Microsoft Patch Tuesday July 2018 (now with Dashboard!)
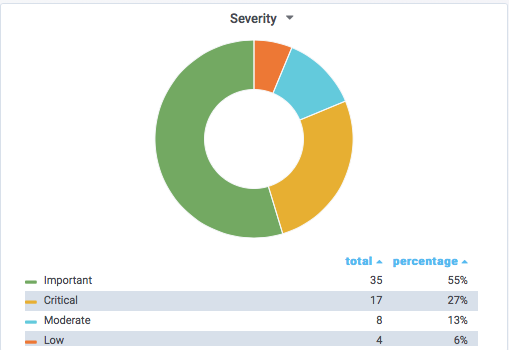
The July update fixes a total of 53 vulnerabilities (not counting Flash). 17 of these vulnerabilites are rated critical. 3 of these vulnerabilities have already been disclosed, but no exploits have been seen yet. As usual, the patches include today's Adobe advisory. As a special treat, we got a new "Dashboard" that our handler Renato Marinho put together. It should allow you to break down the patches better. Nice tool to explain the scope of the patches to management. Feel free to use screenshots and such, or include it /link to it from your security team's website.
You can find the dashboard at https://patchtuesdaydashboard.com
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| .NET Framework Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8202 | No | No | Less Likely | Less Likely | Important | ||
| .NET Framework Remote Code Execution Vulnerability | |||||||
| CVE-2018-8260 | No | No | Unlikely | Unlikely | Important | ||
| .NET Framework Remote Code Injection Vulnerability | |||||||
| CVE-2018-8284 | No | No | Less Likely | Less Likely | Important | ||
| .NET Framework Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8356 | No | No | Unlikely | Unlikely | Important | ||
| ASP.NET Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8171 | No | No | Unlikely | Unlikely | Important | ||
| Chakra Scripting Engine Memory Corruption Vulnerability | |||||||
| CVE-2018-8280 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8286 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8290 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8294 | No | No | - | - | Critical | 4.2 | 3.8 |
| Device Guard Code Integrity Policy Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8222 | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| Internet Explorer Security Feature Bypass Vulnerability | |||||||
| CVE-2018-0949 | No | No | More Likely | More Likely | Important | 2.4 | 2.2 |
| July 2018 Adobe Flash Security Update | |||||||
| ADV180017 | No | No | - | - | Important | ||
| MSR JavaScript Cryptography Library Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8319 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Access Remote Code Execution Vulnerability | |||||||
| CVE-2018-8312 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Edge Information Disclosure Vulnerability | |||||||
| CVE-2018-8289 | No | No | - | - | Important | 4.2 | 3.8 |
| CVE-2018-8297 | No | No | - | - | Important | 4.3 | 3.9 |
| CVE-2018-8324 | No | No | - | - | Critical | 4.3 | 3.9 |
| CVE-2018-8325 | No | No | - | - | Important | 4.3 | 3.9 |
| Microsoft Edge Memory Corruption Vulnerability | |||||||
| CVE-2018-8262 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8274 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8275 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8279 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8301 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8125 | No | No | - | - | Important | 4.2 | 3.8 |
| Microsoft Edge Spoofing Vulnerability | |||||||
| CVE-2018-8278 | Yes | No | - | - | Important | 4.3 | 3.9 |
| Microsoft Macro Assembler Tampering Vulnerability | |||||||
| CVE-2018-8232 | No | No | - | - | Moderate | ||
| Microsoft Office Remote Code Execution Vulnerability | |||||||
| CVE-2018-8281 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Office Tampering Vulnerability | |||||||
| CVE-2018-8310 | No | No | Less Likely | Less Likely | Low | ||
| Microsoft SharePoint Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8323 | No | No | Less Likely | Less Likely | Important | ||
| CVE-2018-8299 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft SharePoint Remote Code Execution Vulnerability | |||||||
| CVE-2018-8300 | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Wireless Display Adapter Command Injection Vulnerability | |||||||
| CVE-2018-8306 | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
| Open Source Customization for Active Directory Federation Services XSS Vulnerability | |||||||
| CVE-2018-8326 | No | No | - | - | Important | ||
| PowerShell Editor Services Remote Code Execution Vulnerability | |||||||
| CVE-2018-8327 | No | No | Less Likely | Less Likely | Critical | ||
| Remote Code Execution Vulnerability in Skype For Business and Lync | |||||||
| CVE-2018-8311 | No | No | Less Likely | Less Likely | Important | ||
| Scripting Engine Memory Corruption Vulnerability | |||||||
| CVE-2018-8242 | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| CVE-2018-8283 | No | No | - | - | Critical | 4.2 | 3.8 |
| CVE-2018-8287 | No | No | More Likely | More Likely | Important | 6.4 | 5.8 |
| CVE-2018-8288 | No | No | - | - | Critical | 6.4 | 5.8 |
| CVE-2018-8291 | No | No | - | - | Critical | 6.4 | 5.8 |
| CVE-2018-8296 | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| CVE-2018-8298 | No | No | - | - | Critical | 4.2 | 3.8 |
| Scripting Engine Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8276 | No | No | - | - | Important | 4.3 | 3.9 |
| Skype for Business and Lync Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8238 | No | No | Less Likely | Less Likely | Important | ||
| Visual Studio Remote Code Execution Vulnerability | |||||||
| CVE-2018-8172 | No | No | Less Likely | Less Likely | Important | ||
| Win32k Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8282 | No | No | More Likely | Unlikely | Important | 8.8 | 8.8 |
| Windows DNSAPI Denial of Service Vulnerability | |||||||
| CVE-2018-8304 | No | No | - | - | Important | 5.9 | 5.3 |
| Windows Denial of Service Vulnerability | |||||||
| CVE-2018-8309 | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
| Windows Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8313 | Yes | No | More Likely | More Likely | Important | 7.8 | 7.1 |
| CVE-2018-8314 | Yes | No | - | - | Important | 4.3 | 3.9 |
| Windows FTP Server Denial of Service Vulnerability | |||||||
| CVE-2018-8206 | No | No | Less Likely | Less Likely | Important | 7.5 | 6.7 |
| Windows Kernel Elevation of Privilege Vulnerability | |||||||
| CVE-2018-8308 | No | No | Less Likely | Less Likely | Important | 6.6 | 5.9 |
| Windows Mail Client Information Disclosure Vulnerability | |||||||
| CVE-2018-8305 | No | No | - | - | Important | ||
| WordPad Security Feature Bypass Vulnerability | |||||||
| CVE-2018-8307 | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
Keywords:
6 comment(s)
My next class:
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |
×
![modal content]()
Diary Archives


Comments
Security risk blocked for your protection
Reason:
This category is filtered: Newly Registered Websites. Sites in this category may pose a security threat to network resources or private information and are blocked.
URL: https://patchtuesdaydashboard.com
Anonymous
Jul 10th 2018
7 years ago
Anonymous
Jul 10th 2018
7 years ago
Keep up the good work, we all appreciate your hard work (all the handlers).
Anonymous
Jul 10th 2018
7 years ago
Anonymous
Jul 11th 2018
7 years ago
Thank you!
Anonymous
Jul 12th 2018
7 years ago
There is reports of issues on several apps.
.Net Framework
https://blogs.msdn.microsoft.com/dotnet/2018/07/20/advisory-on-july-2018-net-framework-updates/
Exchange Server
https://blogs.technet.microsoft.com/exchange/2018/07/16/issue-with-july-updates-for-windows-on-an-exchange-server/
SQL Server
https://blogs.msdn.microsoft.com/psssql/2018/07/26/july-10-2018-windows-updates-cause-sql-startup-issues-due-to-tcp-port-is-already-in-use-errors/
Happy Patching!
Anonymous
Jul 31st 2018
7 years ago