File2pcap - A new tool for your toolkit!
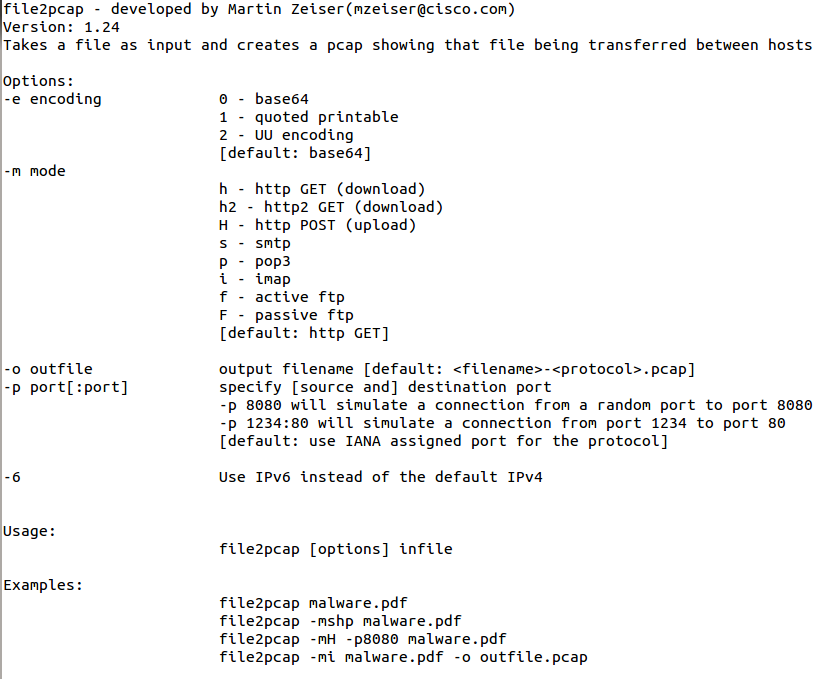
One of our readers, Gebhard, submitted a pointer to a tool today, released by Talos, that I wasn't familiar with. However, when I realized it could generate packets, I had to try it out. Its called File2pcap. The concept of the tool is that instead of having to download a file and capture the traffic in order to write detection content, the tool would simulate the download and generate the traffic that you would see. You get a nice pcap in the end. I took a relatively benign phishing pdf (it had a link in it) and used it for my test. The tool doesn't have any documentation until you compile it and run it. Here are your options:
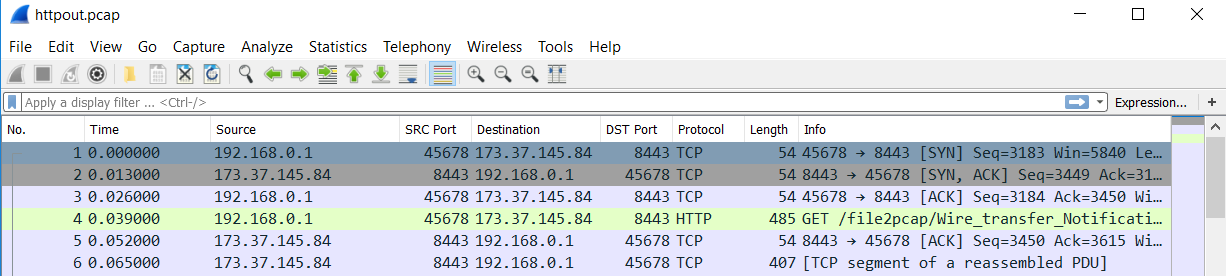
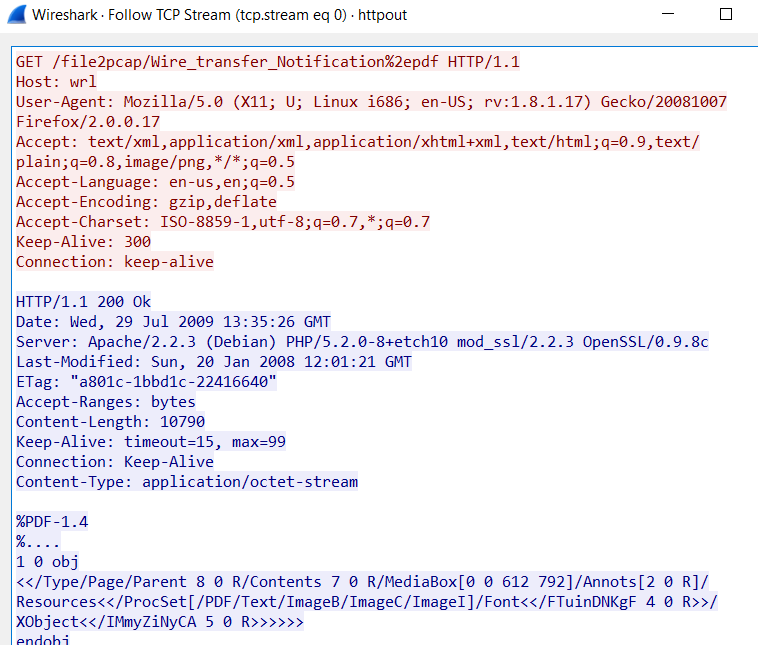
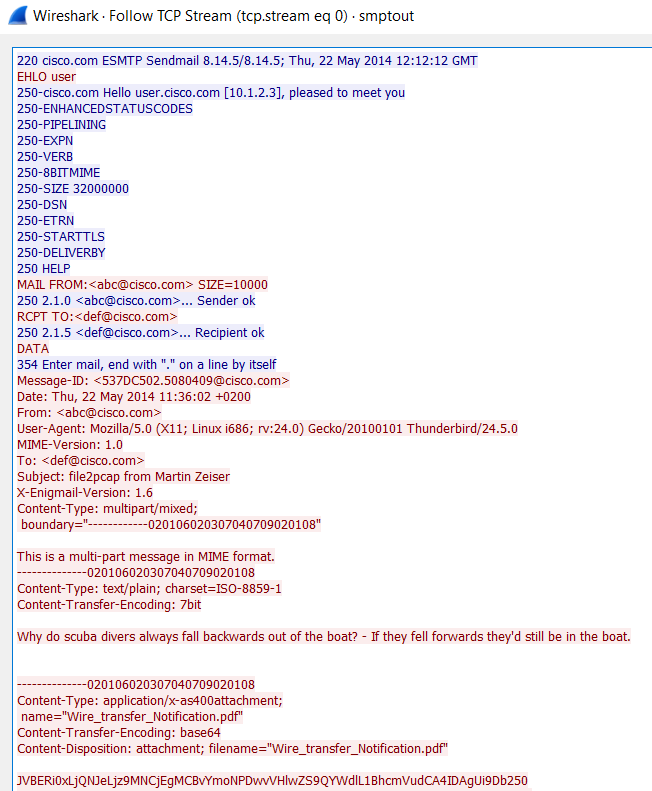
I ran a few test scenarios with it. One for HTTP and one for SMTP. For the HTTP, I used the following command line and specified a file name:
"Writing to httpout.pcap"


Comments