SmartApeSG campaign uses ClickFix page to push NetSupport RAT
Introduction
This diary describes a NetSupport RAT infection I generated in my lab from the SmartApeSG campaign that used a ClickFix-style fake CAPTCHA page.
Known as ZPHP or HANEYMANEY, SmartApeSG is a campaign reported as early as June 2024. When it started, this campaign used fake browser update pages. But it currently uses the ClickFix method of fake CAPTCHA-style "verify you are human" pages.
This campaign pushes malicious NetSupport RAT packages for its initial malware infection, and I've seen follow-up malware from these NetSupport RAT infections.
How To Find SmartApeSG Activity
I can usually find SmartApeSG indicators from the Monitor SG account on Mastodon. I use URLscan to pivot on those indicators, so I can find compromised websites that lead to the SmartApeSG script.
The Infection
Sites compromised through this campaign display pages with a hidden injected script. Given the right conditions, this script kicks off a SmartApeSG chain of events. The image below shows an example.
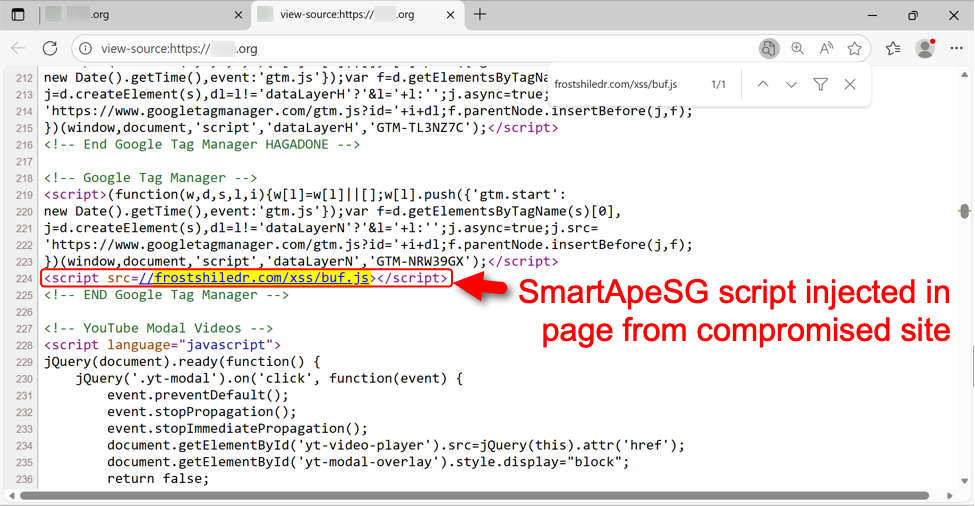
Shown above: Injected SmartApeSG script in a page from the compromised site.
In some cases, this injected script does not kick off the infection chain. I've had issues getting an infection chain during certain times of day, or if I try viewing the compromised website multiple times from the same source IP address. I don't know what the conditions are, but if those conditions are right, the compromised site shows a fake CAPTCHA-style "verify you are human" page.
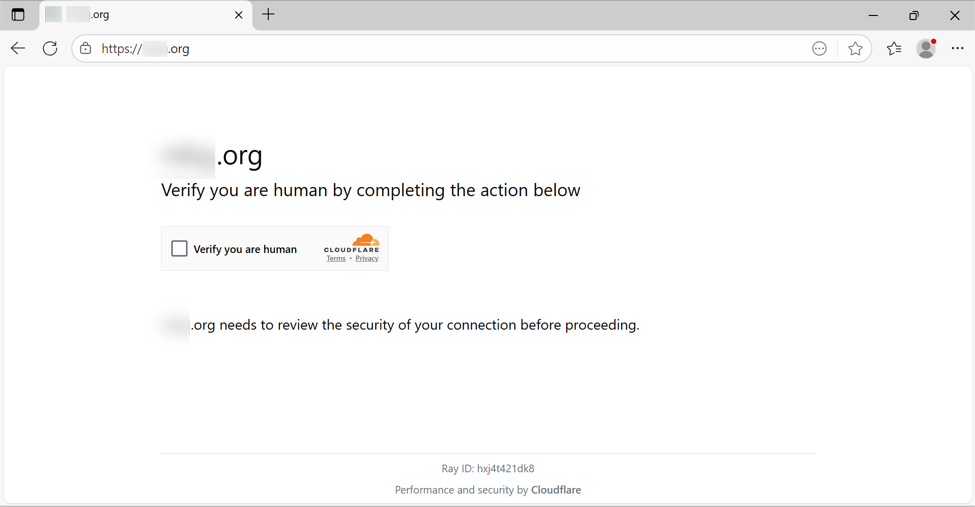
Shown above: Fake CAPTCHA page displayed by the compromised site.
Clicking the "verify you are human" box does the following:
- Injects malicious content into the Windows host's clipboard
- Generates a pop-up with instructions to open a Run window, paste content into the window, and run it.
The clipboard-injected content is a command string that uses the mshta command to retrieve and run malicious content that will generate a NetSupport RAT infection.
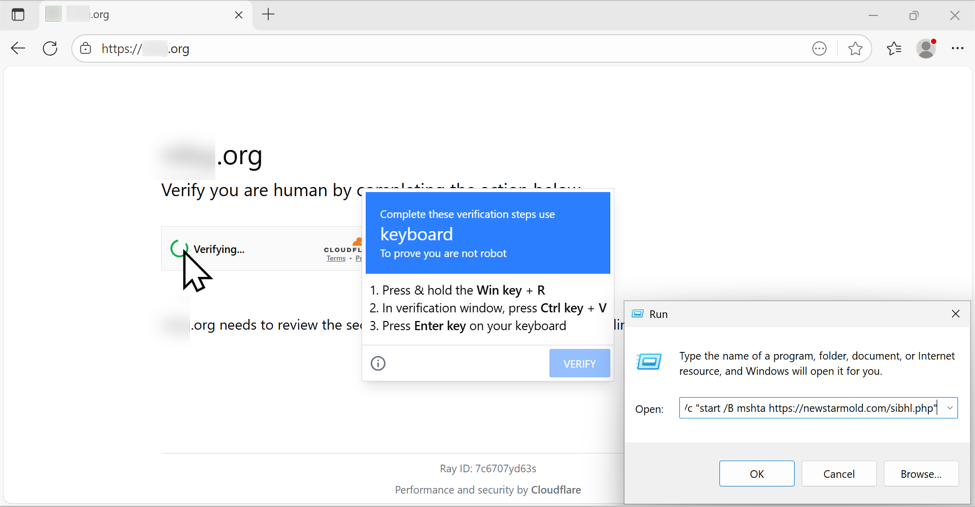
Shown above: Following ClickFix directions to paste content (a malicious command) into the Run window.
Below is a URL list of the HTTPS traffic directly involved in this infection.
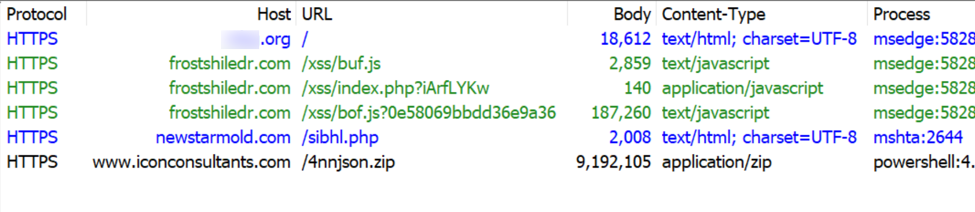
Shown above: HTTPS traffic directly involved in this SmartApe SG activity.
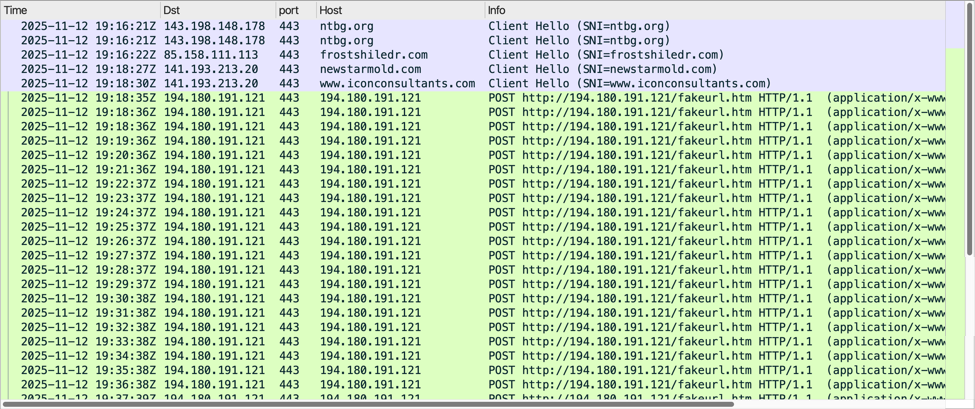
Shown above: Traffic from the infection filtered in Wireshark.
The malicious NetSupport RAT package stays persistent on the infected host through a Start Menu shortcut. The shortcut runs a .js file in the user's AppData\Local\Temp directory. That .js file runs the NetSupport RAT executable located in a folder under the C:\ProgramData\ directory.
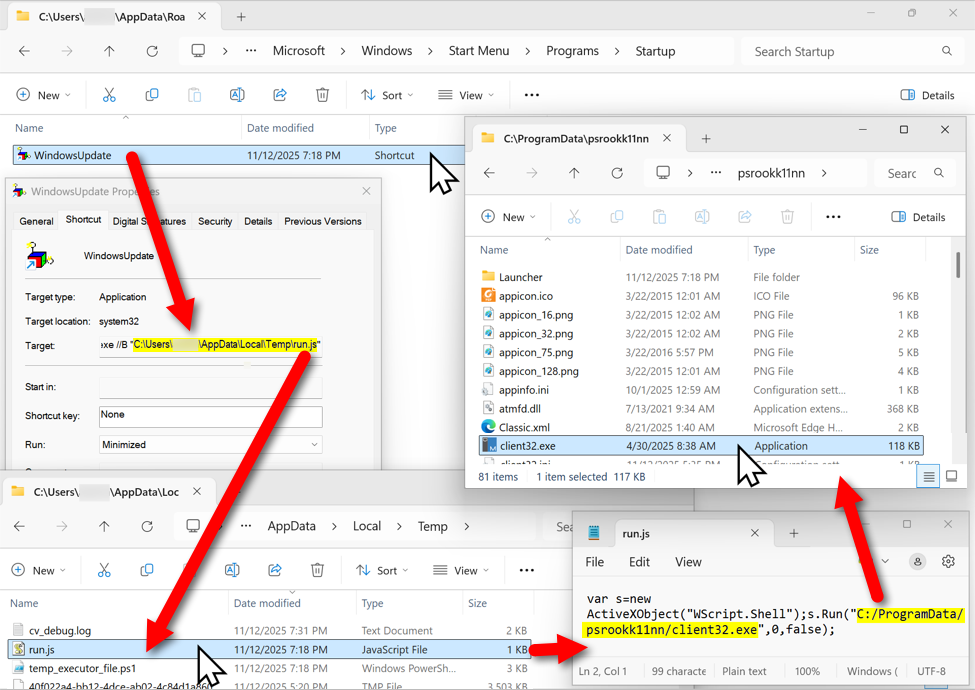
Shown above: The malicious NetSupport RAT package, persistent on an infected Windows host.
Indicators From This Activity
The following URLs were noted in traffic from this infection:
- hxxps[:]//frostshiledr[.]com/xss/buf.js <-- injected SmartApeSG script
- hxxps[:]//frostshiledr[.]com/xss/index.php?iArfLYKw
- hxxps[:]//frostshiledr[.]com/xss/bof.js?0e58069bbdd36e9a36 <-- fake CAPCHA page/ClickFix instructions
- hxxps[:]//newstarmold[.]com/sibhl.php <-- Script retrieved by ClickFix command
- hxxps[:]//www.iconconsultants[.]com/4nnjson.zip <-- zip archive containing malicious NetSupport RAT package
- hxxp[:]//194.180.191[.]121/fakeurl.htm <-- NetSupport RAT C2 traffic over TCP port 443
The following is the zip archive containing the malicious NetSupport RAT package:
- SHA256 hash: 1e9a1be5611927c22a8c934f0fdd716811e0c93256b4ee784fadd9daaf2459a1
- File size: 9,192,105 bytes
- File type: Zip archive data, at least v1.0 to extract, compression method=store
- File location: hxxps[:]//www.iconconsultants[.]com/4nnjson.zip
- Saved to disk as: C:\ProgramData\psrookk11nn.zip
Note: These domains change on a near-daily basis, and the NetSupport RAT package and C2 server also frequently change.
---
Bradley Duncan
brad [at] malware-traffic-analysis.net


Comments