What has Iran been up to lately?
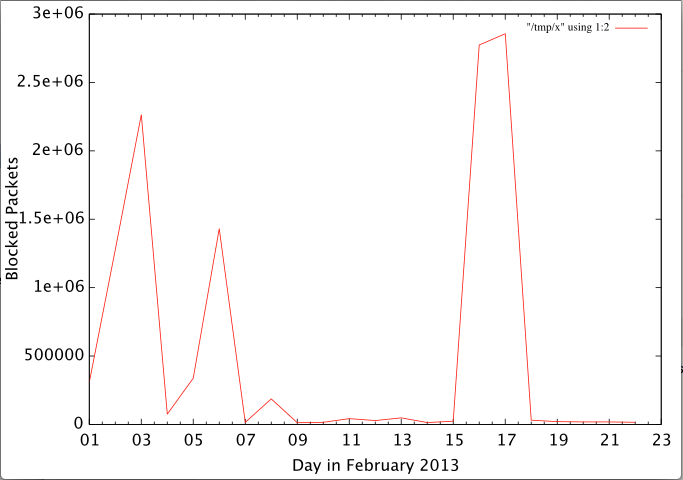
Going over some data earlier today, I noted that a few days ago, we had a notable spike of port scans from Iran in our DShield database. Iran is "spiking" at times, in part because we figure only a relative number of actors are scanning from Iran. So lets see what was going on. First, a plot of the activity from Iran for February:
Click on the image for the full size. This data is fairly "rough" as it is just counting number of dropped packets. This could be one host sending the same packet over and over to the same target. (ok... about 2-3 Million times on the peak days)
Lets look at the ports affected next. Below you will see the data for February 16th:
+------+--------+ | port | count | +------+--------+ | 21 | 466735 | | 53 | 465751 | | 23 | 458511 | | 22 | 457712 | | 80 | 455077 | | 179 | 453416 | | 3389 | 5750 | | 445 | 4926 | | 4614 | 4721 | | 5900 | 356 |
This is getting a bit more interesting. the top 6 ports have almost the same number of "hits", and they are well known server ports. 179 (BGP) is in particular interesting as it is not scanned a lot and more of an "infrastructure" port. But one could expect routers to respond on 23, 22 and 80 as well. 21 and 53? Not exactly router ports.
One host that sticks out for port 179 scans that day (port 179 is easier to investigatate as there are less scans for this port then the others), is 213.217.37.102 .
Scans originating from this particular host confirm the original picture:
+------------+---------+---------+ | targetport | reports | targets | +------------+---------+---------+ | 21 | 386903 | 368 | | 22 | 379809 | 363 | | 23 | 380493 | 365 | | 53 | 387051 | 365 | | 80 | 374014 | 360 | | 179 | 378105 | 366 | +------------+---------+---------+
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Hmmmm
Bill
Feb 22nd 2013
1 decade ago
Laurie
Feb 22nd 2013
1 decade ago
- http://www.akamai.com/html/technology/dataviz1.html
Feb 24, 2013 - 07:43AM est
89.38% above normal...
.
PC.Tech
Feb 24th 2013
1 decade ago
http://junosgeek.blogspot.com/2013/02/junos-out-of-cycle-security-bulletin.html
Kyle
Feb 24th 2013
1 decade ago