Matryoshka Phish
Reader Frank submitted a suspicious email with attachment: a score of zero on VirusTotal, but McAfee warned for an exploit. Taking a look at the content, Frank notice content that looked like encrypted code.
This is the suspicious content:
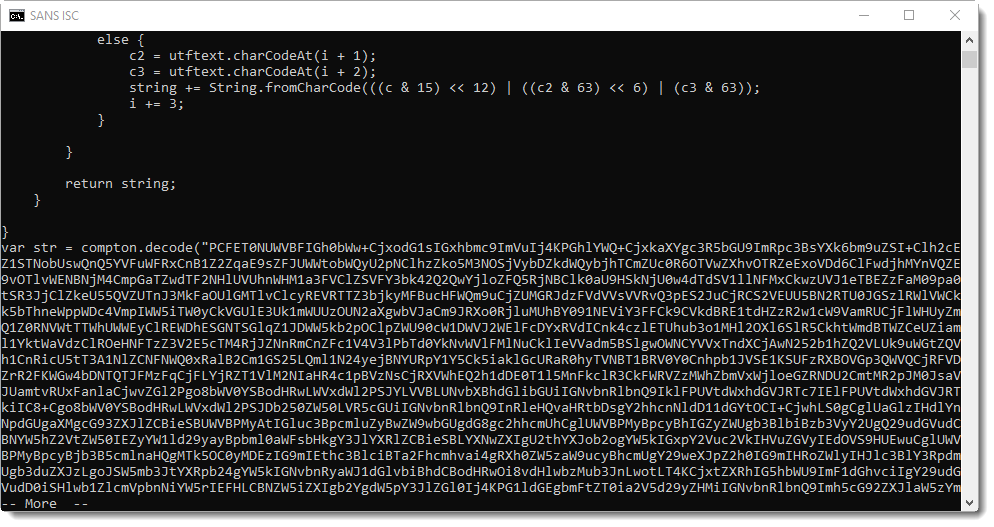
This looks like BASE64 encoded content.
A tip: if you encounter content that looks encoded or encrypted, analyze it with my base64dump tool. This tool recognizes different kinds of encodings, not only BASE64. Use base64dump with option "-e all" to try out all encodings it supports. This will give you output like this:
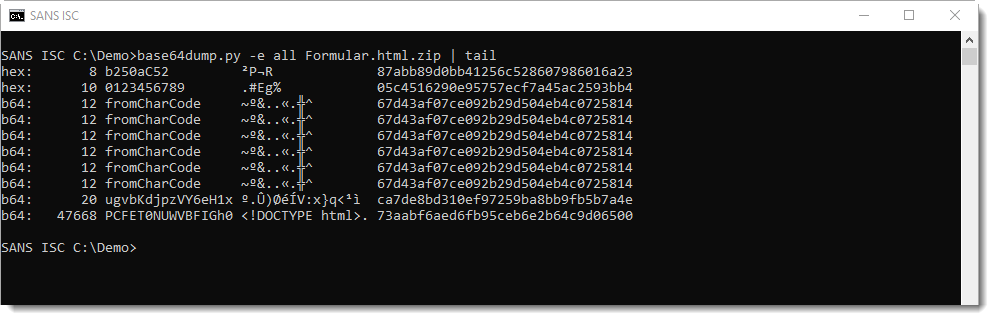
All decoded strings are listed, from shortest to longest. The longest decoded string is 47668 characters long, and is BASE64 encoded (b64). The decoded string starts with "<!DOCTYPE html>": it's an HTML document encoded inside an HTML document.
Looking at the content of the decoded document, I see many German words related to banking. Hence this might be a phishing email to collect banking details. When it comes to the analysis of complex HTML forms, I like to take a look at the document with a browser (in a disconnected virtual machine). A picture is worth a thousand words ...
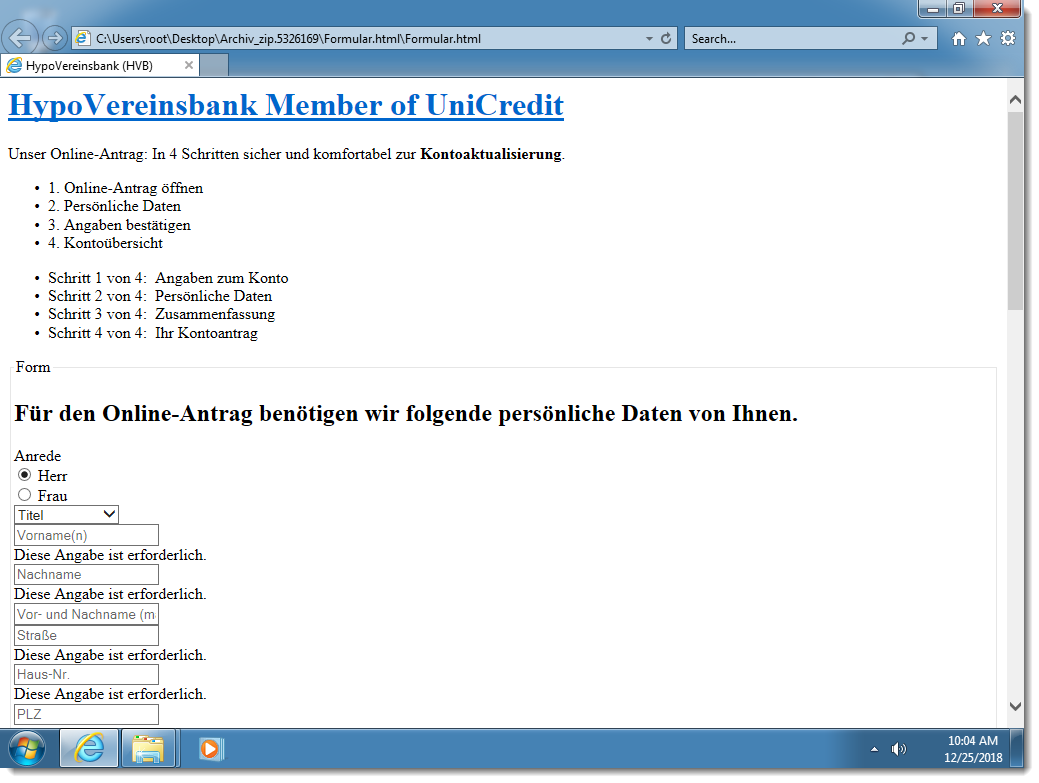
The content of this form has to be delivered to the phisher. Via HTTP or email, for example. To quickly search for URLs and emails in the HTML document, I use my re-search tool with option "-n all" to look for different types of IOCs like URLs and email addresses:
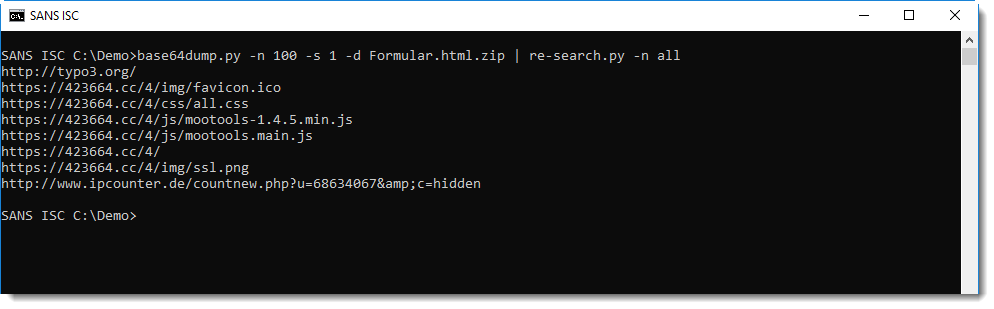
The last URL looks like a web page counter, but it's not for the phishing page, as the stats go back many years:
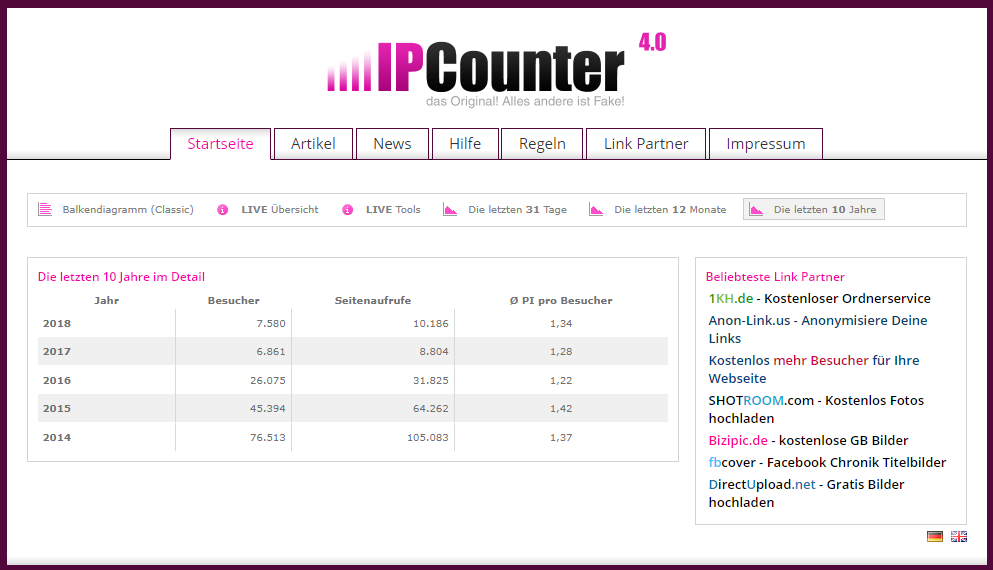
And I would like to hope that there haven't been 150.000 victims falling for this phish...
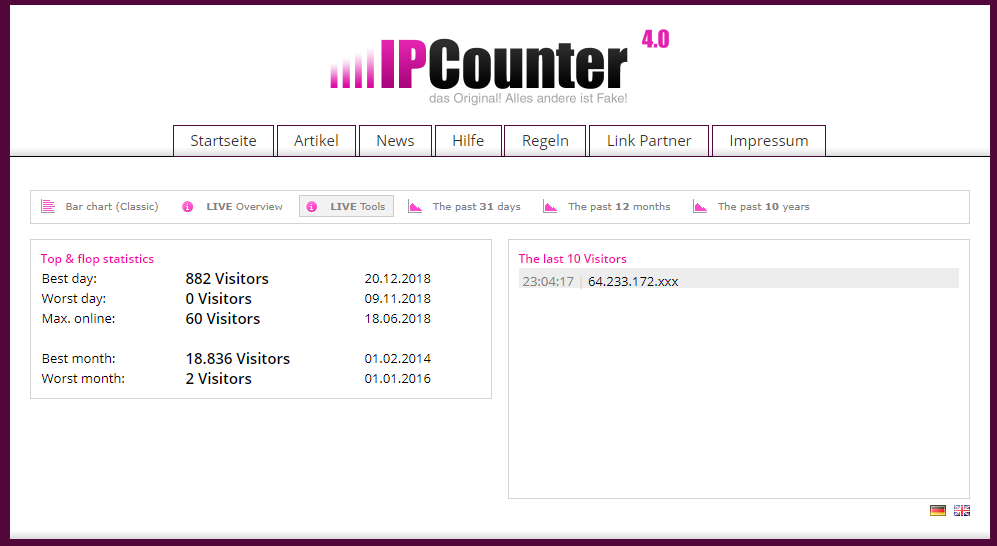
Still, we can get an indication of the success of this phish, with the following statistics:
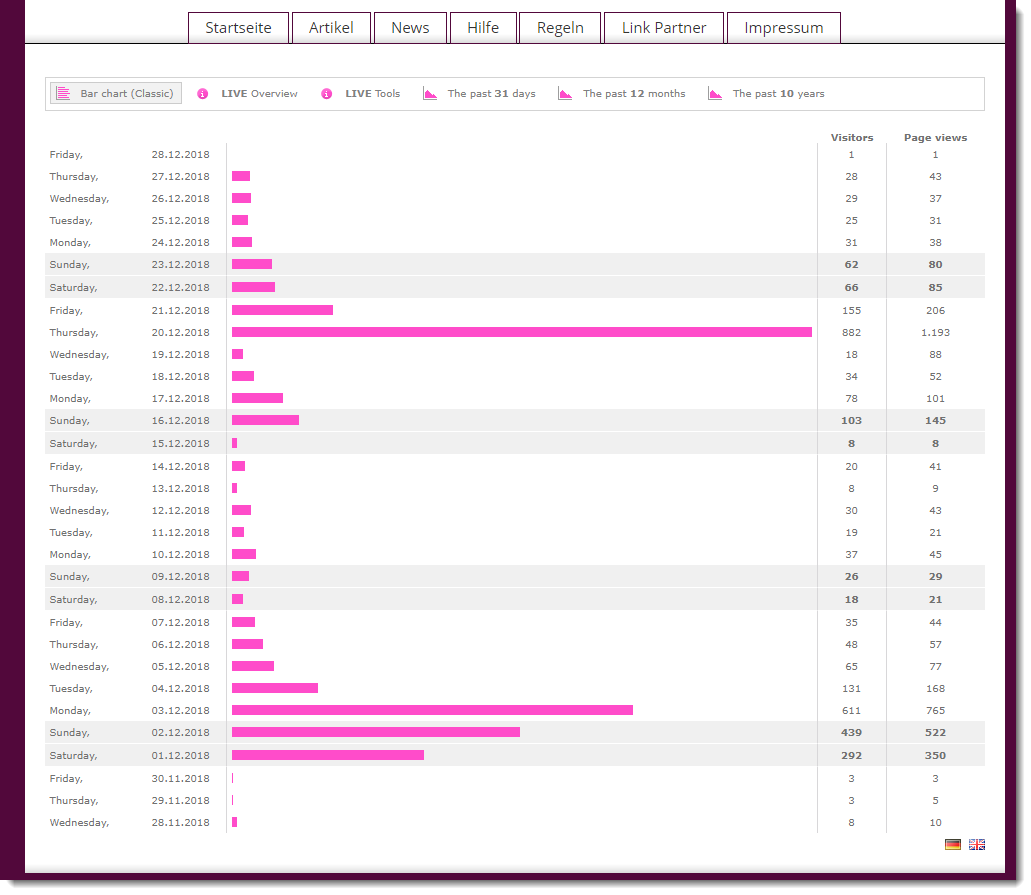
The most popular day is Thursday 20-12-2018 with 882 visitors, and Frank submitted this sample Wednesday 19th ...
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com



Comments
The trick is here to find the execute fucntion and replace it by a little script to write the code to a file.
In this way you can see what woul be excuted.
For example :
Set objFileToWrite = CreateObject(“Scripting.FileSystemObject”).OpenTextFile(“C:\code.txt”,2,true)
objFileToWrite.WriteLine(<excute>)
objFileToWrite.Close
Set objFileToWrite = Nothing
Anonymous
Dec 28th 2018
6 years ago
Anonymous
Dec 28th 2018
6 years ago