VBA Shellcode and EMET
Someone asked me if EMET would stop the malicious document I analyzed in my diary entry Hancitor Maldoc Bypasses Application Whitelisting.
In its default configuration, EMET will stop the shellcode from executing inside the Word process with its EAF protection. But there is no specific mitigation for the process replacement/process hollowing attack.
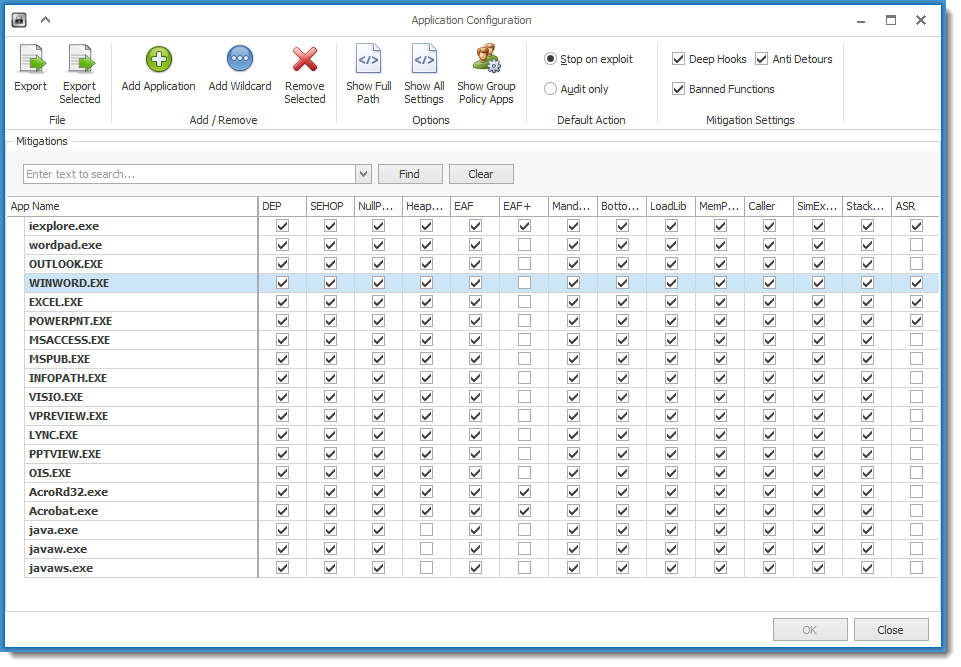
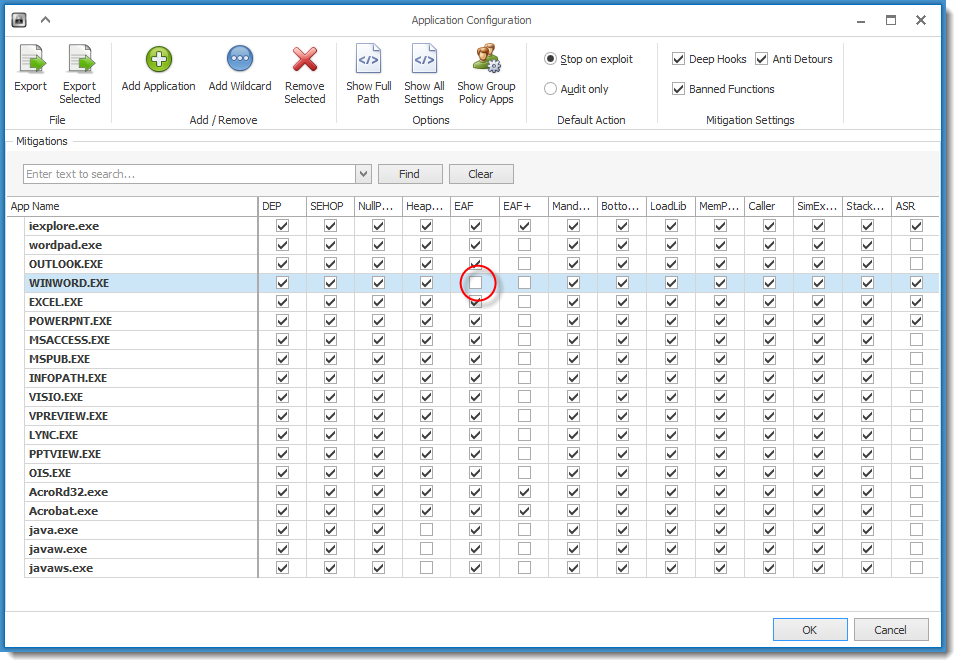
By default, EMET protects MS Word:
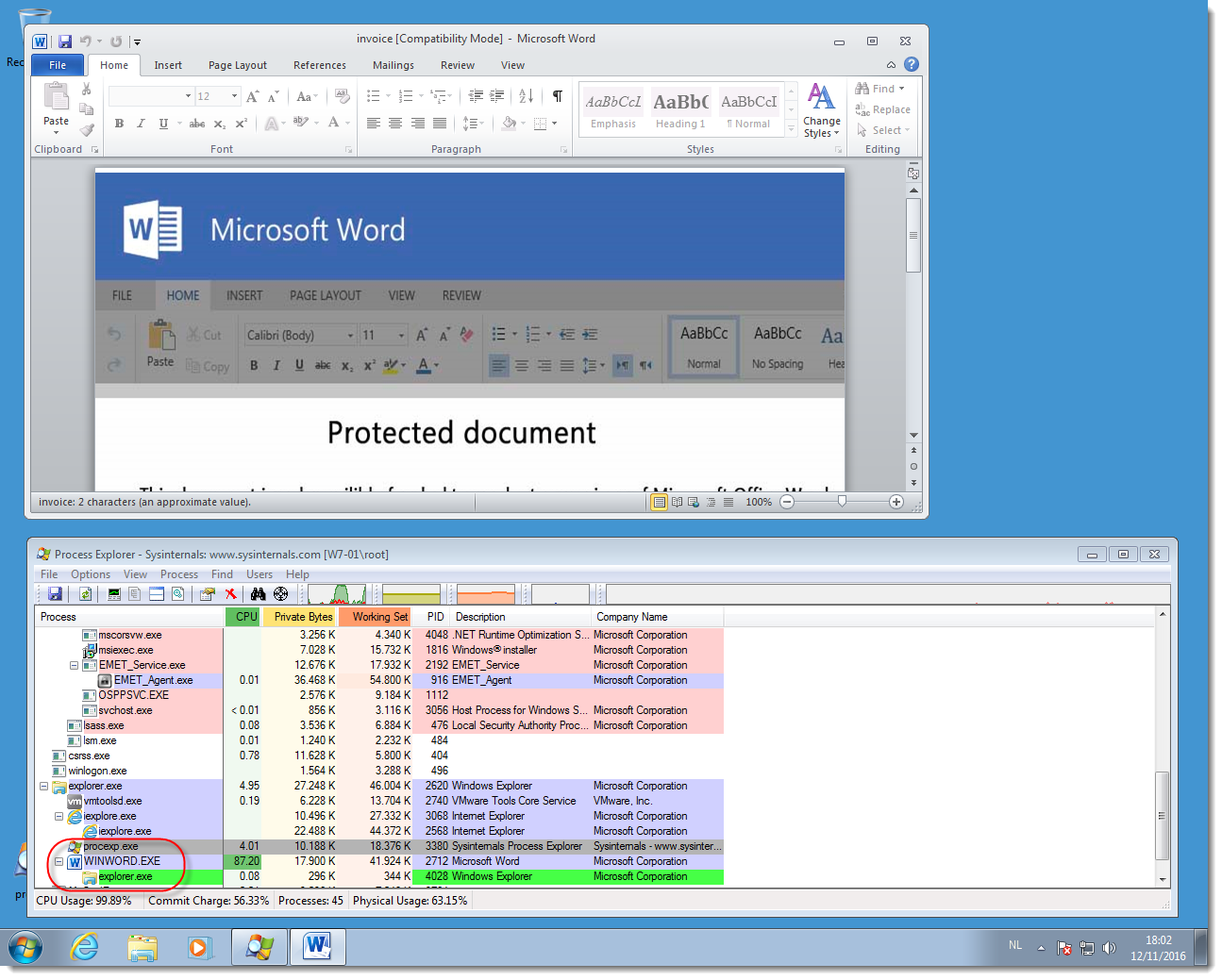
Opening the malicious Word document:
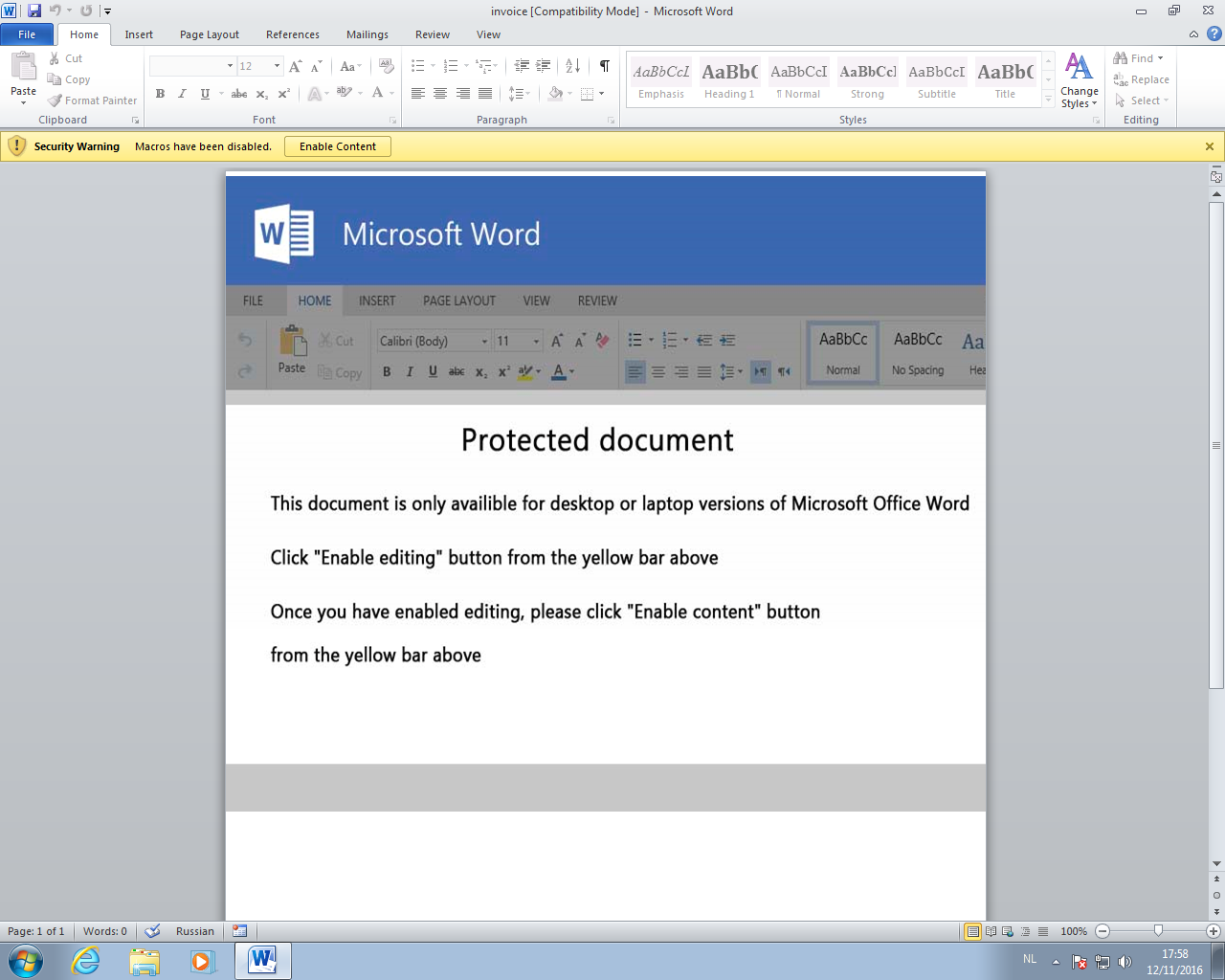
Because of the default macro settings, the VBA code will not execute.
But when we click Enable Content, the VBA code will execute. It will inject shellcode inside the Word process, and this shellcode will lookup the API functions it needs. This behavior will be detected by EMET's Export address table Access Filtering (EAF) and the Word process will be killed.
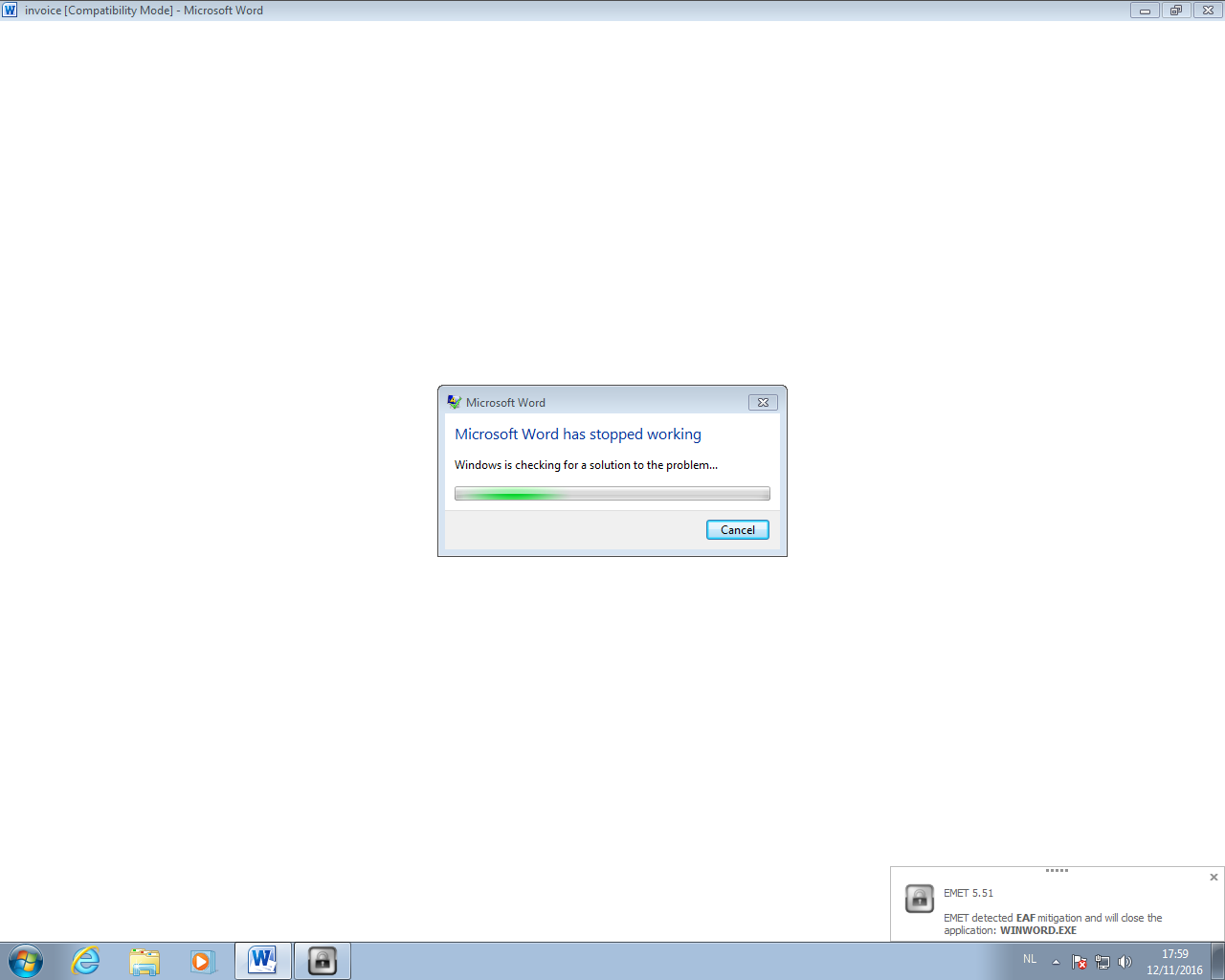
When we disable EAF, the shellcode will be able to run and thus do the process replacement. There is no mitigation for process replacement.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
NVISO


Comments
Anonymous
Nov 13th 2016
9 years ago
Also, with EMET we can collect logs and are able to detect when EAF and other protections are invoked. Would this information be available on Windows 10 by default, or is there a logging cheat sheet advice that we need to follow?
An example of reporting based on EMET; https://blogs.technet.microsoft.com/kfalde/2015/10/02/emet-reporting/
Didier, would you be bothered to try Windows 10 without EMET as well? :)
Anonymous
Nov 14th 2016
9 years ago
Also, with EMET we can collect logs and are able to detect when EAF and other protections are invoked. Would this information be available on Windows 10 by default, or is there a logging cheat sheet advice that we need to follow?
An example of reporting based on EMET; https://blogs.technet.microsoft.com/kfalde/2015/10/02/emet-reporting/
Didier, would you be bothered to try Windows 10 without EMET as well? :)[/quote]
I would be interested in this analysis too!
Anonymous
Nov 14th 2016
9 years ago
Anonymous
Nov 14th 2016
9 years ago
Anonymous
Nov 14th 2016
9 years ago
On Windows 10, the shellcode executes, but the process replacement seems to fail (often).
I'll post a diary entry when I have done more research.
Anonymous
Nov 15th 2016
9 years ago
There is lot of confusion on EMET's use in windows 10 with the built in protections and part of that comes from a mix of information that was released pre-Win10 and post-Win10 plus not being well understood. Windows 10 will only automatically extend the built-in protections to applications that are built with a recent version of Visual Studio and have enable (CFG) Control Flow Guard in the configuration [I want to say Visual Studio 2015 but don't quote me on that].
This leaves lots of questions on if 3rd party apps were coded with visual studio and CFG is enabled? Personally I use EMET with Windows 10 on all my high risk user apps.
Windows 10 anniversary edition did add few more policy options to extend the built in OS protections to applications without EMET's involvement like image loading (Controls what DLLs an app can load) and some of the EMET protections are available but I haven't been able to find options for all the options as of yet. Hopefully the future MS will offer more guidance on configuring these settings as well as complete 1 to 1 mapping for the current EMET options.
Anonymous
Nov 15th 2016
9 years ago
On Windows 10, the shellcode executes, but the process replacement seems to fail (often).
I'll post a diary entry when I have done more research.[/quote]
Thanks a lot, Didier - this is VERY helpful to follow through on.
I have opened a thread in MS Technet Security Forums on the "Feature mapping and migration path for EMET end-of-life"
https://social.technet.microsoft.com/Forums/security/en-US/ada2d63e-fca5-4714-8934-2f72af8068bb/feature-mapping-emet-vs-windows-10?forum=emet - I took the liberty of linking back to this diary entry.
I don't want Microsoft to get away (too easily) with killing off a security product that is both effective and configurable - and integrates well with SIEM products.
Tor.
Anonymous
Nov 16th 2016
9 years ago