Maldoc VBA Anti-Analysis
I was asked for help with the analysis of sample 7c9505f2c041ba588bed854258344c
Here is the analysis with oledump.py:
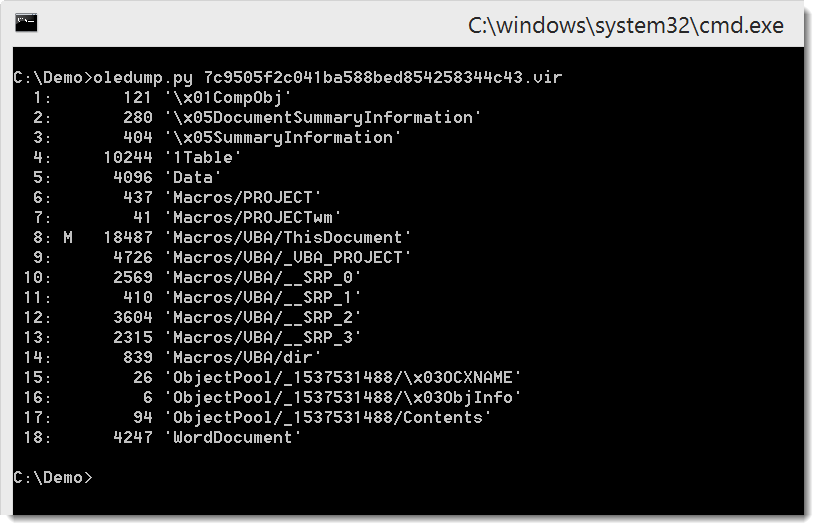
Stream 8 contains VBA code. Searching for string object in the code, we find calls to CreateObject:
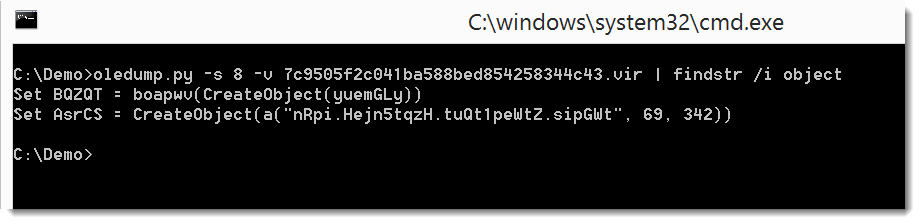
Notice the second call to CreateObject. The argument is a function call (a) with arguments that looks like an encoded string, and 2 numbers. Function a must be the decoding function. This time, in stead of spending time trying to understand how the decode function works and translating it to Python, I'm going to copy it to the VBA interpreter in Excel and execute it. I just have to be careful not to execute the payload. I achieve this by checking each function I copy for potential payload execution statements.
Here is the first step: I copy function a and test it by calling it from sub decode:
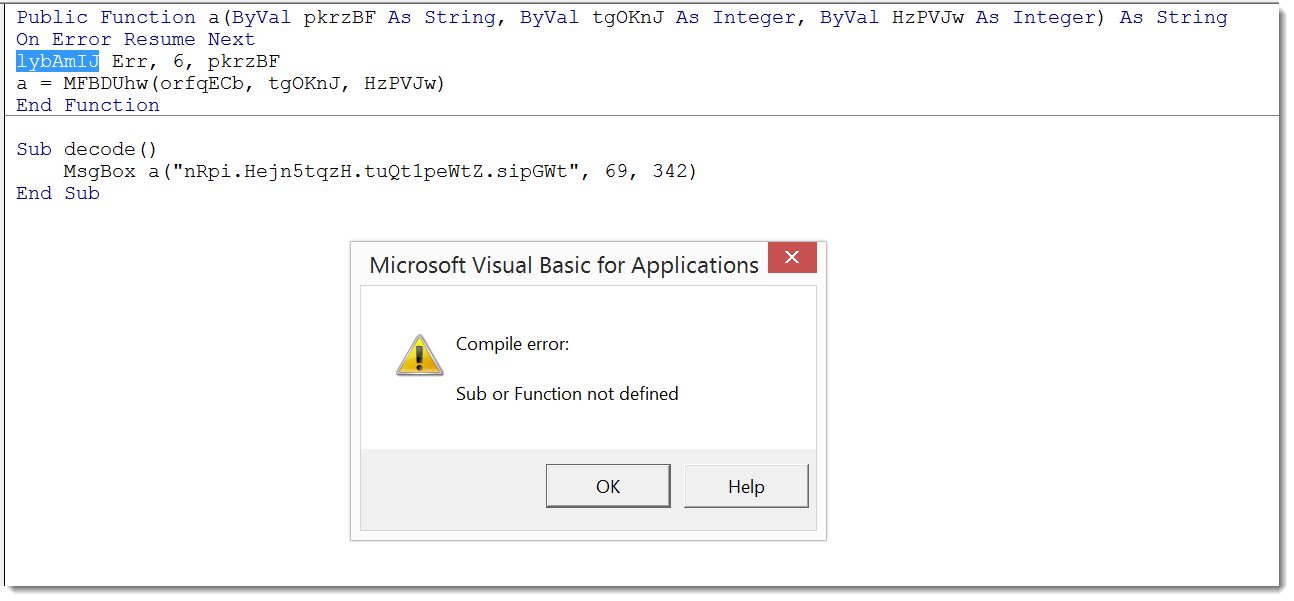
As you can see I get an error because function lybAmIJ is not defined. This is to be expected. By just copying function a, I'm probably missing other functions and code that function a uses. So next step is to add the missing function, run sub decode again, and repeat this process until I get no more error. And I must not forget to check each function I copy for potential payload execution. Finally the VBA code will run without errors, but the messagebox is empty:
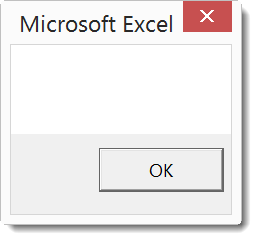
This probably means that I'm still missing some code, maybe uninitialized variables. So I single-step through the code (with the debugger), and I notice that orfqECb is empty:
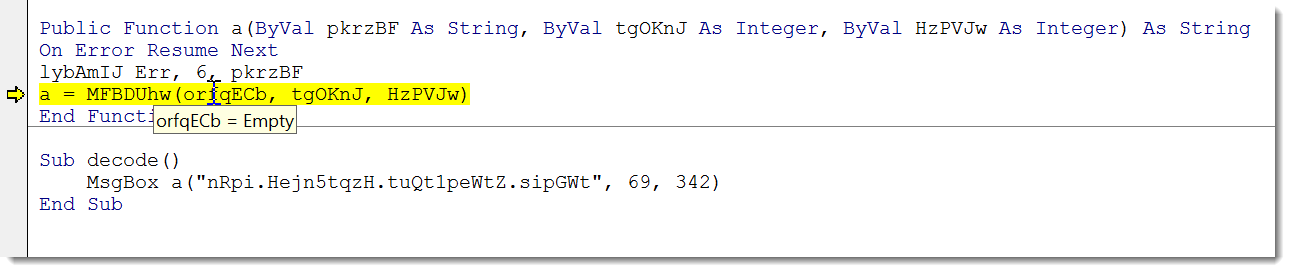
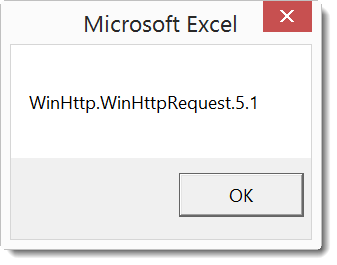
Searching through the code for orfqECb reveals that it is another function that I need to copy. I repeat the process, and finally I get the decoded string:
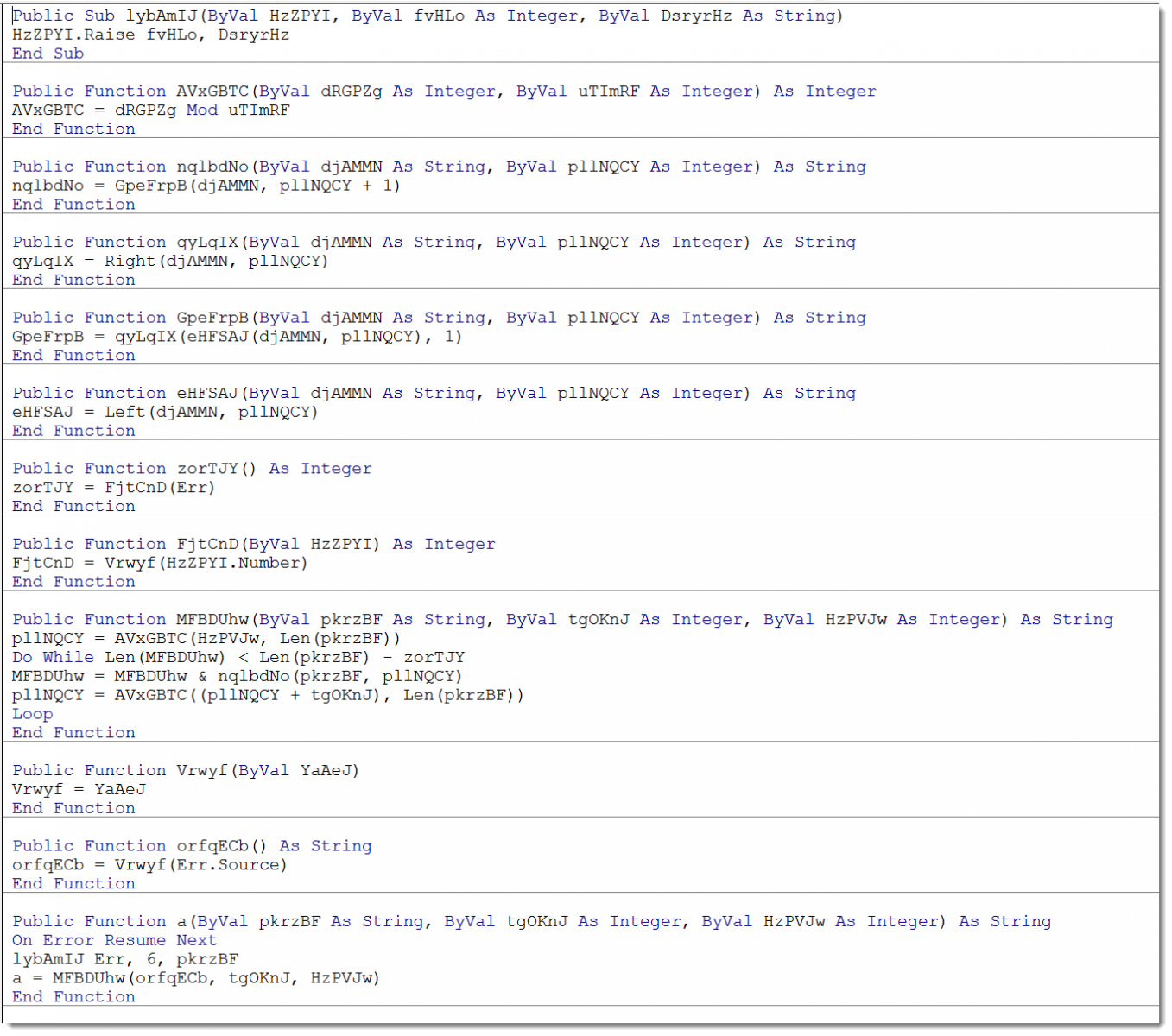
Here is all the code I had to copy:
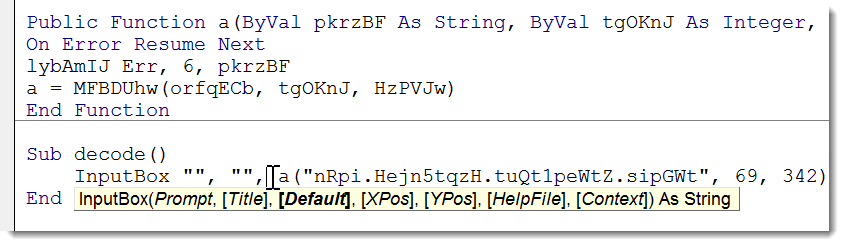
MsgBox is great for displaying the decoded string, but you can not copy the string. And it's useful to be able to copy the decoded string, for example when it is an URL. One trick is to replace MsgBox with InputBox, and provide the decoded string as the third argument: the default string for the InputBox. Like this:
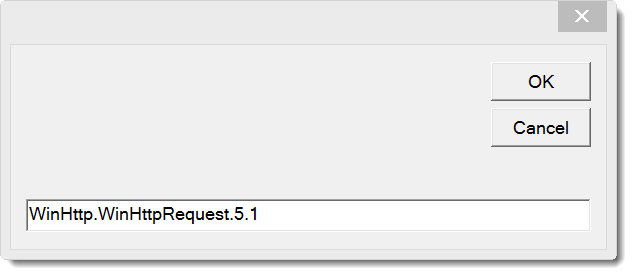
Another trick is to write the decoded string to a cell in the spreadsheet:

The advantage of using a cell, is that you can easily decode many strings and write the results in cells:
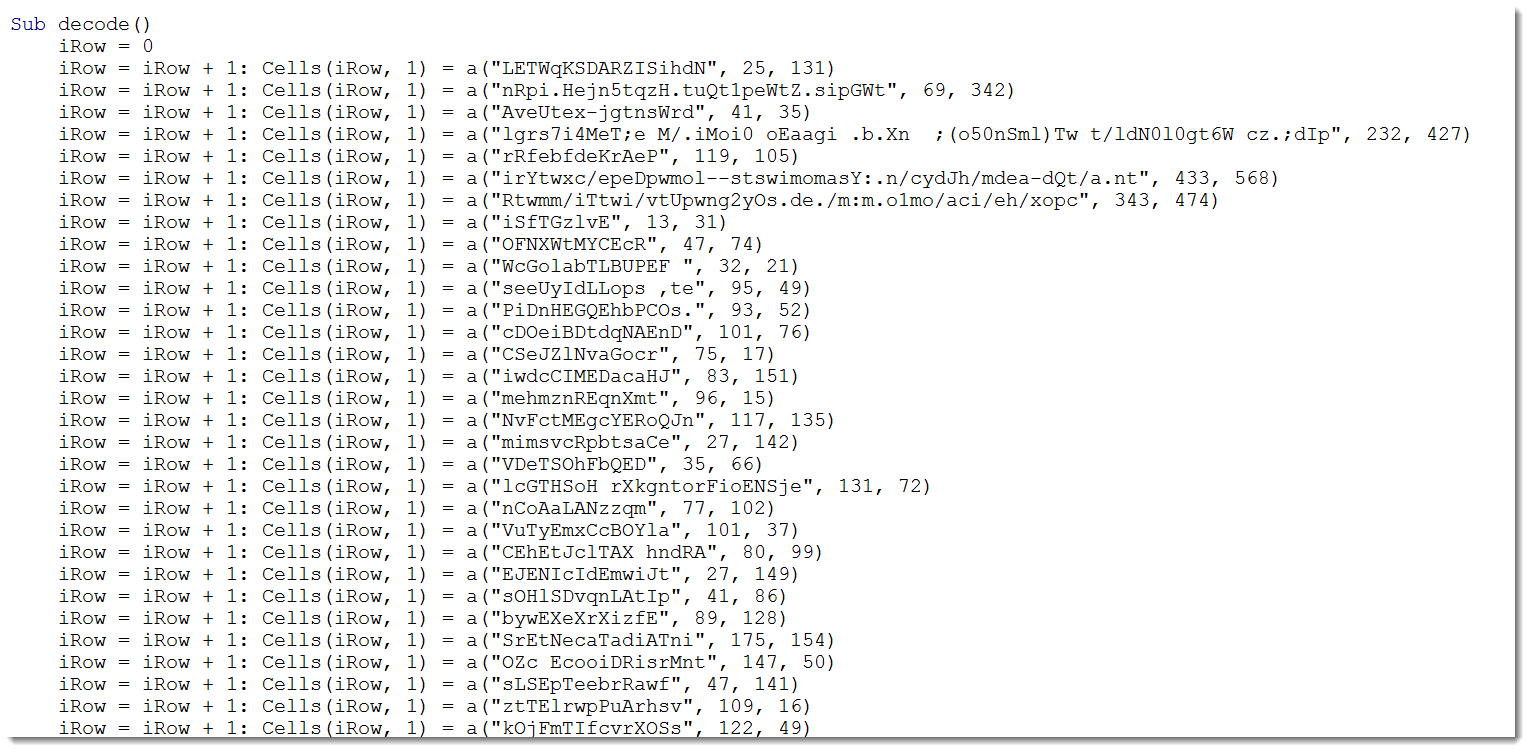
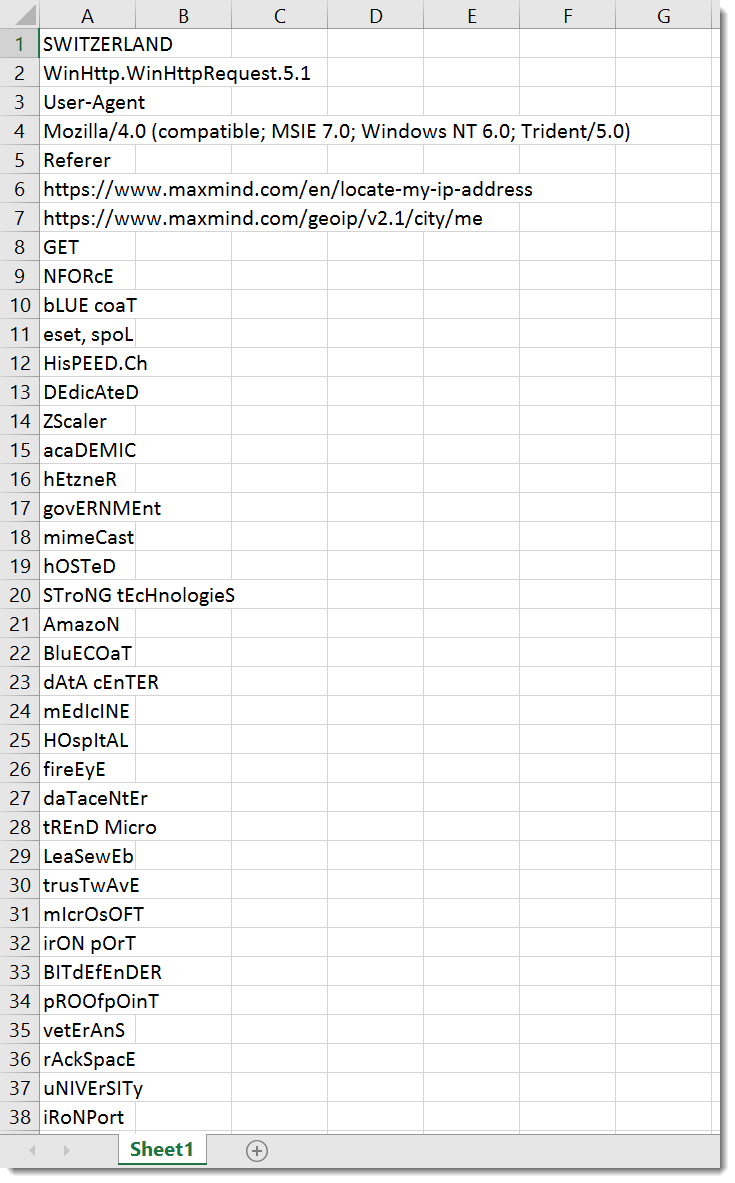
With all strings decoded, it becomes easier to understand what this sample does.
This sample does an IP-geolocation request to Maxmind, and aborts if the reply contains one of these strings:
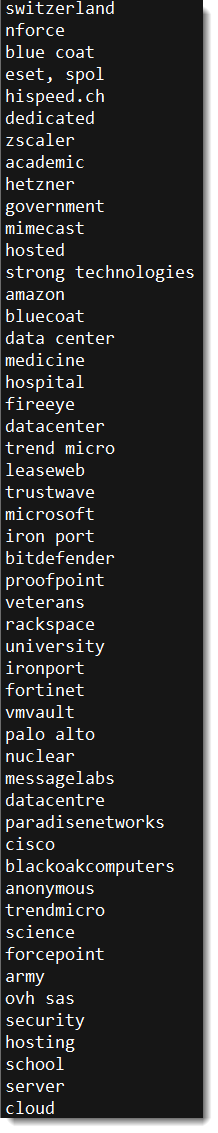
With this list, the malware authors want to avoid detection via dynamic analysis tools/appliances from security vendors (blue coat, eset, fireeye, ...). But it also avoids organizations with medicine, hospital, veterans, ... as keywords.
Next, it looks for running processes on the machine and aborts if it finds these:
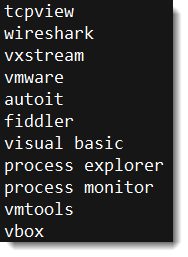
If there is no reason to abort execution, this PowerShell script is executed:

Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments