TCP/5000 - The OTHER UPNP Port
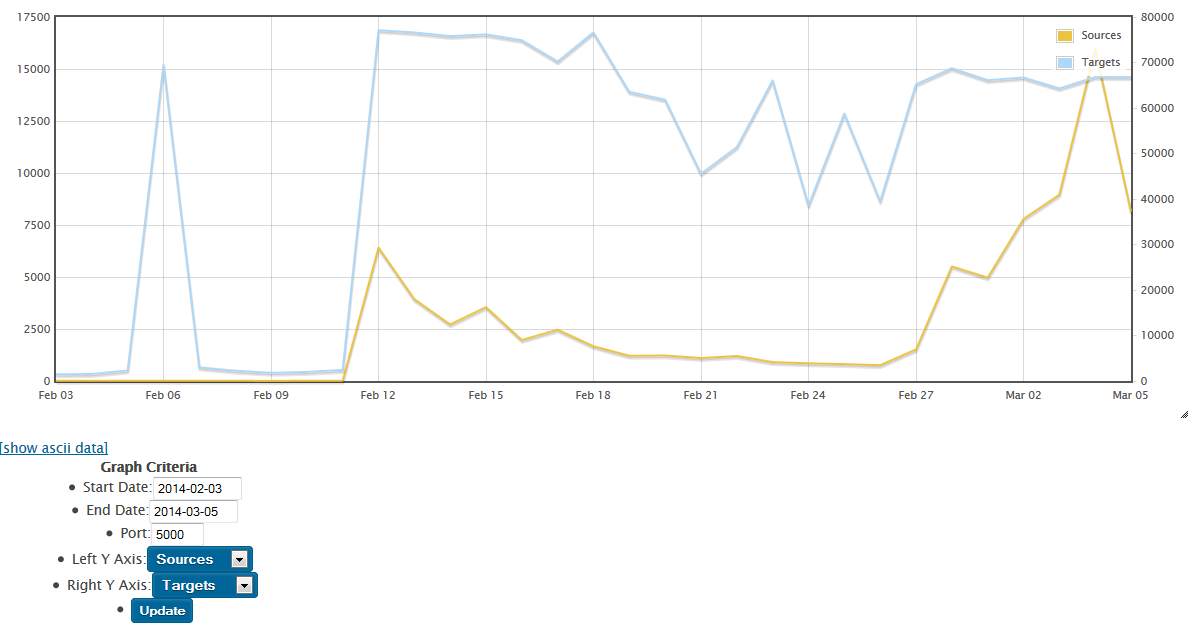
We've all read a lot about the scans and exploits of UPNP (Universal Plug N Play), on UDP port 1900. Jens, one of our readers, pinged us this morning with a question about an uptick he was seeing in TCP/5000, which is also listed as UPNP - who knew? (not me, that's who!)
After a quick check, I'm seeing an uptick in attack activity on TCP/5000 starting in mid-February, both in our dshield database and on various customer firewalls. Our reader was seeing his attacks come from an IP allocated to China, but I'm seeing more attacks sourced from the US.
Does anyone have any of these attack packets captured, preferably more than just SYN packets?
Or if anyone has a sample of the attack software or any malware involved, we'd of course love a sample of that as well !
===============
Rob VandenBrink
Metafore


Comments
Anonymous
Mar 6th 2014
1 decade ago
Anonymous
Mar 6th 2014
1 decade ago
Since the discovery of a couple of remotely exploitable critical vulnerabilities this year, I'm not surprised it gets targeted.
Anonymous
Mar 6th 2014
1 decade ago