Strings Analysis: VBA & Excel4 Maldoc
Malware analysis is difficult.
But there is one method that everybody can follow, even without command-line skills: strings analysis.
This method consists of running a tool on a binary file, like a maldoc, to extract all plaintext strings. There are command-line tools to do this, and even GUI tools.
Of course, there are many ways to make strings analysis impossible, by making the plaintext strings unreadable. Simple file compression is an example.
Xavier's diary entry "Excel Recipe: Some VBA Code with a Touch of Excel4 Macro" malicious document uses a sophisticated method: it combines VBA and Excel 4 macros to download Qakbot. Despite this complexity, strings analysis can be performed on this maldoc to find the URLs.
I found a similar maldoc on VirusTotal (it's also on Malware Bazaar).
For this diary entry, I will analyze this maldoc with CyberChef:
First step: I add the maldoc as input:
Second step: I search for the strings operation:
Third step: I add the strings operation to the recipe:
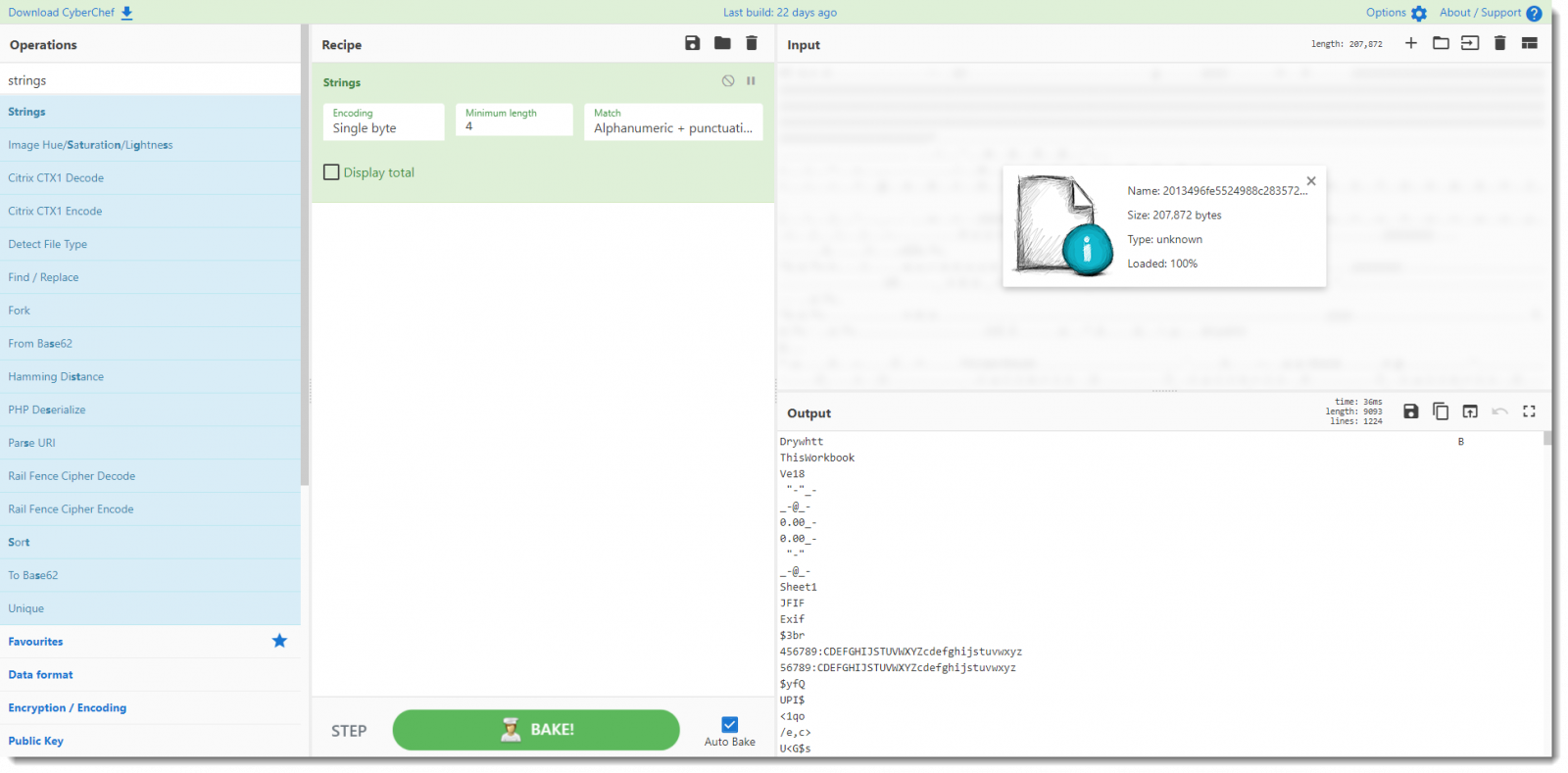
If I browse through the output, I will find the URLs. But I want to automate that too.
Fourth step: I search for the regex operation:
Last step: I add the regex operation to the recipe, and configure it to use the buildtin URL regex and output matches only:
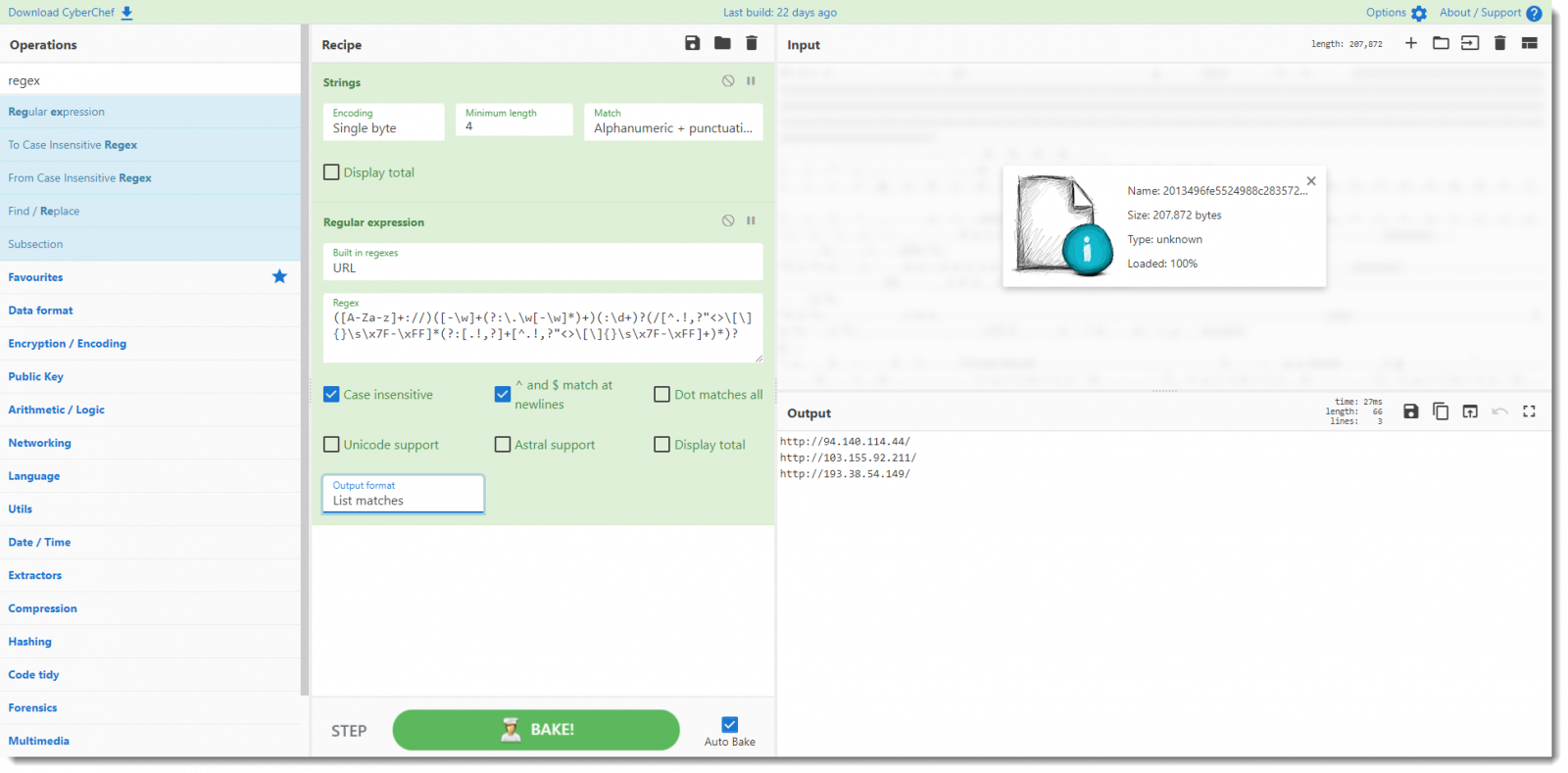
Now, these URLs are actually incomplete. The maldoc's script will add a path to these URLs that is a timestamp terminated with ".dat".
But despite that, the IPv4 addresses we found here, are good IOCs to get started.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments