Having a look at the DDOS tool used in the attacks today
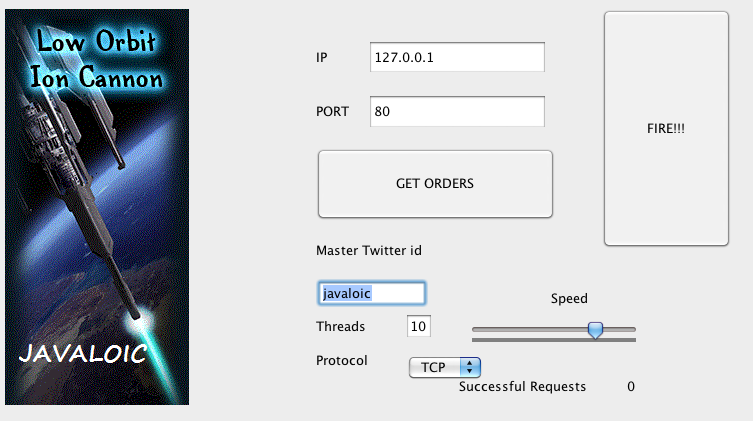 |
You enter the twitter ID that has been communicated to you and then once you enter it on the screen you click the "Get Orders" button and when ready you click the "Fire!!" button. Other than that there isn't really that much to the application. The application uses a hardcoded URL with an interchangeable twitter ID. It pulls a json file down and parses it for target, protocol and port information. When the "Fire!!!" Button is pressed a number of sessions are established with the target server (in my test cases 7 sessions were established). The string "hihihihihihihihihihihihihihihihi" is sent to the port (I assume this may be configurable). And that is basically it. The flood module cranks out multiple requests at a time and the target server gets busy |
UPDATE
|
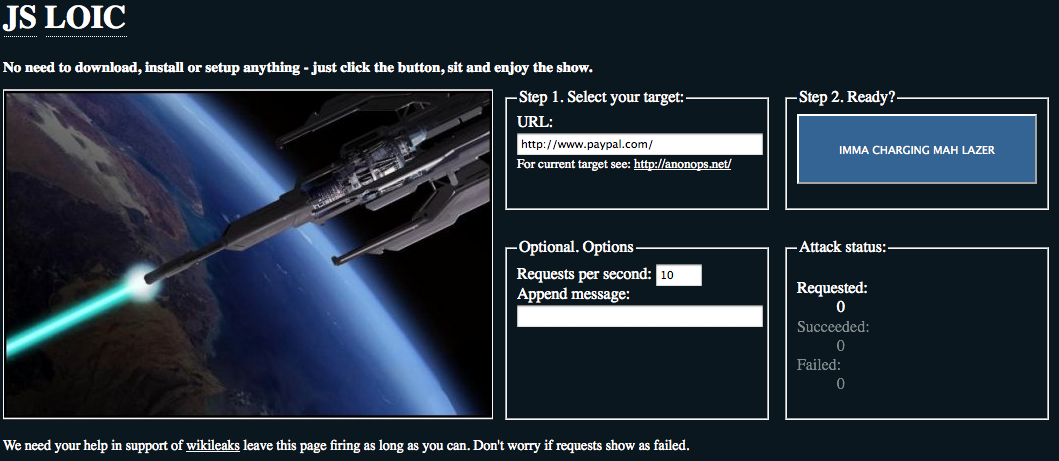
A Java Script version of LOIC is also being used (thanks Jeff). As you can see from the screen shot it comes pre targeted, in this case paypal. There is also a mobile version which doesn't look as pretty and is currently not pre-targeted and uses the same http requests. From the code it does a HTTP request from the target site and has some elements in the code as to not adversely affect the browser being used. Target changes are communicated via the IRC channel to participants. From the looks of it the code could easily be modified to "autofire" rather than require a user to chose to participate. |
 |



Comments
pedantry
Dec 9th 2010
1 decade ago
Mark
Dec 9th 2010
1 decade ago
We're not actually advocating that people partake in this illegal attack now, are we? :p
finnoybu
Dec 9th 2010
1 decade ago
Jim
Dec 9th 2010
1 decade ago
Tom
Dec 9th 2010
1 decade ago
Chavez243
Dec 9th 2010
1 decade ago
attempting to obtain GIAC certification at any level must act in a lawful and ethical
fashion for the benefit of the public, the profession and the companies to whom
they provide professional services"
Mike
Dec 9th 2010
1 decade ago
P
Dec 9th 2010
1 decade ago
What I do like about this is that the end user is making a conscious decision to turn his or her computer over to the controller and become an active participant in an illegal activity. It's a voluntary botnet and the volunteer participant is now just as liable as the bot controller.
Oh, and "whack"-a-mole I think is the proper spelling there.
A
Dec 9th 2010
1 decade ago
anti spelling nazi
Dec 9th 2010
1 decade ago