!
-- Lenny
Lenny Zeltser - Security Consulting
Lenny teaches malware analysis at SANS Institute. You're welcome to follow him on Twitter. You can also track new Internet Storm Center diaries by following ISC on Twitter.
0 Comments
PHPMYADMIN scans
We have received some reports (thanks Drew) of scanning for keyhandler.js which is part of PHPMyAdmin. The PHPmyAdmin site does not specifically mention this script. Scans look as follows:
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:19 -1000] "GET HTTP/1.1 HTTP/1.1" 400 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:19 -1000] "GET /admin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:20 -1000] "GET /admin/pma/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:21 -1000] "GET /admin/phpmyadmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:21 -1000] "GET /db/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:22 -1000] "GET /dbadmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:22 -1000] "GET /myadmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:23 -1000] "GET /mysql/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:23 -1000] "GET /mysqladmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:24 -1000] "GET /typo3/phpmyadmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:24 -1000] "GET /phpadmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:24 -1000] "GET /phpmyadmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:25 -1000] "GET /phpMyAdmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:25 -1000] "GET /phpmyadmin1/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:26 -1000] "GET /phpmyadmin2/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:26 -1000] "GET /pma/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
aa.zzz.qqq.119 - - [24/Jun/2009:08:37:27 -1000] "GET /web/phpMyAdmin/js/keyhandler.js HTTP/1.1" 404 26 "-" "Toata dragostea mea pentru diavola"
Modsecurity or suhosin should help you out keeping this away from your installation. PHPMyadmin should probably only be available from the internal network or limited external sources. So for most of you this shouldn't be an issue. If you do have some captures of what happens when there is a compromise, please use the contact form to let us know.
Mark H - Shearwater
1 Comments
Michael J & Farrah F death SPAM
With the reported death of Farrah Fawcett and Michael Jackson today, it is likely only a matter of hours before we will start seeing SPAM relating to the subject. So it may be a good idea to remind your users that mail from unknown sources should not be opened and links should not be clicked.
If you do see any of the SPAM relating to this drop us a quick note.
Mark H - Shearwater
0 Comments
Special SANSFIRE 2009 Podcast Presentations - John Bambenek
Our second presentation is by one of our Handlers by the name of John Bambenek. You may recognize his name from his appearance on "The Daily Show" on Comedy Central, or his many Diary posts here on the Internet Storm Center. This is a presentation entitled:
"Protecting Your Secret Sauce: Tips and Techniques in Protecting Your Intellectual Property"
I would suggest the way to get these podcasts is through iTunes (if you have iTunes) if not, then you can use whatever method works best for you and follow this link:
http://isc.sans.org/podcast.xml
In order to subscribe through iTunes click here:
Audio and Slides are here: https://www.sans.org/webcasts/show.php?webcastid=92518
-- Joel Esler | http://www.joelesler.net | http://twitter.com/joelesler
0 Comments
Special SANSFIRE 2009 Podcast Presentations
Recently at SANSFIRE 2009, there were a lot of talks given by our Internet Storm Center Handlers. We managed to record all of these talks and have the audio for them and are going to be releasing them over the next several days as regular podcast episodes (note: not stormcast, so if you are subscribed to the stormcast feed, you'll need to subscribe to the regular podcast feed as well).
These are audio only presentations, and were recorded live (so forgive any strange audio artifacts please), the slides are not with the audio. Each presentation I put up on the feed will have a Diary post accompaying it. In the post I will place a link where you can watch the slides and listen to the audio (as it was recorded live).
I would suggest the way to get these podcast is through iTunes (if you have iTunes) if not, then you can use whatever method works best for you and follow this link:
http://isc.sans.org/podcast.xml
In order to subscribe through iTunes click here:
Our first presentation is by one of our wonderful Handlers by the name of Deb Hale. Deb lives out in Iowa and during the floods of last year had some pretty interesting IT challenges thrown in her direction. This is a presentation entitled:
"Iowa Floods and Tornadoes: Losses and IT lessons learned - Disaster Recovery and Restoration after the Storms"
Audio and Slides are here: https://www.sans.org/webcasts/show.php?webcastid=92513
-- Joel Esler | http://www.joelesler.net | http://twitter.com/joelesler
0 Comments
TCP scanning increase for 4899
An observant reader reports that he is seeing a very noticeable increase in TCP scanning for port 4899 and our dshield data confirms an uptick. Port 4899 is the default port for the Radmin tool, which is a windows-based computer remote-control package. According to his data, the scans are mostly originating from Spanish-speaking South American countries. We don't have confirmation that the attackers are looking for Radmin, so if you have some packet captures please upload them and we can take a look.
Handler: Kyle Haugsness
0 Comments
Exploit tools are publicly available for phpMyAdmin
As a follow-up to our earlier diary about phpMyAdmin scanning, there is at least 2 exploits posted in the last 20 days on public forums for exploiting the bug from March 2009 described here: www.phpmyadmin.net/home_page/security/PMASA-2009-3.php. Suggested advice is to re-verify that your phpMyAdmin is patched and also not accessible to the general Internet to prevent future exploitation of unknown bugs.
Handler: Kyle Haugsness
0 Comments
Adobe Shockwave Player Update
Several readers pointed out that Adobe released a security update for the Shockwave Player today which apparently can be exploited by a remote website. No exploit details made public yet. It should be pointed out that their upgrade instructions recommend uninstalling the old version, rebooting the machine, and then installing the new version.
www.adobe.com/support/security/bulletins/apsb09-08.html
Handler: Kyle Haugsness
2 Comments
New Thunderbird out, patches couple of vulnerabilities
Couple of readers wrote in to say that a new version of Thunderbird has been released.
Version 2.0.0.22 fixes couple of security vulnerabilities (with highest rating medium), so if you are using this e-mail client be sure to install the updates. The list of fixes can be seen at http://www.mozilla.org/security/known-vulnerabilities/thunderbird20.html#thunderbird2.0.0.22
Thanks to everyone writing in (too many to mention!).
0 Comments
Help us: How to make ISC/DShield more useful
I am looking for feedback for the next iteration of the ISC/DShield web site. What kind of information, in particular when it comes to the home page, would make the site more useful to you? If it is not already your homepage, what would it take to make it your homepage?
Use our contact form to submit feedback.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
0 Comments
Slowloris and Iranian DDoS attacks
In last couple of days we posted two diaries (http://isc.sans.org/diary.html?storyid=6601 and http://isc.sans.org/diary.html?storyid=6613) with information about Slowloris, a tool that was released last week that performs a resource exhaustion DoS attack on Apache web servers.
There has been a lot of chat about the tool on the web, so it was just a matter of time when we would see it using in real DoS attacks. Last week I posted a diary about two groups launching DDoS attacks on Iranian web sites (http://isc.sans.org/diary.html?storyid=6583). Both of these attacks were relatively simple and used existing, old tools for performing DoS attacks.
However, over the weekend some forums and web sites asking people to run DDoS attacks "expanded" their selection of tools by including Slowloris – nothing we didn't really expect to see.
Regarding Slowloris, we received a lot of information from our readers about various scenarios when Slowloris does and does not work. First of all, Adrian Ilarion Ciobanu posted several diary comments pointing to his written two years ago describing similar attack to Slowloris. Adrian posted some interesting stuff too about Apache DoS attacks at http://pub.mud.ro/~cia/computing/apache-httpd-denial-of-service-example.html. Frank Breedijk wrote in to say that he tested Slowloris with Cisco CSS load balancers which appear to be immune.
Finally, an unofficial patch has been released at http://synflood.at/tmp/anti-slowloris.diff - I haven't tested it but the patch is supposed to dynamically change the TimeOut value depending on the load (which depends on the number of Apache processes that are currently processing HTTP requests).
--
Bojan
0 Comments
Say it ain't so....
According to the Australian version of the SORBS website, Michelle (formerly Matthew) Sullivan is announcing a possible closure of the website due to contract issues. The Spam and Open Relay Blocking System (SORBS) anti-spam project is having some difficulties and states that it will close as of 20 July 2009 at noon. The site is asking for alternative hosting and states that it is officially for sale.
Read the pending closure notification at www.au.sorbs.net and a history of the organization at www.us.sorbs.net
Mari Nichols
1 Comments
phpMyAdmin Scans
Happy Fathers Day (at least those in the USA),
Earlier today one of our readers (Thanks Alice) noticed that there was a lot more activity related to one of her servers which was running phpMyAdmin. Upon further investigation it appears that her server had been compromised by exploitation of the vulnerability detailed in PMASA-2009-4. The attacker uploaded a lot of the same old types of tools such as a misnamed EnergyMech IRC bot, a perl based UDP flooding tool, and an automated tool to attempt phpMyAdmin.
It is now past time to update to phpMyAdmin 3.1.3.2 and/or updating firewall rules to limit the public Internet from touching this web application.
Updated: Monday 06/22/2009 22:30 UTC
I have heard more reports locally about activity which seems to point to phpMyAdmin scanning and exploitation. I haven't seen a copy of the exploiting tool as of yet. If you happen to get a copy of the tool, or get packet captures of it at work, please feel free to send to us.
Scott Fendley ISC Handler
0 Comments
Apache HTTP DoS tool mitigation
If you've been following our diaries or any other IT Security related news, you probably know about the Apache HTTP DoS tool that was released on Thursday (see the original diary at http://isc.sans.org/diary.html?storyid=6601).
We received some information from our readers and I did a bit more testing so I decided to put up a diary with possible mitigation options – I hope to update the diary as we receive more stuff.
So, to recap the previous diary: the tool works by exhausting Apache processes; this is done by sending incomplete request headers so Apache keeps waiting for the final header line to arrive, the tool instead just sends a bogus header to keep the connection open. Besides Apache (both versions 1.x and 2.x), Squid is also affected. Knowing how many servers running on Apache there are, this makes the tool very dangerous since it doesn't require absolutely any knowledge from the attacker – all he/she has to do is run the tool and the target site goes down. So, what mitigation options (if any) we have?
First of all, those running some load balancers or reverse proxies in front of their Apache installations should check if they are really vulnerable or not – it's possible that the proxy is not affected by this vulnerability.
If you are running a standalone Apache server (as probably most web hosters are), you still have some mitigation options, but you should be very careful about them. NOTE: Test all these options thoroughly first as they might impact legitimate access to your server!
The TimeOut Directive, described at http://httpd.apache.org/docs/2.2/mod/core.html#timeout is the most important option here. It defines how long Apache will wait to receive a GET request, or amount of time to wait between receiving packets on POST requests. This is particularly interesting for POST requests and warrants additional research to see if the tool can be modified further to attack such, hardened servers.
So, the default for TimeOut is 300 seconds – 5 minutes – for a GET request to arrive. This means that the DoS tool can keep one connection tied up for up to 5 minutes, after that it has to open another connection. Since the default number of connections is 256 the tool can easily exhaust this. I did some testing with lowering this value down to 5 seconds – this might be too low because some slow clients will not be able to get the web page so don't blindly put this in your configuration files. Anyway, since the tool has the option for specifying timeout, I put it to 4 seconds to see if the attack still worked. And sure, it worked fine, but the tool had to send much more traffic. My measurements showed that in order to DoS an Apache server with TimeOut set to 5 seconds the tool needed about 2MB of traffic per minute. That is only ~45 kb/sec which makes this attack even more dangerous – a lone DSL user might DoS a big site. However, the TimeOut directive is still probably the best mitigation option.
Another possibility is also to use a module, such as mod_limitipconn, which limits the number of connections from one IP address. Again, use this with caution since you might prevent legitimate visitors if they are coming from behind a proxy. Also, this option is only partially good – sure, it will stop a script kiddie without other resources from DoS-ing your web site, but an advanced attacker can easily run the tool from dozen of machines.
And this is, unfortunately, more or less what we have at the moment. I will do more research on the scenario with the POST request and TimeOut directive – will post an update if I find something interesting. If you did some research and have workarounds please let us know.
--
Bojan
7 Comments
Situational Awareness: Spam Crisis and China
Gary Warner, Director of Research at the UAB Computer Forensics, posted a very interesting analysis from the past 48 days concerning the amount of spam which has ties to China.
The post is a call for increased awareness of the situation with certain registrars and hosting providers in China who have become spam havens in recent times. It is our hope as with Gary's that by exposing the amount spam, fraudulent messages, and criminal activity occurring within a few areas of China, that those of you who have contacts in China may be able to educate our respective counterparts at ISPs, hosting providers and in law enforcement to the statistics. With that education, we expect that the government or high level business personnel will take appropriate steps to mitigate this situation as has been done with other locations in years past.
Thanks Gary for posting this very enlightening blog located at garwarner.blogspot.com/2009/06/spam-crisis-in-china.html
Scott Fendley
ISC Handler on Duty
3 Comments
G'day from Sansfire2009
Well SANSFIRE 2009 is drawing to a close. As you may know SANSFIRE is the SANS conference hosted by the Storm Center. A number of the handlers give presentations and it allows us to meet face to face, usually over a beer or two. Yes we do talk about normal stuff, but there is a fair amount of geek speak during these meetings. It is a nice opportunity to shoot the breeze, share ideas and even do some planning. A number of us have never met face to face so it was very nice to put a face to the email/IM or diary entry.
The various handler talks were webcast and should be available online I'll put a link in as soon as I know where.
A number of us attended classes and sessions. Steve H was in 709 Developing Exploits for Penetration Testers and Security Researchers, his head did not explode, he seems to have goten through quite nicely. One of the highlights for me was the scapy workshop presented by Judy Novak. I had played a little with the tool previously, but this was something else. She makes it very simple and from the responses in the room it was very well received. It might be a bit short to do the workshop in Canberra, but we'll schedule it for Sydney if we can. Scapy allows you to craft your own packets, it is very flexible and easy to use. Well worth a look if you need to test an IDS, firewall or just send some packets and play with results.
Anyways, time to pack up and start heading for a plane.
Mark H
0 Comments
Explaining Defense in Depth
Realizing That You Have a Problem
Once an organization reaches a certain size, you end up with a situation where separate groups are responsible for firewalls, IDS, anti-virus, etc. Often these groups will not share a common chain of command. Eventually, you may find yourself on a conference call similar to this (note, the names and protocols have been changed to protect the guilty.)
Alan the Intel Guy: “Based on law-enforcement’s reports, the group is using NFS to compromise systems.”
Betty from Vulnerability Assessment: “We’re scanning for running NFS daemons, I’ll shoot our report over to you.”
Alan: “Pat, do we have an IDS rule to detect NFS sessions crossing the perimeter?”
Pat, in IDS: “Let me check…”
Gene in management: “Shouldn’t the firewalls be blocking NFS?”
At this point Alan starts Googling for a LOLCat that says something like: “Defense in Depth: you’re doing it wrong.”
Illustrating the Problem to Technical People
Repeat after me:
“AV signatures are reactive”
“IDS signatures both false-positive AND false-negative”
“Your regularly-scheduled firewall maintenance doesn’t always go so regularly-scheduled.”
Putting it Into Terms Your Boss Can Understand
Earlier this week while I was piggybacking into the building behind a couple of co-workers, I overheard a bit of their conversation about a show they had watched on TV the previous day. It was likely Dr. Phill or something. An otherwise perfect couple was having marital difficulties whenever something important was accidentally sent through the washing machine. One blamed the other for not emptying their pockets while the other counter-blamed because they didn’t check the pockets before running the wash.
The solution: do both.
At this point, the wise manager will observe: “but isn’t this a wasteful duplication of effort?”
So you must counter: “it’s a small price to pay (by automated processes I may add) to make certain that your Rolex doesn’t go through the wringer.”
1 Comments
Apache HTTP DoS tool released
Yesterday an interesting HTTP DoS tool has been released. The tool performs a Denial of Service attack on Apache (and some other, see below) servers by exhausting available connections. While there are a lot of DoS tools available today, this one is particularly interesting because it holds the connection open while sending incomplete HTTP requests to the server.
In this case, the server will open the connection and wait for the complete header to be received. However, the client (the DoS tool) will not send it and will instead keep sending bogus header lines which will keep the connection allocated.
The initial part of the HTTP request is completely legitimate:
GET / HTTP/1.1\r\n
Host: host\r\n
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; .NET CLR 1.1.4322; .NET CLR 2.0.503l3; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729; MSOffice 12)\r\n
Content-Length: 42\r\n
After sending this the client waits for certain time – notice that it is missing one CRLF to finish the header which is otherwise completely legitimate. The bogus header line the tools sends is currently:
X-a: b\r\n
Which obviously doesn't mean anything to the server so it keeps waiting for the rest of the header to arrive. Of course, this all can be changed so if you plan to create IDS signatures keep that in mind.
According to the web site where the tool was posted, Apache 1.x and 2.x are affected as well as Squid, so the potential impact of this tool could be quite high considering that it doesn't need to send a lot of traffic to exhaust available connections on a server (meaning, even a user on a slower line could possibly attack a fast server). Good news for Microsoft users is that IIS 6.0 or 7.0 are not affected.
At the moment I'm not sure what can be done in Apache's configuration to prevent this attack – increasing MaxClients will just increase requirements for the attacker as well but will not protect the server completely. One of our readers, Tomasz Miklas said that he was able to prevent the attack by using a reverse proxy called Perlbal in front of an Apache server.
We'll keep an eye on this, of course, and will post future diaries or update this one depending on what's happening. It will be interesting to see how/if other web servers as well as load balancers are resistant to this attack.
--
Bojan
4 Comments
Wireshark 1.2.0 released
Thanks to ISC reader Bob who told us that Wireshark updated one of our favourite tools. This is a new release branch of Wireshark and they have added many new features including a 64-bit Windows (x64) installer, Macintosh OS X support has been improved, GeoIP lookups has been added to name a few. This release also comes with WinPcap 4.1beta5 rather than the older stable 4.0.2.
References:
Release announcement: http://www.wireshark.org/news/20090615.html
Release Notes and bug fixes: http://www.wireshark.org/docs/relnotes/wireshark-1.2.0.html
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
Teaching Comprehensive Packet Analysis in Ottawa, ON this coming September
0 Comments
Web server survival time research
Lately, I have been writing new labs for an update version of my DEV 422 Defending web app course. One of the labs is about log analysis, so naturally, I would want to get some really cool and neat logs for my students. As some of you may know, I help run the Web honeypot project so I have access to tons of logs but it would be much more interesting to see logs from real systems and real compromise.
I decided to setup my high interaction honeypot using a real system and lots of monitoring and limiting outbound control. My platform of choice? Windows 2000 fully unpatched box running IIS and having only port 80 exposed. I put that on a typical DSL connection and waited...
The wait was very long. At some point, I wondered if the box is even accessible so I got a few other handlers to check out accessibility for me and they have all proven that the W2K box works (fully unpatched too, unicode traversal is great for testing).
I waited and waited; 2 weeks passed by, nothing happened. My box was not compromised at all. There were a total of 8 scanning attempts but they look random and no one ever did anything harmful.
I suppose my actions raised more questions than answers,
- Does attackers stay away from the DSL ranges while scanning for web flaws? My other servers get much more scanning attempts.
- Are any bad guys scanning thru the whole Internet looking for infrastructure type of flaws anymore? Application flaws are so much more common.
Your thoughts are welcomed..... Write in to us via Email or leave us comments.
P.S. If you have cool web app compromise logs for donation, please write in via the contact form. Many thanks.
------------------------
Jason Lam, http://twitter.com/jasonlam_sec
https://blogs.sans.org/appsecstreetfighter/
2 Comments
Useful browser addon - WOT
I have been playing around with the WOT browser add-on for couple weeks with good results. WOT stands for Web Of Trust, it is a community knowledge based system where information on websites are shared. After installing the add-on, the links from search engines are tagged with extra symbols showing whether the site's "reputation" level. Very simple to understand, red means potentially bad site and green means good site.
As you can imagine, lots of links to malicious sites flow through my mailbox every day, WOT toolbar was able to identify most of them (I only recall a few instances where it failed). On the other hand, some of the seemingly legit site seems to be tagged as dangerous but these are rare and I honestly didn't look too deeply as to whether they have real bad stuff or not.Â
Overall, I would recommend it to average users as an extra layer of defense. Worthwhile to mention that it is available both in Firefox and IE. If you choose to use it, remember to contribute back to the project back by helping to rate sites as you visit them. Time to introduce my parents to this add-on. 
9 Comments
URL Shortening Service Cligs Hacked
A post over at Cligs talks about an intrusion with their URL shortening service. In essence, an malicious individual got in and edited all the destination URLs to point to freedomblogging.com, likely for nefarious purposes. This exposes two problems with URL shortening services.
1) Previously, malware domains tend to be easy to spot. The URLs tend to be less and less sensical as it is difficult to get a domain name that looks close enough to a legit site. However, with URL shortening you are using a well-known and "safe" domain. There is generally no way (for most services at least) to see the destination URL that a shortened URL points to. For twitter and facebook, URL shortening services are common and no one thinks twice of them. E-mail has become a less reliable means for phishing because of the anti-spam services involved. With URL shortening, it becomes easier because it "looks legit". It's little more than an accepted form of obfuscation.
2) Most URL shortening services are not highly financed (nor do they need to be). If a URL shortening service was penetrated, it would be easy to take a popular shortened URL and modify it to point to malware instead the intended "clean" site. This is what happened with Cligs.
The bad news: We are behind the curve on dealing with this threat.
The good news: Some simple steps could be used to help prevent this. "Blocklisting" malicious domains from URL shortening, deactivating known malicious shortened URLs and more real/near-time monitoring of what URLs get shortened to shorten the detection cycle.
--
John Bambenek
bambenek /at/ gmail /dot/ com
2 Comments
Iran Internet Blackout: Using Twitter for Operational Intelligence
One of the topics in the halls here at SANSFIRE is how twitter has been the one tool that has breached the attempt of Iranian national censors to control the information flow within and outside the country. Much of the media reporting on the violence that has resulted from the protests was first covered on twitter before it made the news. Can twitter be a useful intelligence tool? Kinda.
The problem with twitter, or for that matter any "as-it-happens" information, is that there is no good way to determine the reliability of that information. You can read some of the latest posts on the Iranian issue here. On of the top posts as I write this is that the Iranian Army itself is moving into Tehran to restore order. Is that, in fact, true? I tend to think not, but time will tell.
Because of the way "trending" twitter topics work, anyone talking about an issue will show up in that feed. That includes accounts just created today. Why does this matter? It's relevant because it would be trivial to put up "counterintelligence" via twitter. There is no tools with which to measure the "reputation" of the person posting the information. Number of followers and tweets helps, but most of the people posting information have followers in the hundreds which is a trivial amount of followers to acquire before even posting your first tweet.
An example I use in my criticism of emergency text messaging is that there have been incidents where false information led victims TO a threat instead of away from one. While there is some debate, the Omagh bombing in N. Ireland in 1998 arguably included this where the Real IRA called in a bomb threat to the court house by the car bomb was near a market center. The result was that the police evacuated people to the area the bomb actually. "Leading people to the threat" is a real danger in unreliable information and it is a tactic that's known. Bottom-line is that unreliable communications can be used just as easily by people who would feed in unreliable or intentionally false information (counter-intelligence).
From an information security perspective, the threat is leading people to malicious websites. Set up a blog with an archive of posts on the issue, "borrow" a few pictures of the conflict and post them. Tweet a message that says "live images of protestors being shot at" and point to your blog that also includes pre-tested malware that is known to be not detected by AV vendors. Twitter and social networking tools provide another mechanism to lead people to the cyber-threat where only e-mail was used before. Twitter has no "anti-spam" features, everyone talking about a subject shows up.
So while the use of twitter and other tools provide for a means to breach censorship rules of foreign regimes, it does not come without risks. Is the information valid? Is it leading you to malware infecting your machine?
P.S. I'm working on the intellectual exercise of developing a "honeypot" for twitter / social networking so we can get some visibility into those who would use those avenues to distribute malware. Feel free to send in suggestions.
--
John Bambenek
bambenek /at/ gmail /dot/ com
1 Comments
Iranian hacktivism
With the increase of violence in Iran due to the recently held election, it was just a matter of time when we will see some hacktivism. Similarly to some previous cases, we are again seeing people calling supporters of one or the other side to attack certain web sites. Back in January we saw Israeli proponents asking people to run a special program that will attack Palestinian web sites (http://isc.sans.org/diary.html?storyid=5638). It turned out that this "special" program was actually a Trojan horse, so obviously people behind it had a little bit different agenda.
Regarding the current events in Iran, it was interesting to see that proponents are inviting people to support their case over Twitter – they posted instructions on how to launch DDoS attacks against some Iranian sites as Twitter updates. It's clear that Twitter became increasingly interesting to hacktivists due to a large user base.
So far I've seen two groups launching DDoS attacks against Iranian web sites – in both cases we are talking about technically very, very simple attacks.
The first group created a special web page that supporters should visit. This web page is very simple – it creates 10 iframes, each iframe pointing to a different site in Iran. The visitor can then change the frequency which will be used to refresh iframe status. The browser will then regularly refresh every single web site from the list attached below. This is a poor man's DDoS; what's interesting is that I've seen a very similar method used by the Cyber Jihad program last year.
The second group uses a bit more advanced approach. They created a .NET application called "Low Orbit Ion Canon". This is a very simple HTTP and TCP/UDP flooder, as you can see in the screenshot below. All the user has to do is enter the target web site and/or IP address and click on the Launch button after which the tool will start the attack in the background.
The two attacks described show that hacktivism is still in its early days – both applications have some errors and are relatively easy to mitigate and analyze (even after the authors of LOIC used EZIRIZ's .NET Reactor to protect the code).
We will keep an eye on the development of the situation, of course, and post additional diaries if there is something interesting.
--
Bojan
1 Comments
Drive-by Blackouting ?
Talk about "critical infrastructure protection"... If the facts behind this article over at "The Register" are true (and I have no doubt that they are), we are currently making our electricity grid more brittle and susceptible to attacks, and we even have stimulus money paying for it. Then again, installing "smart" power meters with broken security clearly does have a stimulus effect - it will create lots of jobs like "Meter Patcher", "Meter Replacer" and "Grid Restarter". But if the average music sharing P2P program uses better crypto than a remotely controllable network of power meters ... then it's probably high time to start paying attention. (Thanks to ISC reader Martin for the contribution)
0 Comments
SANSFIRE 2009 Starts Tomorrow
SANSFIRE 2009 starts tomorrow and will be your best opportunity to meet various handlers (about 15 will attend during the conference) and learn about what they are involved in at the ISC. In addition to a large number of training classes (23 week long classes, 11 1-3 day classes) we got a number of exciting evening talks scheduled.
SANSFIRE runs from 13-22 June in Baltimore, MD. For details, see the course overview and the SANS@Night schedule as well as the special event schedule.
In case you missed it and cannot be at the conference, we will stream all evening talks. You will need to sign up for individual talks, but it is free via Elluminate. The URL to register for evening talks is here.
Guy Bruneau IPSS Inc. gbruneau at isc dot sans dot org
0 Comments
From the mailbag: Sympatico hacked, TCP dead, SHA-1 out, Belarus DoS
In other news this week...
Sympatico may have been hacked, TCP might be dead, SHA-1 may be on its way out, and political hacktivism.
A major ISP in Canada, Sympatico, appears to have had a breach of their web site according to Websense, malicious code appeared to have been inserted briefly. More info is here http://securitylabs.websense.com/content/Alerts/3416.aspx
A major issue with the TCP protocol implementation may lead to Denial of Service (DoS) to virtually any web site. Reported in Phrack issue 66.
The SHA-1 hashing algorithm is showing its age, researchers may be on their way to creating practical collisions. The paper is found here. http://eprint.iacr.org/2009/259.pdf
Arbor reports that Denial of Service attacks have been ongoing against a Belarus news site. The article is here. http://asert.arbornetworks.com/2009/06/ddos-floods-in-belarus-political-motivations/
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
2 Comments
Green Dam
China has mandated that software that can block certain sites and content be installed on all new computers. While this is certainly very interesting from a sociological and political point of view, the security implications are significant. Millions of computers must be running this particular piece of software. Even more so is that the software appears to be buggy. User experiences indicate that it does not work very well, and makes the computer sluggish. Analysis of the code has identified a number of vulnerabilities, at least one of which is exploitable. More than one remotely exploitable buffer overflow has been reported, with exploit code that is delivered via IIS or potentially any web site. It takes advantage of the Green Dam software as it interacts with Internet Explorer or other browsers. Think of the damage that can be done with a botnet or botnets with somewhere around 50 million systems! Another possible impact is the potential for other parties to monitor Internet activity, control, steal information, or otherwise interrupt the majority of computers in a single country. The analysis by Scott Wolchok, Randy Yao, and J. Alex Halderman of the The University of Michigan is available here. The exploit code certainly is not difficult to find.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
0 Comments
Google updates for Chrome
Google has released an update for Chrome, their own web browser. From their advisory here: "Google Chrome's Stable channel has been updated to version 2.0.172.31 to fix two security issues in WebKit." CVE-2009-1690 is a memory corruption which can lead to arbitrary code execution within the sandbox. CVE-2009-1718 is an information leak. Both CVE's name Apple Safari, however they also affect Google Chrome.
Cheers,
Adrien de Beaupré
Intru-shun.ca Inc.
0 Comments
DTV Flag Day
Today is transition day for digital television in the United States. This reminds me of "flag day" many years ago on January 1 1983, the day when the ARPANET changed from NCP to the TCP/IP protocol suite. It wasn't the happiest day for many, but if we had not gone through that transition then there would be multiple protocols and many incompatible networks today. OK, maybe somewhere along the way we'd have done the conversion to TCP/IP but the longer we would have waited the harder it would have been to do. So while moving to DTV may be painful, at least it's being done, and we can soon take advantage of the new frequencies for things like wireless broadband and improved features available to over-the-air digital TV broadcasts.
Marcus H. Sachs
Director, SANS Internet Storm Center
0 Comments
Firefox 3.0.11 is available
One thing is for sure! Our ISC readers love their Firefox.
We have received a number of emails telling us that Firefox version 3.0.11 is now in the update pipeline. Firefox 3.0.11 provides a number of fixes for security vulnerabilities.
Release notes are available here.
-- Rick Wanner - rwanner at isc dot sans dot org
0 Comments
Dshield Web Honeypot going beta
We started the Dshield Web Honeypot project roughly one year ago. The goal of this project is to replicate what Dshield had done for the community on the web application side. We are not trying to detect targeted attacks but fast scanning and replicating threats that has potential to affect the whole community quickly.
Similar to the original Dshield project, we rely on volunteers to feed us logs. In the case of web logs, it is not easy to collect detailed log (eg. HTTP header, HTTP body) by using the web server logs alone, this is why we have a PHP + Apache based client component for volunteer to install as their log collector (or honeypot). We are announcing today that the client software for this project is turning beta. Special thanks to the volunteers on this project
For this project to be successful, we need your support in sending us logs. The honeypot client software can be downloaded from the Dshield portal under My Information (login first).
For the impatient, here are the high level instruction.
The installation start off with downloading and untar'ing the code into a directory. Run the config.php under /lib to configure the client. Then run the update-client.php to ensure you have the latest copy of all the code. This process should be followed by running of the update-template.php, which updates all the web pages in the honeypot. After that, it's a matter of configuring the Apache virtual host (sample config under /docs) and it should be all set.
Once you are submitting web logs, the Dshield main portal page should let you view all the logs you are submitting (1 hr time delay). Let us know how this is working out for you.
-------------------------------------------------
Jason Lam - http://twitter.com/jasonlam_sec
4 Comments
WHO Declares Flu A(H1N1) a Pandemic
Several media outlets are reporting that the World Health Organization (WHO) has officially declared the A(H1N1) flu outbreak a pandemic.
More information is available at the following sites:
http://www.nytimes.com/2009/
http://www.who.int/csr/disease/swineflu/en/index.html
www.euro.who.int/influenza/AH1N1/20090611_11
The April diary on this issue can be found here.
The SANS Leadership Lab Pandemic Planning page is also worth a look.
From a security point of view we can expect a new rash of bogus domains, phishing and malware attacks. So as usual be diligent.
-- Rick Wanner rwanner at isc dot sans dot org
0 Comments
MIR-ROR Motile Incident Response - Respond Objectively Remediate
Anybody who reads my diaries has long since figured out that I am a big fan of the Sysinternals tools. So when long-time reader, regular contributor, and full time Uber-Dork Russ McRee from HolisticInfoSec.org pointed me at a new incident response tool based on the Sysinternals tools it immediately piqued my interest..
The tool is MIR-ROR - Motile Incident Response - Respond Objectively Remediate. MIR-ROR is a live response tool for Windows machines based on Sysinternals tools and other useful tools originally put together by Microsoft Forensics guru Troy Larson and now being maintained by HolisticInfosec.org. More info about MIR-ROR can be found on the HolisticInfoSec Blog and reviewed in the ISSA Journal Toolsmith series. The tool itself can be found at Codeplex.
I haven't had a chance to review MIR-ROR myself, so I would appreciate any of you who have spent any time with MIR-ROR to please provide your opinions via our contact page. I will summarize as the day goes on.
-- Rick Wanner - rwanner at isc dot sans dot org
0 Comments
Java 6 update 14 released
Sun has updated Java to 6u14. Details can be found here:
http://java.sun.com/javase/6/webnotes/6u14.html
Do note that while the list of bugs fixes is impressive, they also state: "This feature release does not contain any new fixes for security vulnerabilities to its previous release".
Many thanks to Roseman for providing the link to the details.
--
Swa Frantzen -- Section 66
0 Comments
SysInternals Survey
Hands-down the best tools for determining what is going on on a Windows system are Mark Russinovich's and Bryce Cogswell's Sysinternals Tools. Frequent contributor Roseman has pointed out that Microsoft is asking for your help improving the Sysinternals tools. Over at the Microsoft Technet blog they are requesting Sysinternals users to take a short survey.
If you are a Sysinternals user please consider taking five minutes to contribute to their future.
-- Rick Wanner - rwanner at isc dot sans dot org
0 Comments
Adobe June Black Tuesday upgrades
In the past it was by accident, but from now on it'll be by policy: Adobe will add to the monthly workload by releasign their patches on a monthly schedule to concide with the Microsoft scheme.
June yielded just one bulletin:
Affects Acrobat (Reader) on Windows and Mac
This fixes following CVE names:
CVE-2009-0198, CVE-2009-0509, CVE-2009-0510, CVE-2009-0511, CVE-2009-0512, CVE-2009-0888, CVE-2009-0889, CVE-2009-1855, CVE-2009-1856, CVE-2009-1857, CVE-2009-1858, CVE-2009-1859, and CVE-2009-1861.
Note that the bulletin states "Additionally, this update resolves Adobe internally discovered issues".
Among the list are a number of JBIG2 filter vulnerabilities.
JBIG2 filter vulnerabilities have been exploited in the wild, so you really want this upgrade now.
--
Swa Frantzen -- Section 66
0 Comments
Microsoft June Black Tuesday Overview
Overview of the June 2009 Microsoft patches and their status.
| # | Affected | Contra Indications | Known Exploits | Microsoft rating | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS09-018 | A vulnerability in freeing memory on Windows 2000 server leads to remote code execution and another one leads to DoS on active directory on Windows 2000 and 2003 server as well as ADAM installation on XP and server 2003. Replaces MS08-060 and MS08-035. |
|||||
| Active Directory CVE-2009-1138 CVE-2009-1139 |
KB 971055 | No known exploits | Severity:Critical Exploitability:1,3 |
N/A | Critical | |
| MS09-019 | A cumulative patch for IE. The worst of them leads to random code execution. Affects IE5.01 up to and including IE8. Replaces MS08-014. |
|||||
| Internet Explorer CVE-2007-3091 CVE-2009-1140 CVE-2009-1141 CVE-2009-1529 CVE-2009-1530 CVE-2009-1531 CVE-2009-1532 |
KB 969897 | CVE-2007-3091 is publicly known with claims going as far back as May 2004 (unverified). | Severity:Critical Exploitability: 3,3,3,1,3,2,2,3,3 |
Critical | Important | |
| MS09-020 | Input validation errors in the WebDAV extentions for IIS allow privilege escalation. | |||||
| Webdav IIS CVE-2009-1122 (CVE-2009-1535) CVE-2009-1676 |
KB 970483 | CVE-2009-1535, better known as CVE-2009-1676, is publicly known and covered in SA 971492. | Severity:Important Exploitability:3,1 |
N/A | Important | |
| MS09-021 | A number of vulnerabilities allow random code execution. Updates for Office for Mac versions are bundled with the fixes for MS09-017 and MS09-027. Replaces MS09-009, MS08-057 and MS08-074 |
|||||
| Excel CVE-2009-0549 CVE-2009-0557 CVE-2009-0558 CVE-2009-0559 CVE-2009-0560 CVE-2009-0561 CVE-2009-1134 |
KB 969462 | No known exploits | Severity:Critical Exploitability: 2,1,2,1,3,1,1 |
Critical | Important | |
| MS09-022 | Vulnerabilities in th eprint spooler allow random code execution, Information leaks and Privilege escalation. Replaces MS07-021. |
|||||
| print spooler CVE-2009-0228 CVE-2009-0229 CVE-2009-0230 |
KB 961501 | No known exploits | Severity:Critical Exploitability: 1,3,1 |
Important | Important | |
| MS09-023 | A vulnerability in generating file previews allows HTML scripting to run on affected clients. | |||||
| Windows Search CVE-2009-0239 |
KB 963093 | No known exploits | Severity:Moderate Exploitability:3 |
Important | Less Urgent | |
| MS09-024 | A buffer overflow vulnerability allows code execution on affected systems. Replaces MS08-072. |
|||||
| Works convertors CVE-2009-1533 |
KB 957632 | No known exploits | Severity:Critical Exploitability:1 |
Critical | Important | |
| MS09-025 | Multiple vulnerabilities allow privilege escalation. Replaces MS09-006. |
|||||
| Windows kernel desktop CVE-2009-1123 CVE-2009-1124 CVE-2009-1125 CVE-2009-1126 |
KB 968537 | Microsoft claims CVE-2009-1123 and CVE-2009-1126 are publicly known. | Severity:Important Exploitability: 2,1,1,1 |
Important | Important | |
| MS09-026 | A vulnerability in the RPC marshalling engine allows privilege escalation and random code execution. Replaces MS07-058. |
|||||
| RPC CVE-2009-0568 |
KB 970238 | Microsoft claims CVE-2009-0568 is publicly known. | Severity:Important Exploitability:2 |
Important | Important | |
| MS09-027 | Multiple vulnerabilities allow random code execution. Updates for Office for Mac versions are bundled with the fixes for MS09-017 and MS09-027. Replaces MS08-072. |
|||||
| Word CVE-2009-0563 CVE-2009-0565 |
KB 969514 | No known exploits | Severity:Critical Exploitability:2,1 |
Critical | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them
--
Swa Frantzen -- Section 66
3 Comments
Safari 4.0 released - contains security fixes
Apple released yesterday an update to Safari 4.0 (which had been in beta for quite some time)
The release also contains a large number of fixes for security vulnerabilities:
CFNetwork: CVE-2009-1704, CVE-2009-1716
ImageIO: CVE-2009-0040
International components for Unicode: CVE-2009-0153
libxml: CVE-2008-3281, CVE-2008-3529, CVE-2008-4409, CVE-2008-4225, CVE-2008-4226
Safari: CVE-2009-1682, CVE-2009-1706, CVE-2009-1707, CVE-2009-1708
Safari windows installer (no CVE name)
Webkit: CVE-2006-2783, CVE-2008-1588, CVE-2008-2320, CVE-2008-3632, CVE-2008-4231, CVE-2009-1681, CVE-2009-1684, CVE-2009-1685, CVE-2009-1686, CVE-2009-1687, CVE-2009-1688, CVE-2009-1689, CVE-2009-1690, CVE-2009-1691, CVE-2009-1693, CVE-2009-1694, CVE-2009-1695, CVE-2009-1696, CVE-2009-1697, CVE-2009-1698, CVE-2009-1699, CVE-2009-1700, CVE-2009-1701, CVE-2009-1702, CVE-2009-1703, CVE-2009-1709, CVE-2009-1710, CVE-2009-1711, CVE-2009-1712, CVE-2009-1713, CVE-2009-1714, CVE-2009-1715, CVE-2009-1718
Needles to say, this update comes as highly recommended for anybody using safari.
Note some CVE names are quite old ... e.g. CVE-2006-2783 was first discussed more than 3 years ago in Mozilla (June 1st, 2006) and was fixed by Apple for iPhone and iPod almost a year ago (July 11th, 2008).
--
Swa Frantzen -- Section 66
0 Comments
Kloxo (formerly Lxadmin) Vulnerability Exploited
We've had several readers (Kirk being the first) alert us to a vulnerability in Klaxo being exploited in at least one location.
It has been reported that pretty much anything hosted on VAserv is down and updates are being posted to that page.
Daniel writes "The Kloxo/HyperVM solution is popular with cheap hosts. I imagine it's only a matter of time before other installations are hit as these exploits are trivial to reproduce/customize." - Great
Happy Monday everyone.
Christopher Carboni - Handler On Duty
0 Comments
Scareware Tactics
It has been an interesting week. Lots of activity, but a slightly weird. It's a beautiful day at the beach, so I'm going to pose you all a question that has peaked my interest this week.
Have any of you ever dealt with scareware or ransomware in your environment? Do you have a written strategy for handling this type of incident in your incident response plan? Have you gotten your legal team involved? Can you give us the big picture and help the rest of us get ready for this type of incident? No enterprise identity necessary.
I'd like to hear about your strategies. Please send me your comments. I'll post them as we get some comments.
1 Comments
Browsers indicating Sourceforge.net connection issue
We've had a couple of reports about Sourceforge connection issues. Browsers display different messages like "Connection Interrupted - The document contains no data. - The network link was interrupted while negotiating a connection. Please try again" or the "connection is being reset while the page/s are loading". Any additional facts will be appreciated and posted.
Thanks for the reports Brandon and anonymous ( ; ^ )..
2 Comments
ARRA/HIPAA Breach Reporting Dates Approaching
September 14th, 2009 or "thereafter"
The American Recovery and Reinvestment Act of 2009 was signed into law on February 17, 2009. The "Breach" notification portion of the law goes into effect 30 days after the Secretary of HHS "promulgates" "interim final regulations". Although those are not "promulgatedt" yet, a date can be calculated.
The way I calculate this, August 16th would be when the last day "interim final regulations" could be published, add 30 days, and the notification requirements "will apply to breaches of unsecured PHI" on September 14th, 2009 or "thereafter".
American Recovery and Reinvestment Act of 2009, Subtitle D—Privacy, Sec. 13402. Notification in the case of breach.
Related Diary
Unusable, Unreadable, or Indecipherable? No Breach reporting required
0 Comments
Don't TRY to hit me... Hit me!
Remember that scene in the Matrix where Neo does that "come 'n get me" hand wave thing at Agent Smith? Generally speaking, there's a really good reason you NEVER do stuff like that. When you get to thinkin' you're all cool and start taunting people, an ass-whoopin' usually follows. And, without fail, a few splendid cinematic moments later, Keanu is laying on the ground, bleedin', after having been used to rearrange the masonry in a subway tunnel.
Obviously having never learned the "taunting->ass-whoopin'" connection, the folks over at StrongWebmail decided to throw down against the collective badness of the Internet and, apparently, got their butts handed to them in a paper bag. Our friends over at El Reg are reporting that their "Hack our CEO's webmail account" contest ended... well.. pretty much like you would expect.
Here's some free marketing advice to any security company contemplating a "Hack Us If You Can" contest: DON'T. There is no upside to these things, people. If no one hacks you, it likely only proves that no one cares... and if your contest turns out the way that StrongWebmail's did, you can kiss $10K bucks and your reputation goodbye all in one fell swoop.
Update: Mike Bailey, one of the trio of researchers involved in popping the account, has put up a blog entry that doesn't say much, but confirms the hack.
--
Tom Liston - Handler On Duty - InGuardians, Inc.
0 Comments
Chalk one up for the good guys
Based on a complaint filed by the U.S. Federal Trade Commission (FTC) in the San Jose Division of the U.S. District Court for the Northern District of California, a temporary restraining order has been issued, effectively shuttering a rogue Internet Service Provider that allegedly recruits, knowingly hosts, and actively participates in the distribution of spam, child pornography, and other harmful electronic content.
The complaint alleges that Pricewert LLC, which does business under a variety of names including 3FN and APS Telecom, actively shielded its criminal clientele by either ignoring take-down requests issued by the online security community, or shifting its criminal elements to other Internet protocol addresses it controlled to evade detection.
The FTC also alleges that the defendant engaged in the deployment and operation of botnets – in filings with the district court, it is alleged that more than 4,500 bots were controlled by command-and-control servers hosted by 3FN.
More information is availble from the FTC's website.
0 Comments
Targeted e-mail attacks asking to verify wire transfer details
There is a new e-mail wave doing the rounds (we have reports from June 3 & 4). It is a very targeted e-mail attack against different organizations, that contains an attached malware specimen in the form of a RTF file, called "details.rtf". The mail asks the victim to verify a wire transfer, being the malicious attachment the alleged wire statement.
In some of the cases, the victims are indeed financial personel within the target organization in charge of daily wire transfers. Time to spread an internal awareness campaign in your financial departments!
The current AV detection rate is low (according to VirusTotal) for the samples we have received:
- 7/39 - SHA1 : 0f7288043f556542744fd2c87511ff002b5d5379
- 4/39 - SHA1 : e248fd659415f15d1238063efd1f122f91ac071c
The spare phishing e-mail looks like this:
--
From: Kenneth Duford [mailto:ken.duford@<VARIOUS-DOMAINS>]
Sent: Wednesday, June 0X, 2009 XX:XX PM
To: <VICTIM E-MAIL>
Subject: Re:Please verify wire details <VICTIM NAME>
The wire transfer has been released.
BENEFICIARY : <VICTIM NAME>
ABA ROUTING# : XXXX1197
ACCOUNT# : XXX-XXX-XXX394
AMMOUNT : $17,653.15
<TARGETED VICTIM COMPANY NAME>
Please check the wire statement attached and let me know if everything is correct.
I am waiting for your reply.
Kenneth Duford
--- On Sun, 02/06/09, <VICTIM NAME> <VICTIM E-MAIL> wrote:
From: <VICTIM NAME> <VICTIM E-MAIL>
Subject: wire transfer
To: ken.duford@<VARIOUS-DOMAINS>
Date: Mon, 1 June 2009, 10:47 AM
We still haven't received the wire transfer.
Thank you
<VICTIM NAME>
--
Some of the domains we have seen in the "From" field are pinnaclerestaurantcorp.com and teoinc.com.
An early analysis thanks to fellow handler Pedro confirms the exe (or .scr) component is trying to connec to "abfforms.com", with this specific URL: "/bluehost/index.php?open=myid". Currently the site is suspended.
Thanks to the ISC readers (that want to remain anonymous) for the initial details and samples.
--
Raul Siles
www.raulsiles.com
1 Comments
Malware targetting banks ATM's
Interesting recent article (June 2009) about evolving malware specimens targeting and compromissing bank ATM (Automated Teller Machines) devices in Eastern Europe. It complements a previous similar article (March 2009, original post) . Additional technical details are available here (PDF file).
The most interesting sections are its advanced ATM specific capabilities (hey, the ATM has a printer, so let's use it), the backdoor management interface (with different privilege levels), the option to force the machine to dispense all its cash, and that it works against ATM's from multiple vendors (although all ATM's were Windows XP based).
The main point is, really, how did the ATM's get infected in the first place? Physical access is mentioned (insider threat?), but I wonder: Would we see this kind of malware silently spreading through the banks private financial networks?
Do you trust your bank ATM's?
--
Raul Siles
www.raulsiles.com
3 Comments
New version (v 1.4.3.1) of BASE available
A new version of BASE (v.1.4.3.1) has been released, fixing a number of XSS flaws as well as a potential SQL injection flaw that have existed through numerous releases of BASE. BASE is a web-based interface to perform analysis of network intrusion data gathered by Snort. You can download the latest version here.
As these vulnerabilities were publicly announced previously on the Internet, without prior notification to Kevin Johnson (main BASE author) or the BASE project team, I want to emphasize how important responsible full disclosure is. Specially for open-source projects, where the authors devote their time to make the project freely available for everybody, it is fair to let them know first and give them a reasonable time to fix the vulnerability. In this case, only a few days (in particular 6 days) after the announcement a new version was ready. Not bad in my opinion.
Additionally, these flaws can be exploited being authenticated or not, depending on your BASE set up. Still today, lot of people do not require authentication to use BASE, which is a mistake. If it is your case, please, act as soon as possible!
Finally, as we have seen in the past a few times, do not expose your BASE web interface to the whole Internet. Keep it private within a protected management network.
--
Raul Siles
www.raulsiles.com
2 Comments
Another Quicktime Update
Apple released another Quicktime update, version 7.6.2. This update applies to Mac OS Xv10.4.11, OS X v10.5.7, Window Vista and Windows XP SP3. It looks like the update takes care of 10 vulnerabilities. All of the vulnerabilities stem from viewing a maliciously crafted movie or picture file.
The second link says that this update includes changes that increase reliability, improve capatibility and enhance security. It also says that this update improves the compatibility with Apple ProRes media and improves ITunes support. (Interesting that they bundled these in with a security update).
Make sure that you pay attention to the updater. It looks like there are 2 choices for the update. Just the update or the update and ITunes. If don't have ITunes it looks like it would install it.
1 Comments
Yet another "Digital Certificate" malware campaign
Thanks to ISC reader Tom for passing on yet another socially engineered attempt to install malware in victim's PCs.
This time a "Bank of America Digital Certificate Updating" scheme is used, where a victim of the luring EMail is directed to a fake website that looks like this:
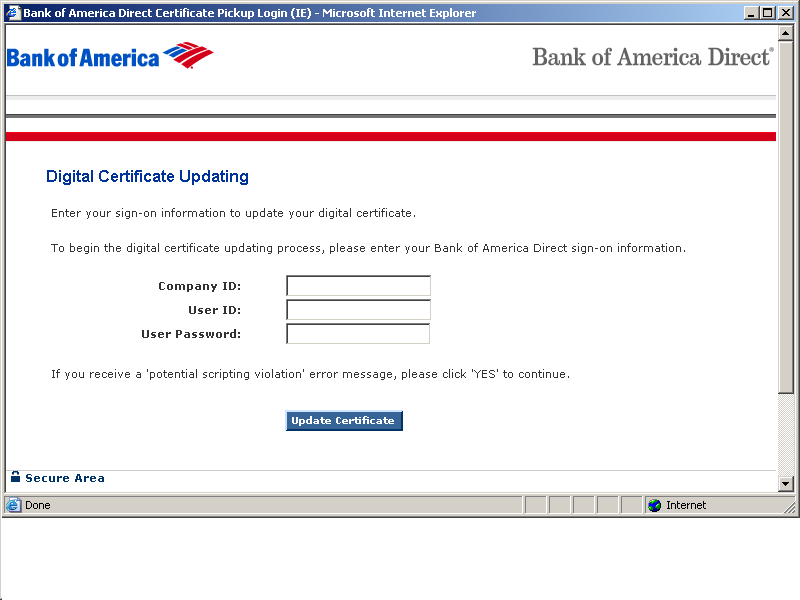
(I really like the "If you receive a 'potential scripting violation'... advice heh-heh)
Using the <Update Certificate> button here will net you a piece of Malware that has approximately %30 AV coverage (as indicated by VirusTotal). A quick analysis of said malware shows probable signs of, suprise-suprise, Waledac...
G.N. White
Handler on duty (no certificate necessary)
0 Comments



1 Comments